777-azure-notes-3(az-104)
Online Hosted Instructions | AZ-104-MicrosoftAzureAdministrator
- great online doc for azure in cli Azure Citadel
online lab:
-
exercies lab 8 is useful in setting network
-
‘AZ-104 Official Course Study Guide.pdf’ → contains all the official doc from MS learn by exam topic (useful in work too)
- like detailed json (arm template)
-
777-az104-offical-doc → by exam topics links
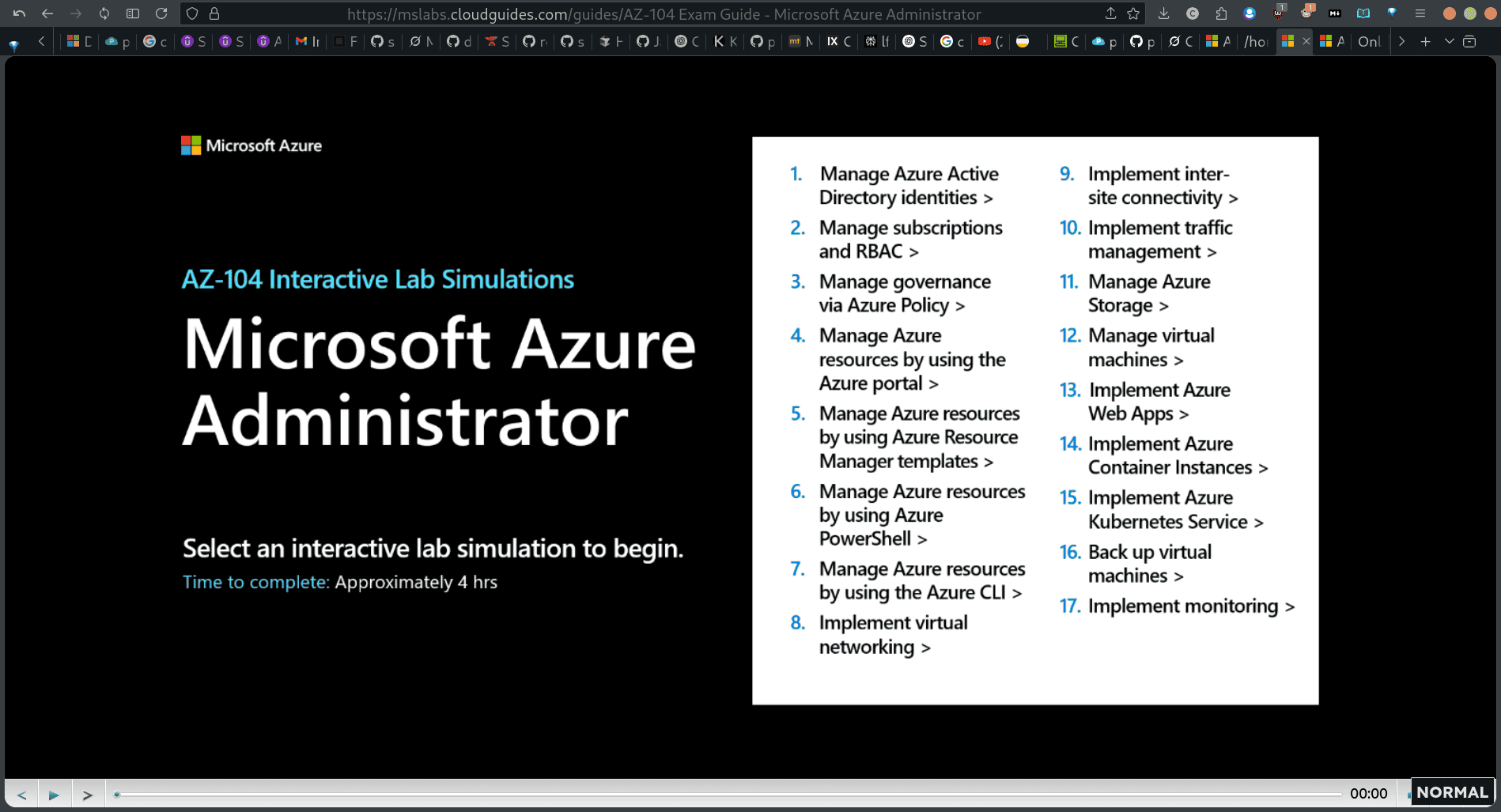 → clickable
→ clickable
- Manage Azure Active Directory identities >
- in private mode browser
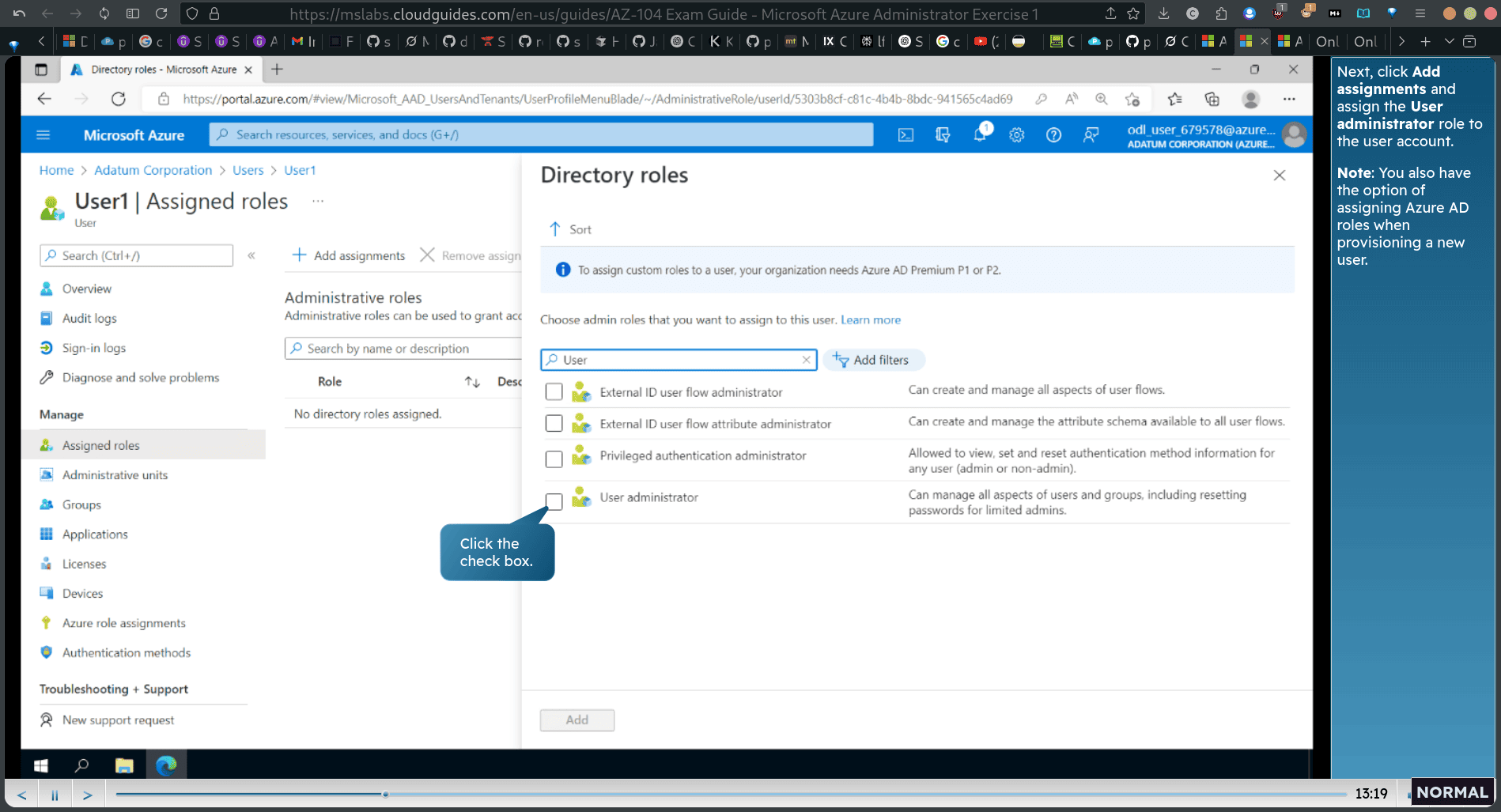
Task 2: Create Azure AD groups with assigned and dynamic membership
- asign user to use these premium active directory
- create group
- dynamic user
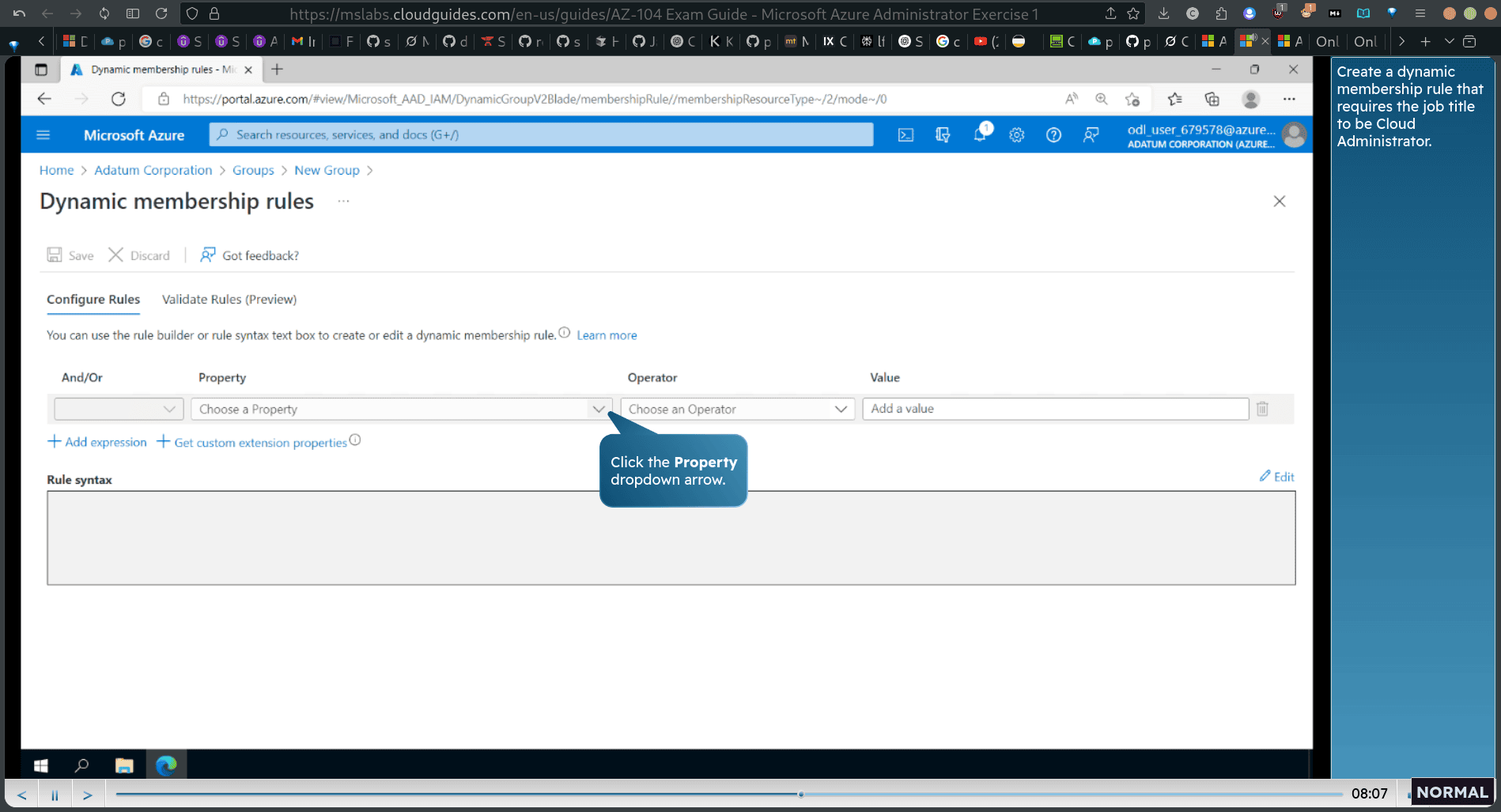 dynamic query (rule that appiled)
dynamic query (rule that appiled)
e.g. job title equal cloud administrator
 another example
another example
 assigned example
pick the user
assigned example
pick the user
Task 3: Create an Azure AD tenant
Task 4: Manage Azure AD guest users
- copy User principal name
- switching
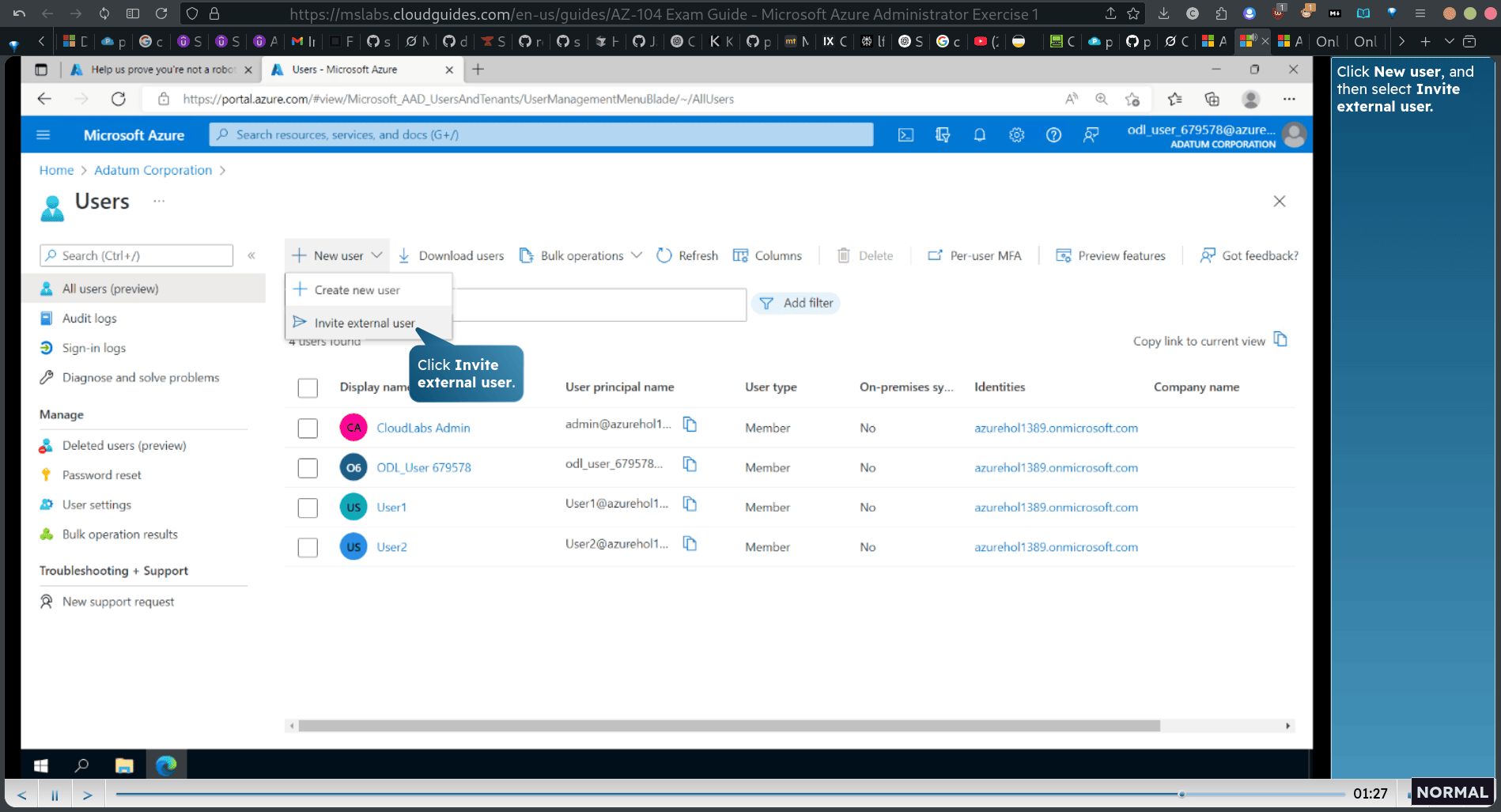 invite external user
invite external user
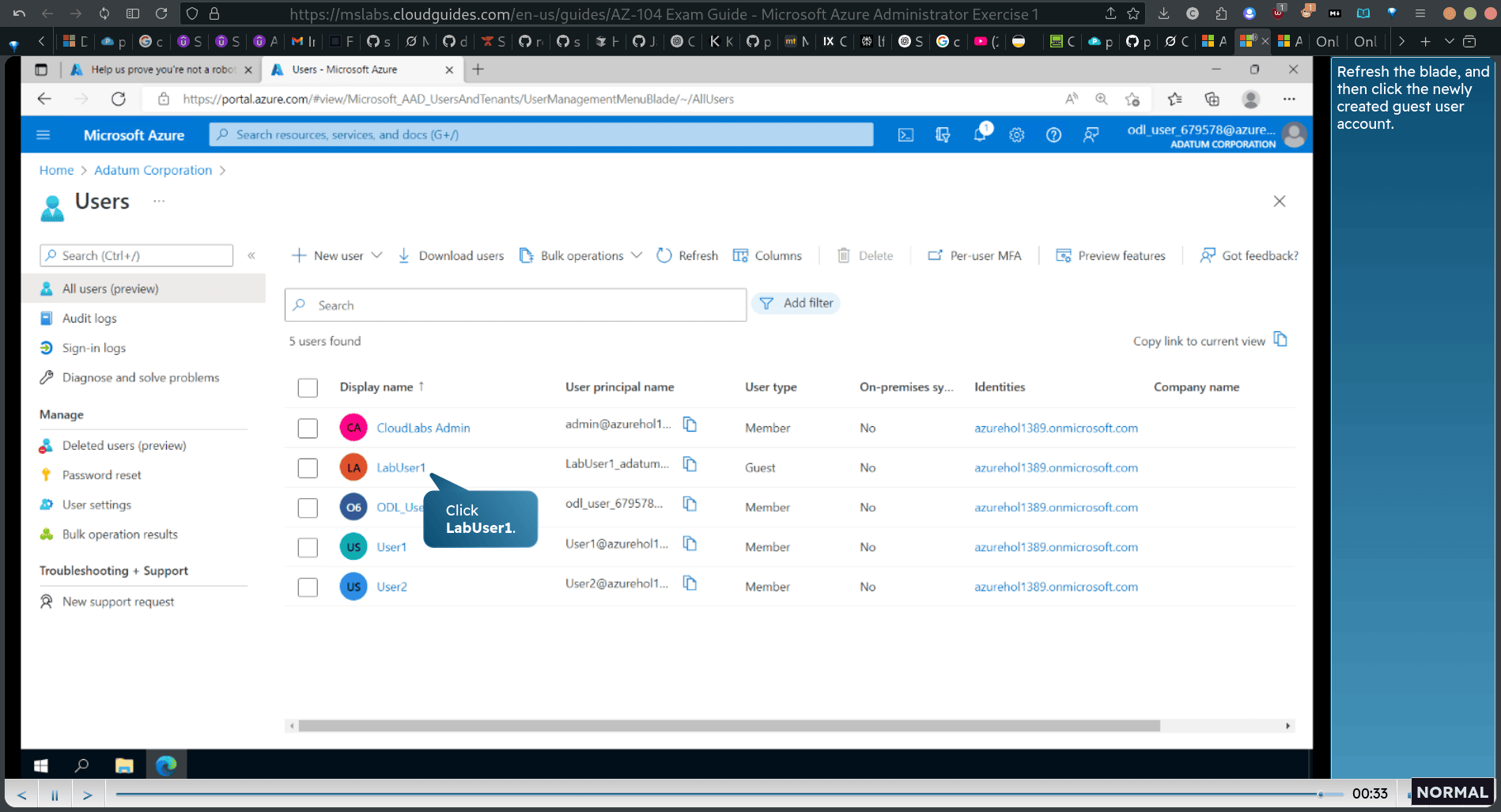
- guest user now
and then add the user into group
2. Manage subscriptions and RBAC >
Task 1: Implement management groups
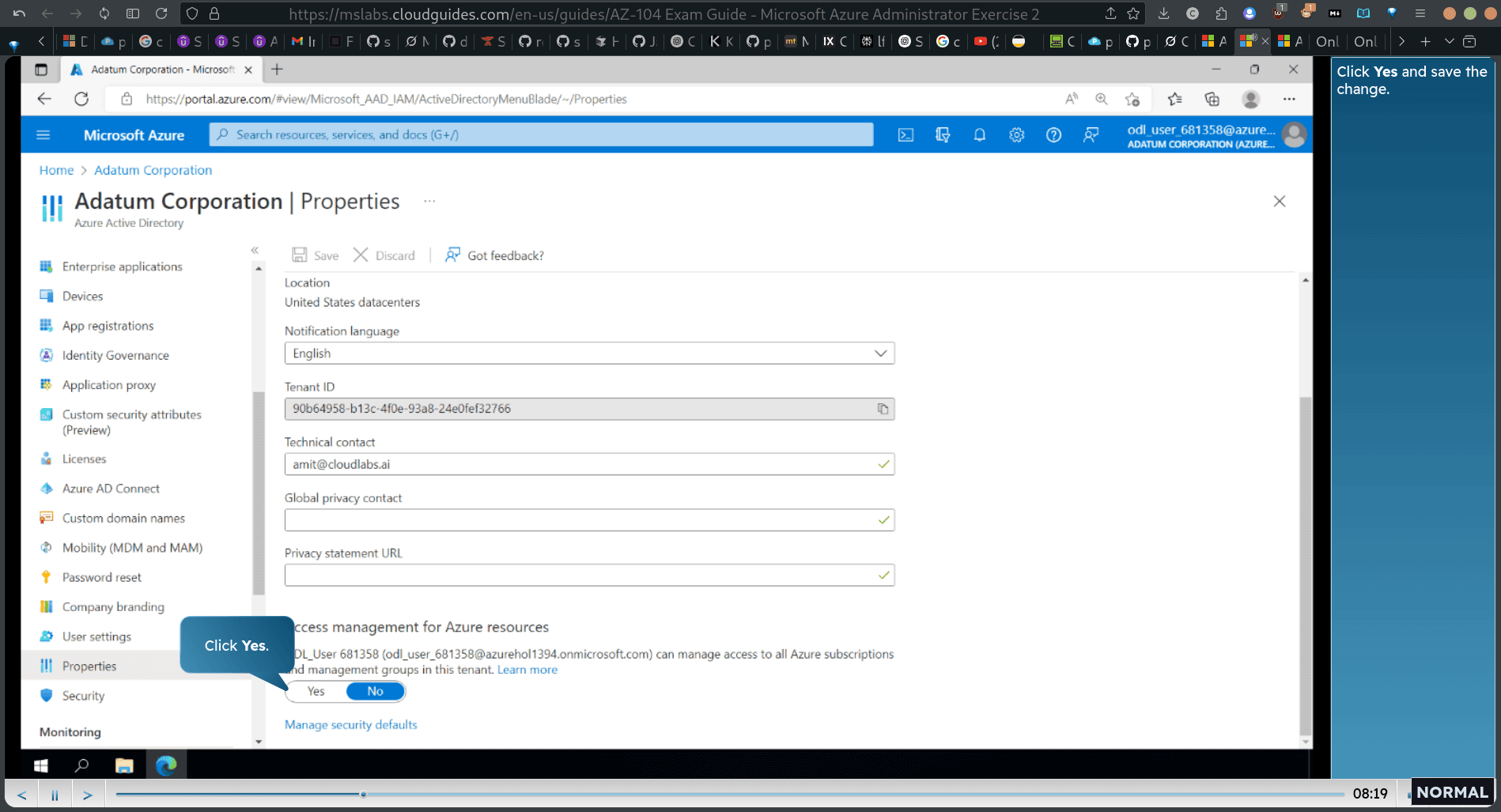 property → setting → access
property → setting → access
search management group
click start using management group
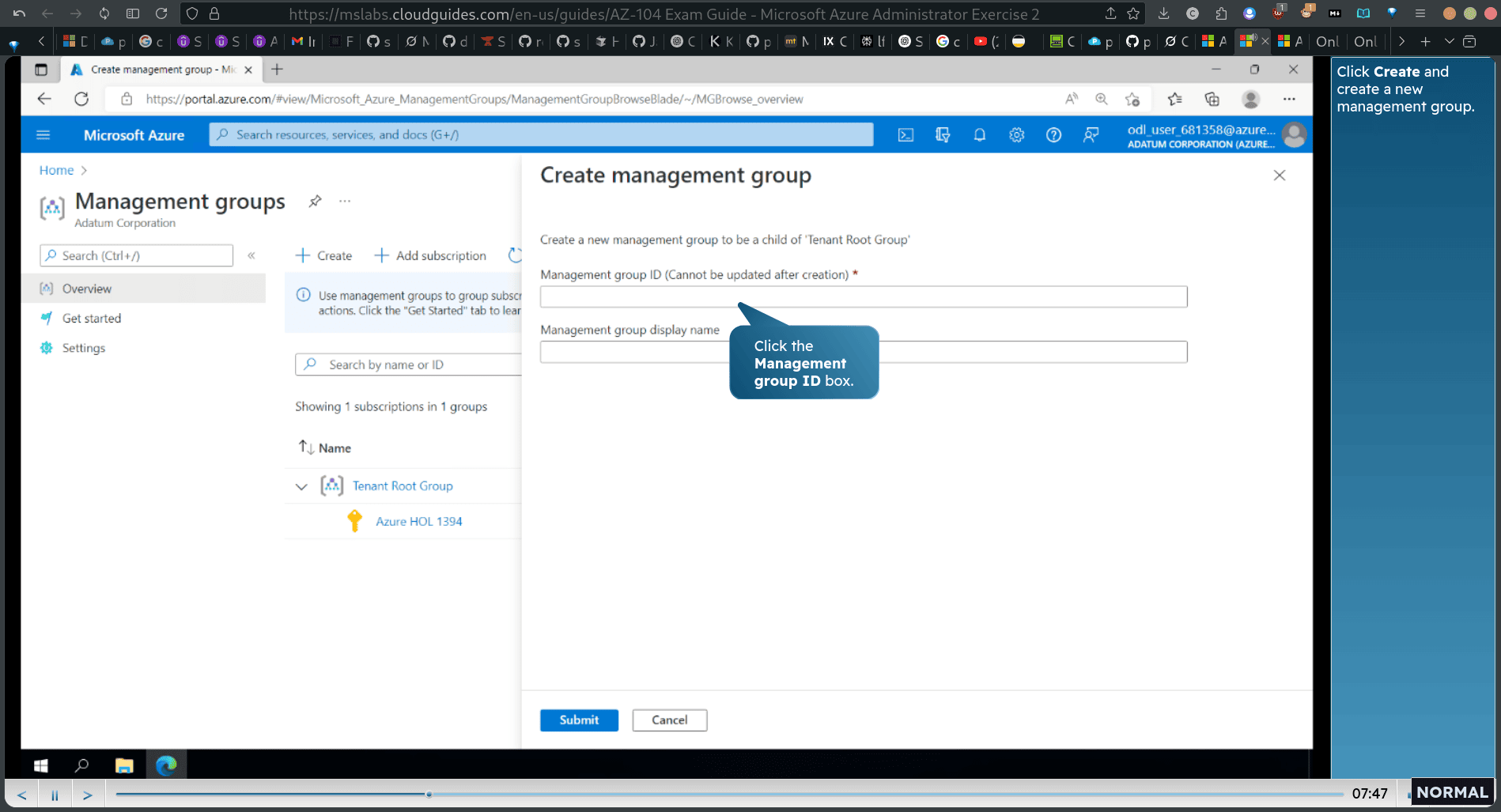
- create a new management group
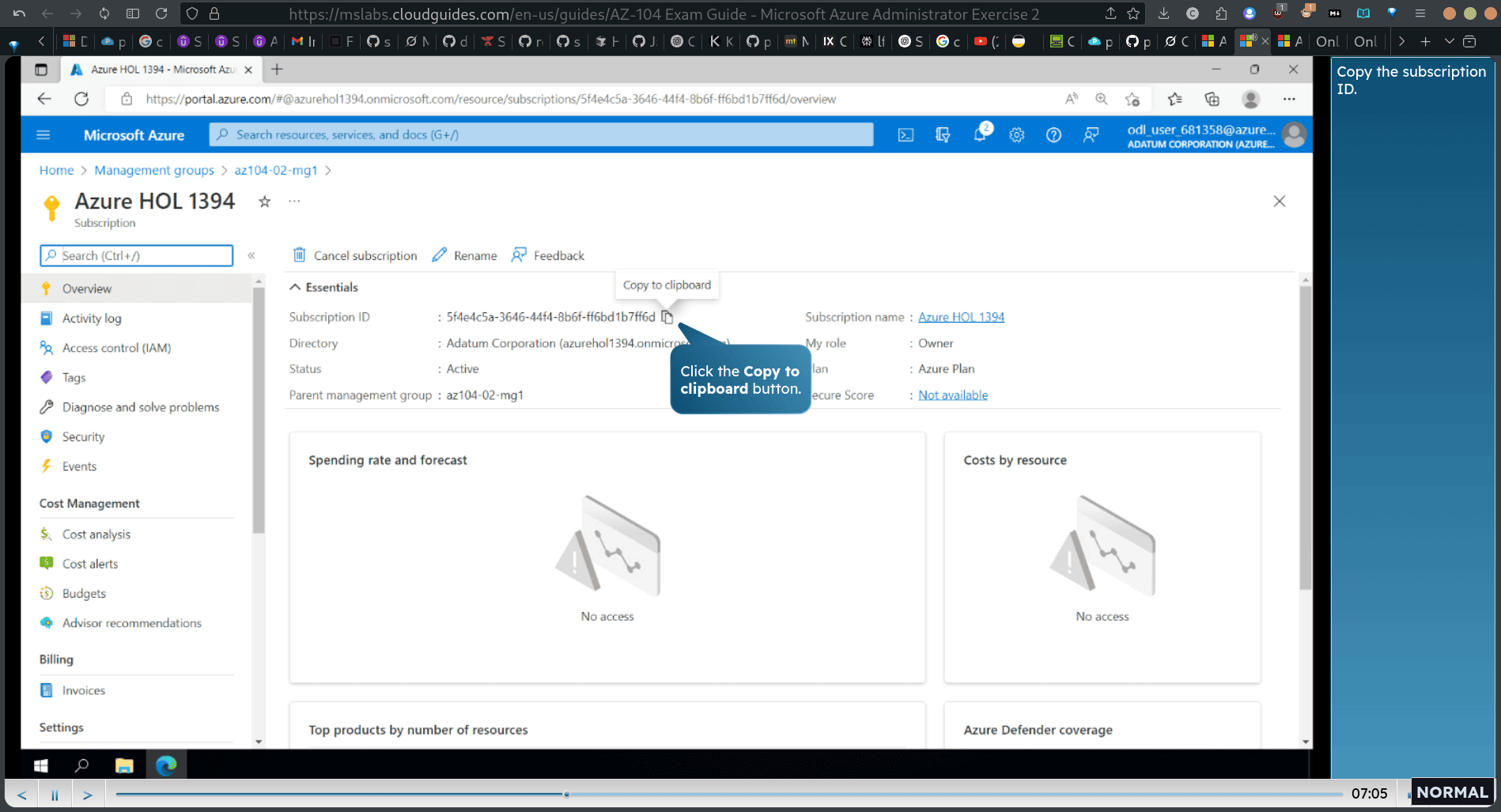
- copy the subscription ID
Task 2: Create custom RBAC roles
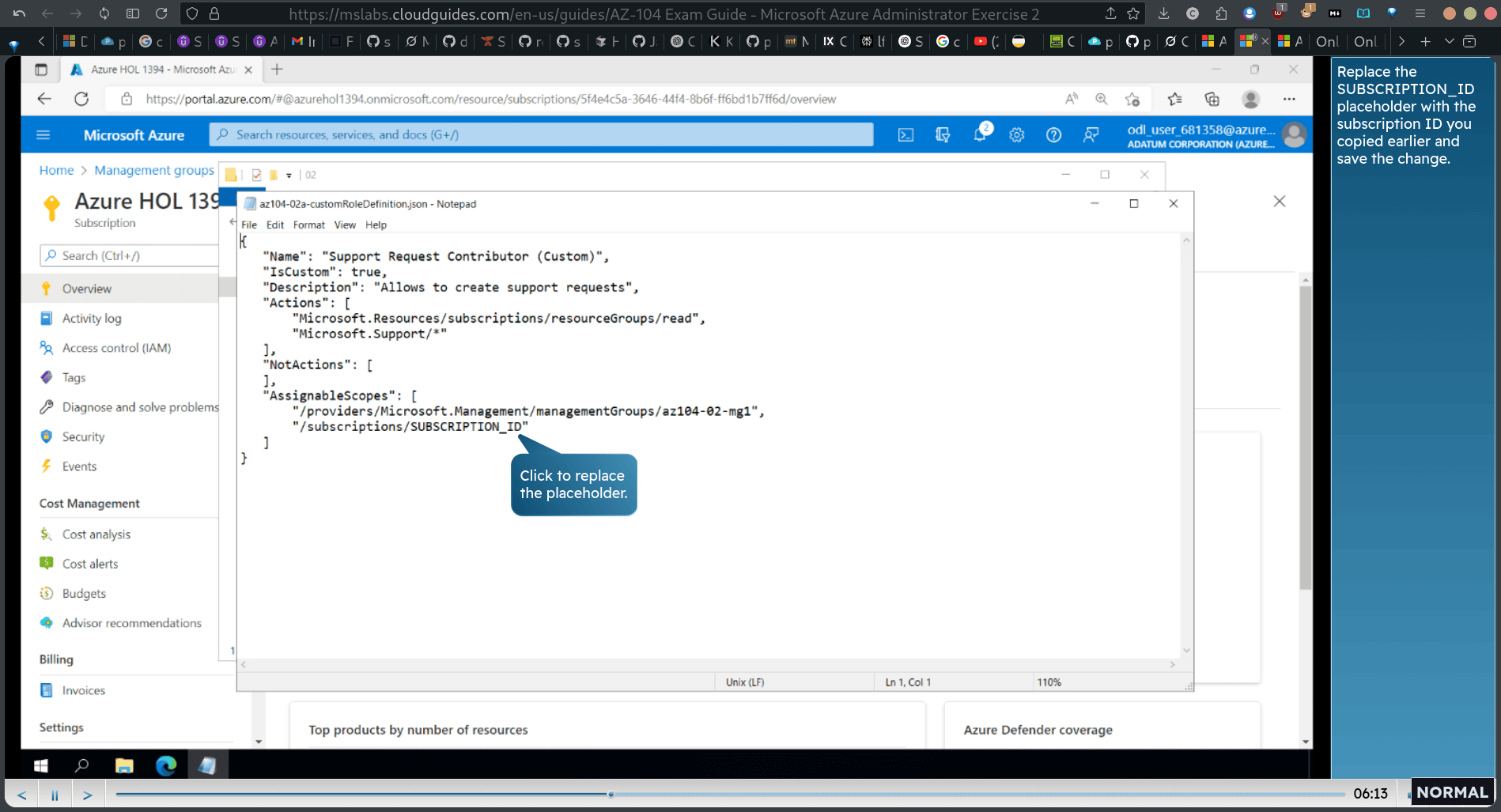
- replace the sub ID (from clipboard)
cloud shell → power shell
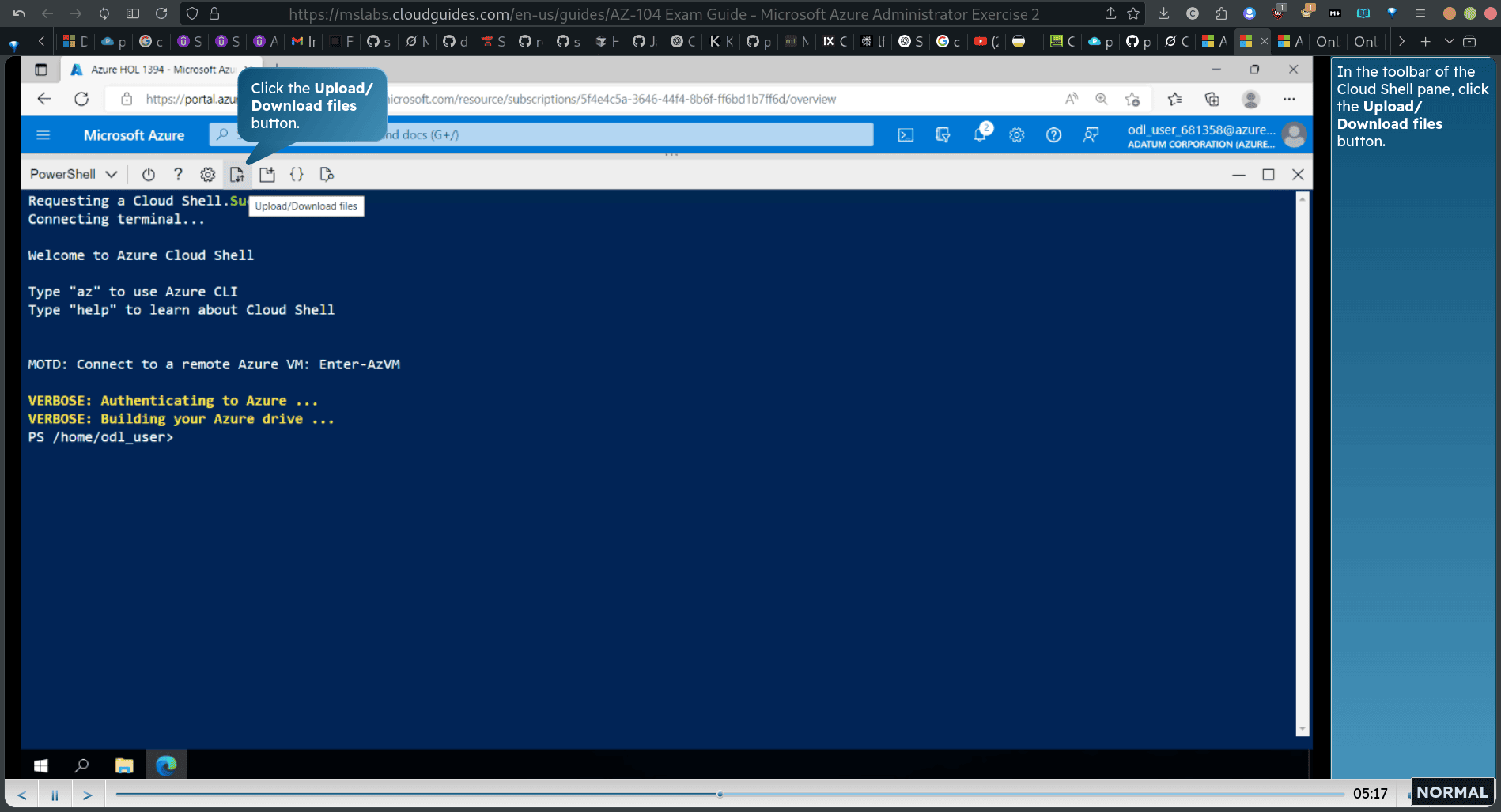
 click the storage blog then
click the storage blog then
upload the json file in the home directory
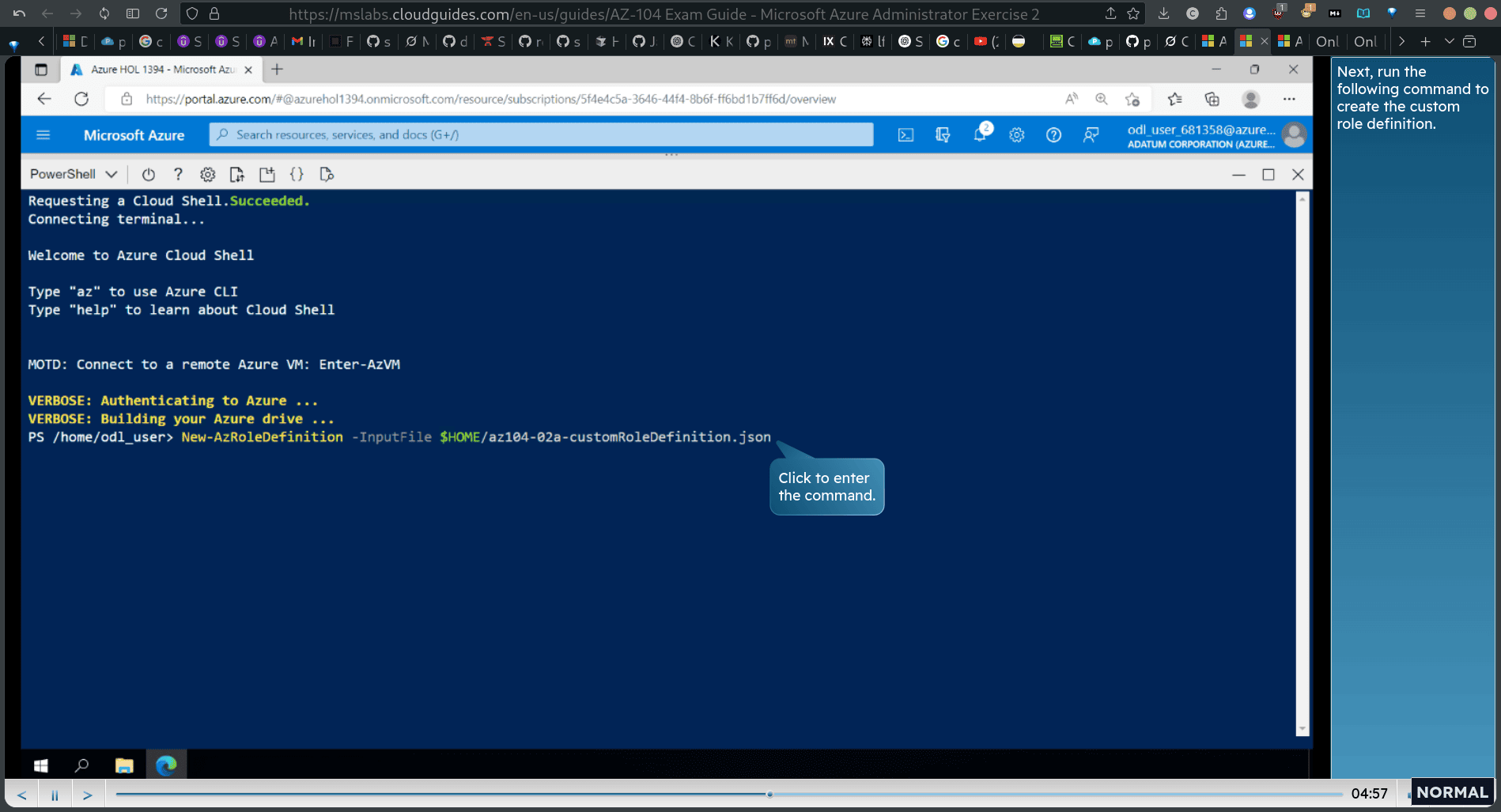
New-AzRoleDefinition -InputFile $HOME/az104-82a-customRoleDefinition.json
Task 3: Assign RBAC roles
copy a new created user , User principal name again
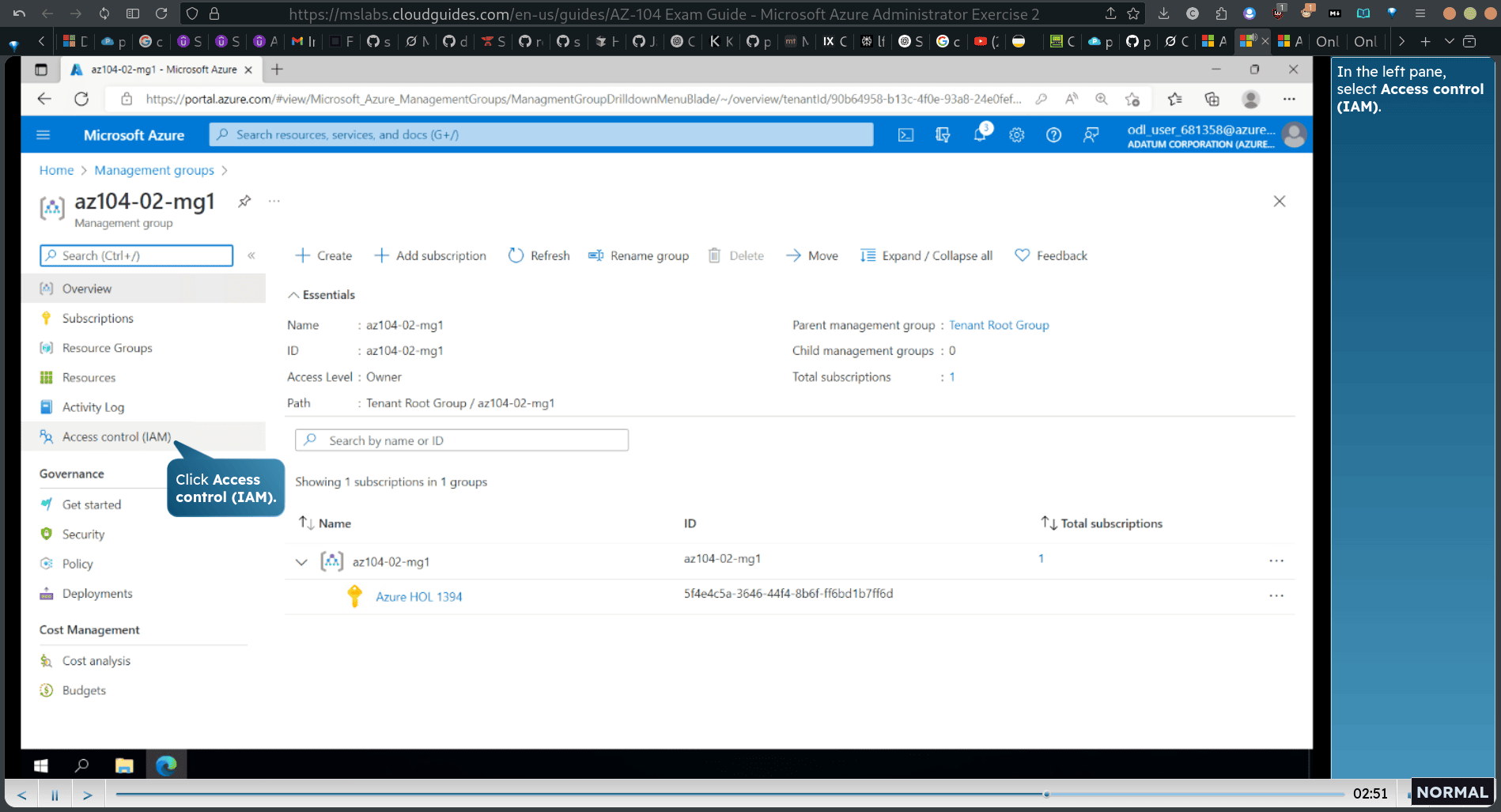
- access control IAM
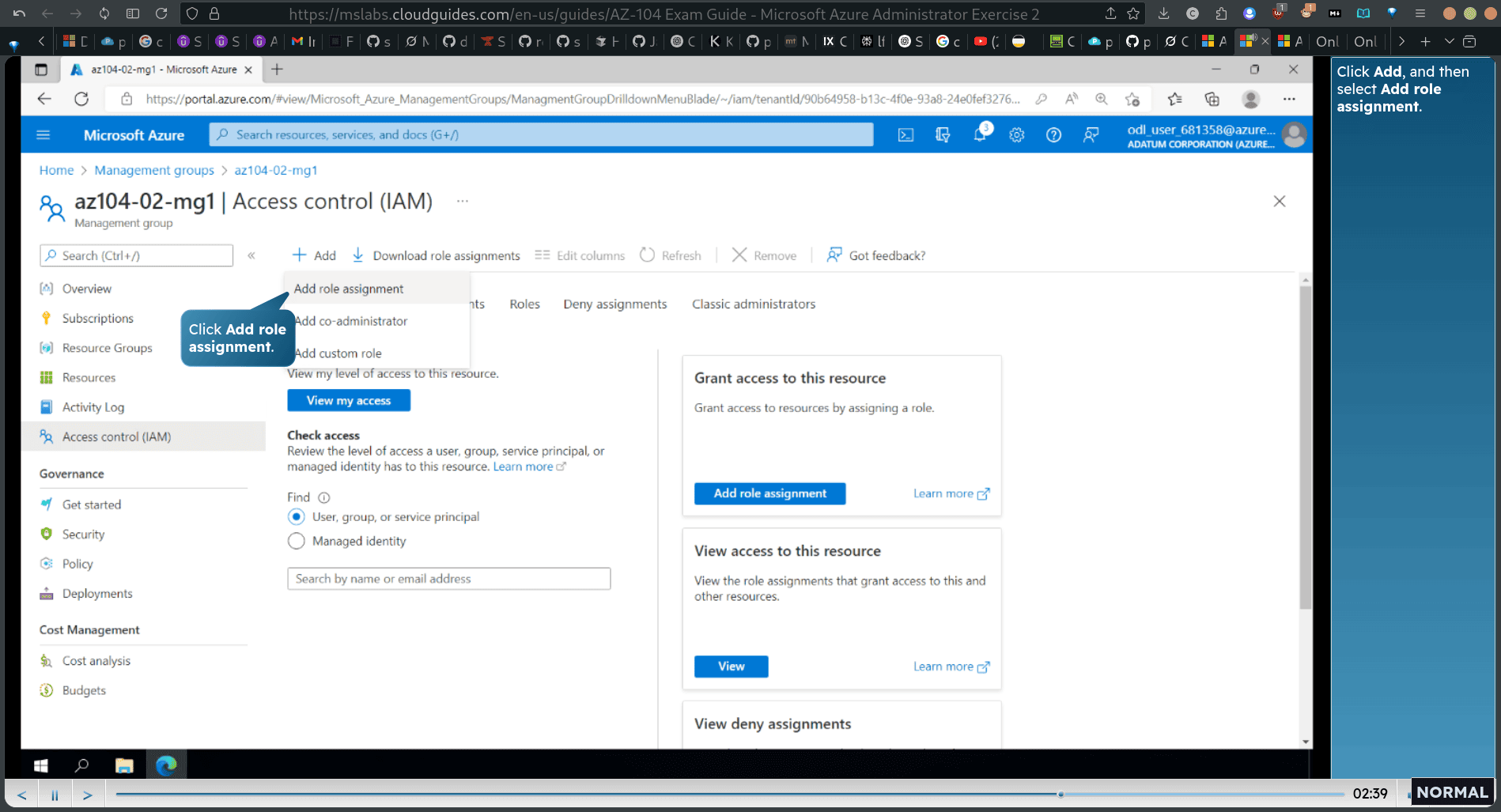 add role assignment
add role assignment
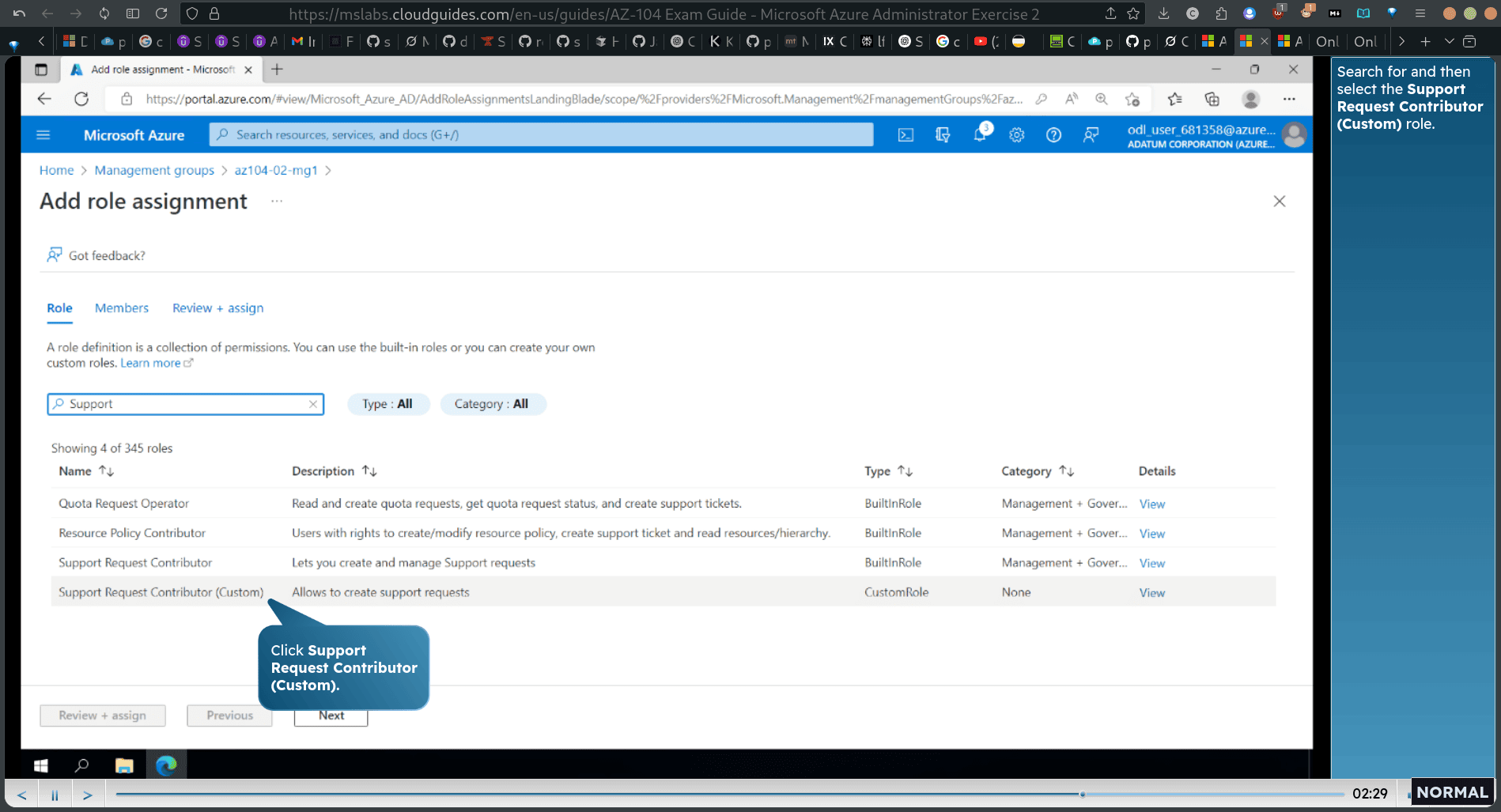
adding member (new created user)
- login your new created user check wheather he can access all resource (from search bar)
 help + support
help + support
- Create a support request
- Service and subscription limits (quotas) type issue
3. Manage governance via Azure Policy >
User → property → edit → setting
created user
click user → assigned role
 user admin role
user admin role
login in that new ac
 view AD
view AD
click and scroll and click user settings
 notice don’t have any permission
notice don’t have any permission
scroll up click user
create new user
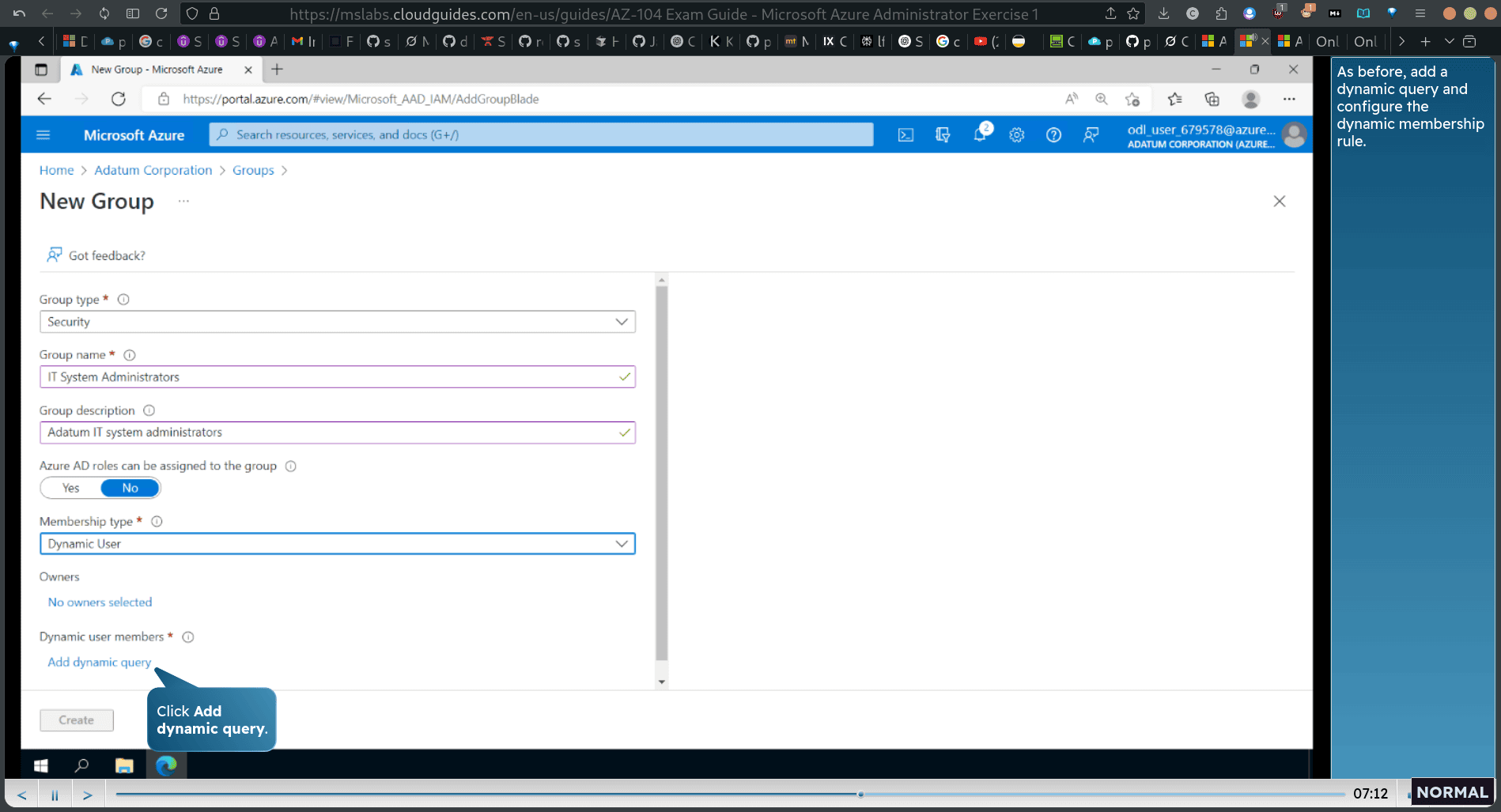
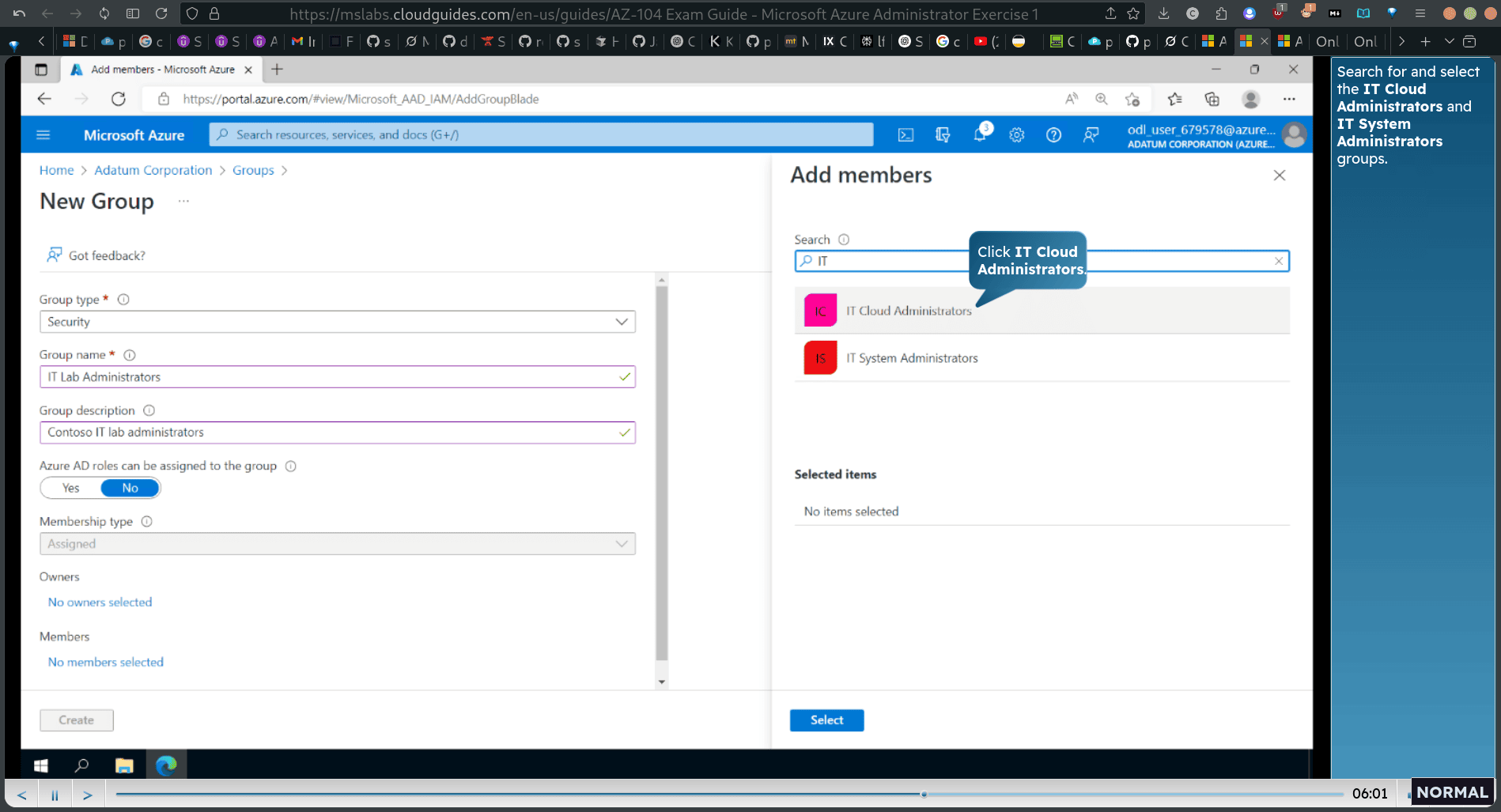
Task 2: Create Azure AD groups with assigned and dynamic membership
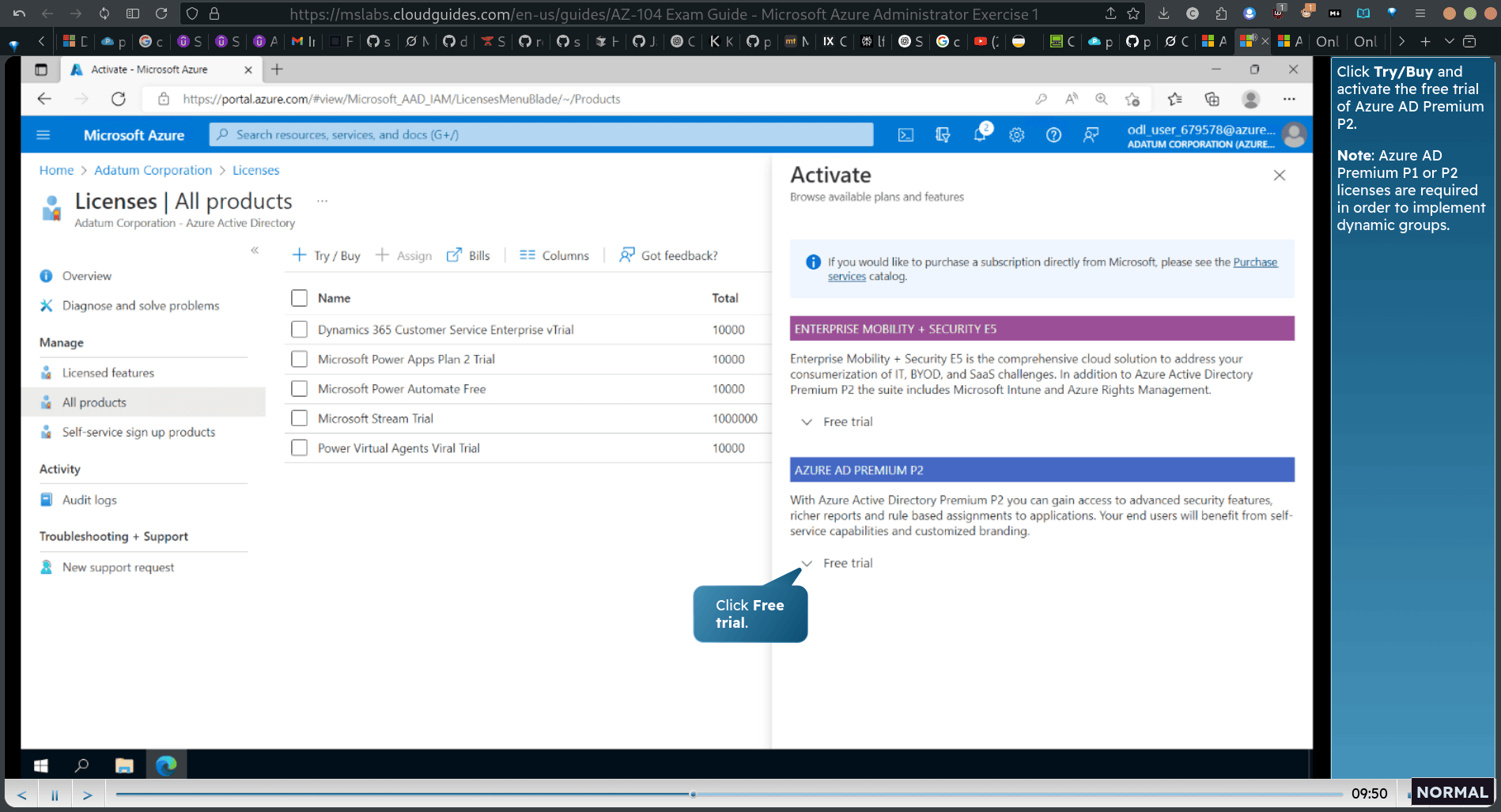
click ad company
click licnese
 select all product
select all product
click try/buy
click new item and assigne with new ac
go back azure AD → Group
created new three group
-
it cloud admin dynamic rule ⇒ job title equal cloud admin
-
securit group for it system admin
-
security group for lab admin
click security(all three are inside) , click cloud admin
click members verify that cloud admin is in the group
Task 3: Create an Azure AD tenant
back to adatumn active directory → click manage tenants (first page)
 overview
overview
 click the link lab (new tenant)
click the link lab (new tenant)
- god damn it is the same exercise i did before , what the foo (i click the wrong link), no wonder why it is the same
3. Manage governance via Azure Policy ( real one)
Task 1: Create and assign tags via the Azure portal
 click the ac
click the ac
click the tag in the left
new role → infra
go back storage ac link (from tab bar)
 new tag did’nt in the frontend though
new tag did’nt in the frontend though
Task 2: Enforce tagging via an Azure policy
search policy → Definition
assign
- define the scope
review and created
go back to the resource group
- click created
new storage
Task 3: Apply tagging via an Azure policy
search policy → assignment
delete assignemn and confirm
click assign policy , → scope →
click policy defitinion → more
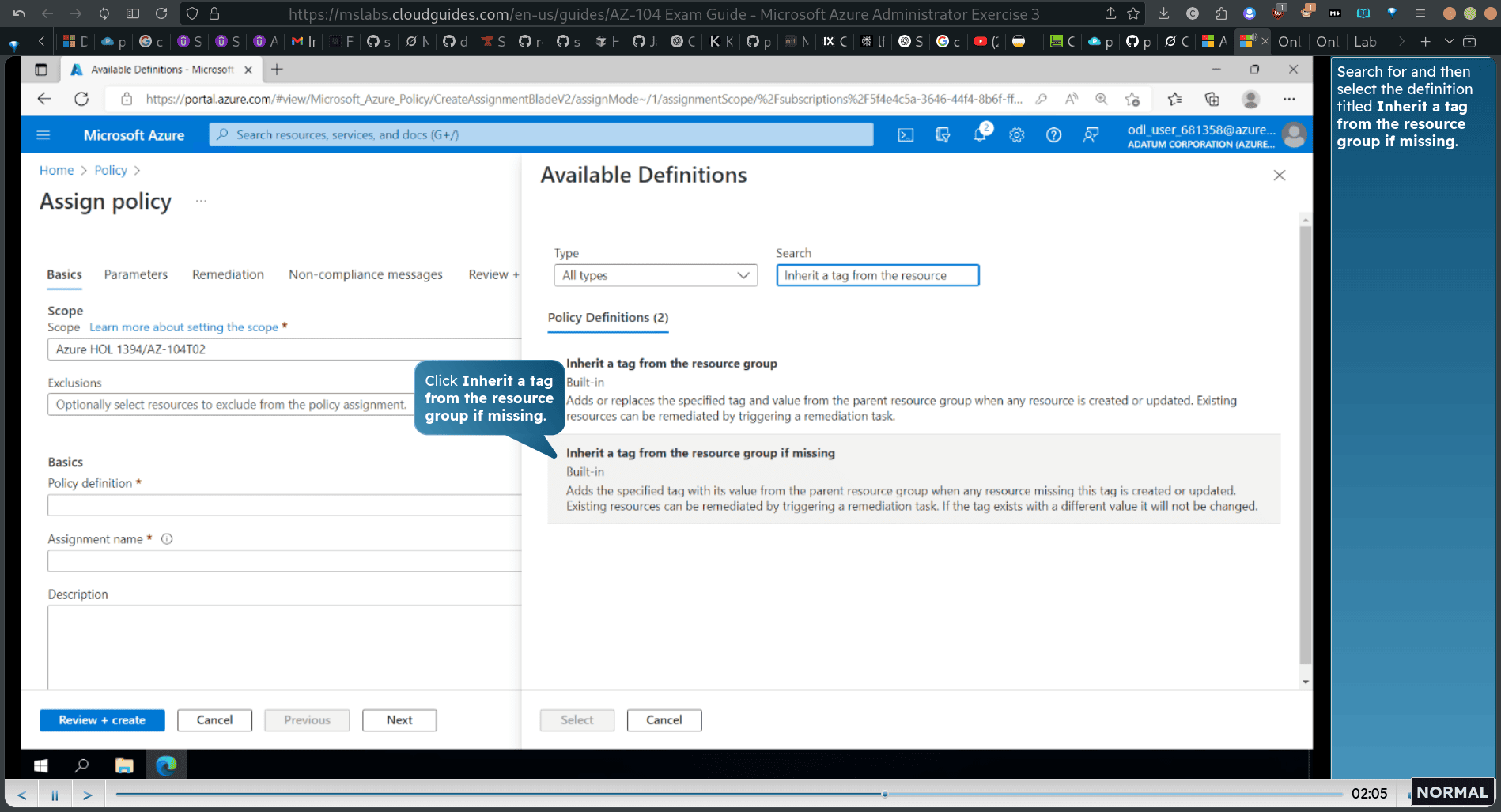
- Inherit a tag from the resource group if missing
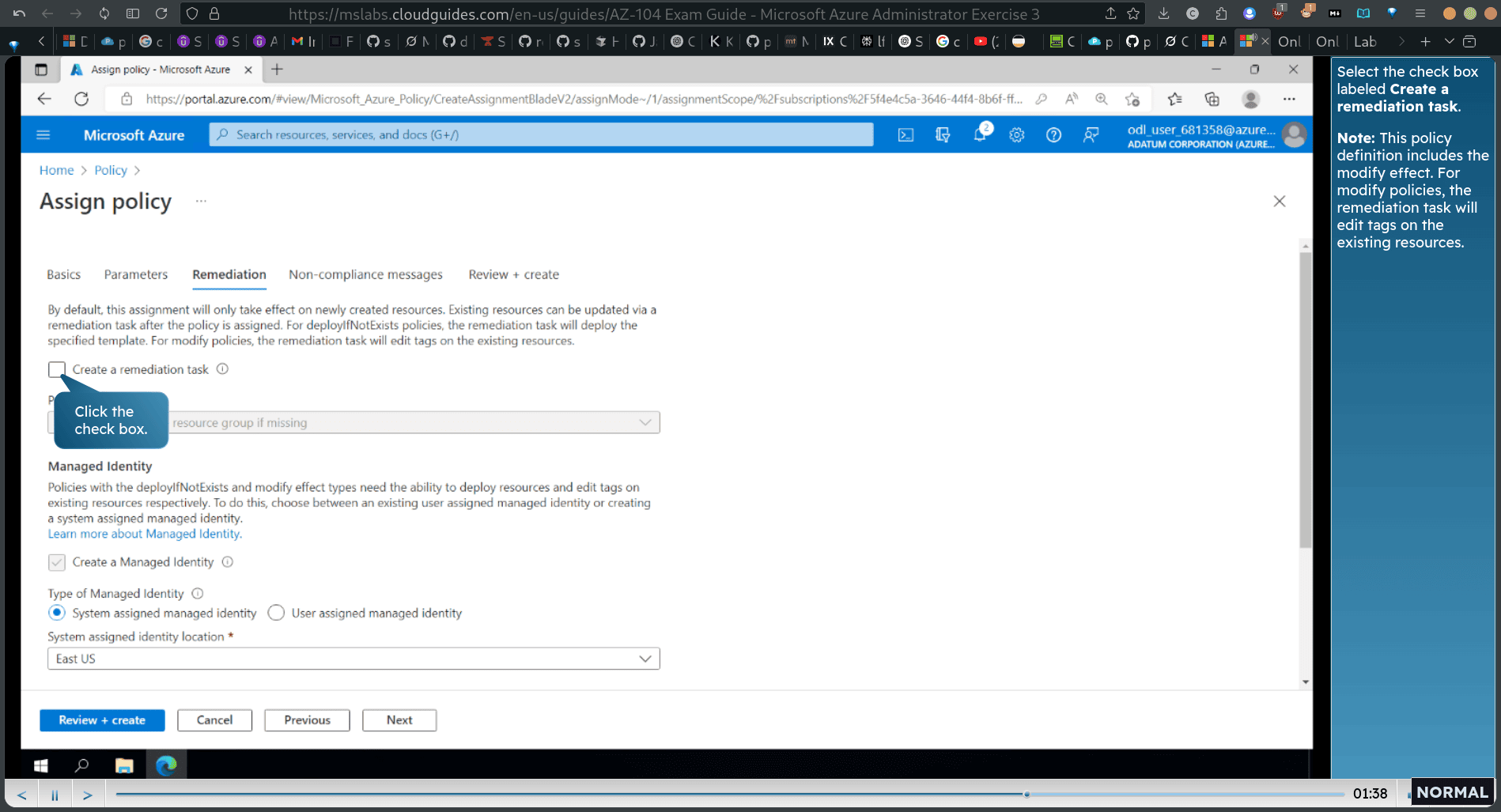
Select the check box labeled Create a remediation task.
create
now new created storage account will come up tag in the front end (go the resource→ overview : tag )
4. Manage Azure resources by using the Azure portal >
Task 1: Deploy resources to an existing resource group
search disk
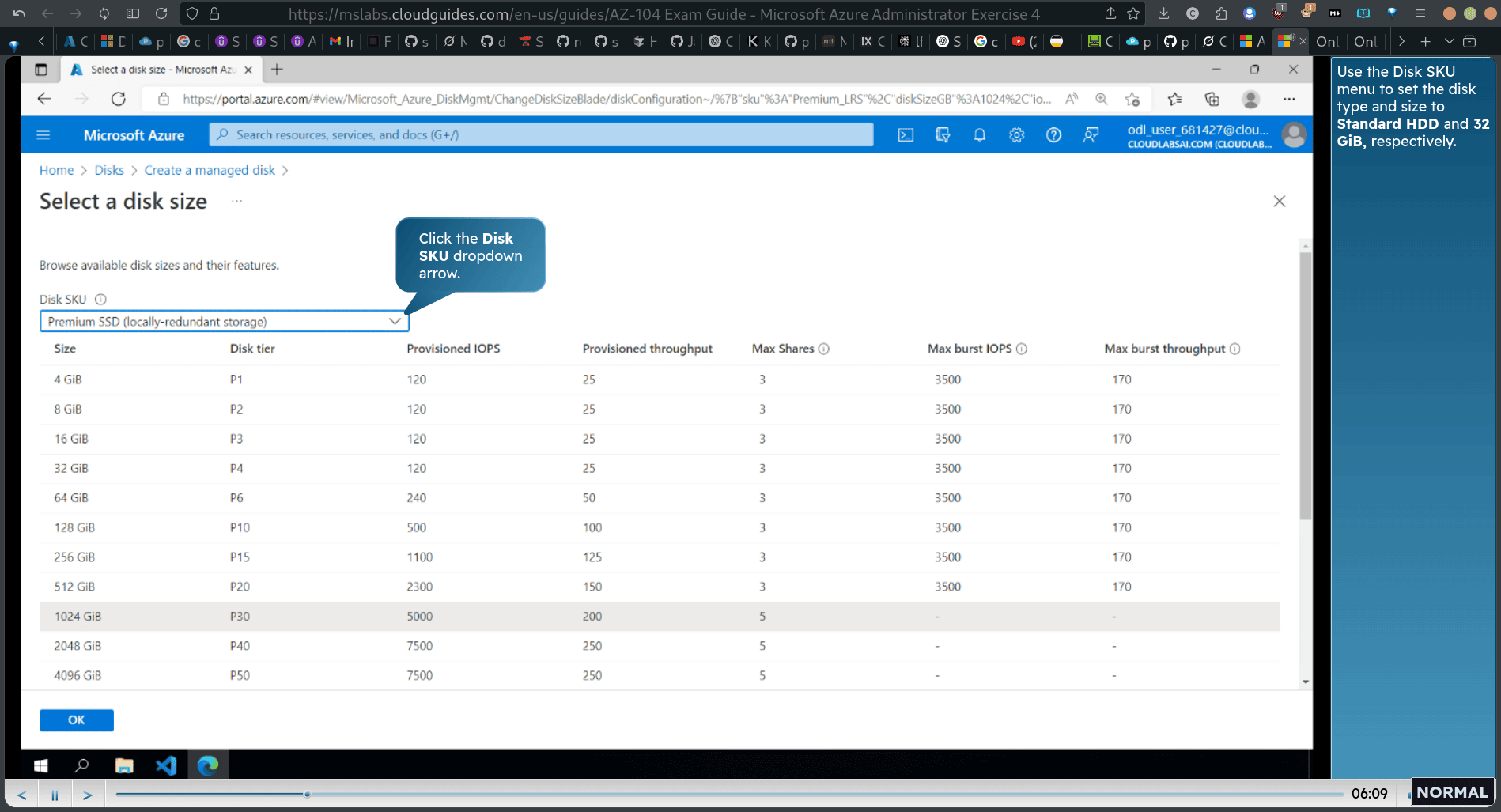 32 gb → create
32 gb → create
Task 2: Move a resource between resource groups
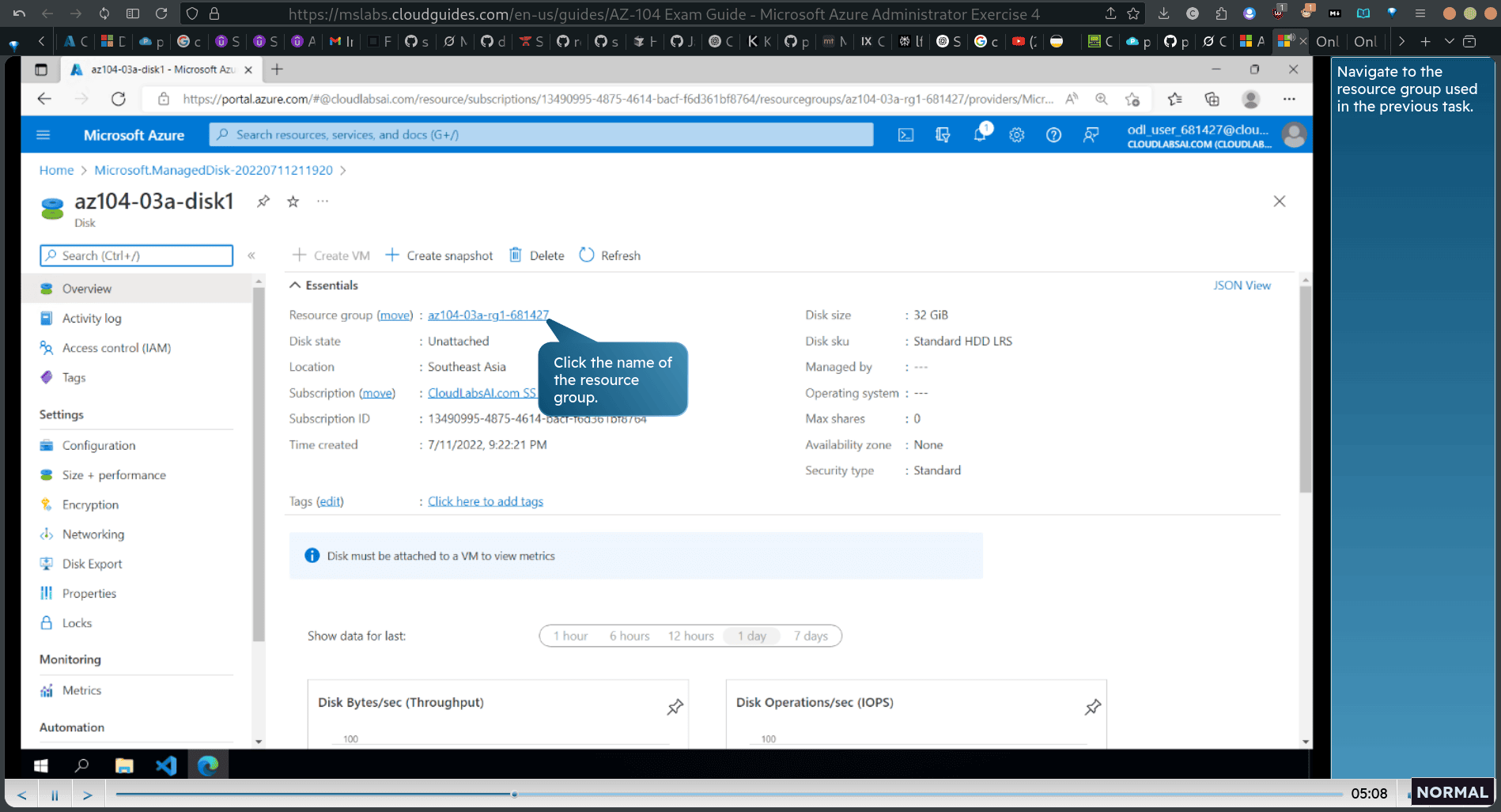
select new disk → move → move to other resource groups
search resource group and verify
Task 3: Implement and test a resource lock
 delete lock from a new disk item
delete lock from a new disk item
warning → delet fail
5. Manage Azure resources by using Azure Resource Manager templates >
Task 1: Review an ARM template for deployment of an Azure managed disk
 deployment
deployment
 select one and → template
select one and → template
click input and look for the info
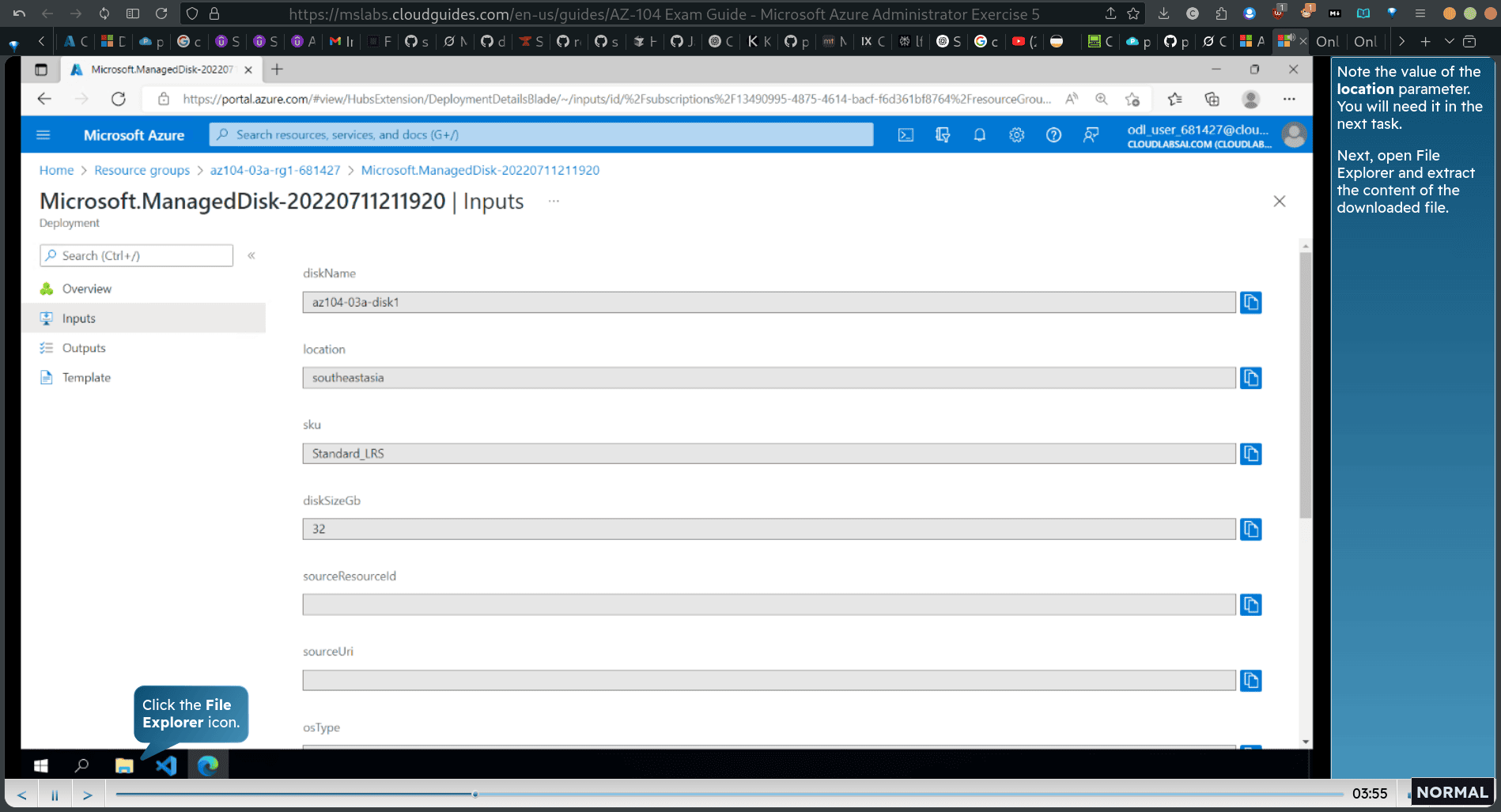
extract the downloaded file
Task 2: Create an Azure managed disk by using an ARM template
Search Deploy a custom template in portal
click build your won template
load file
upload the download and extracted template
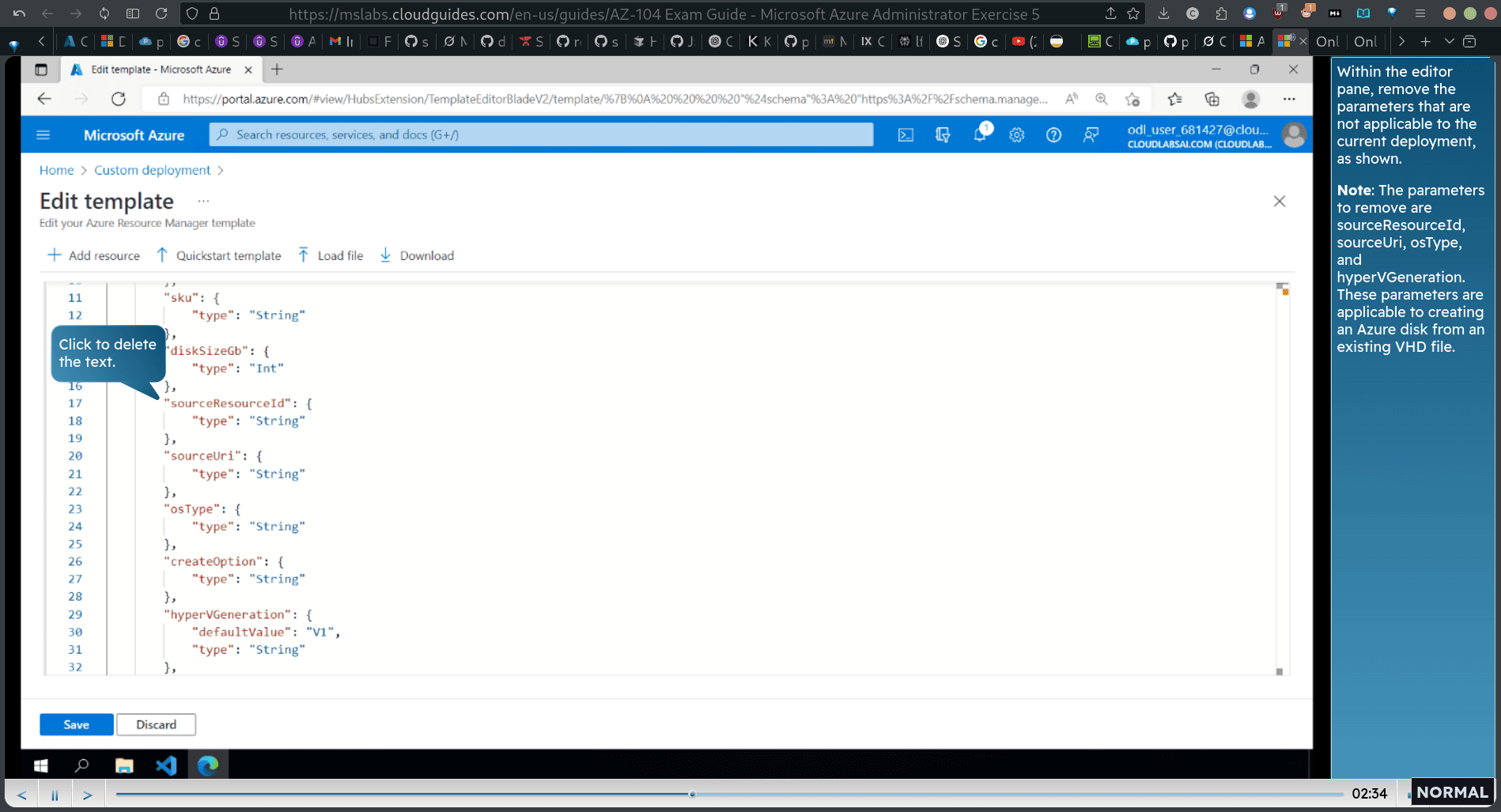
remove the unnessary item in json
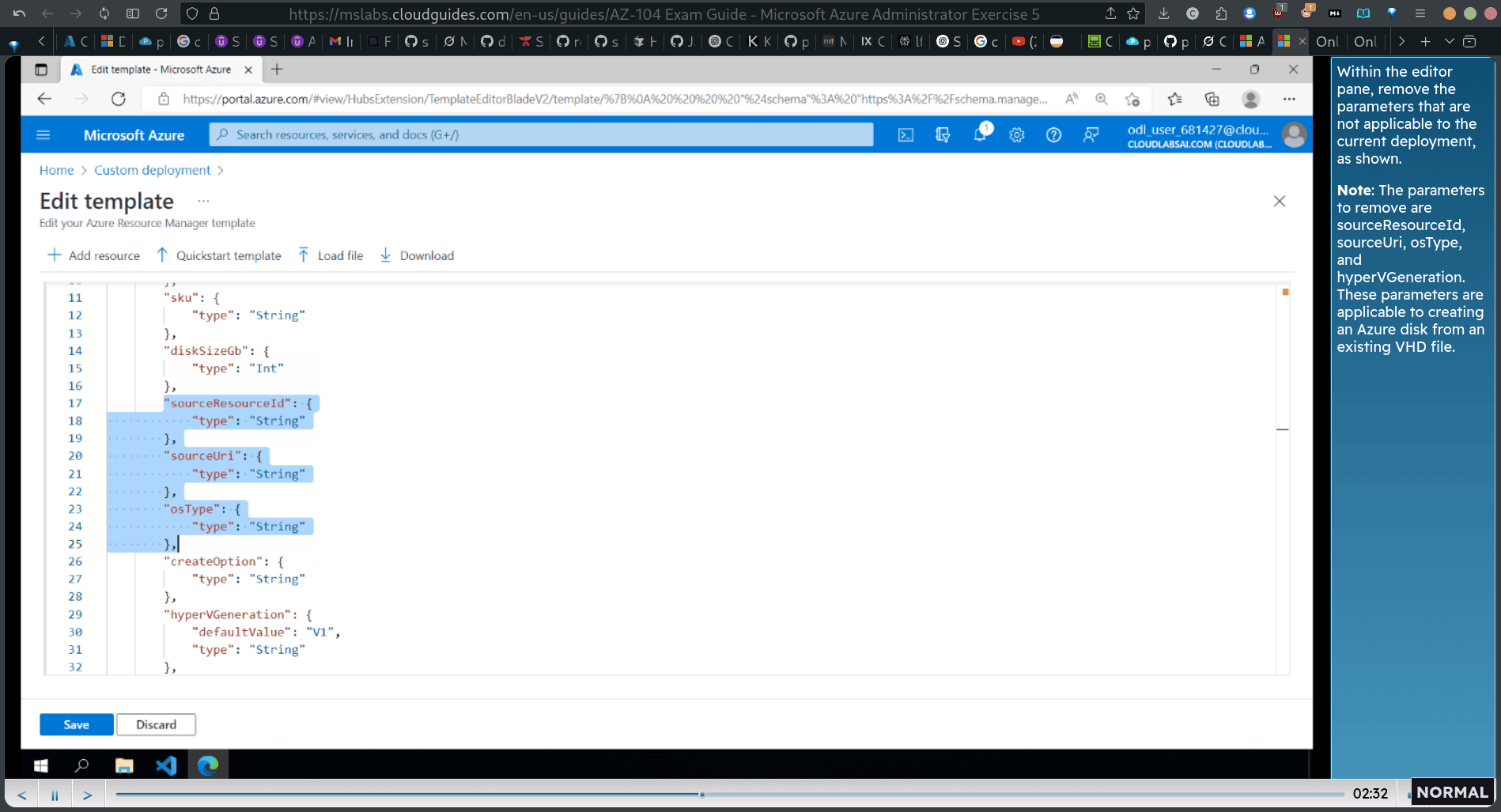
delete these three
and this one
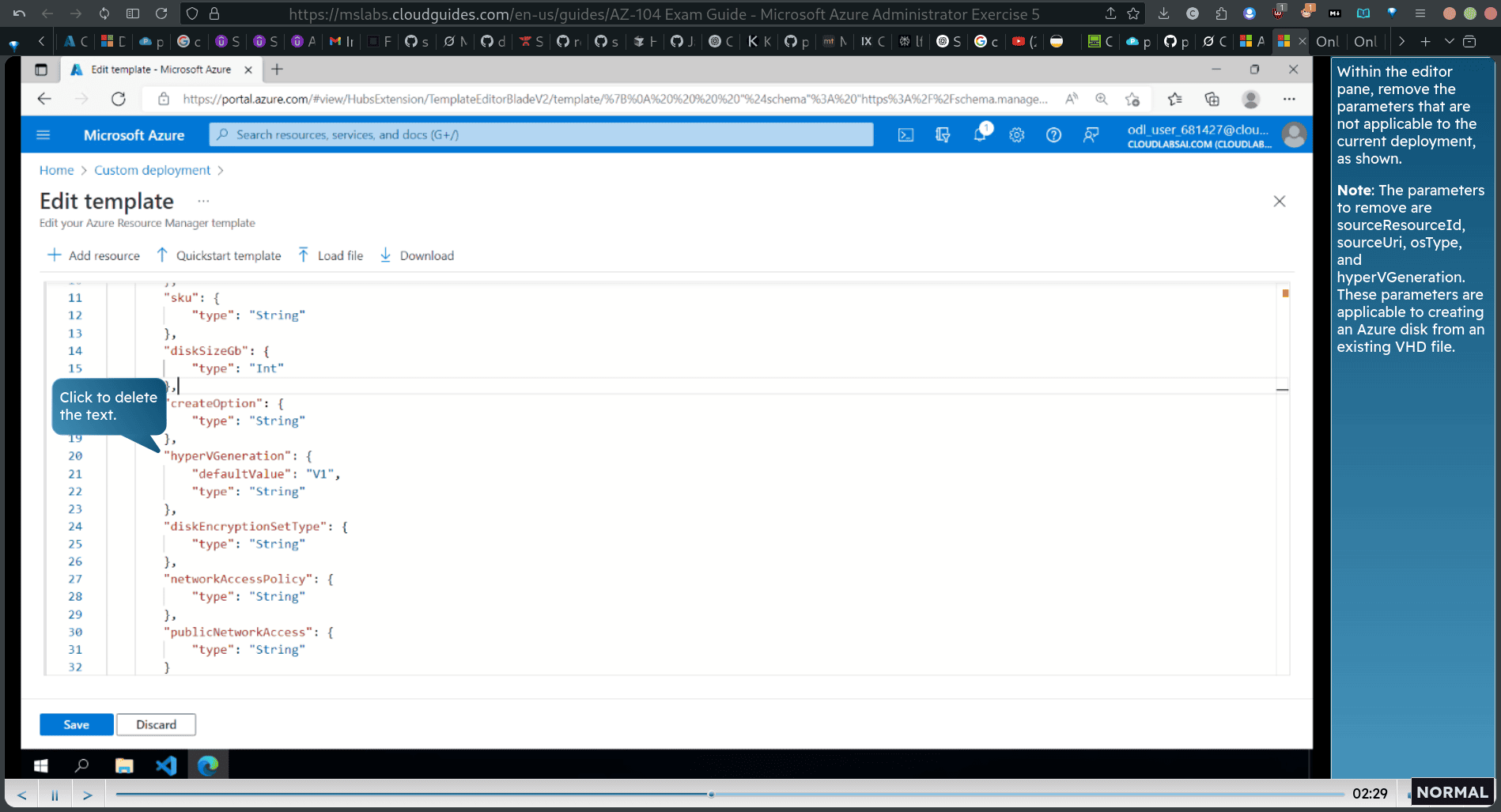
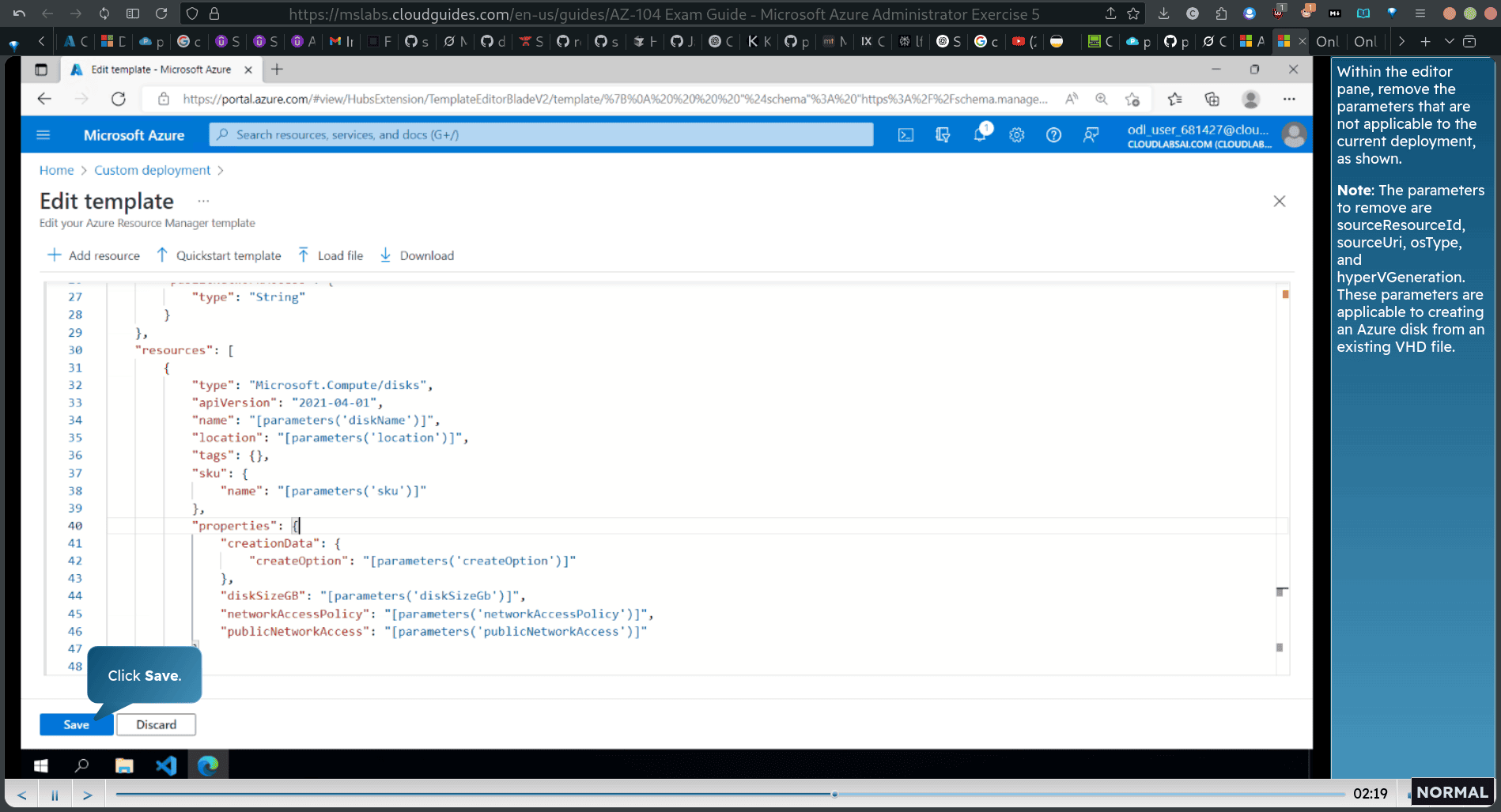
delete the os line as well
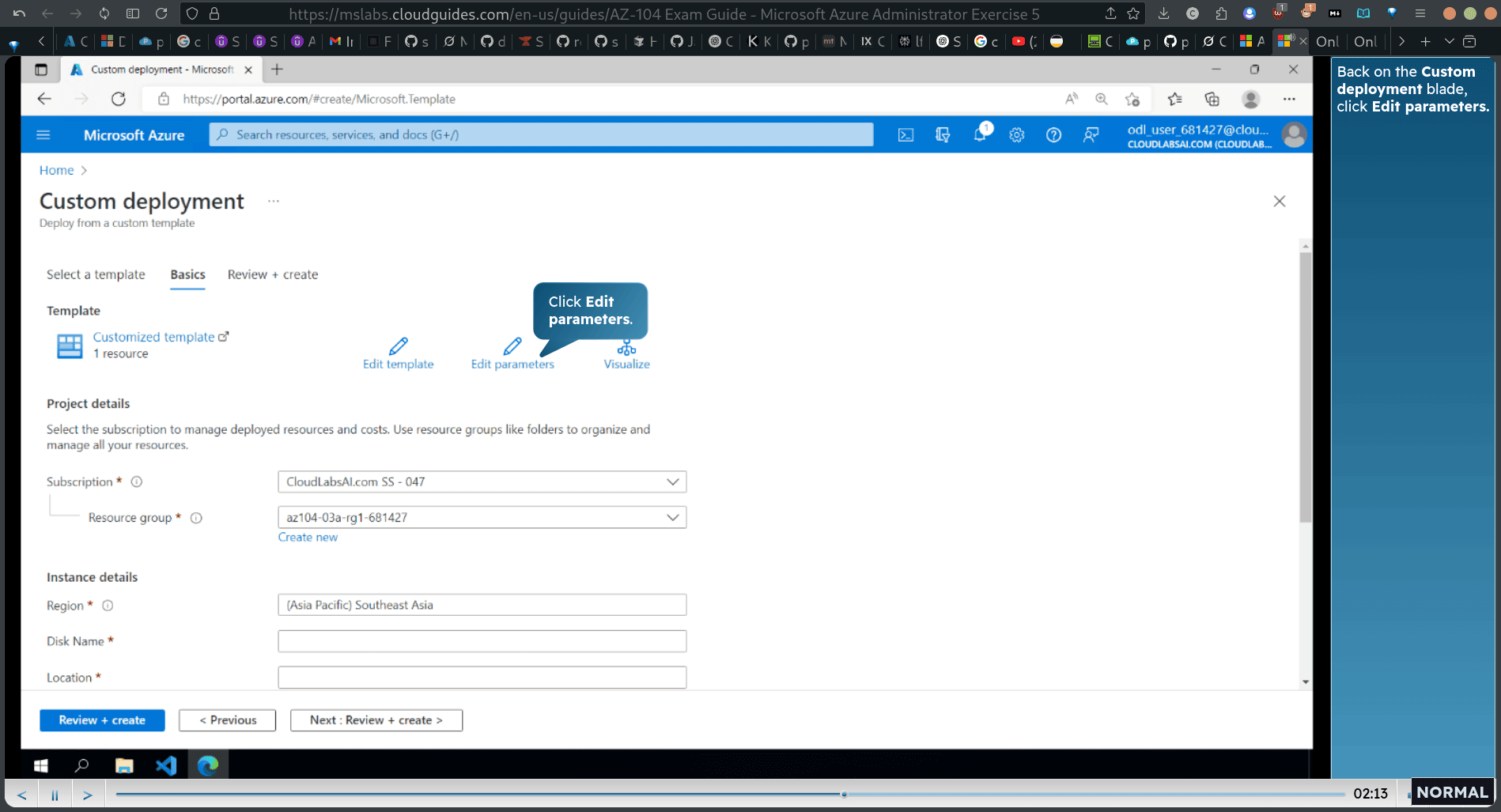 edit parameters
edit parameters
click load file and upload parameter from extrated file
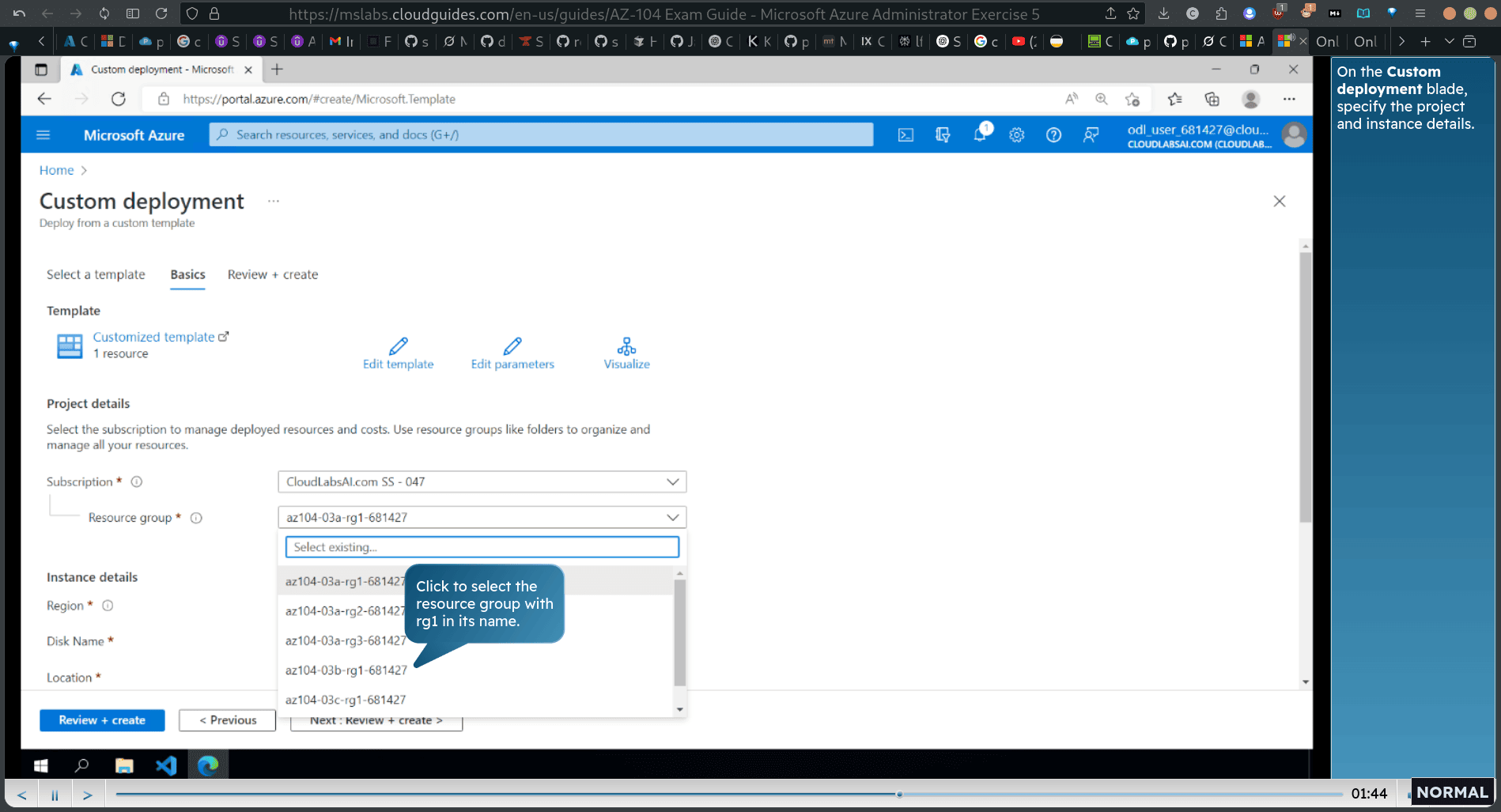
- change the resource group if necessary, like disk name
create
Task 3: Review the ARM template-based deployment of the managed disk
search resource group → deployment → select → inputs and templates
6. Manage Azure resources by using Azure PowerShell
Task 1: Start a PowerShell session in Azure Cloud Shell
cloud shell → powershell
Task 2: Create a resource group and an Azure managed disk by using Azure PowerShell
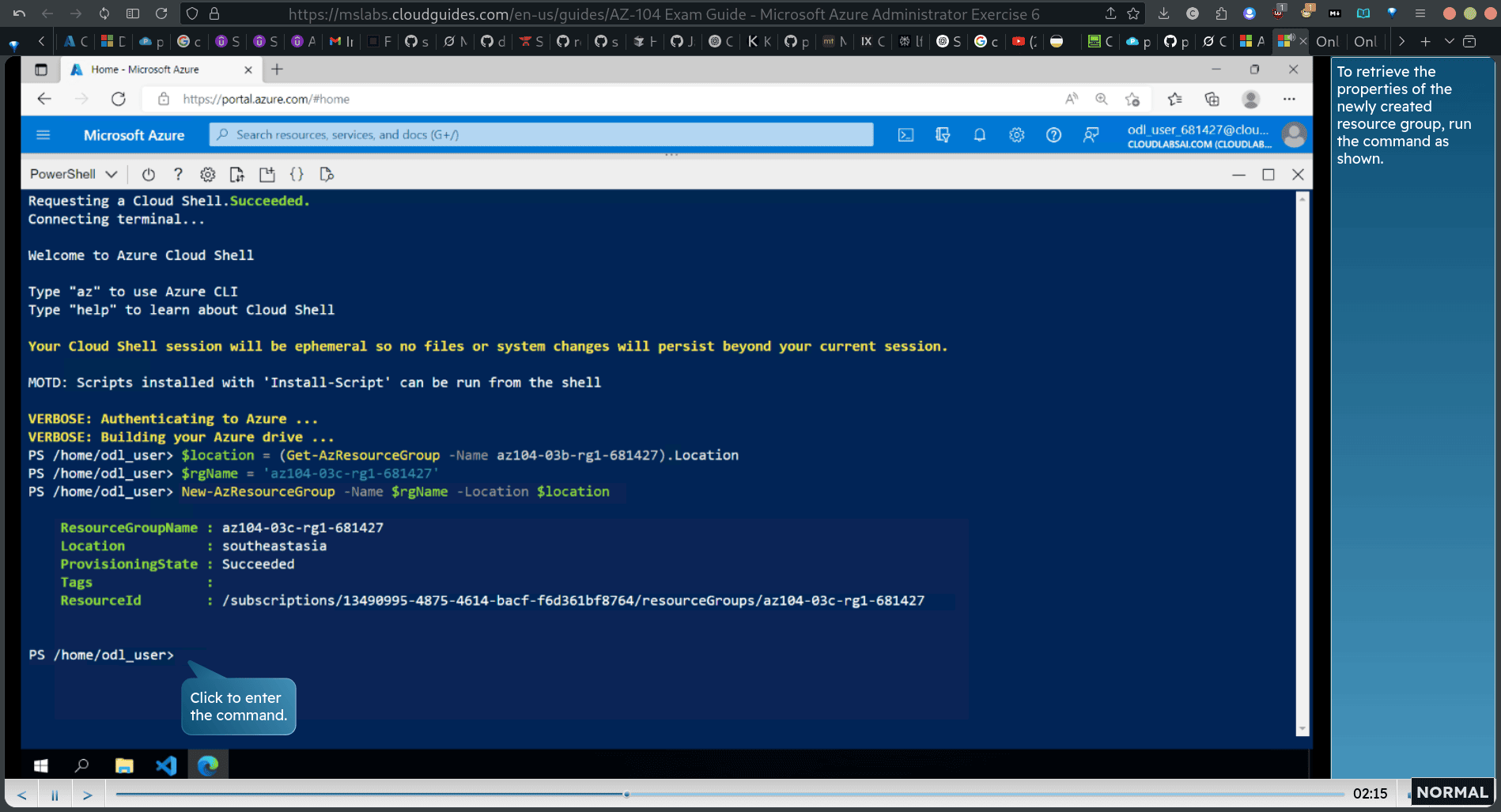
$location = (Get-AzResourceGroup -Name az104-03b-rgl-681427).Location
From the PowerShell session within Azure Cloud Shell, run the commands as shown to create a resource group in the same Azure region as the resource group you created in the previous lab.
New-AzResourceGroup -Name location
Get-AzResourceGroup -Name $rgName
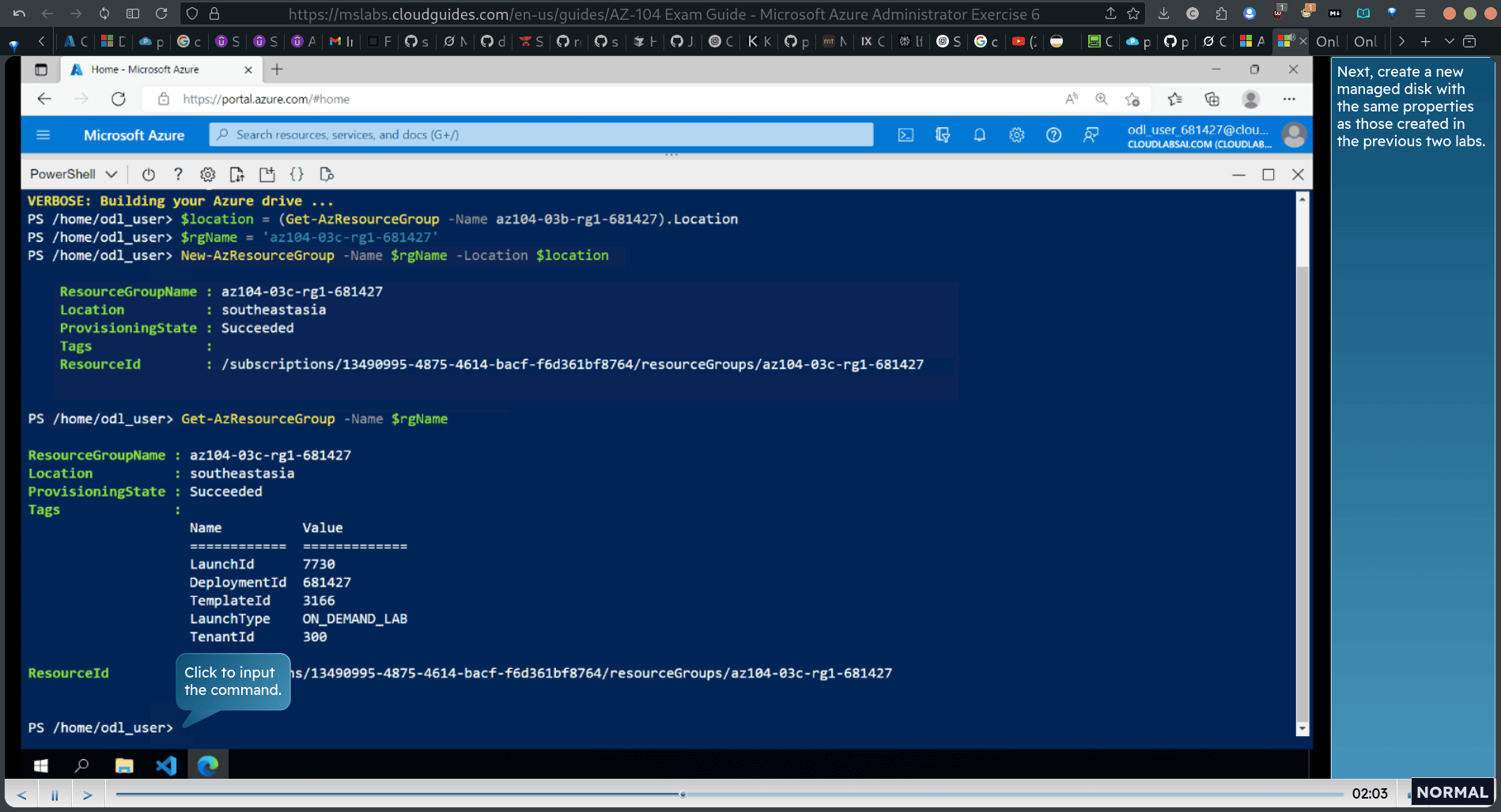
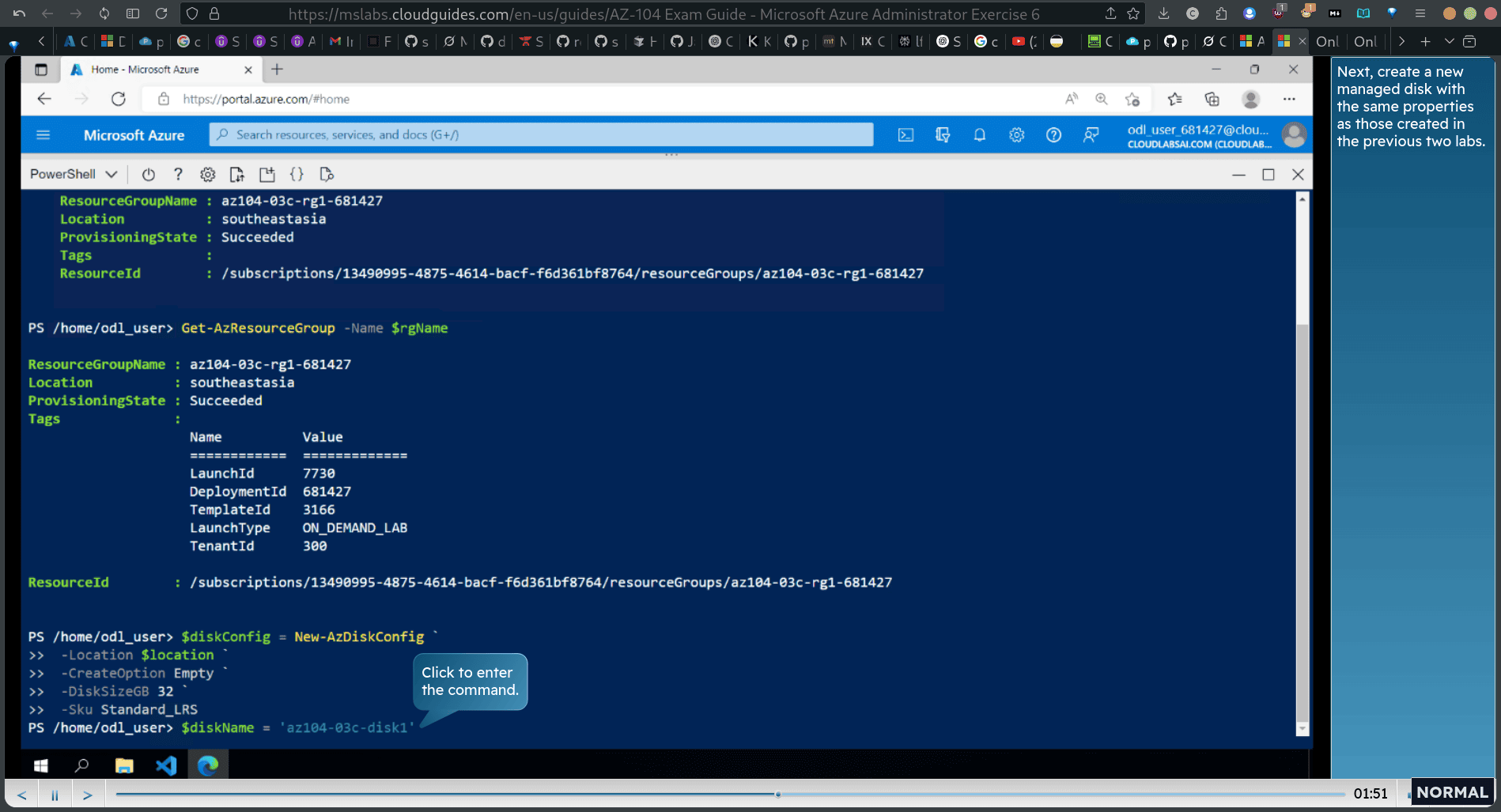
Next, create a new managed disk with the same properties as those created in the previous two labs.
$diskConfig = New-AzDiskConfig `
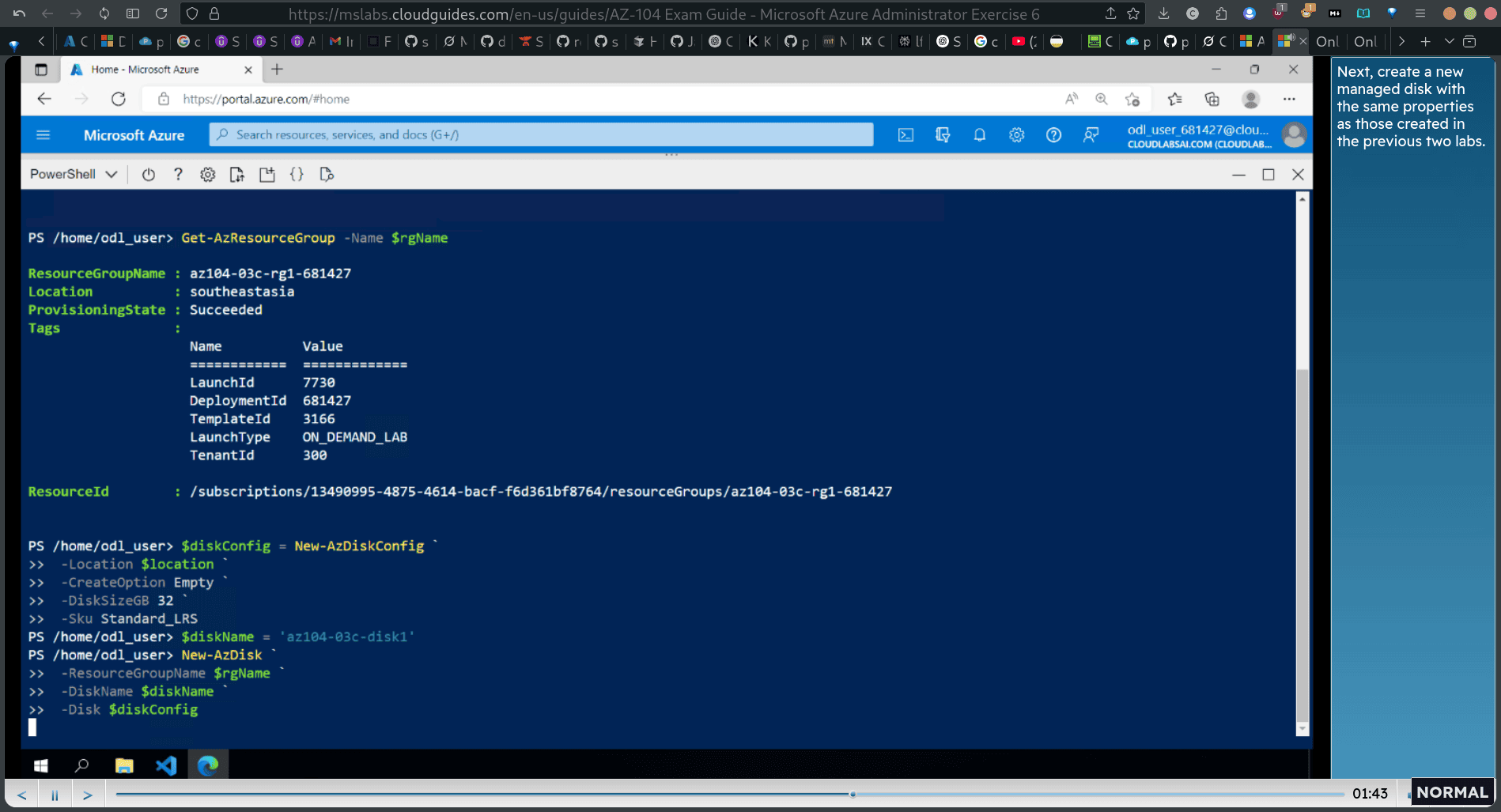
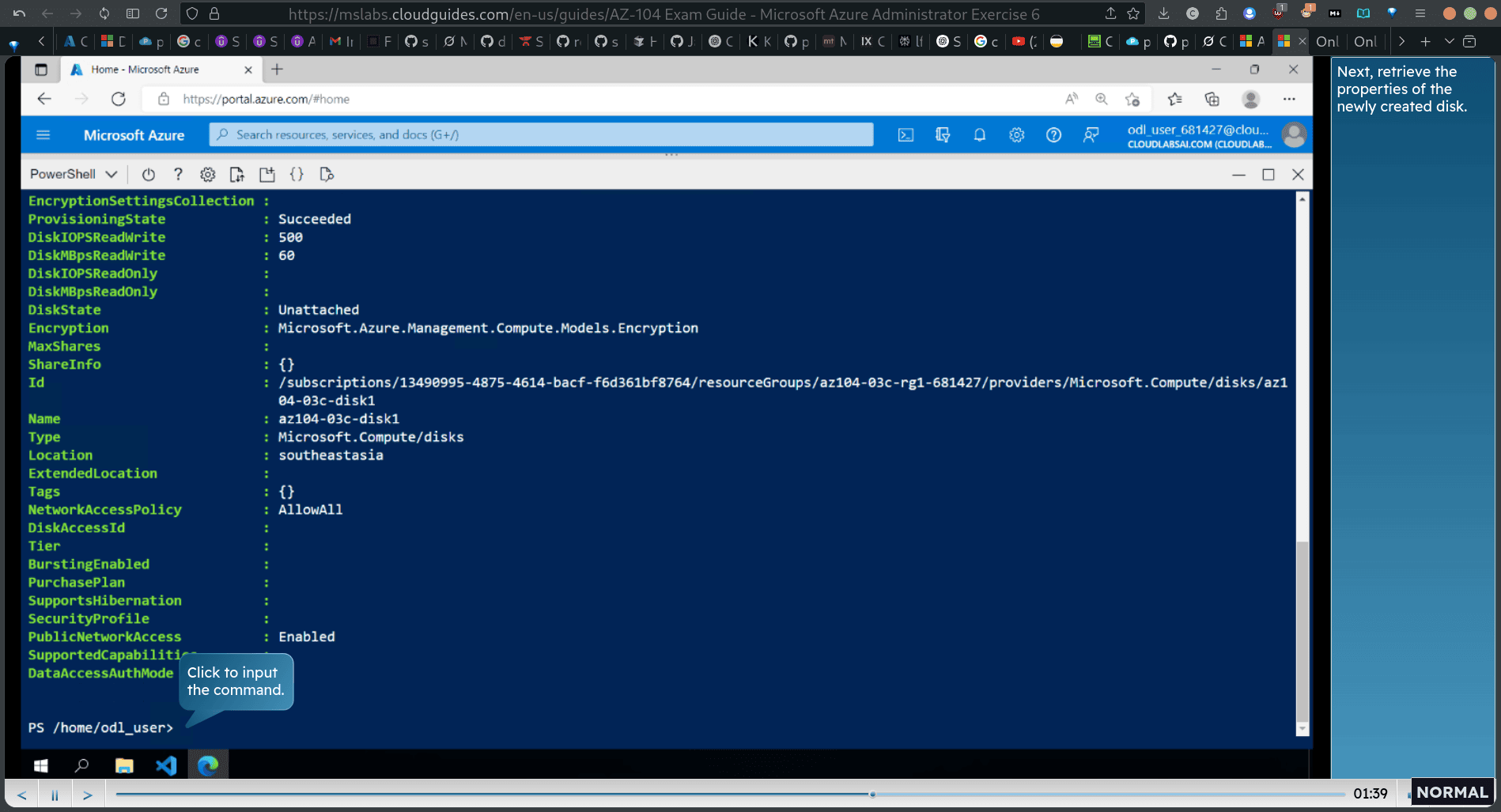 properitis
properitis
Get-AzDisk -ResourceGroupName diskName
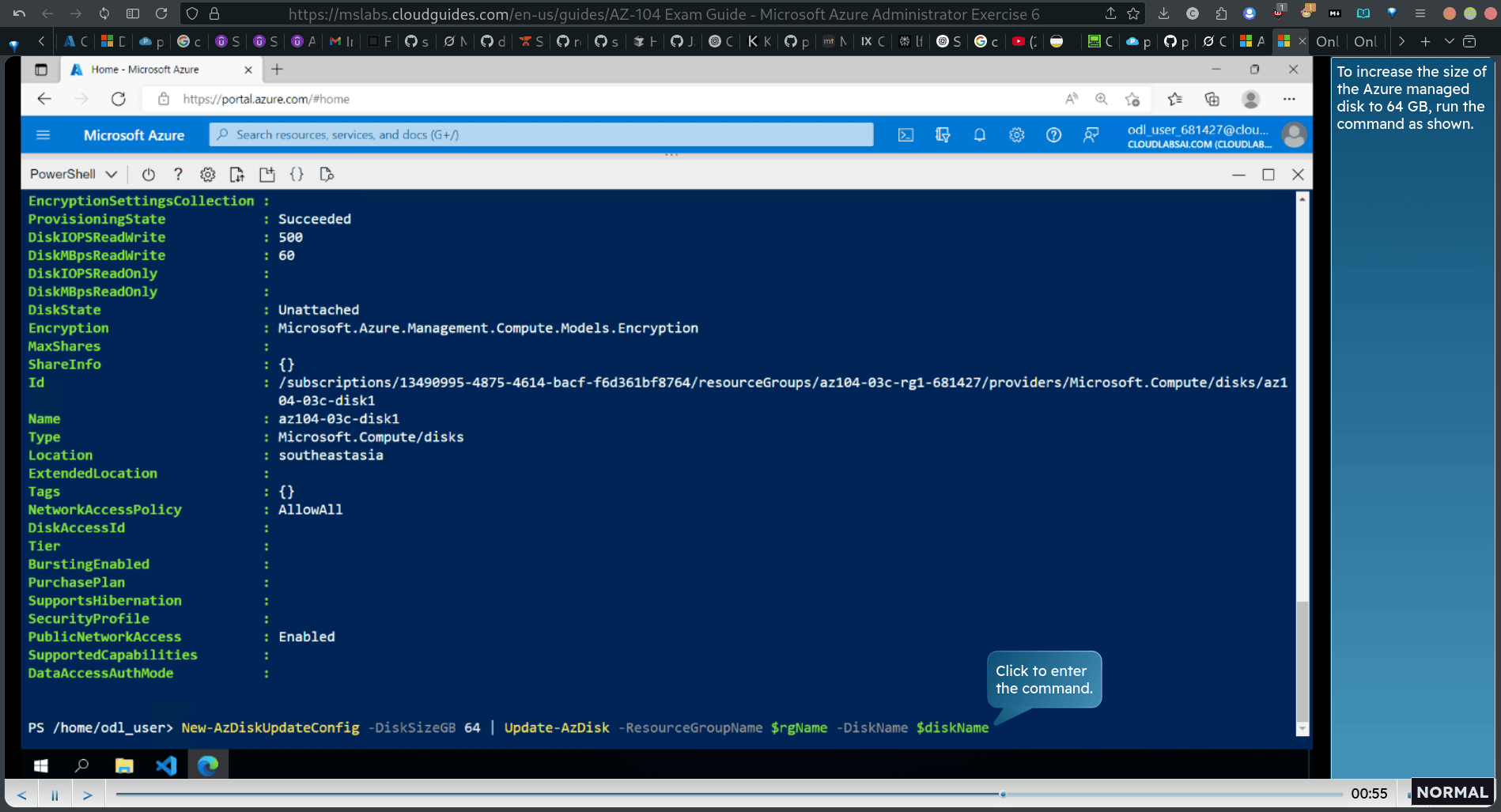
Task 3: Configure the managed disk by using Azure PowerShell
New-AzDiskUpdateConfig -DisksizeGB 64 | Update-AzDisk -ResourceGroupName diskName
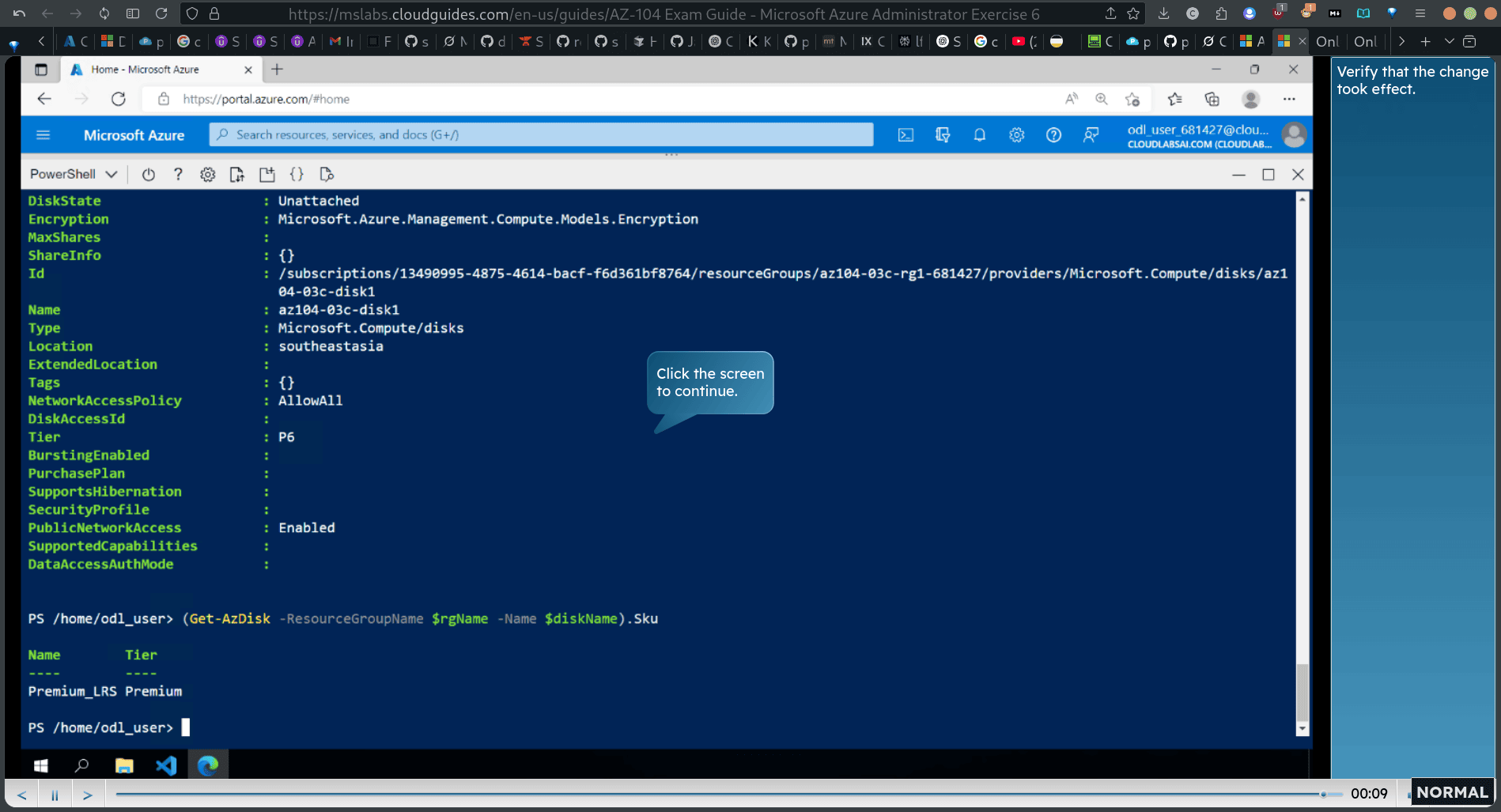
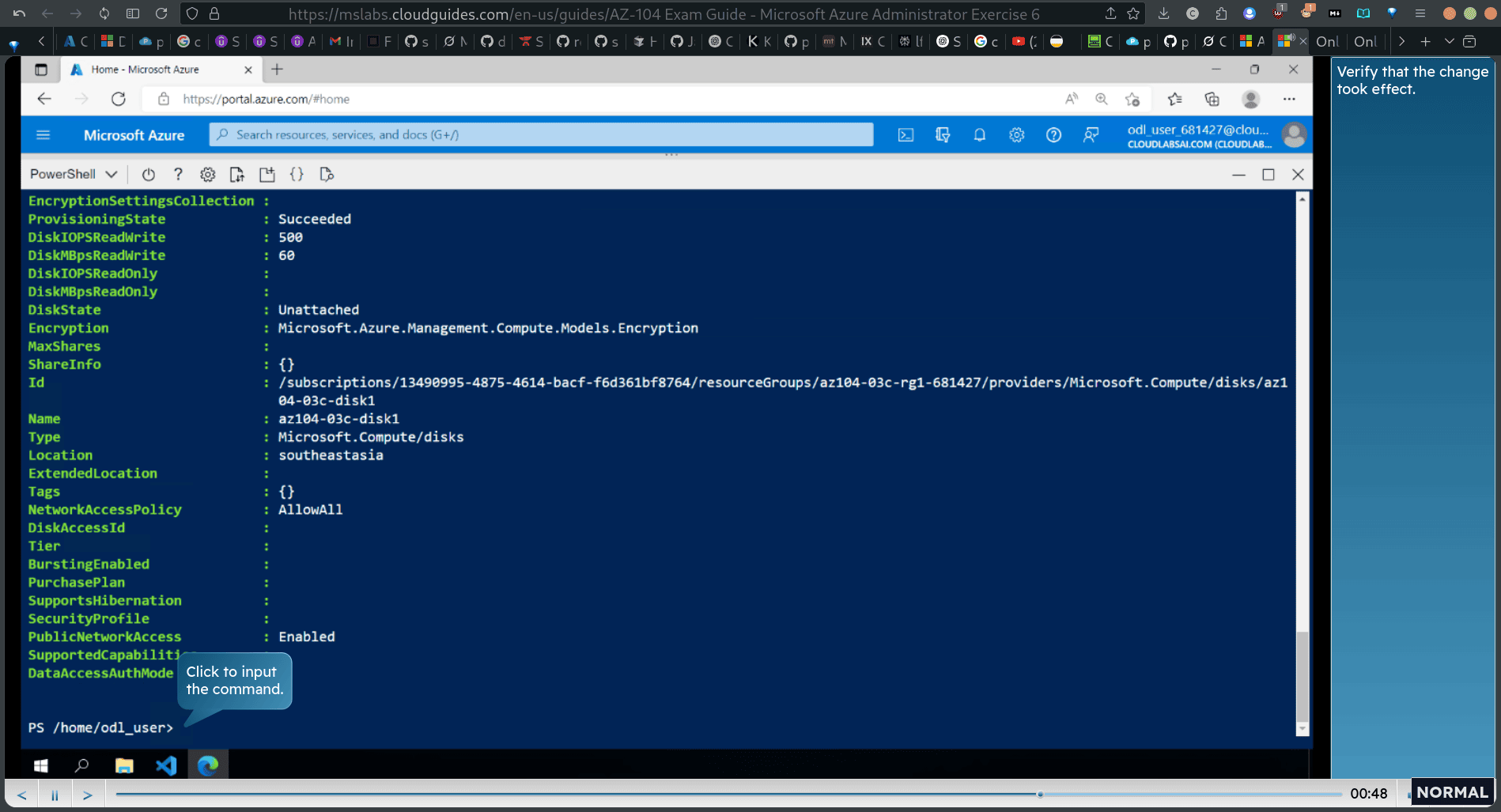 verify the change
verify the change
Get-AzDisk -ResourceGroupName diskName
(Get-AzDisk -ResourceGroupName diskName).Skul verify the current sku
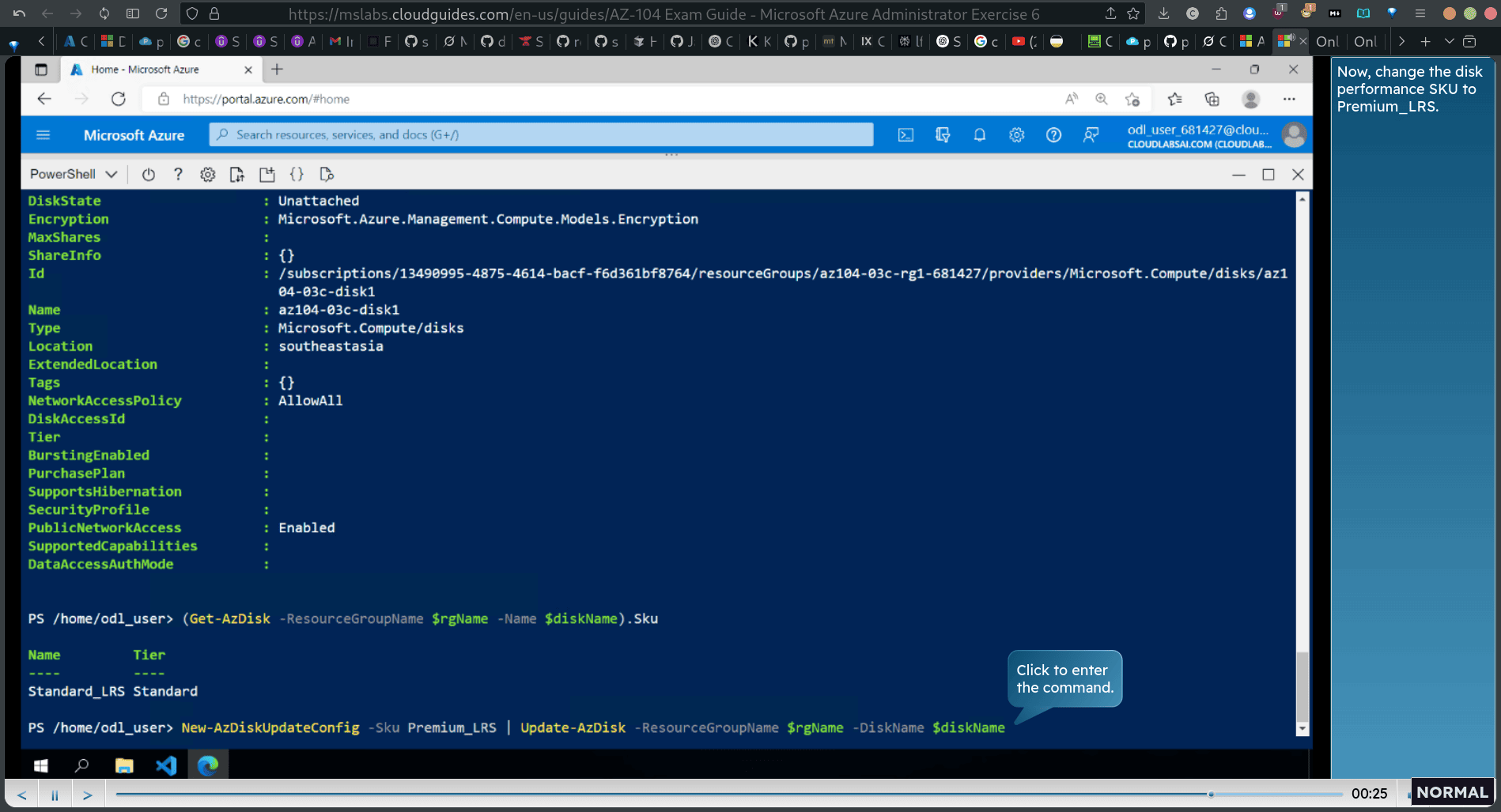
New-AzDiskUpdateConfig -Sku Premium_LRS | Update-AzDisk -ResourceGroupName diskName
chanage the premium verify the change
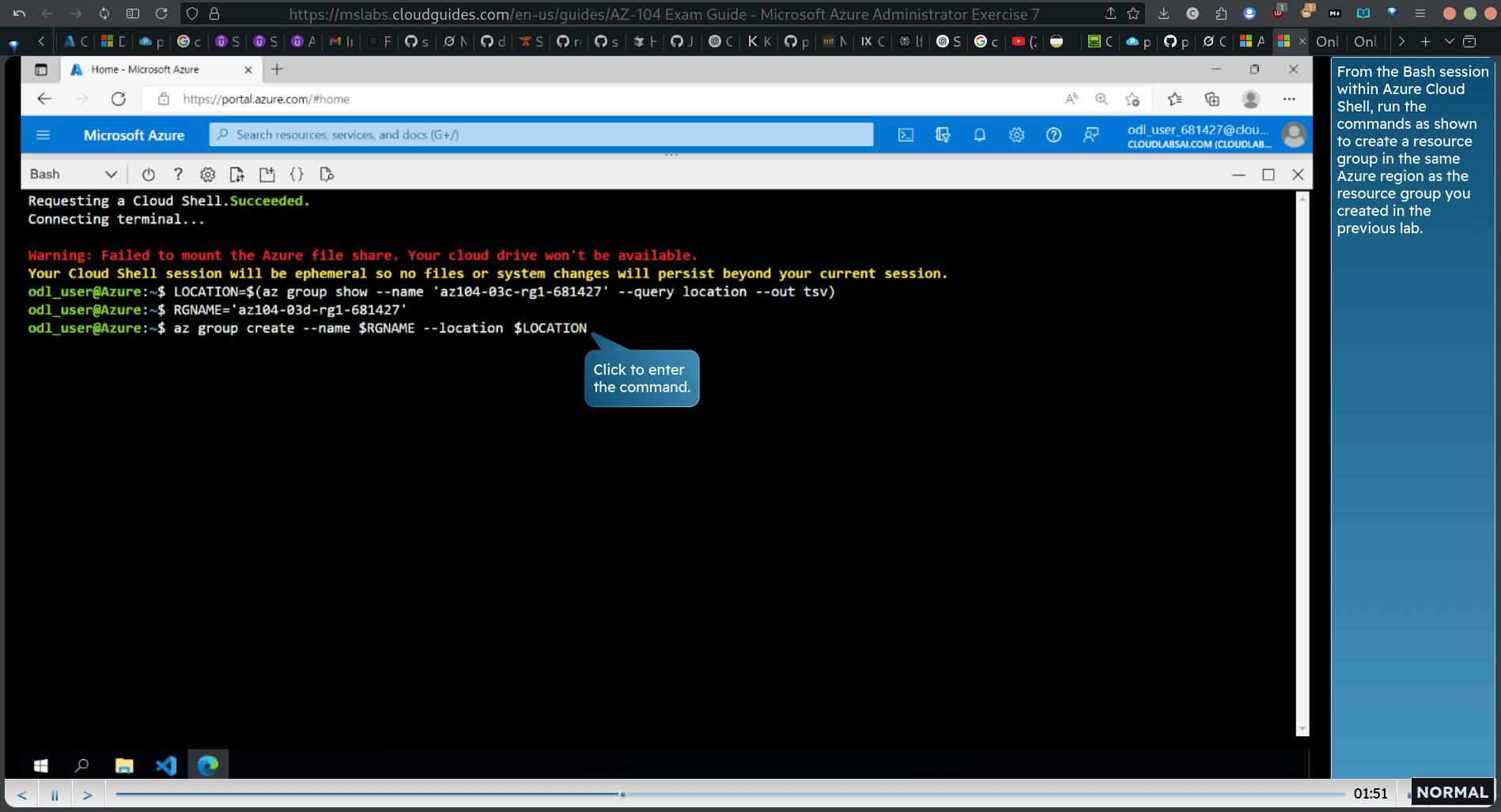
7. Manage Azure resources by using the Azure CLI > bash
Task 1: Start a Bash session in Azure Cloud Shell
cloud → bash
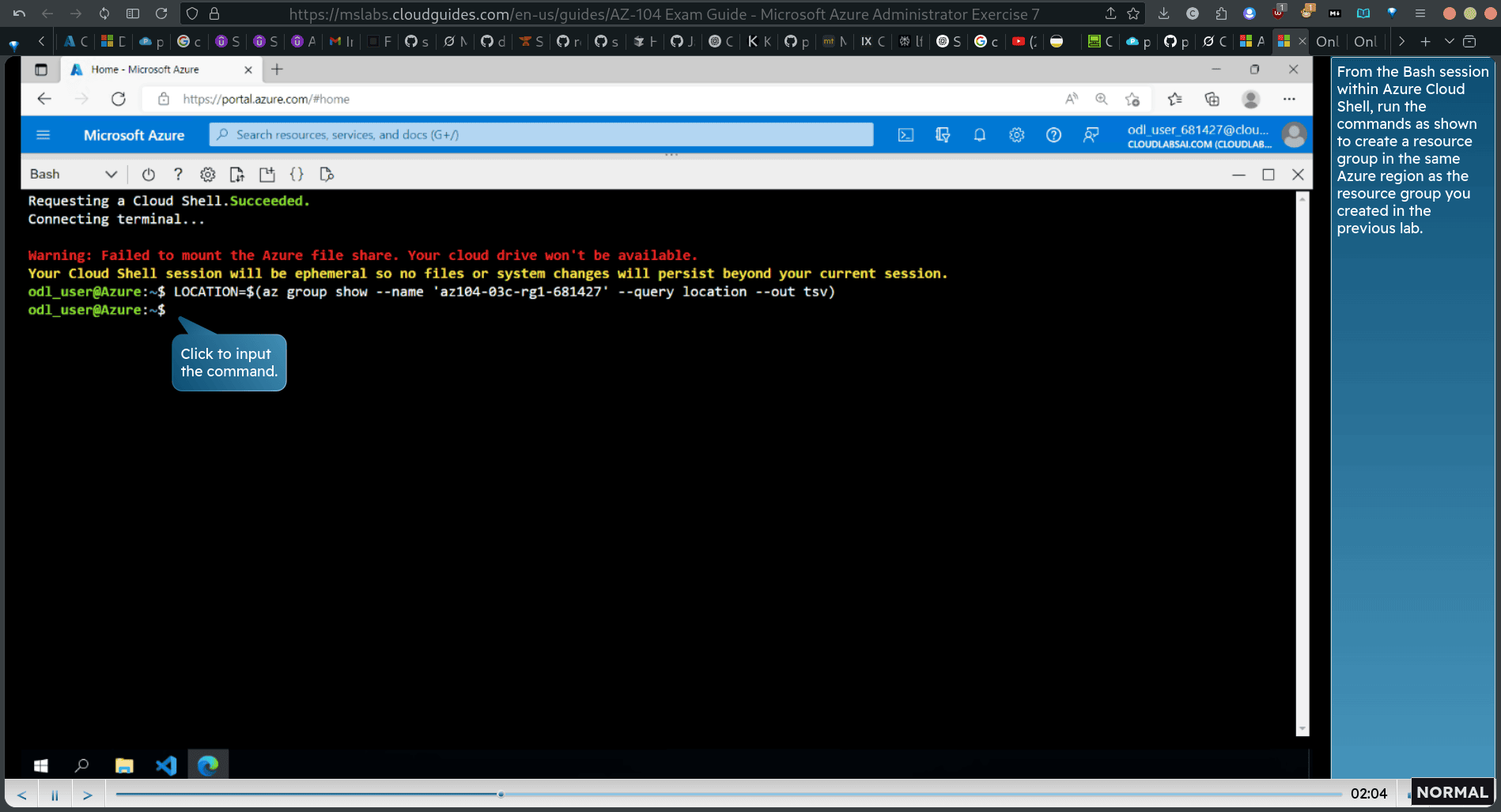
Task 2: Create a resource group and an Azure managed disk by using Azure CLI
LOCATION=$(az group show —name ‘lle-QZc-rgl-&SlléT —query location —out tsv)
RGNAME=‘az104-03d-rgl-681427”
az group create —name LOCATION
az group show —name $RGNAME
- checking
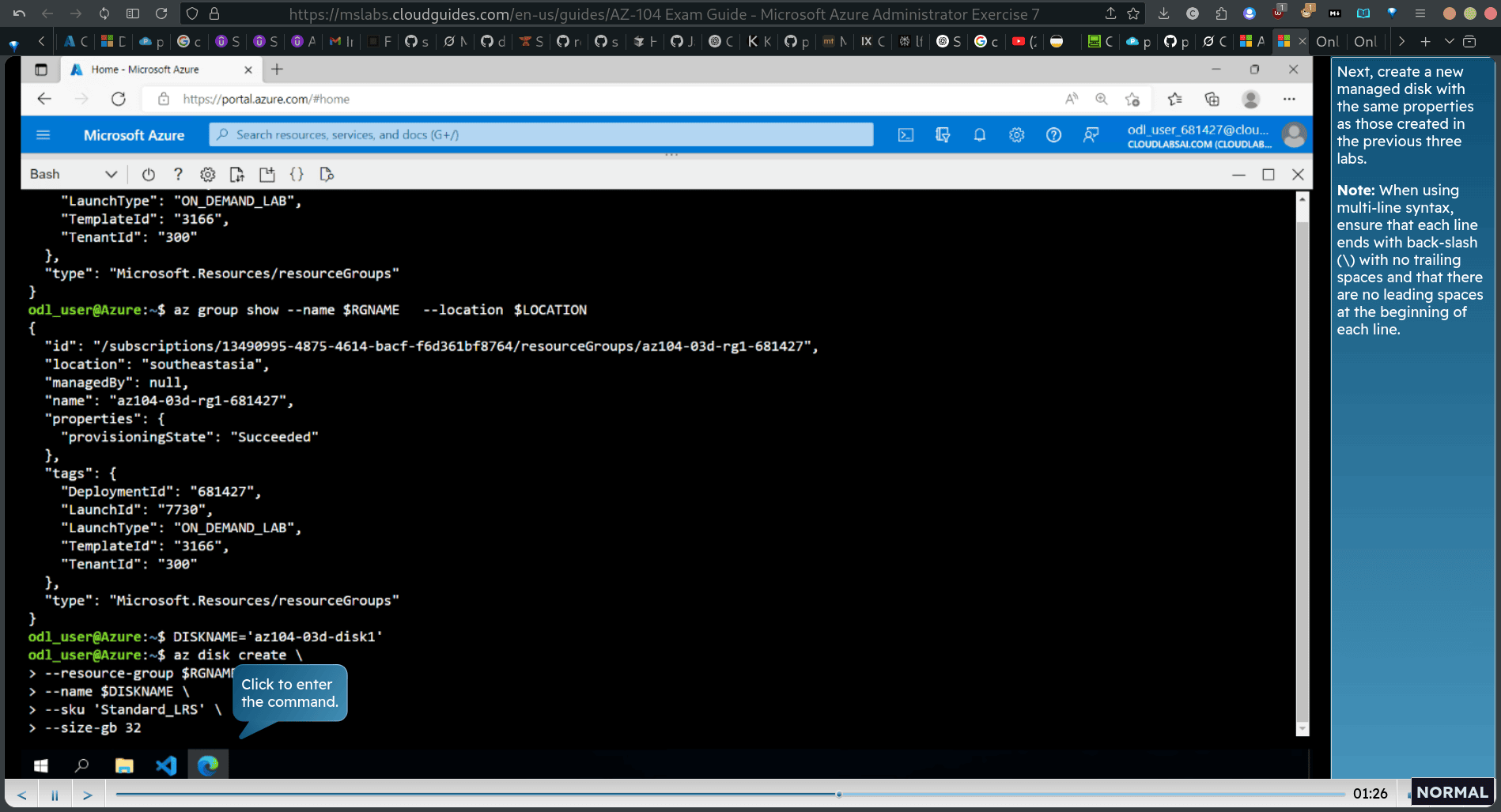
DISKNAME=‘az104-03d-diskl”
az disk create \ resource group , name $Disname , sku ‘Standard_LRS’, —size-gb 32
az disk show —resource-group DISKNAME
- retrieve the property on newly created disk
Task 3: Configure the managed disk by using Azure CLI
az disk update —resource-group DISKNAME —size-gb 64 az disk show —resource-group DISKNAME —query diskSizeGb
az disk update —resource-group DISKNAME —sku ‘Premium_LRS’
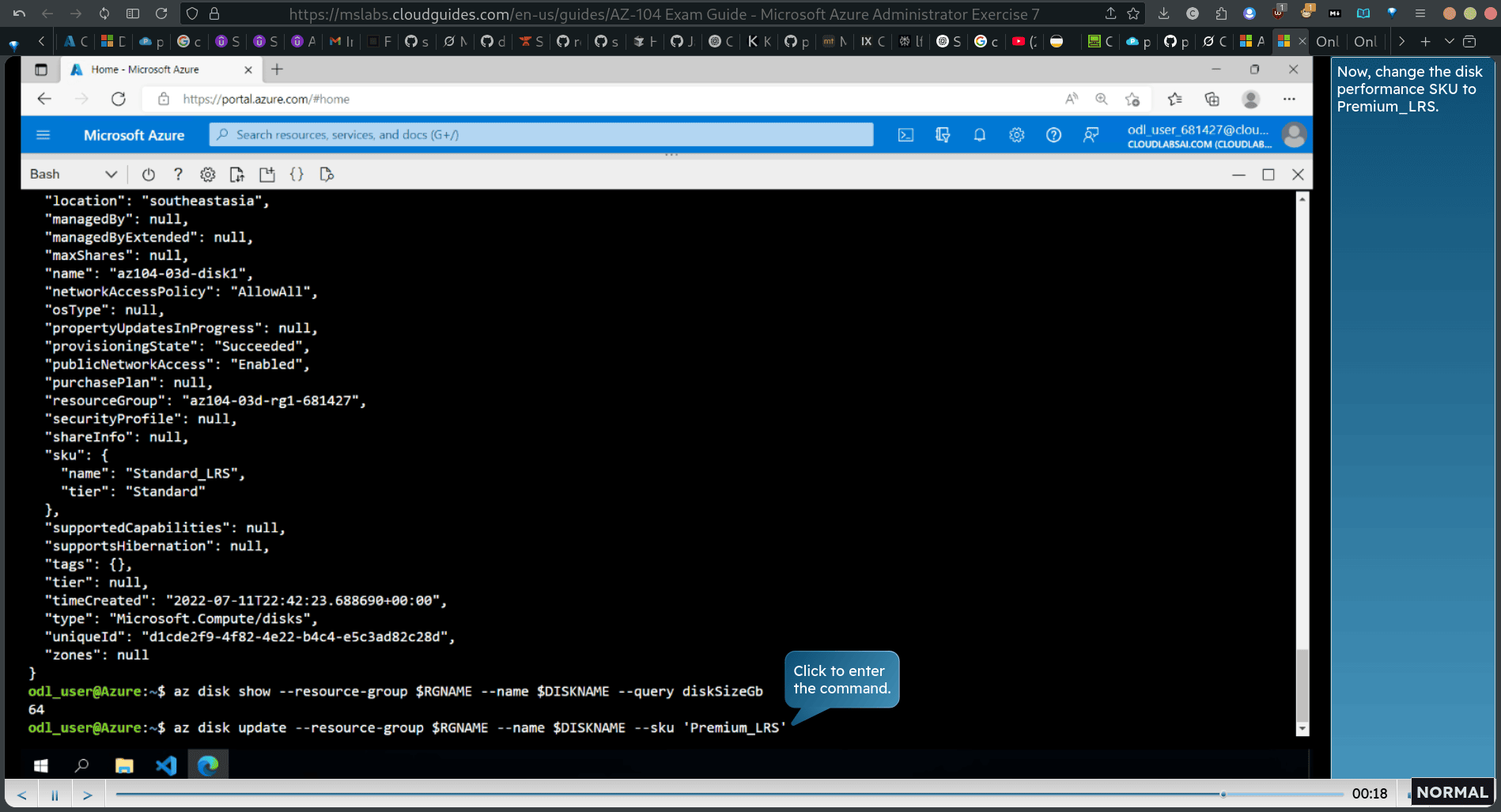 verify:
az disk show —resource-group DISKNAME —query sku
verify:
az disk show —resource-group DISKNAME —query sku
8. Implement virtual networking >
Task 1: Create and configure a virtual network
Virtual network
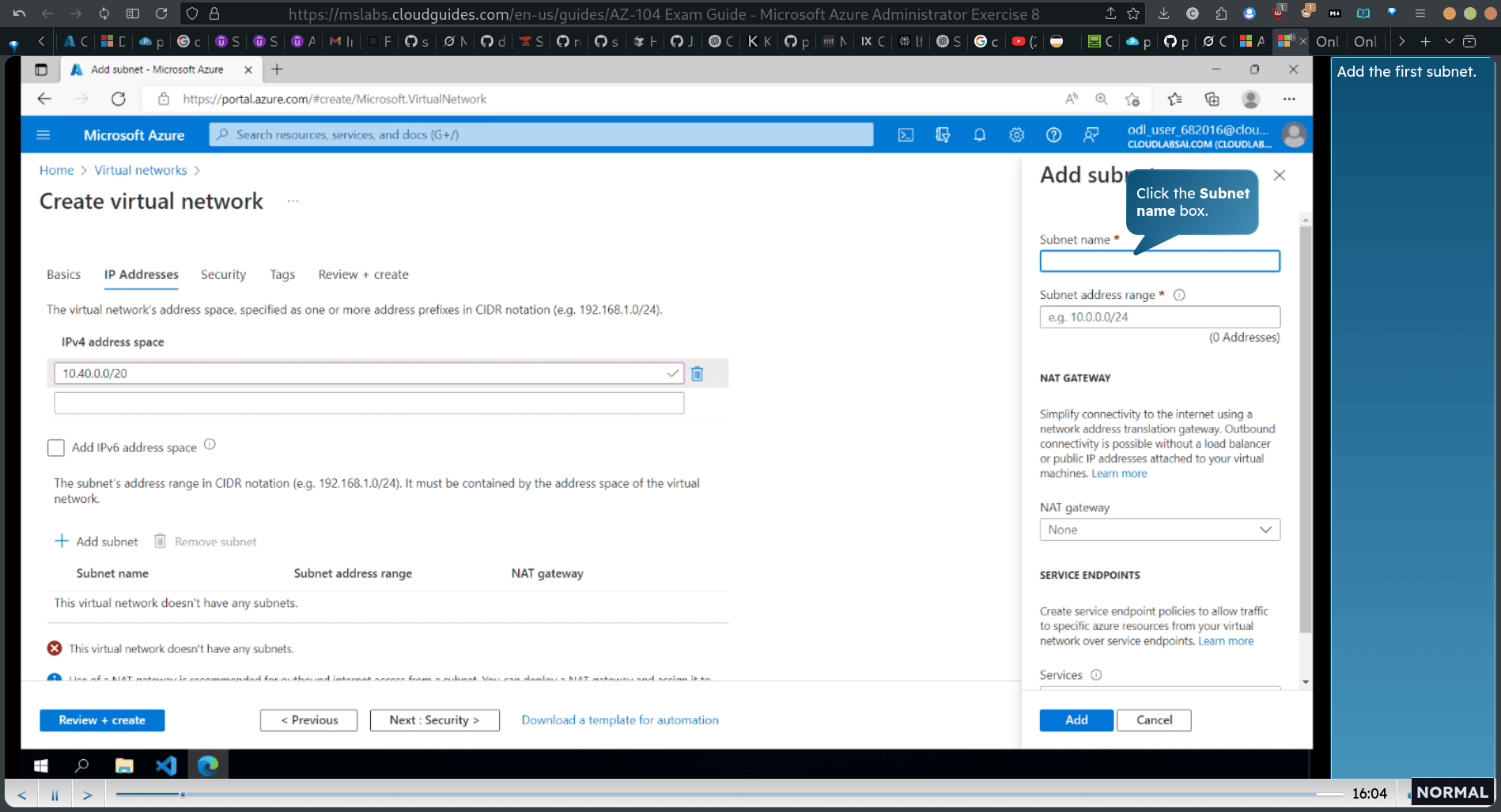 modify the ip address /20
modify the ip address /20
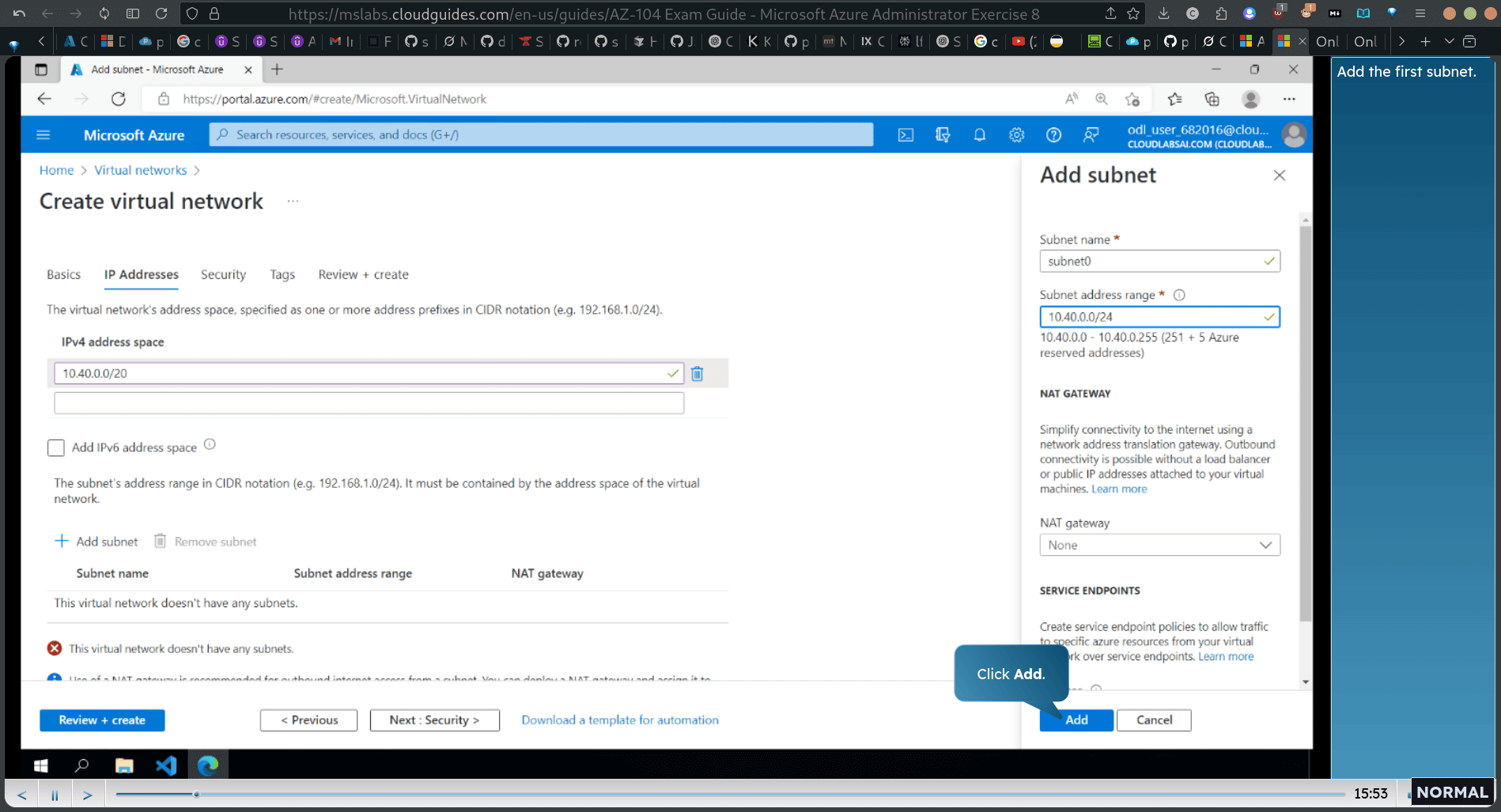 subnet /24
subnet /24
10.40.0.0/20 → 10.40.0.0/24
Sure! Here’s how to choose the right subnet size based on your scenario in Azure.
🔍 1. Ask: How many IP addresses do you need?
Azure reserves 5 IPs per subnet, so subtract that from the total.
| CIDR | Usable IPs | Typical Use |
|---|---|---|
/30 | 1 | Point-to-point links |
/29 | 3 | Tiny test environments |
/28 | 11 | Small dev/test subnet |
/27 | 27 | Small VM group or service tier |
/26 | 59 | Medium-sized web tier |
/24 | 251 | Larger services or databases |
/20 | 4091 | Whole VNet address space (avoid using this as a subnet!) |
📘 Example Use Cases
🔸 If you’re creating:
- A dev/test subnet with 2–5 VMs → use
/28or/27 - A frontend subnet for 20-30 web servers → use
/26 - A shared services subnet (DNS, AD) → use
/27 - A future-proof subnet for scalable apps → use
/24
🧮 How to calculate the subnet size
Use the formula:
2^(32 - CIDR block) - 5 = usable IPs
So for /26:
2^(32-26) - 5 = 64 - 5 = 59 usable IPs
✅ Subnet Planning Tips for Azure
- Start small, but leave space to scale (e.g., use
/27instead of/28) - Separate roles into subnets: frontend, backend, database, management
- Avoid using the entire address space in a single subnet
- Leave gaps for future subnets when designing your CIDR blocks
If you tell me:
- How many VMs or services you want to deploy
- Whether it’s dev, test, or production
- How much room you want for future expansion
… I can recommend the best CIDR for your subnet. Want to do that?
Great question! You subtract 5 IP addresses from each Azure subnet because Azure reserves them for internal use. Here’s the breakdown:
🔹 Why does Azure reserve 5 IP addresses per subnet?
When you create a subnet in Azure, it automatically reserves 5 IPs for internal functions:
| Reserved IP | Purpose |
|---|---|
| .0 | Network address (e.g., 10.40.0.0) — identifies the subnet |
| .1 | Default gateway — used by Azure for routing outbound traffic |
| .2 - .3 | Reserved by Azure for future use |
| .255 | Broadcast address (in traditional networking), reserved |
So: First 4 + last 1 = 5 reserved IPs
🔸 Example: 10.40.0.0/24 subnet
- Total IPs:
2^(32 - 24) = 256 - Reserved by Azure:
5 - Usable IPs:
256 - 5 = 251
✅ Why this matters:
When planning your subnets, always keep these 5 reserved IPs in mind. If you need 20 VMs, a /27 (32 total IPs → 27 usable) would work. But if you use /28 (16 total IPs), you’d only get 11 usable — maybe not enough.
Let me know how many machines or services you’re planning, and I can suggest a subnet size that leaves enough usable space!
Why does Azure reserve 5 IP addresses per subnet?
When you create a subnet in Azure, it automatically reserves 5 IPs for internal functions: Reserved IP Purpose .0 Network address (e.g., 10.40.0.0) — identifies the subnet .1 Default gateway — used by Azure for routing outbound traffic .2 - .3 Reserved by Azure for future use .255 Broadcast address (in traditional networking), reserved
So: First 4 + last 1 = 5 reserved IPs
create
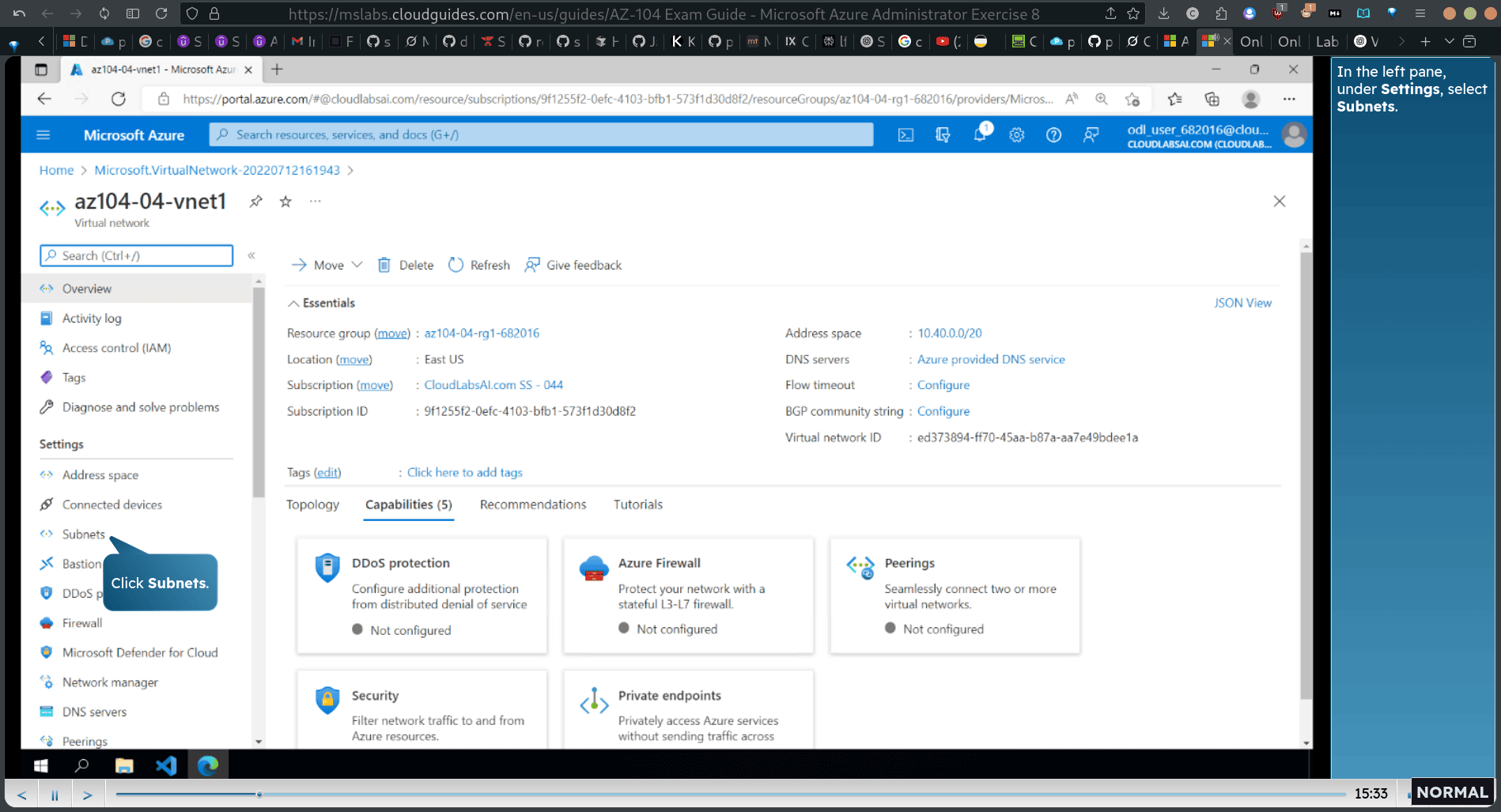 select subnet
select subnet
add new subnet for newly
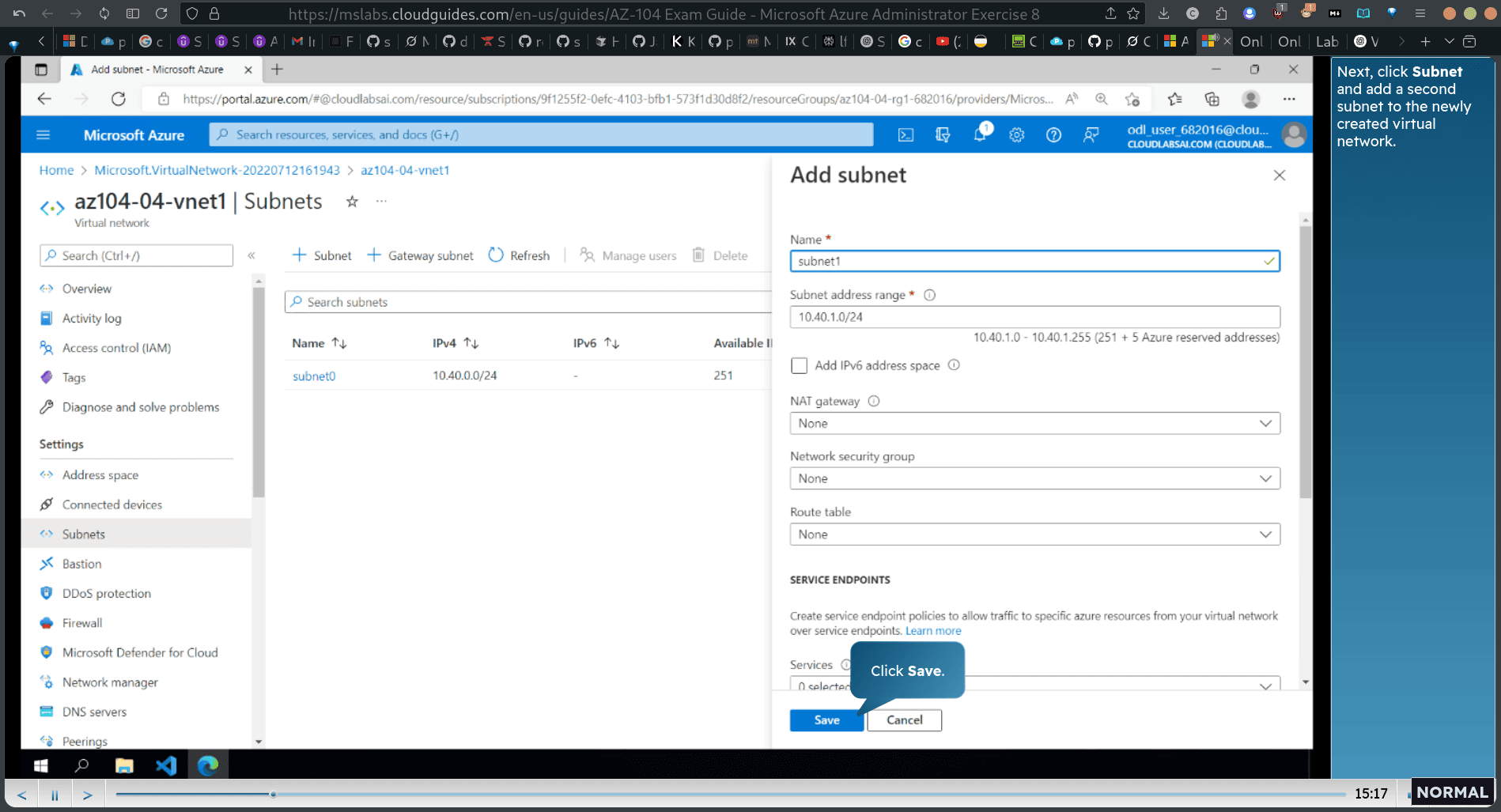
10.40.1.0/24
Task 2: Deploy virtual machines into the virtual network
cloud → powershell →storage
upload
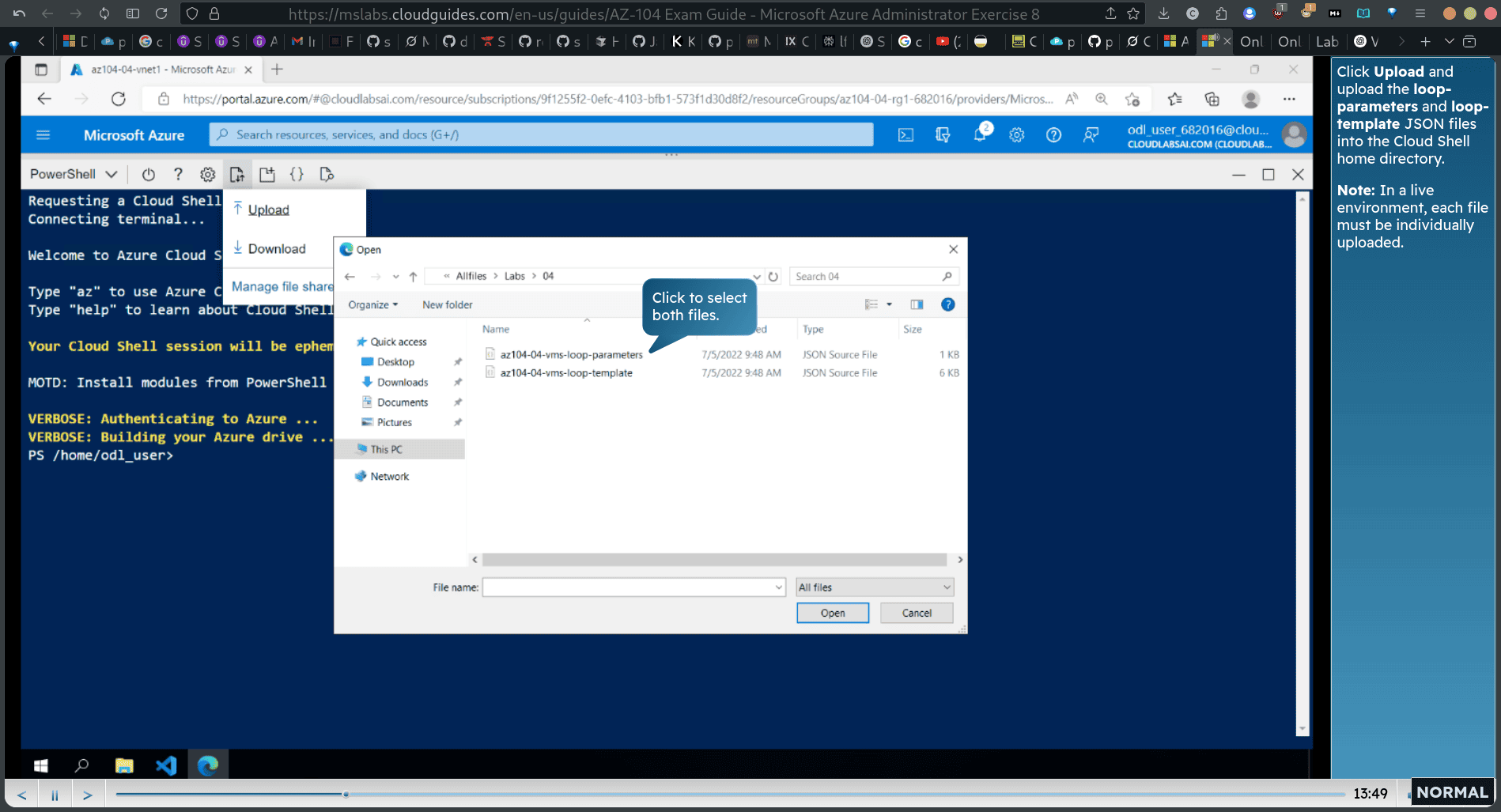 upload both VM → vms loop parameters and template
upload both VM → vms loop parameters and template
code . → vs code
parameter → change the password
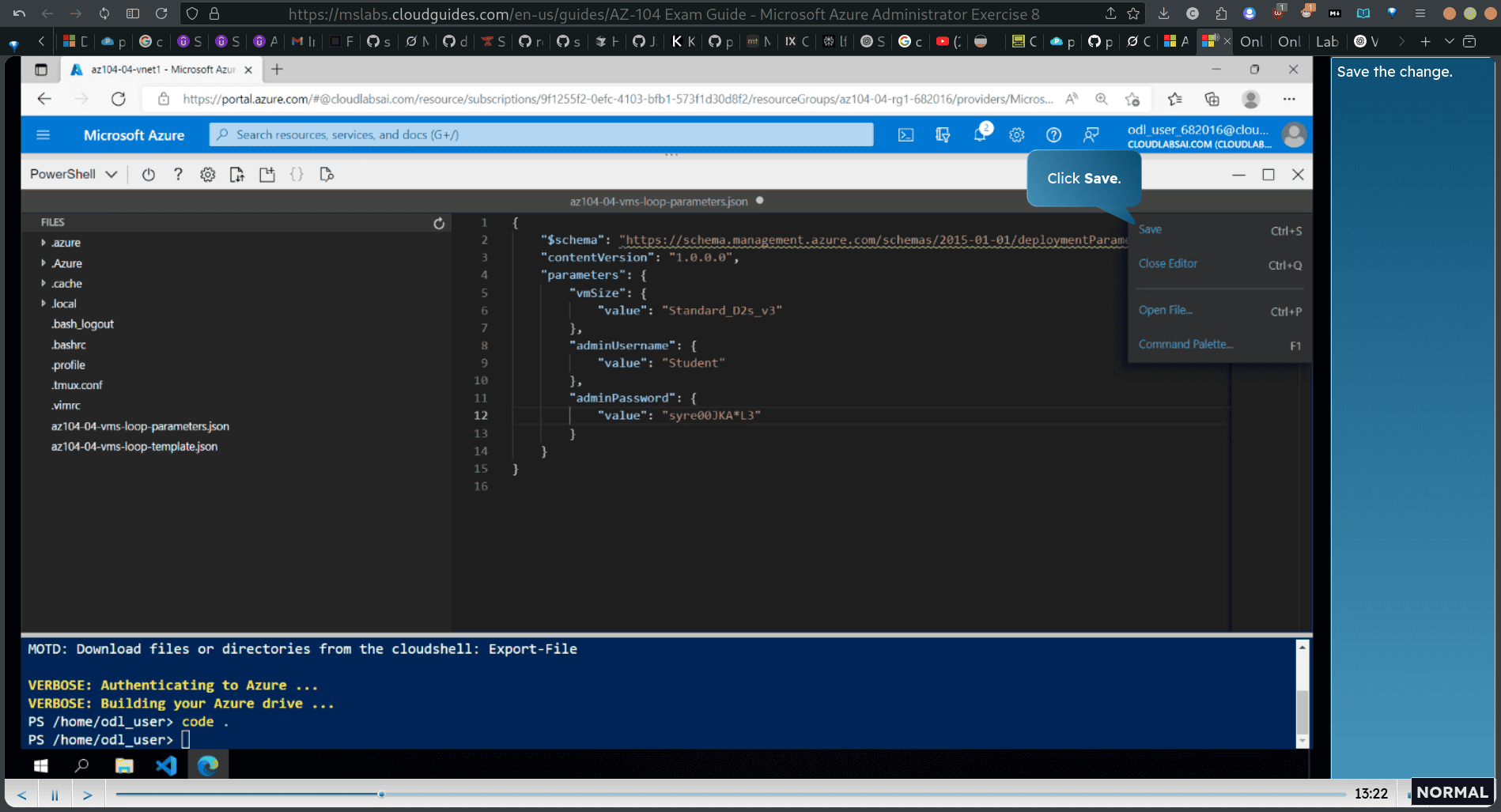
$rgName = ‘az104-04-rgl-682016”
New-AzResourceGroupDeployment `
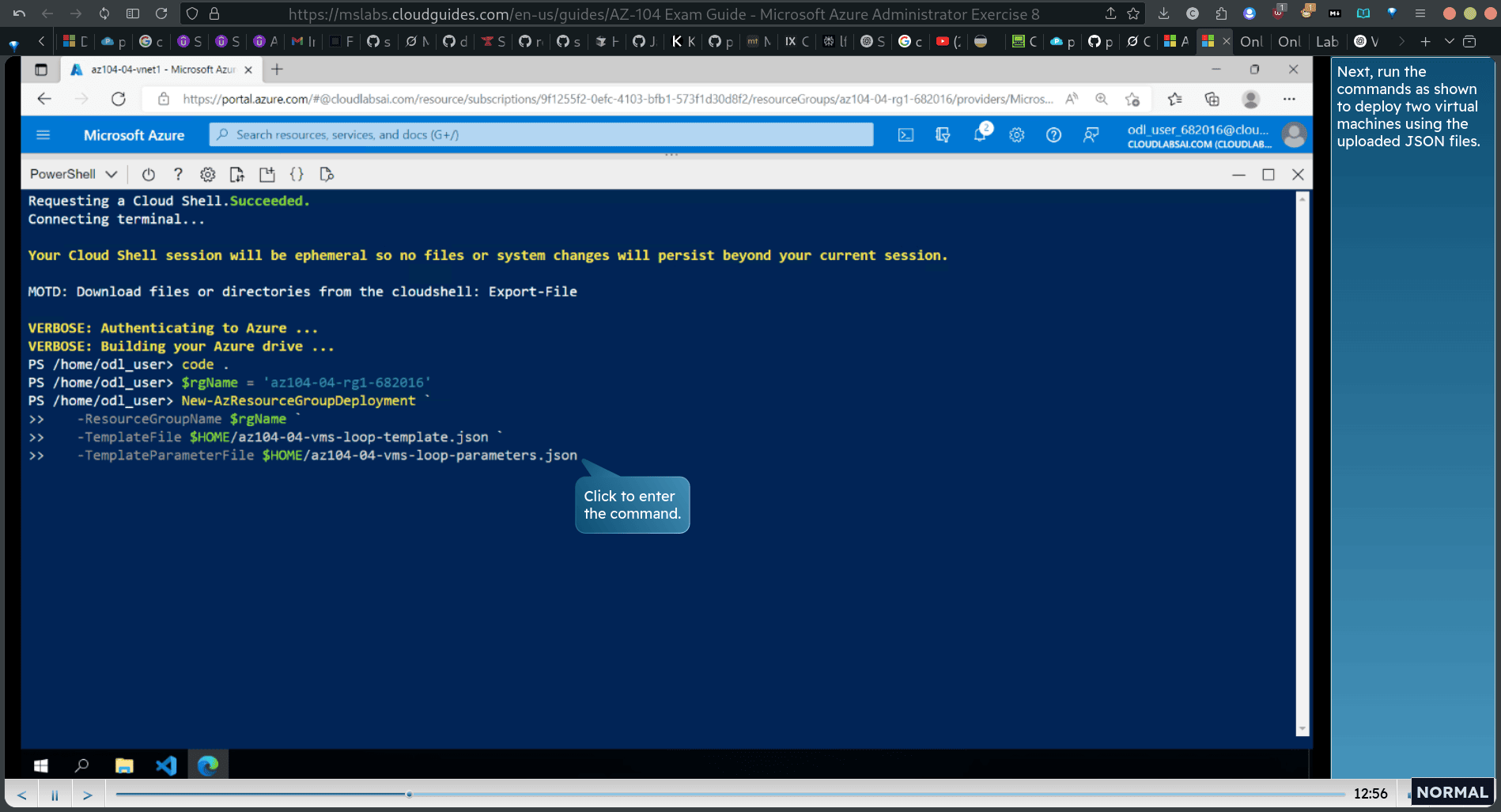
Task 3: Configure private and public IP addresses of Azure VMs
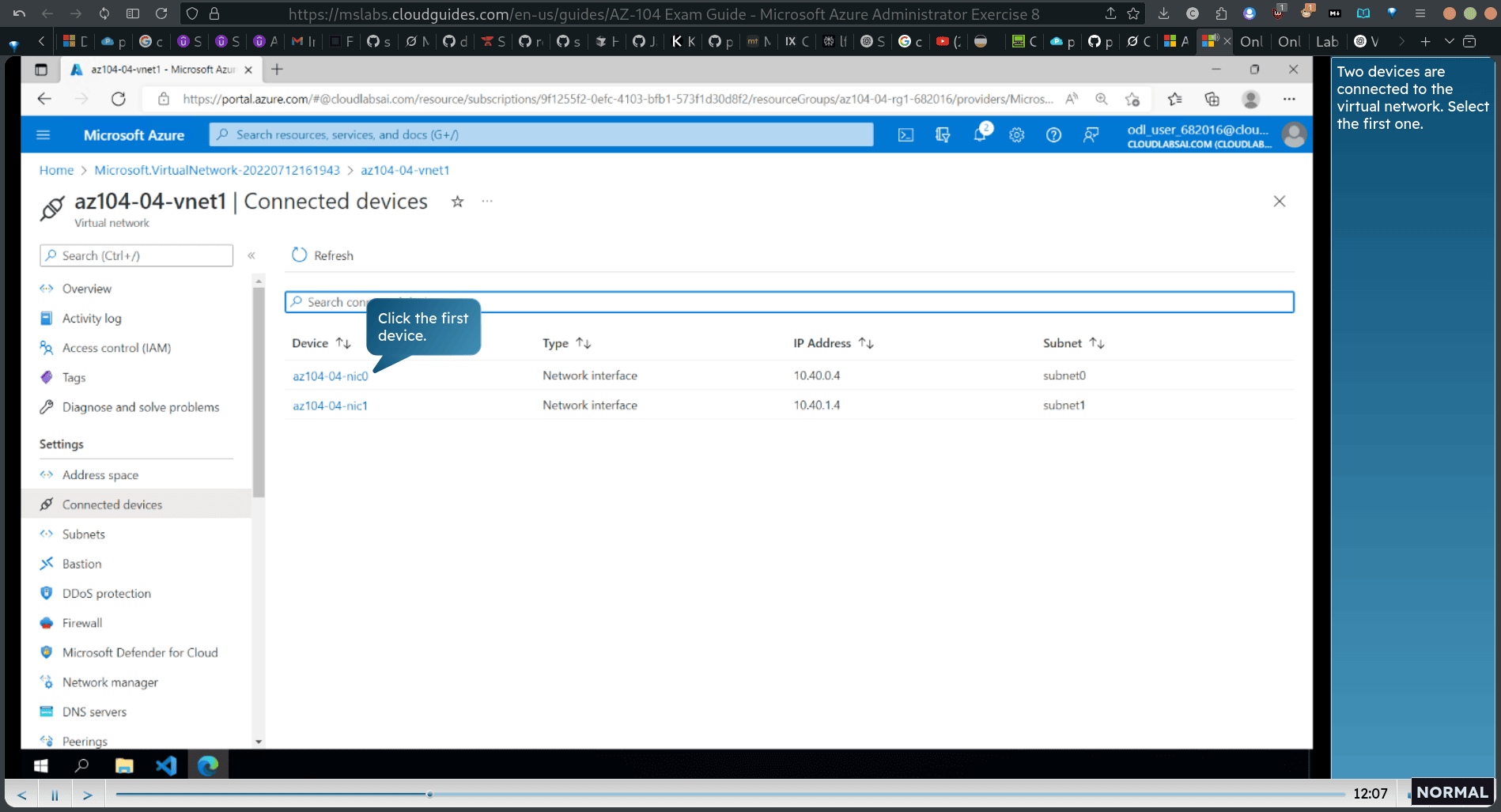
connect device → ip config
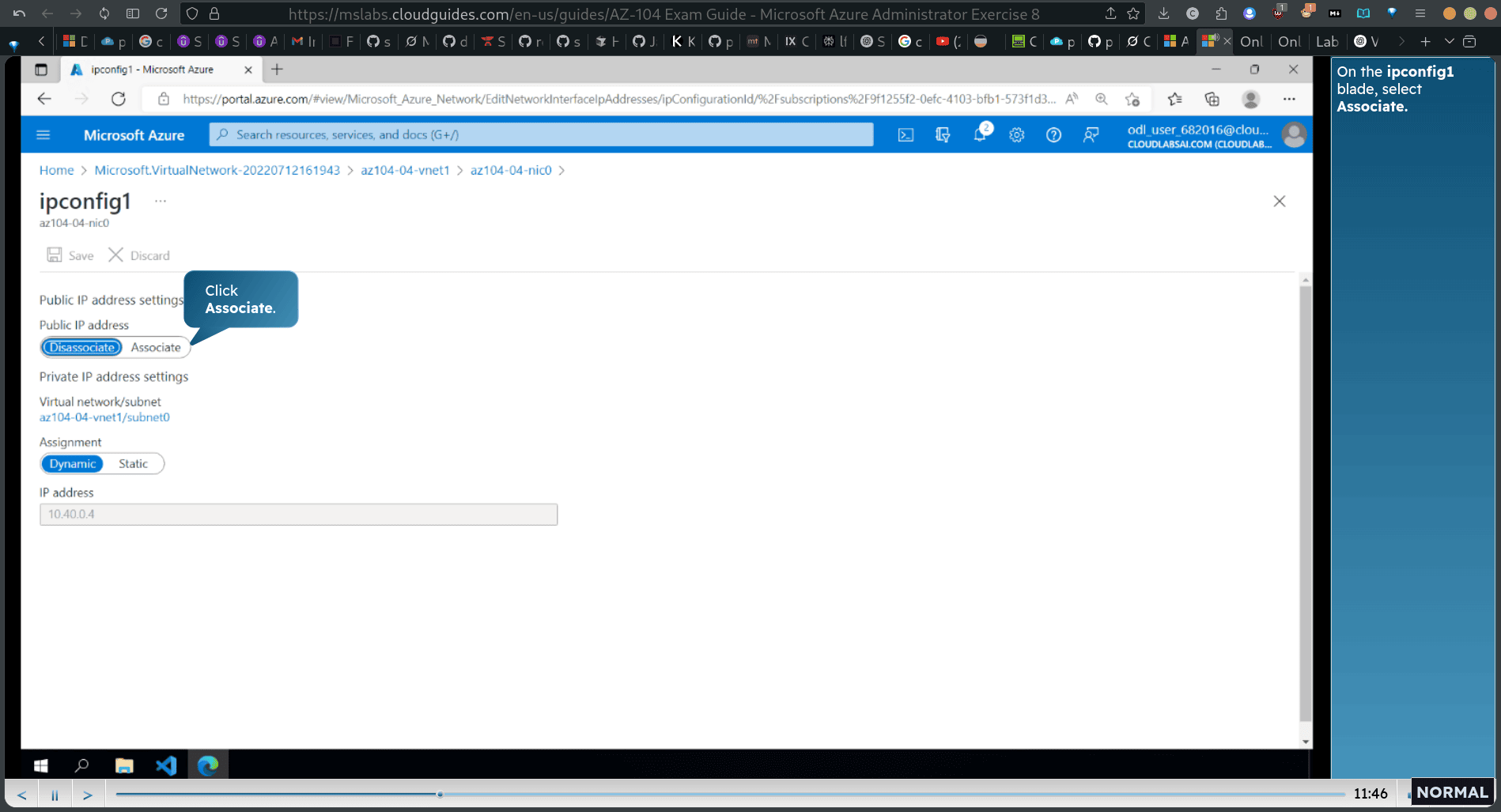 associate
associate
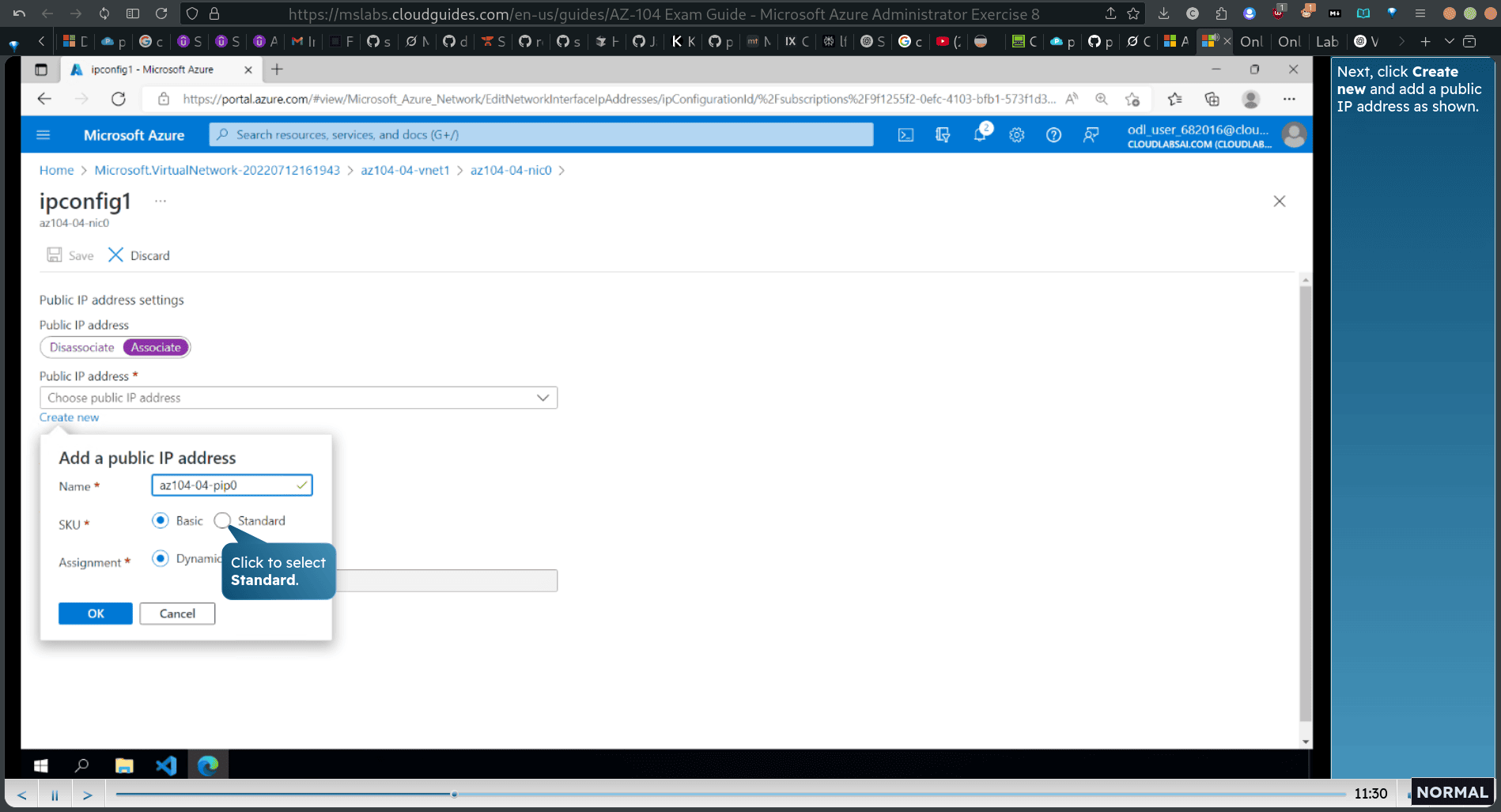
add public id address
assignment → static 10.40.0.4
select second device
ip config →
again
Task 4: Configure network security groups
Search VM select the first VM
connect → RDP → Remote desktop → download RDP file
 using public addres → port 3389 → RDP
using public addres → port 3389 → RDP
connect fail as expected
- → network security group
go to resource
- allow inbond security rules
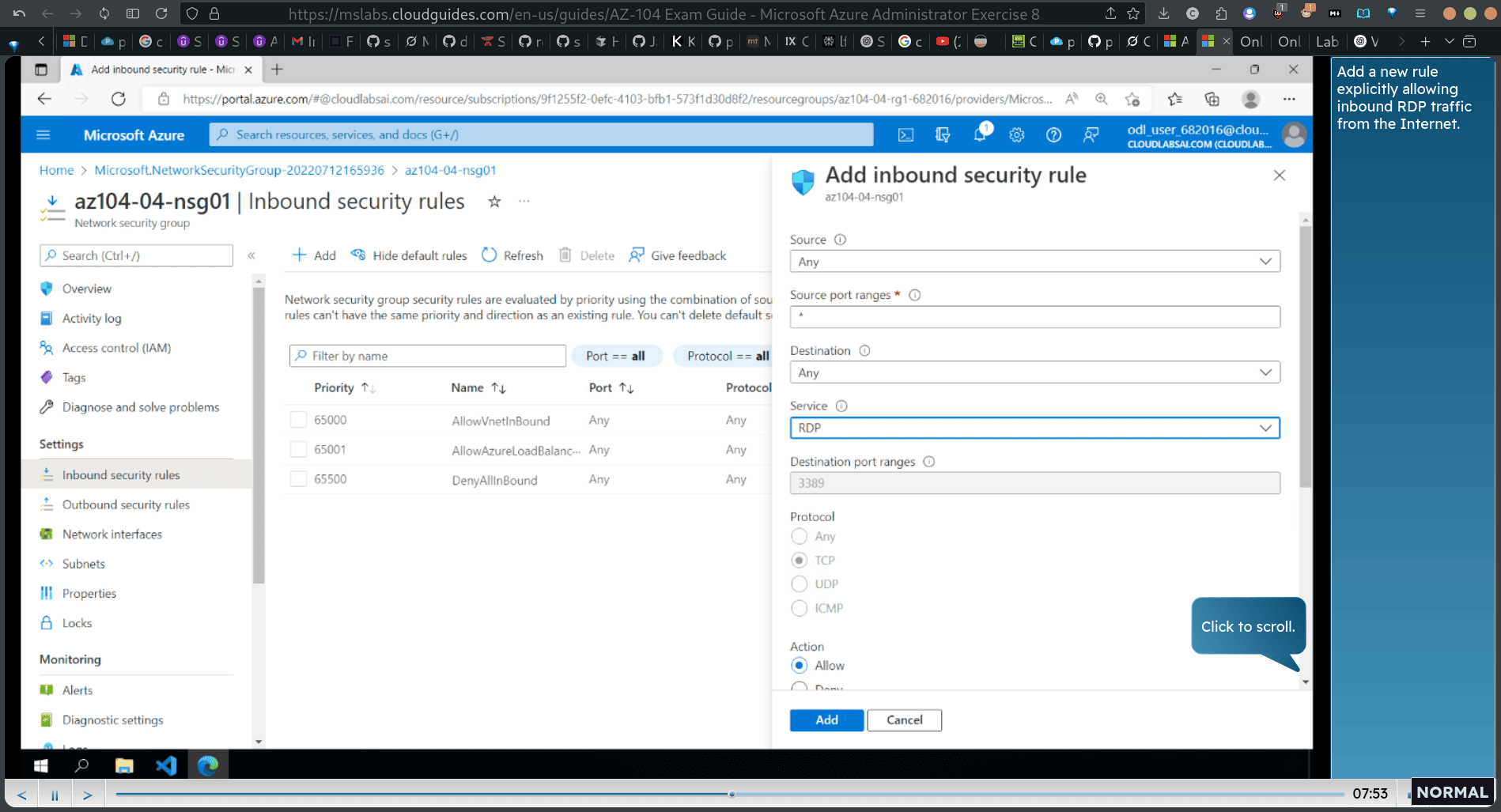 allow rdp
allow rdp
click priority , → 300 , name
- Network interfaces → associate
select associated to network security group
select both newly
go back to VM
 now can be used in rdp
now can be used in rdp
Task 5: Configure Azure DNS for internal name resolution
private azure dns zones
search private azure dns zones
Virtual network links → add
-
Enable auto registration
-
Verify that both virtual machines appear in the list of record set as auto registered. Next, return to the RDP session for the first virtual machine.
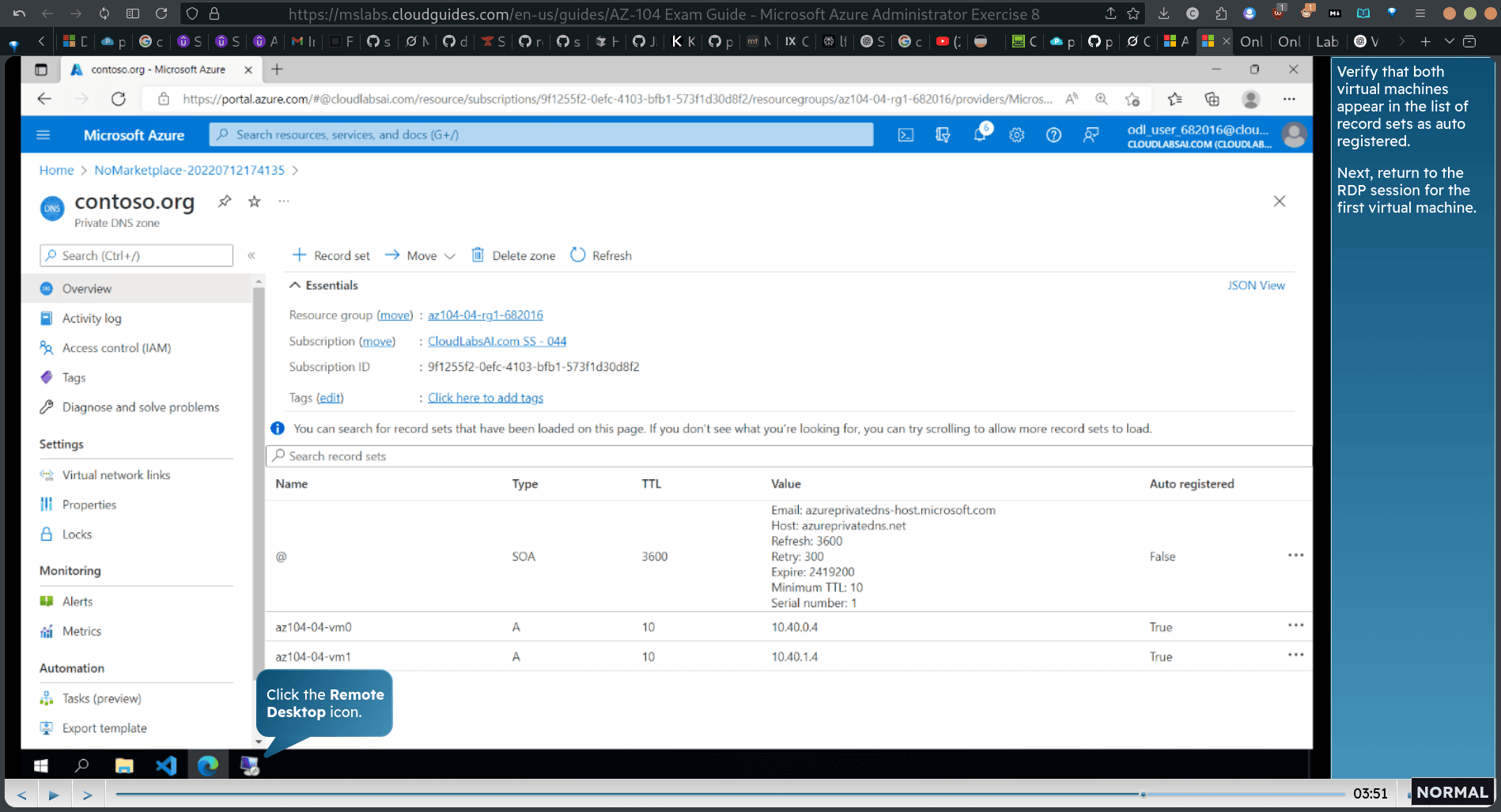
back to rdp window → , run as admin powershell :
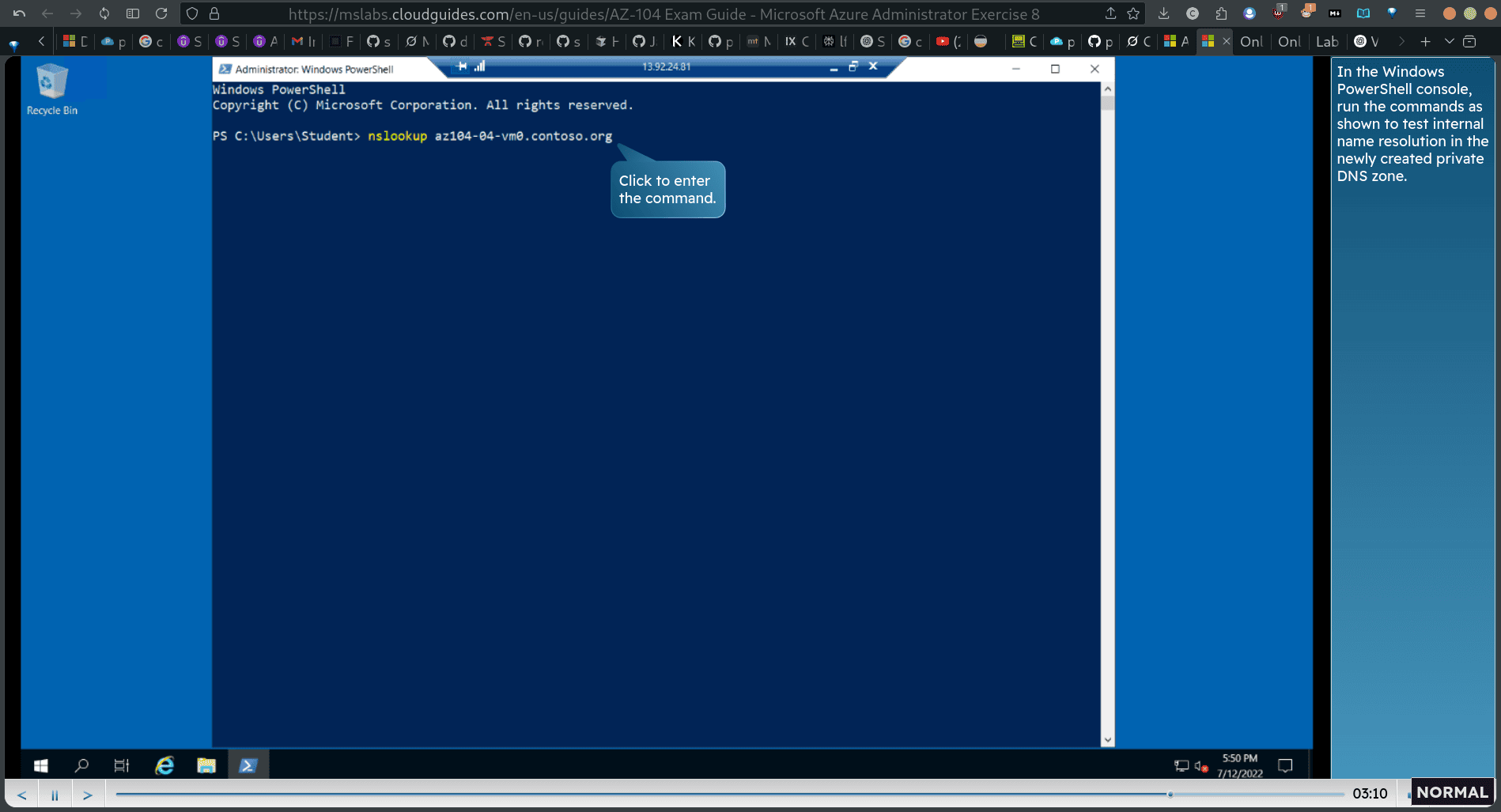
nslookup az104-04-vm0.contoso.org In the Windows PowerShell console, run the commands as shown to test internal name resolution in the newly created private DNS zone.
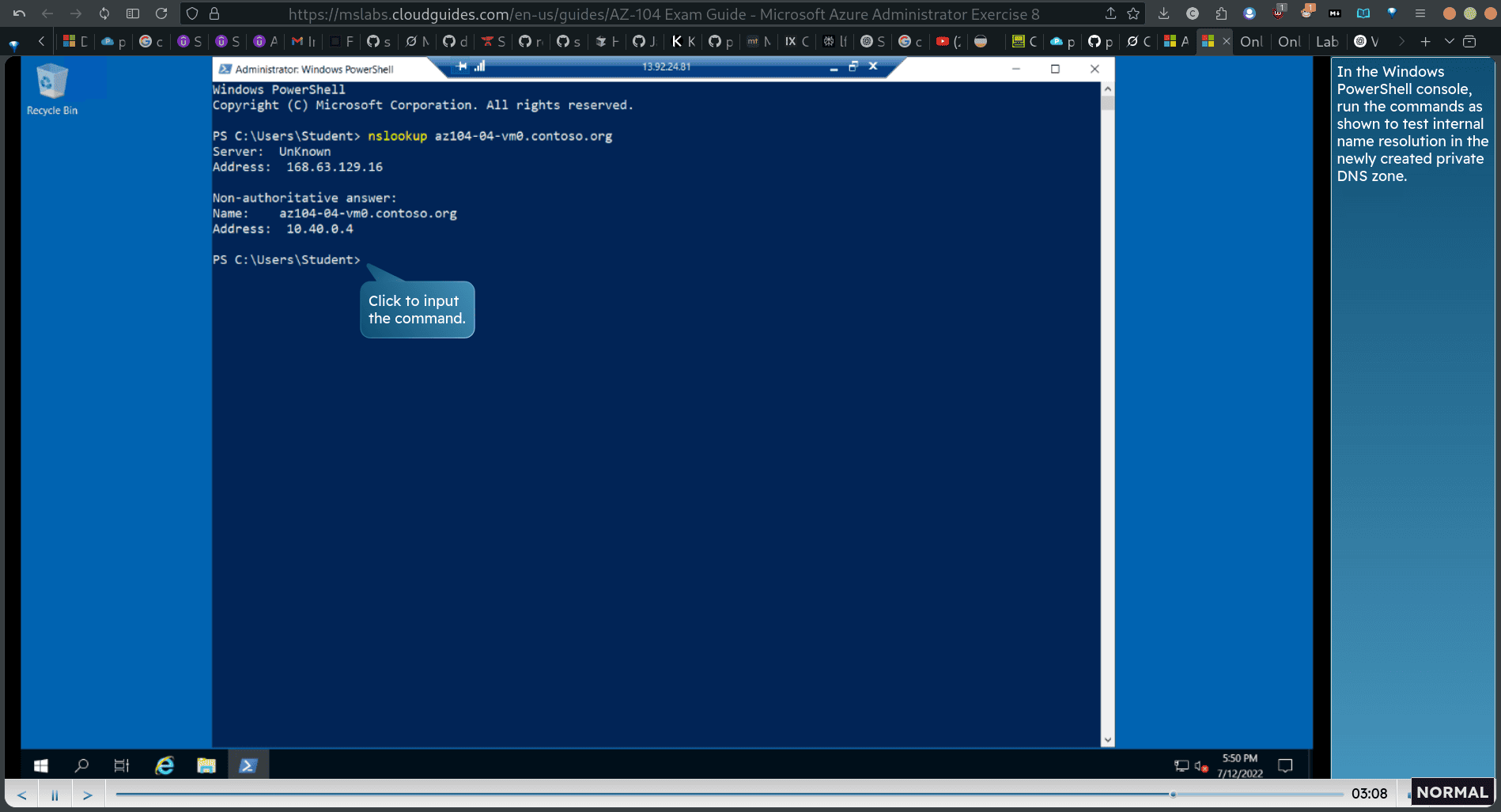 nslookup az104-84-vm1.contoso.org
nslookup az104-84-vm1.contoso.org
Task 6: Configure Azure DNS for external name resolution
search dns zone
name → dns name
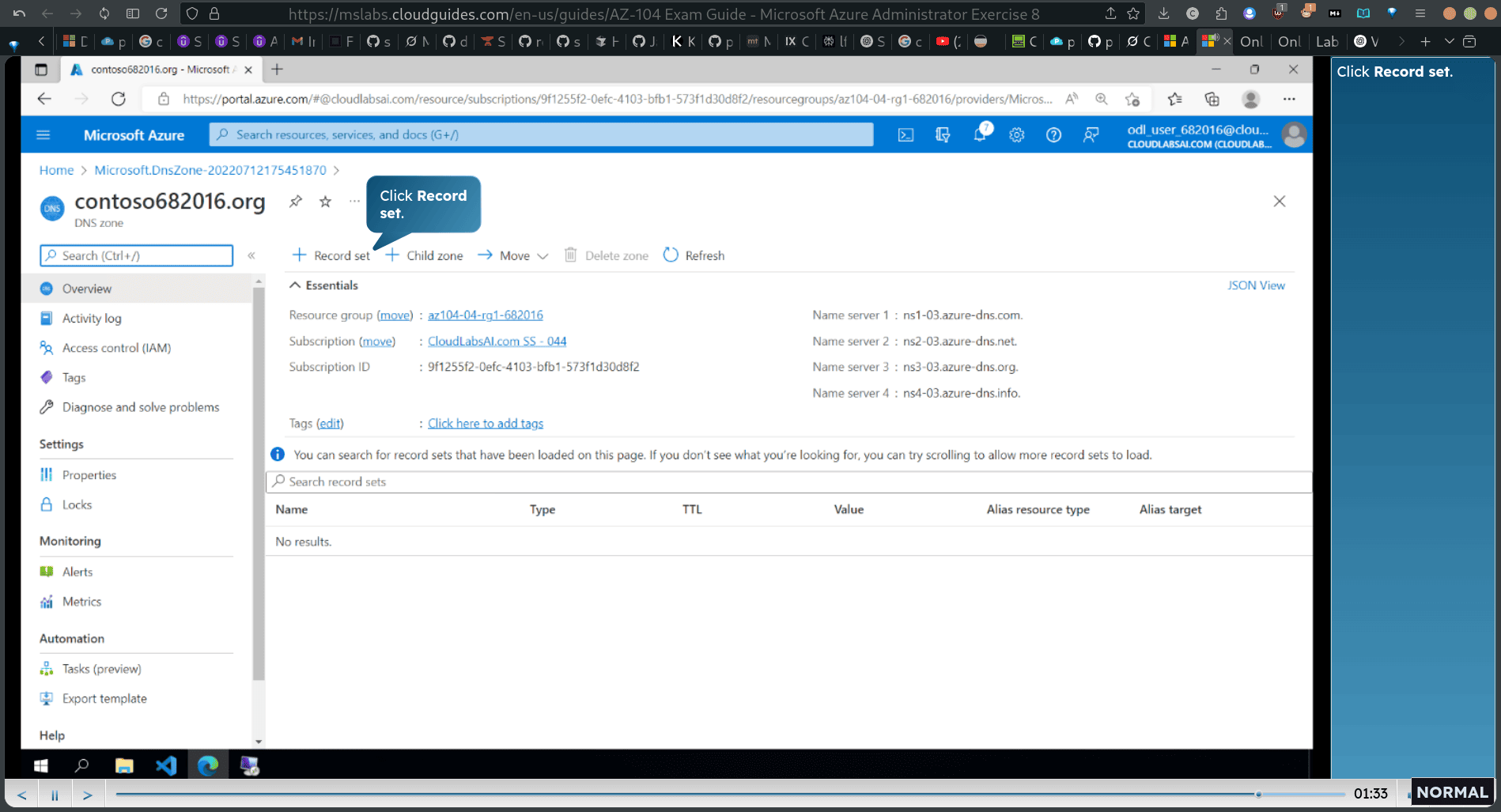 overview → record set
overview → record set
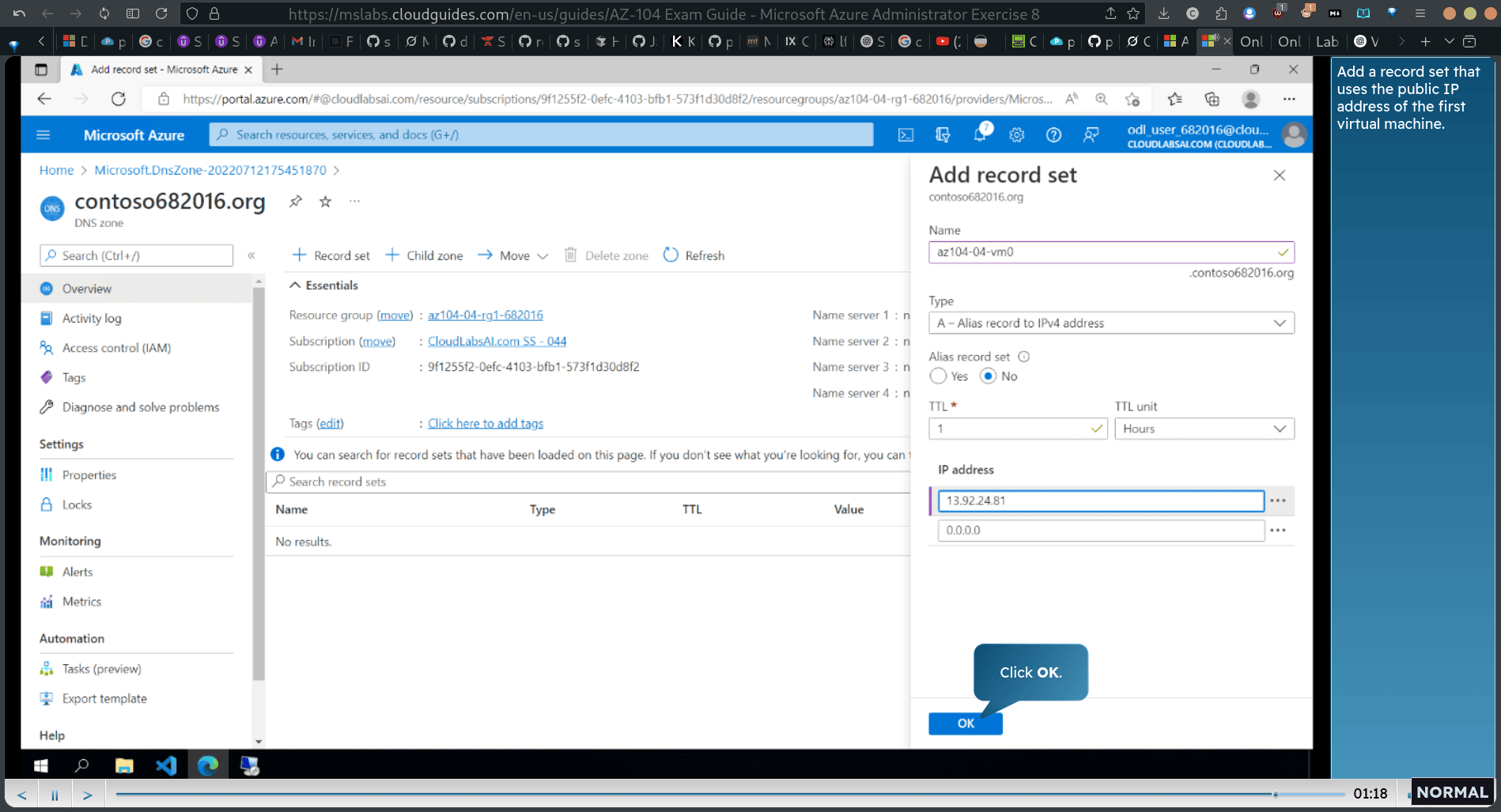
-
Add a record set that uses the public IP address of the first virtual machine.
-
Next, add a record set that uses the public IP address of the second virtual machine.
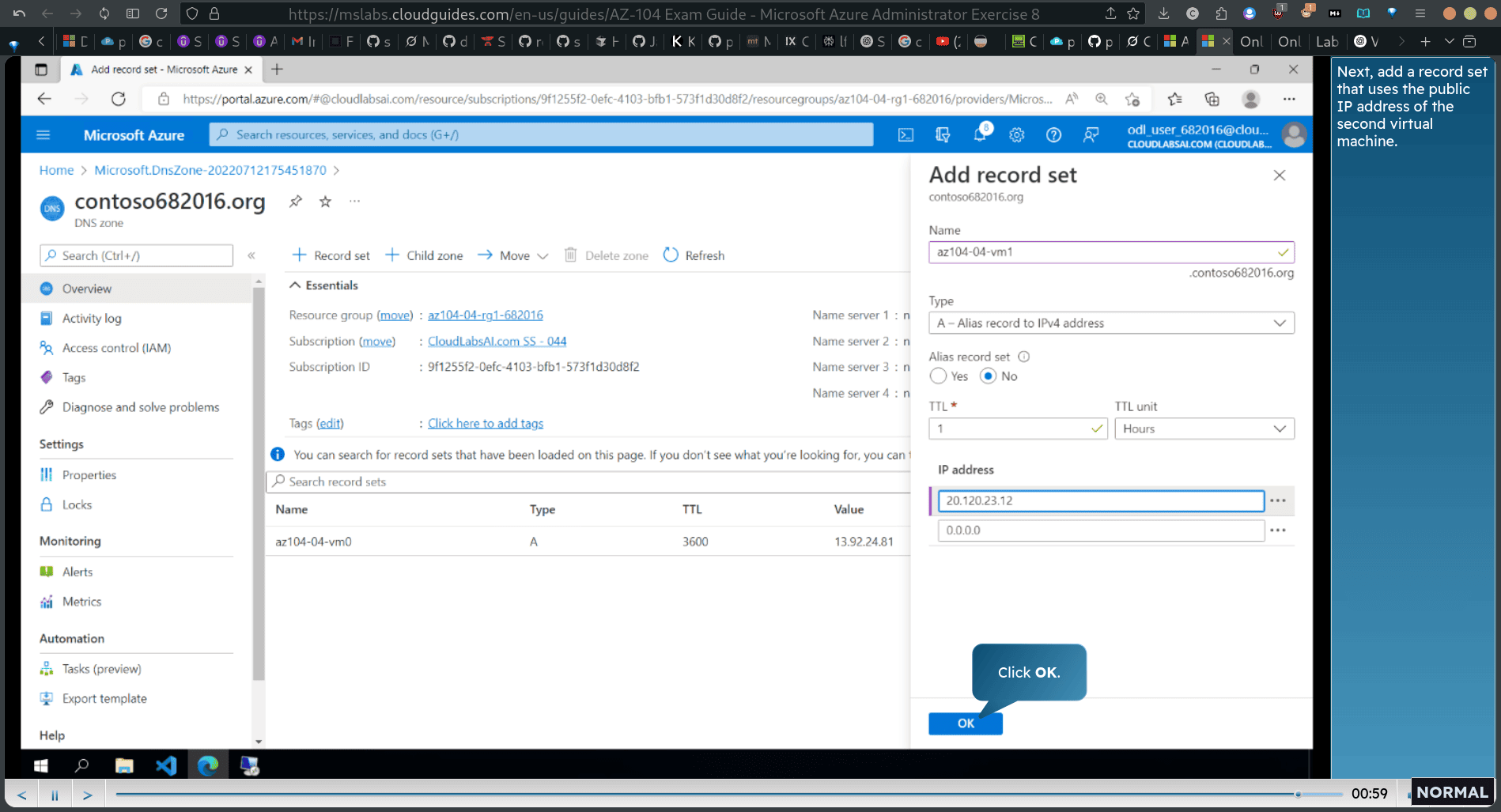
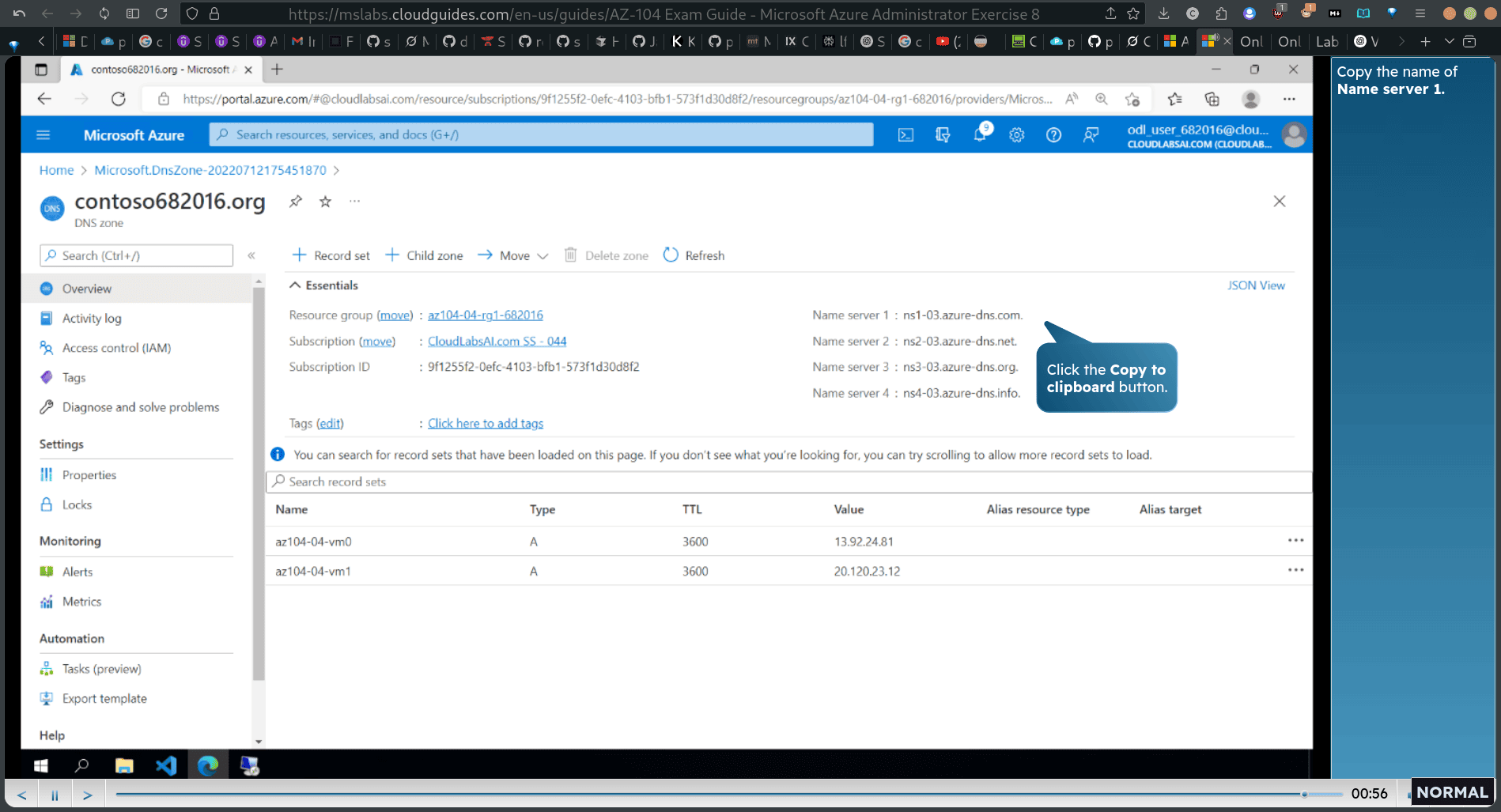
- copy the name of name sever 1
cloud shell → nslookup az104-84-vm@.contoso682016.org nsl1-03.azure-dns.com.
- In the PowerShell console, run the command as shown fo test external name resolution in the newly created DNS zone for the first DNS record set. Note: Use the name of Name server 1 and the name of the DNS domain created earlier in this task.
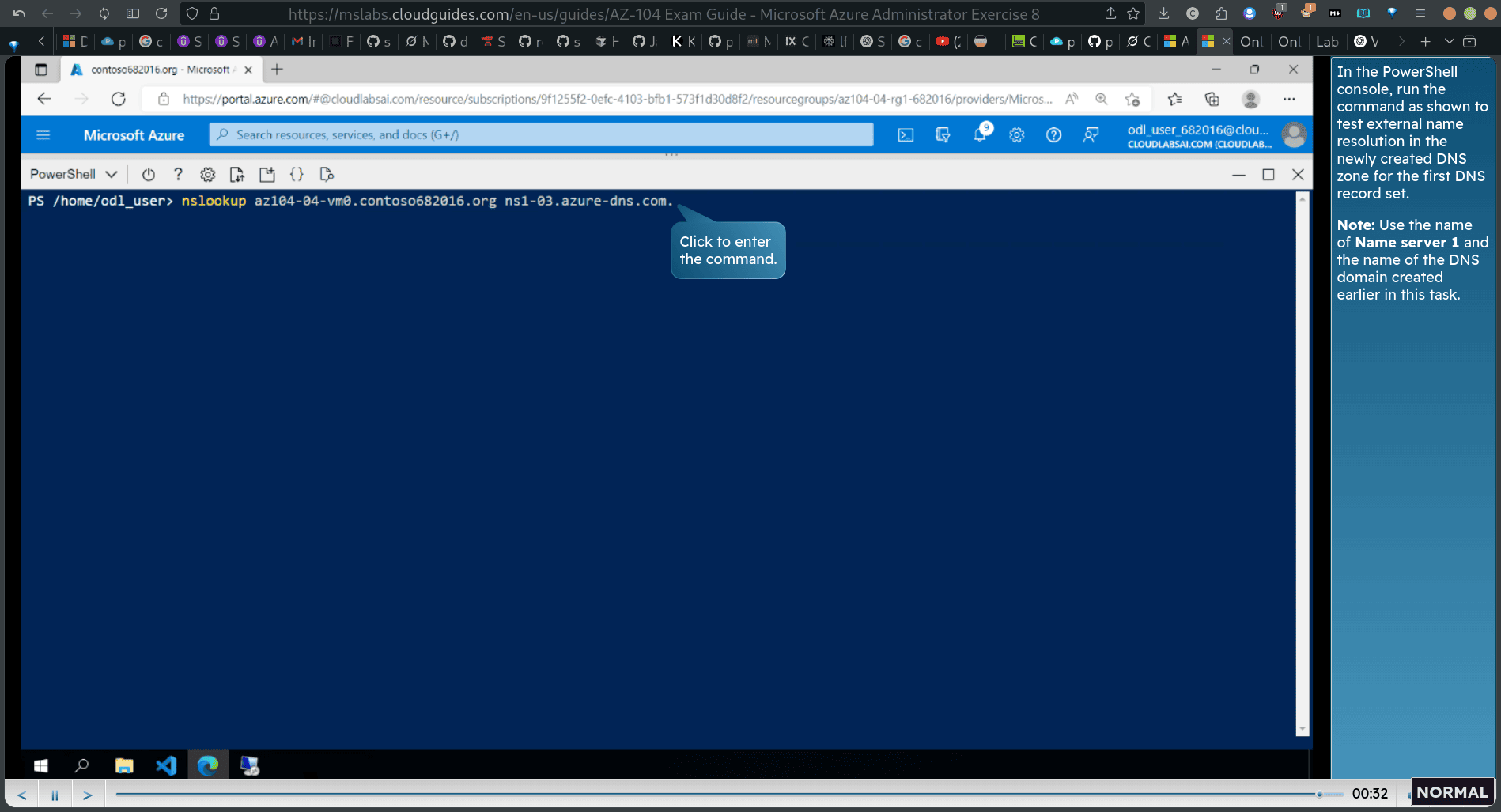
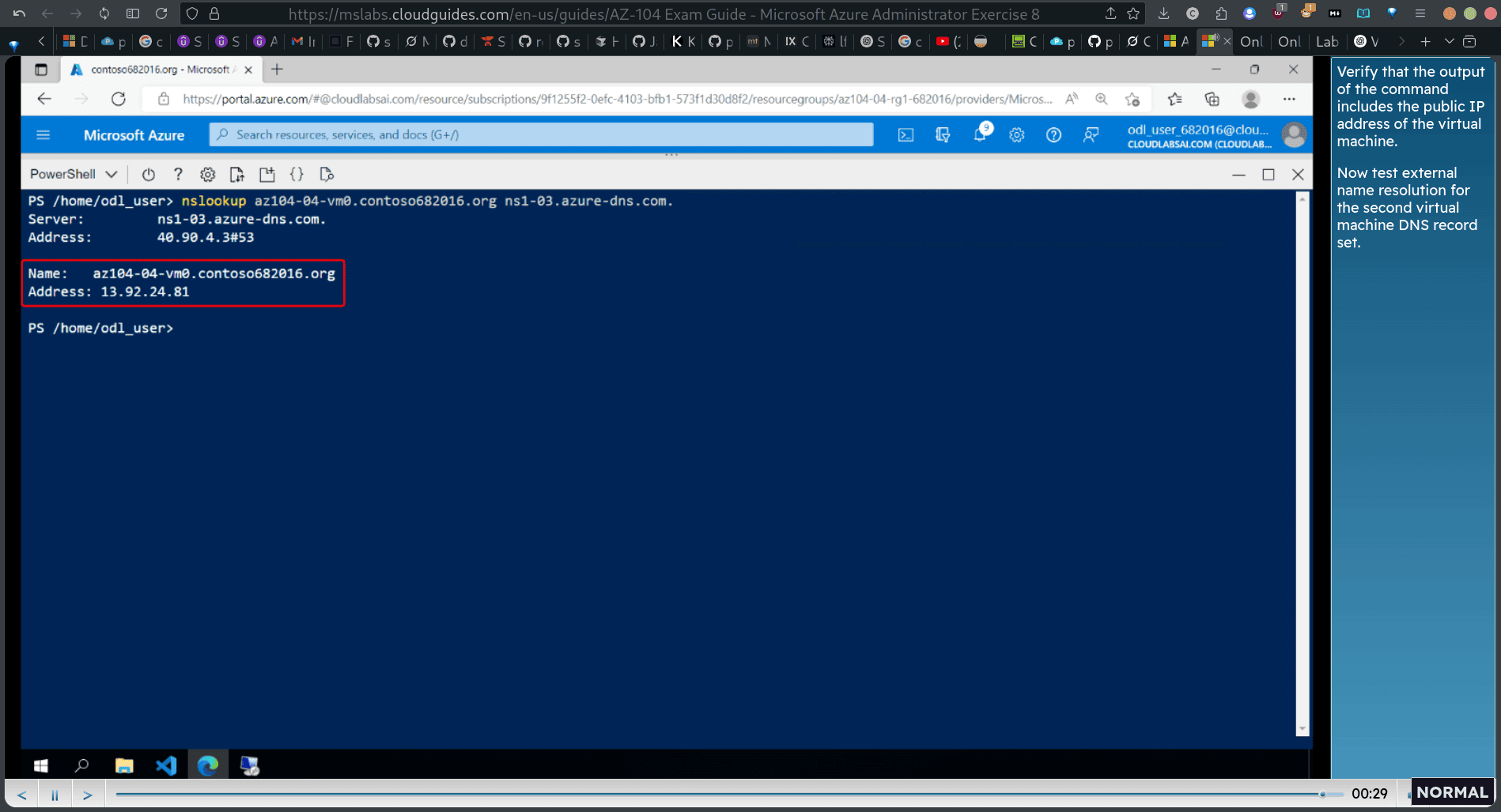
- Verify that the output of the command includes the public IP address of the virtual machine. Now test external name resolution for the second virtual machine DNS record set.
nslookup az104-84-vml.contoso682016.org ns1-83.azure-dns.com.
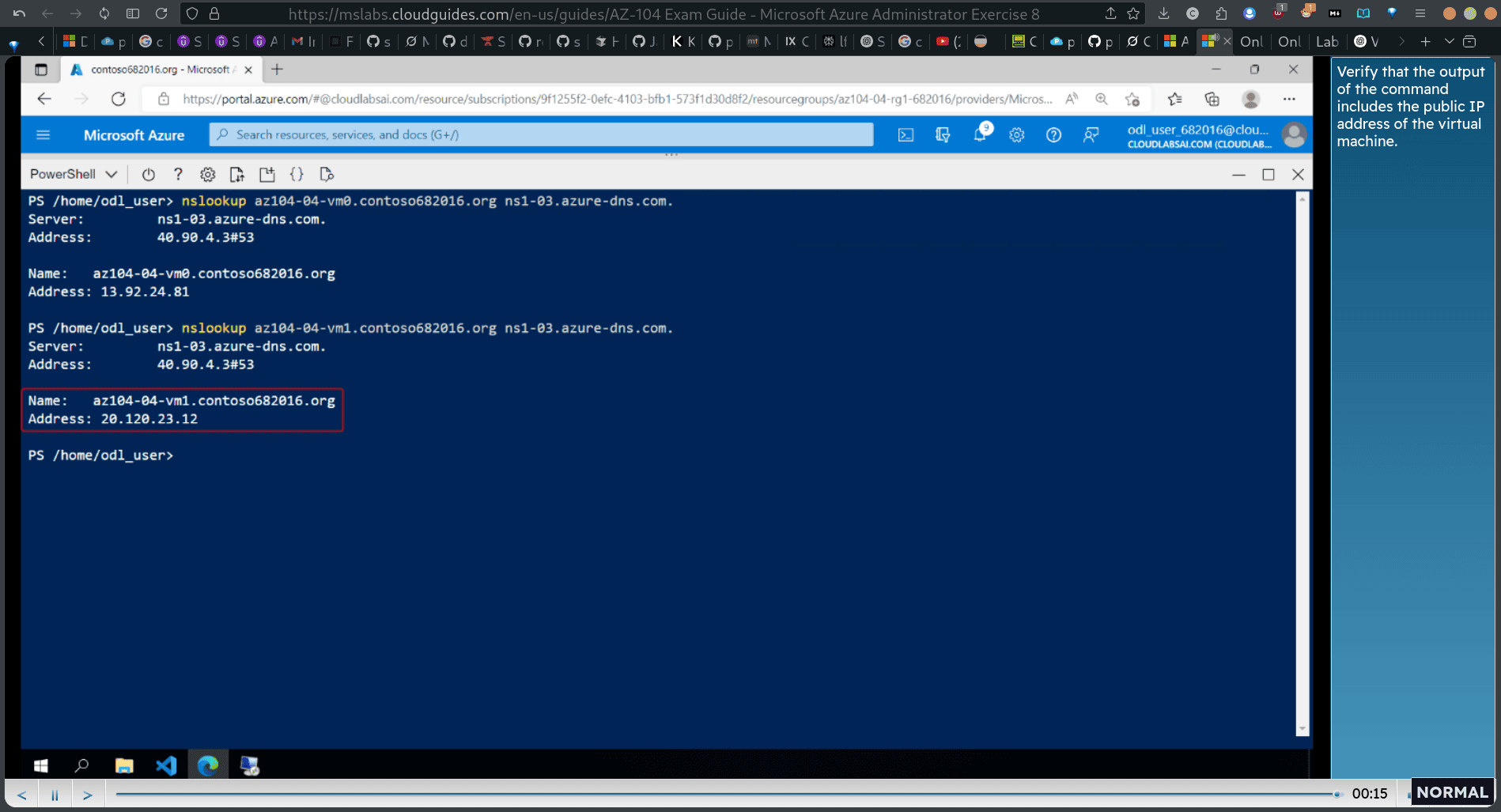
9. Implement inter- site connectivity >
Task 1: Create and configure a virtual network
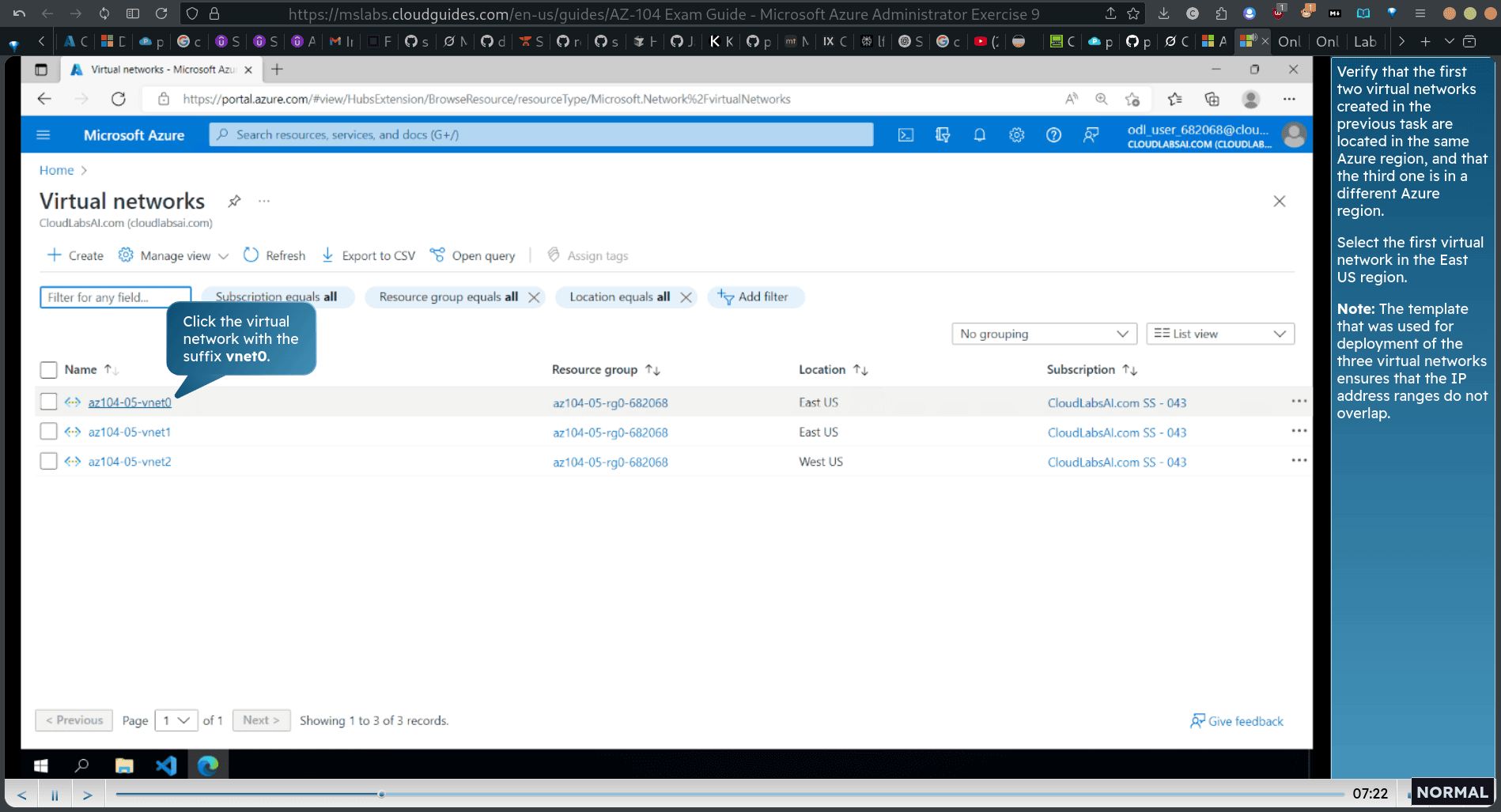
In this first task, you will deploy three virtual machines, each into a separate virtual network, with two of them in the same Azure region and the third one in another Azure region.
cloud shell → power → storage → upload
loop paraetmers → loop template
code . → change the password (seem like a azure policy ? have to change password)
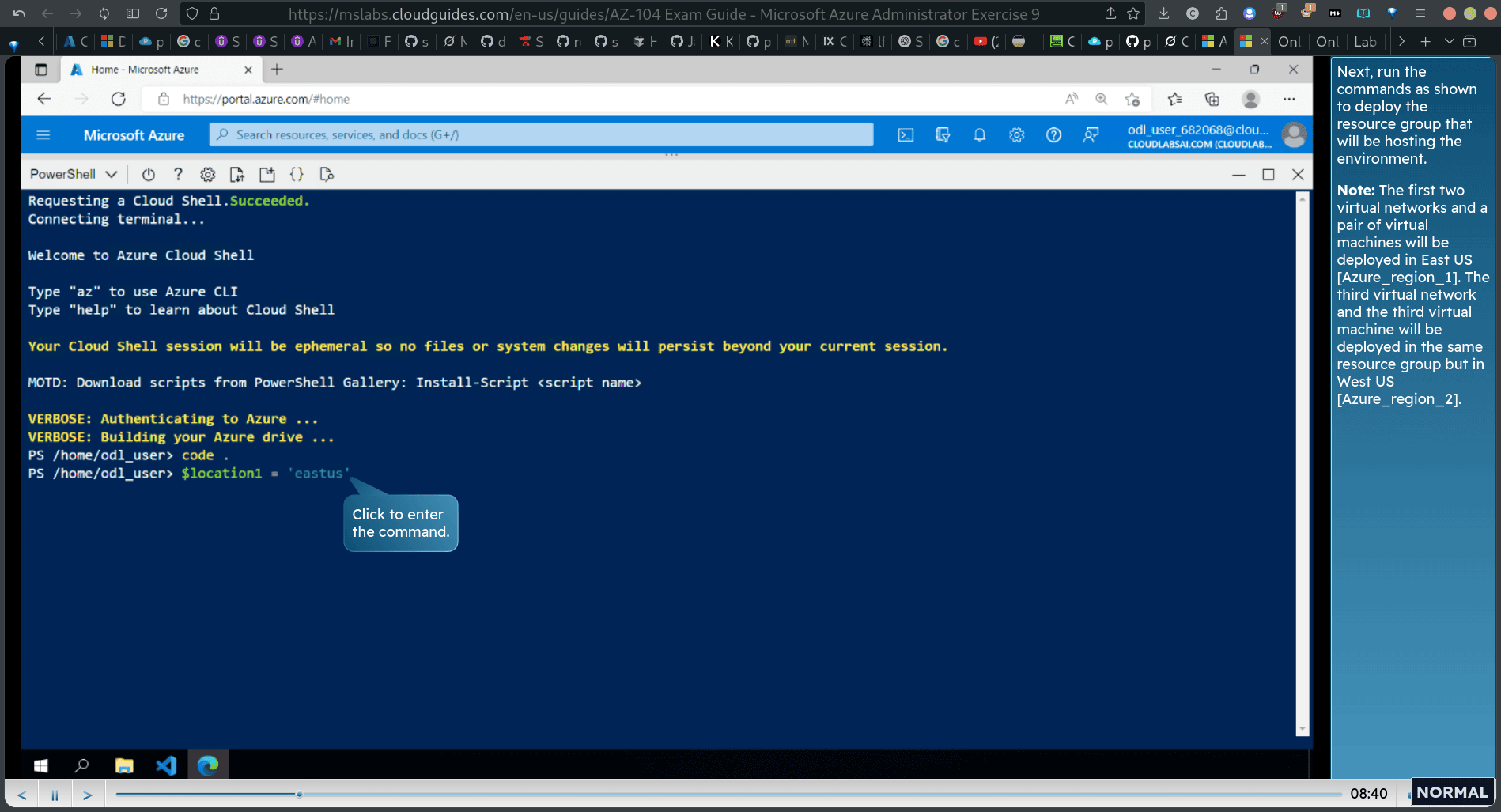
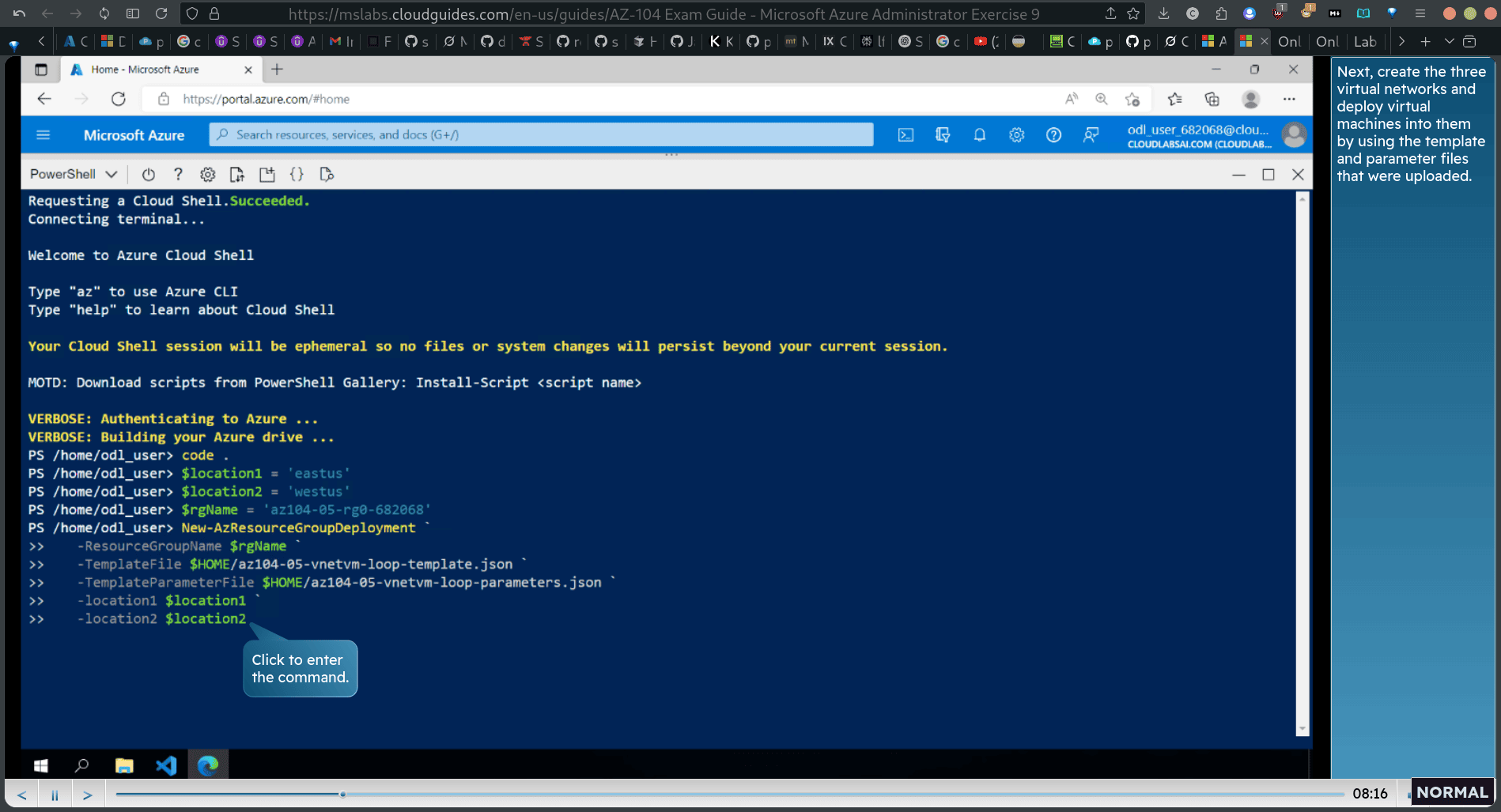
- Note: The first two virtual networks and a pair of virtual machines will be deployed in East US [Azure_region_1]. The third virtual network and the third virtual machine will be deployed in the same resource group but in West US [Azure_region_2].
$location1=‘eastus’
rgName = ‘2z104-85-rg0-682068”
- using loop template :
Task 2: Configure local and global virtual network peering
search Virtual network
verify the cli result:
click → peering → add
name (from .. to )
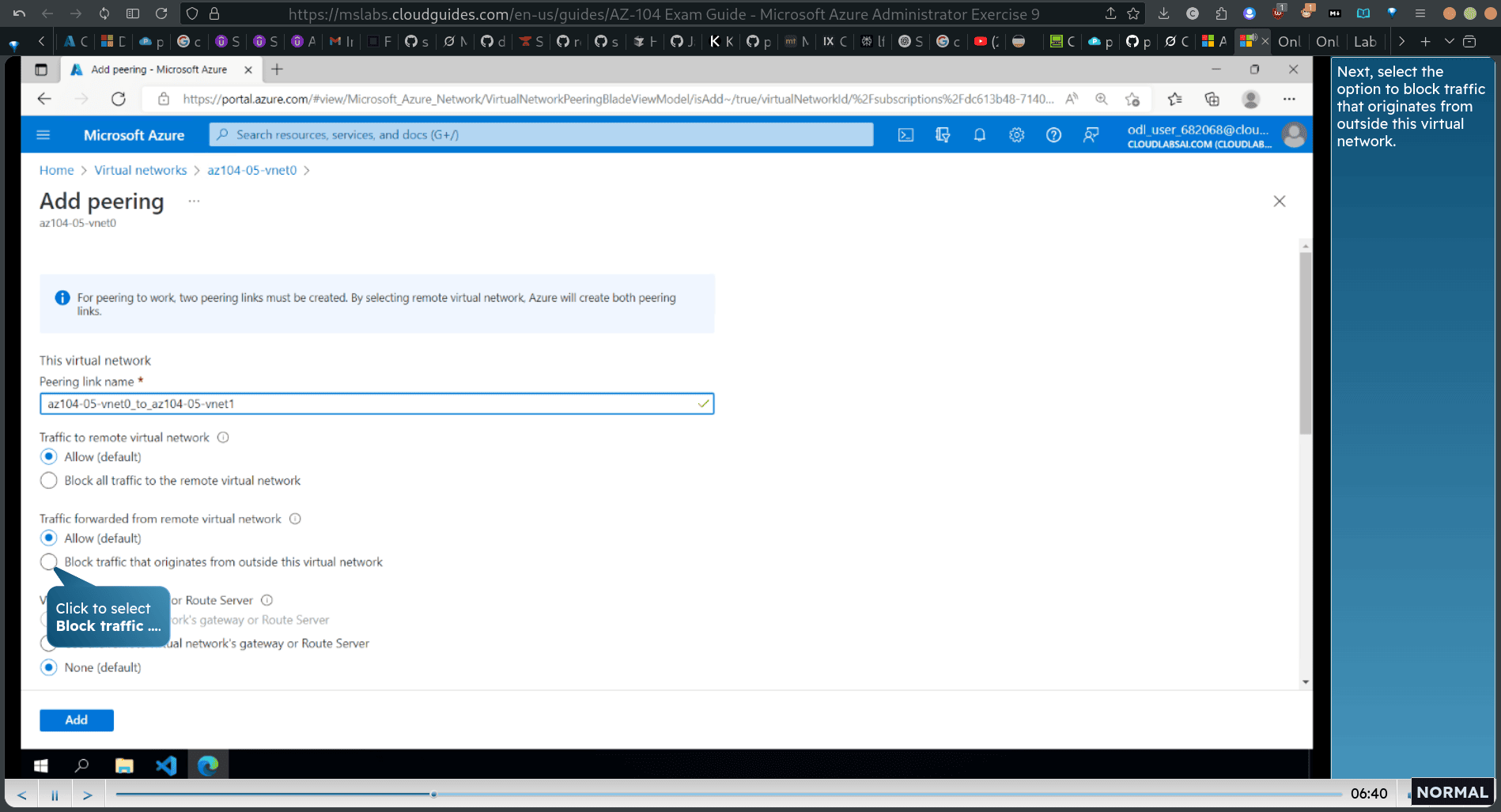
- Next, select the option to block traffic that originates from outside this virtual network.
scroll down: (for remote Virtual network)
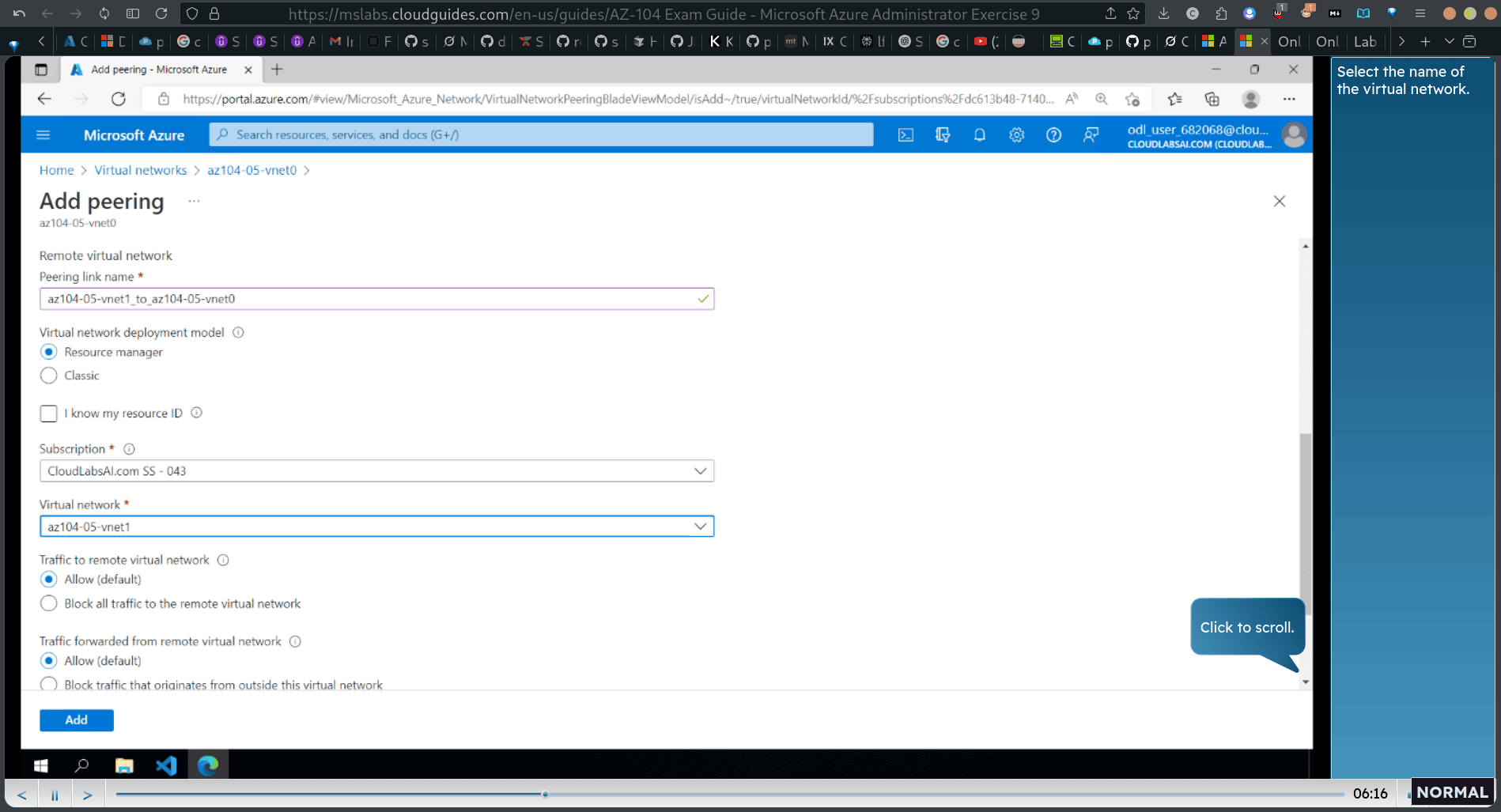
-
block traffic aswell
-
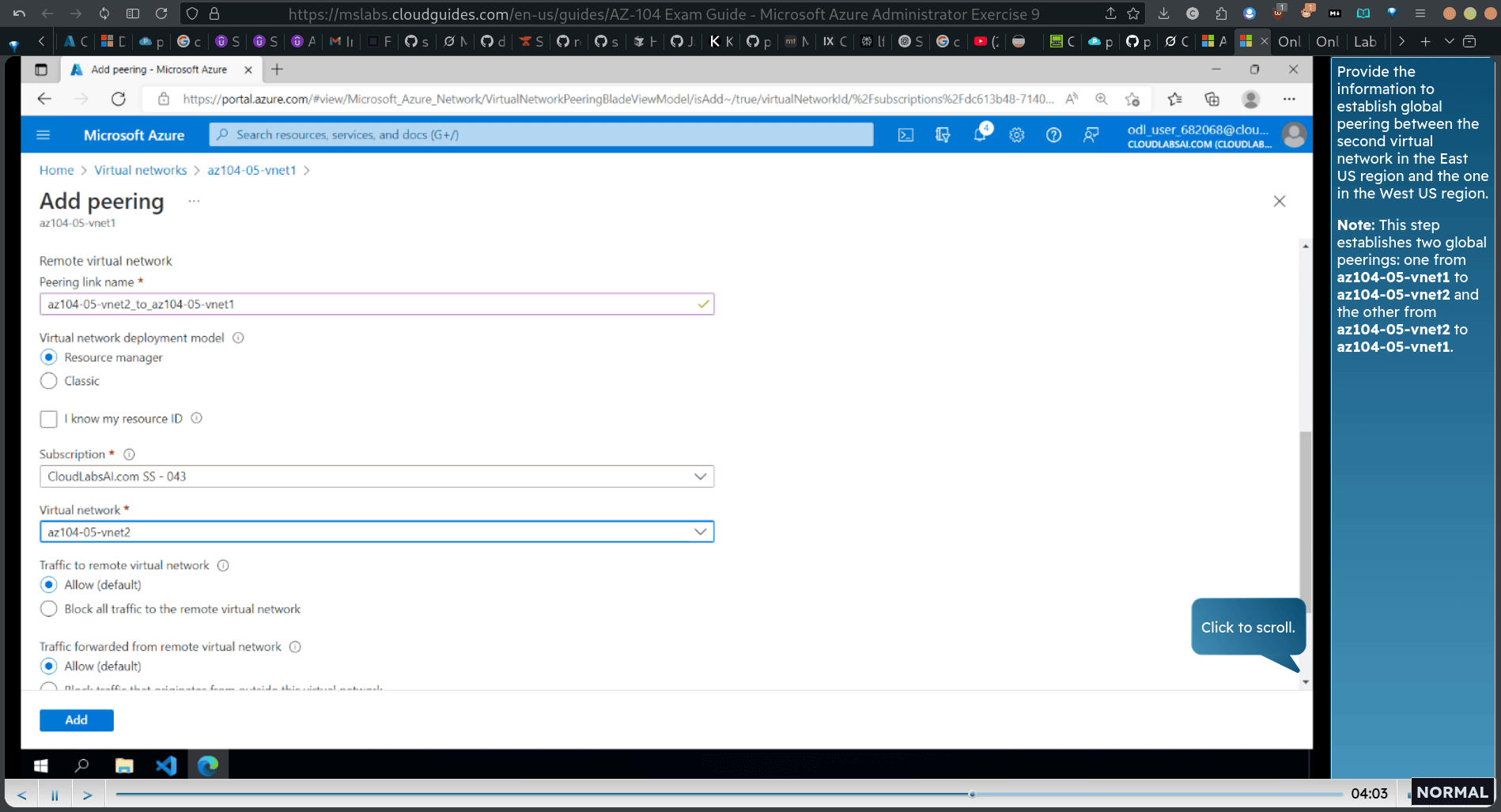
Provide the information fo establish global peering between this virtual network in the East US region and the virtual network in the West US region.
-
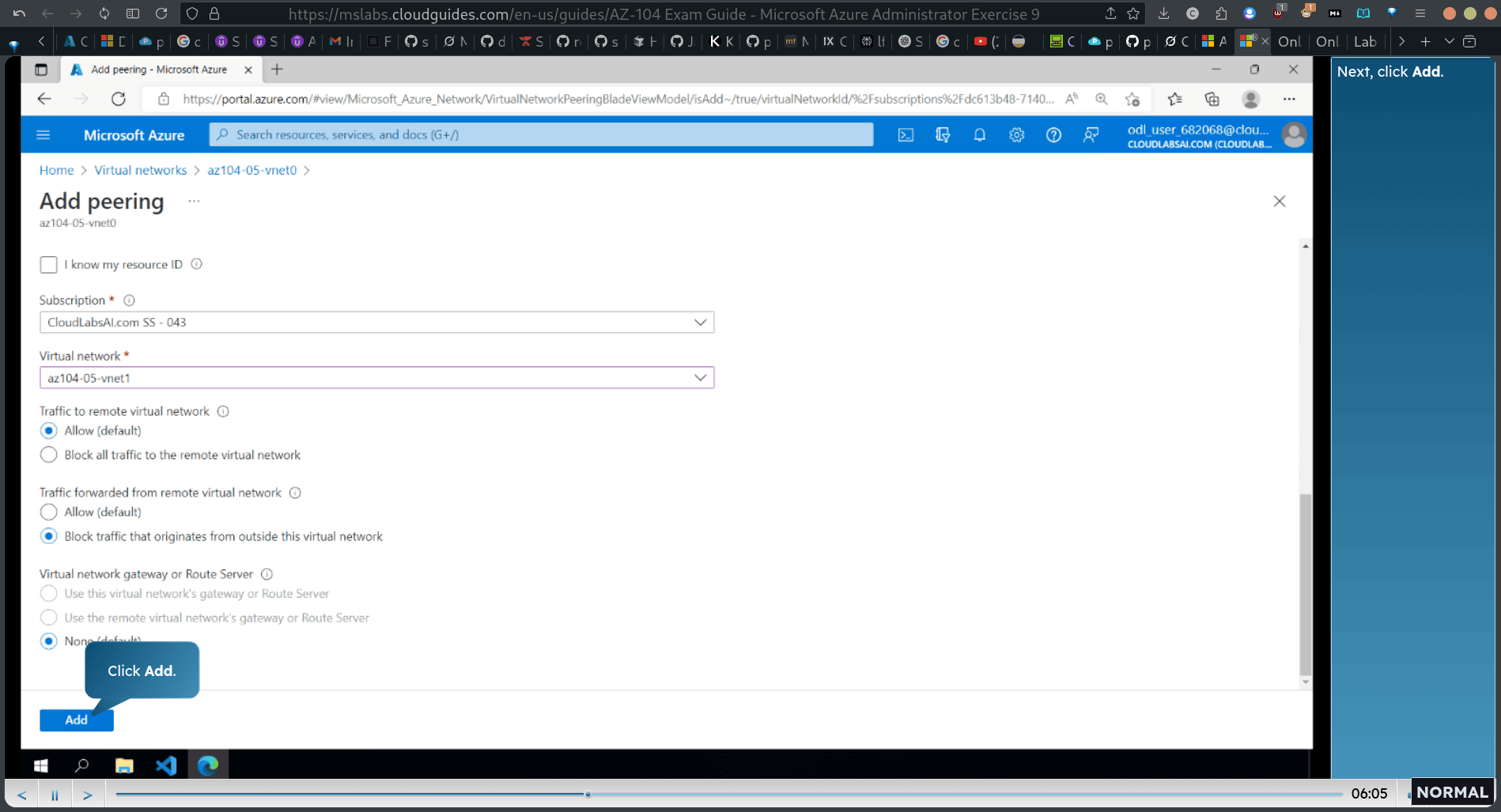
First, provide the peering link name for this virtual network. Note: This step establishes two global peerings: one from az104-05-vnet0 to az104-05-vnet2 and the other from az104-05-vnet2 fo az104-05-vnet0.
block traffic as well
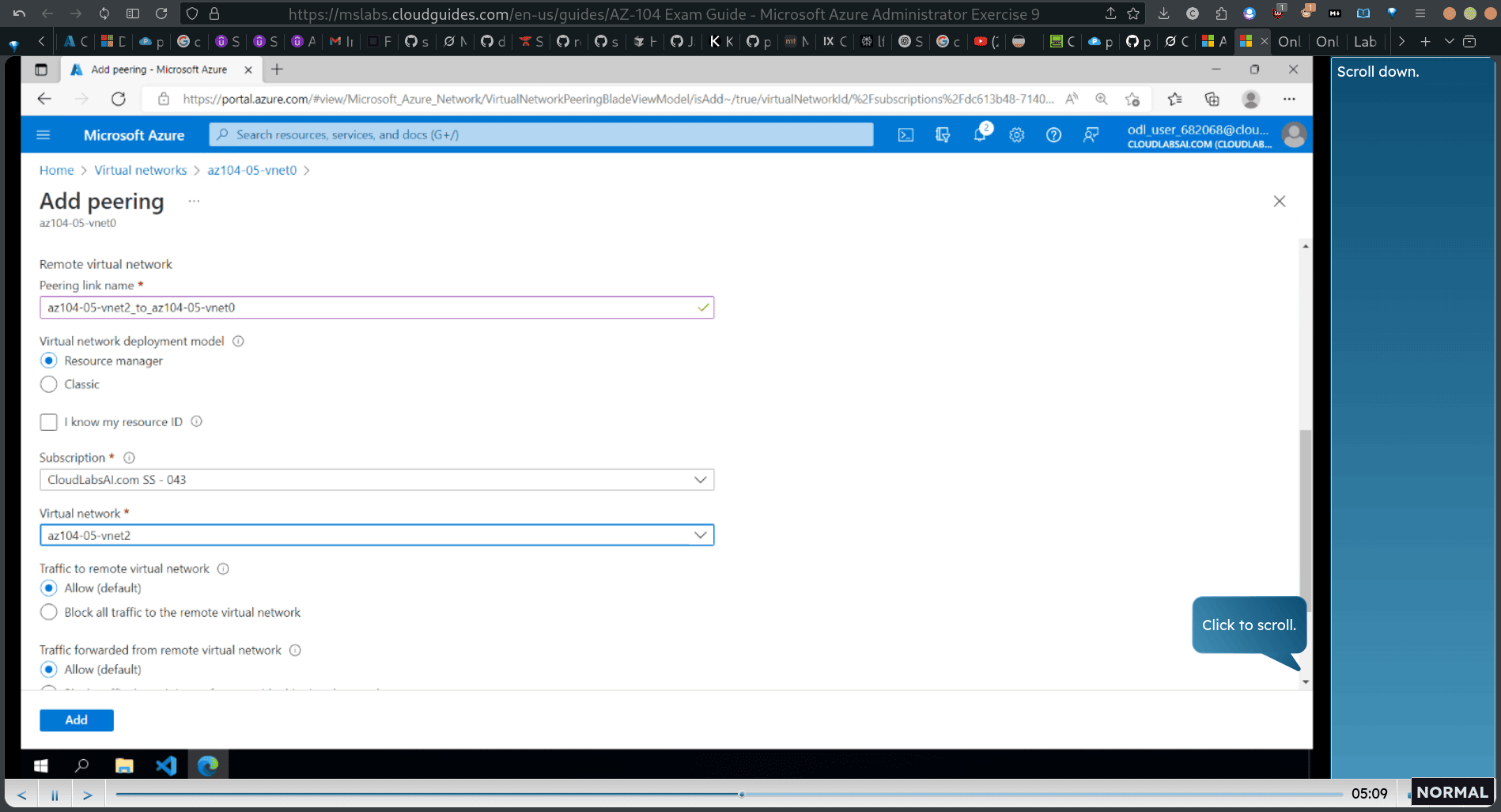
back to network :
 select second vnet1
select second vnet1
-
peering again
-
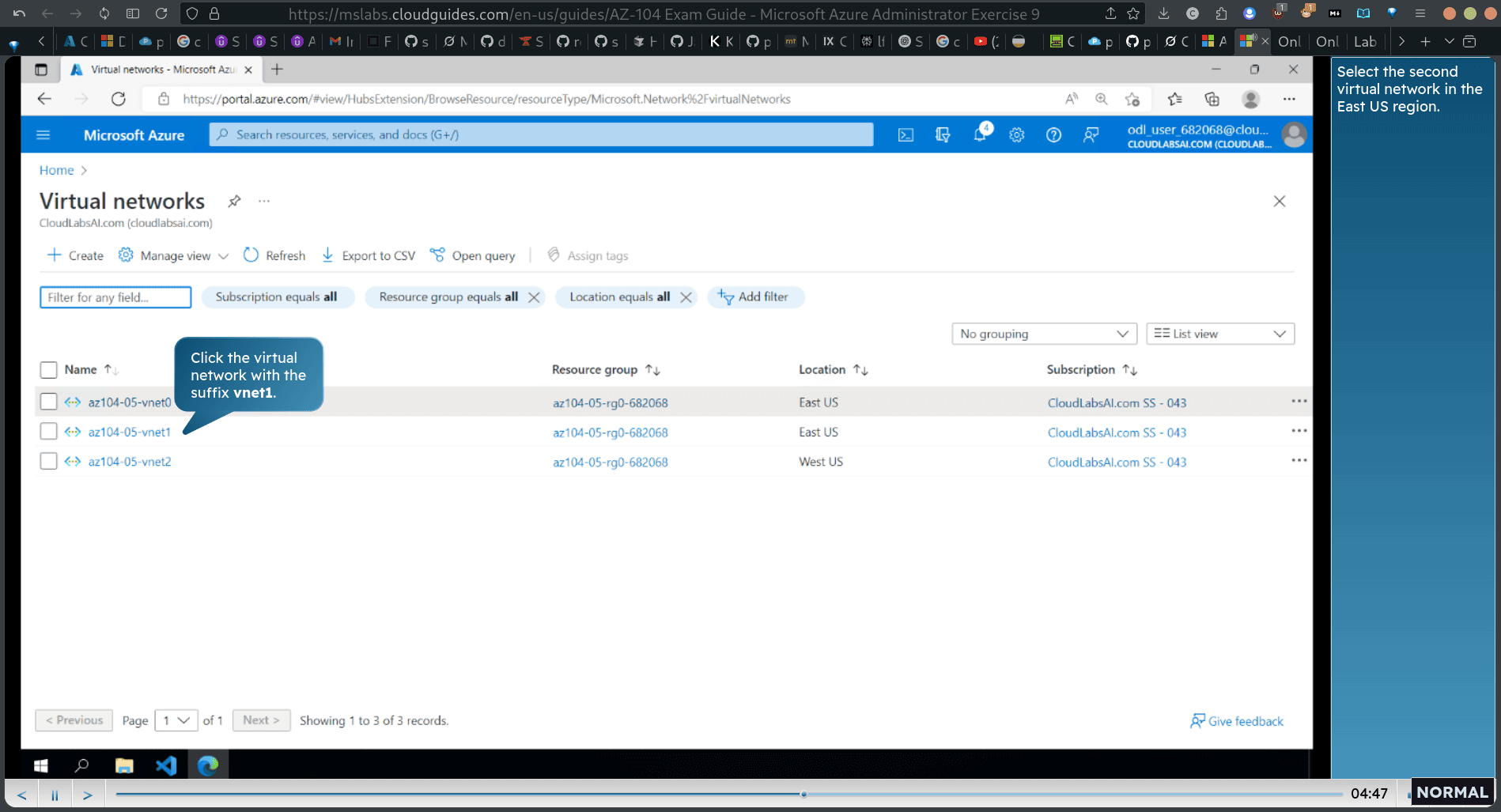
Provide the information fo establish global peering between the second virtual nefwork in the East US region and the one in the West US region.
-
Note: This step establishes two global peerings: one from az104-05-vnet1 to az104-05-vnet2 and the other from az104-05-vnet2 to az104-05-vnet1.
Task 3: Test inter-site connectivity
Search VM select the firts in east us
click onlien → rdp
- run powershell as admin
Test-NetConnection -ComputerName 10.51.0.4 -Port 3389 -InformationLevel ‘Detailed’ Note: The test uses TCP 3389 since this is this port is allowed by default by operating system firewall.
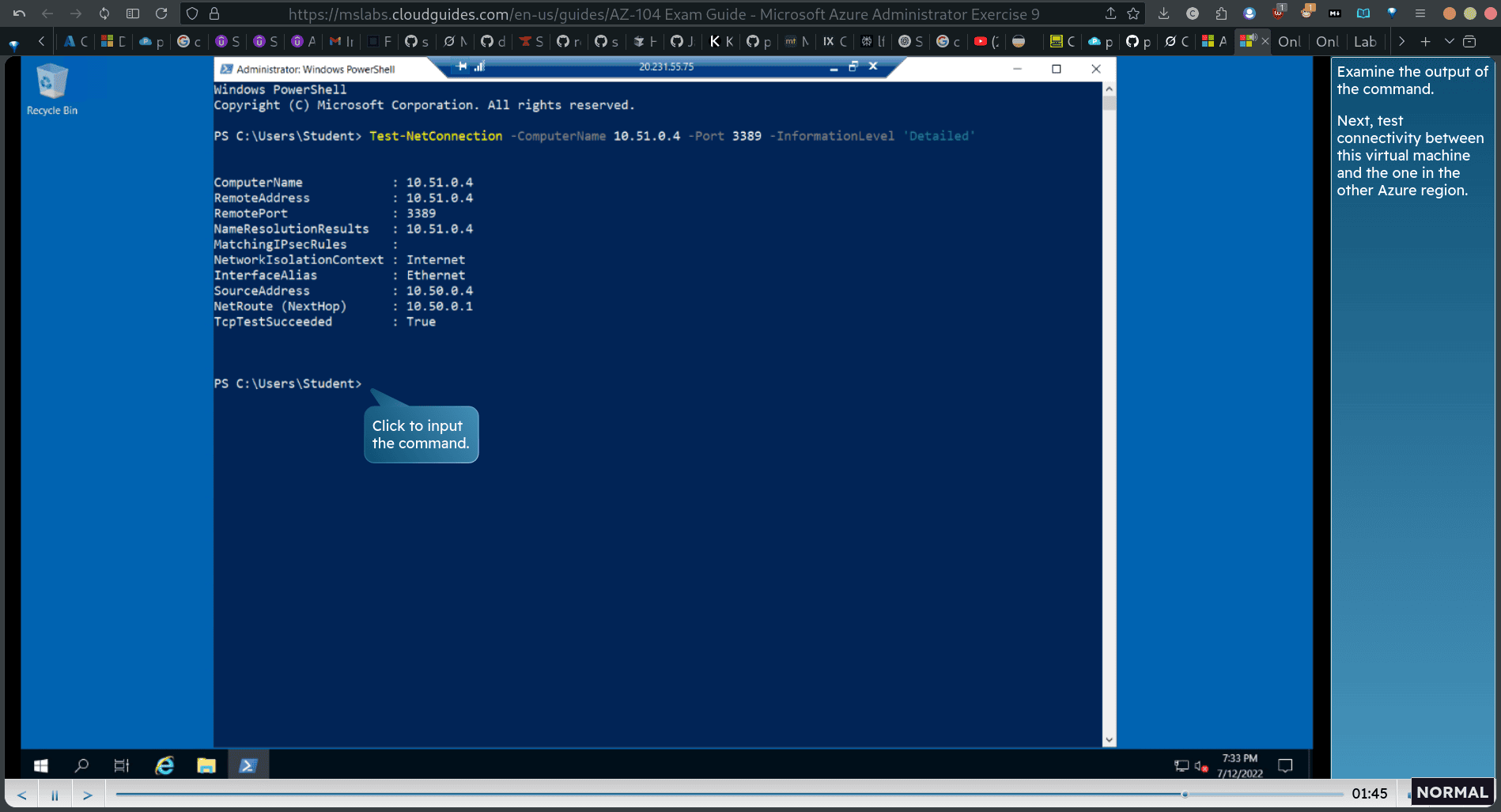 exam the output
exam the output
Test-NetConnection -ComputerName 10.52.0.4 -Port 3389 -InformationLevel ‘Detailed’
 select the second vm
select the second vm
Test-NetConnection -ComputerName 10.52.0.4 -Port 3389 -InformationLevel ‘Detailed’
10. Implement traffic management >
Task 1: Deploy virtual machines
- The first two will reside in a hub virtual network, and the remaining two will reside in separate spoke virtual networks.
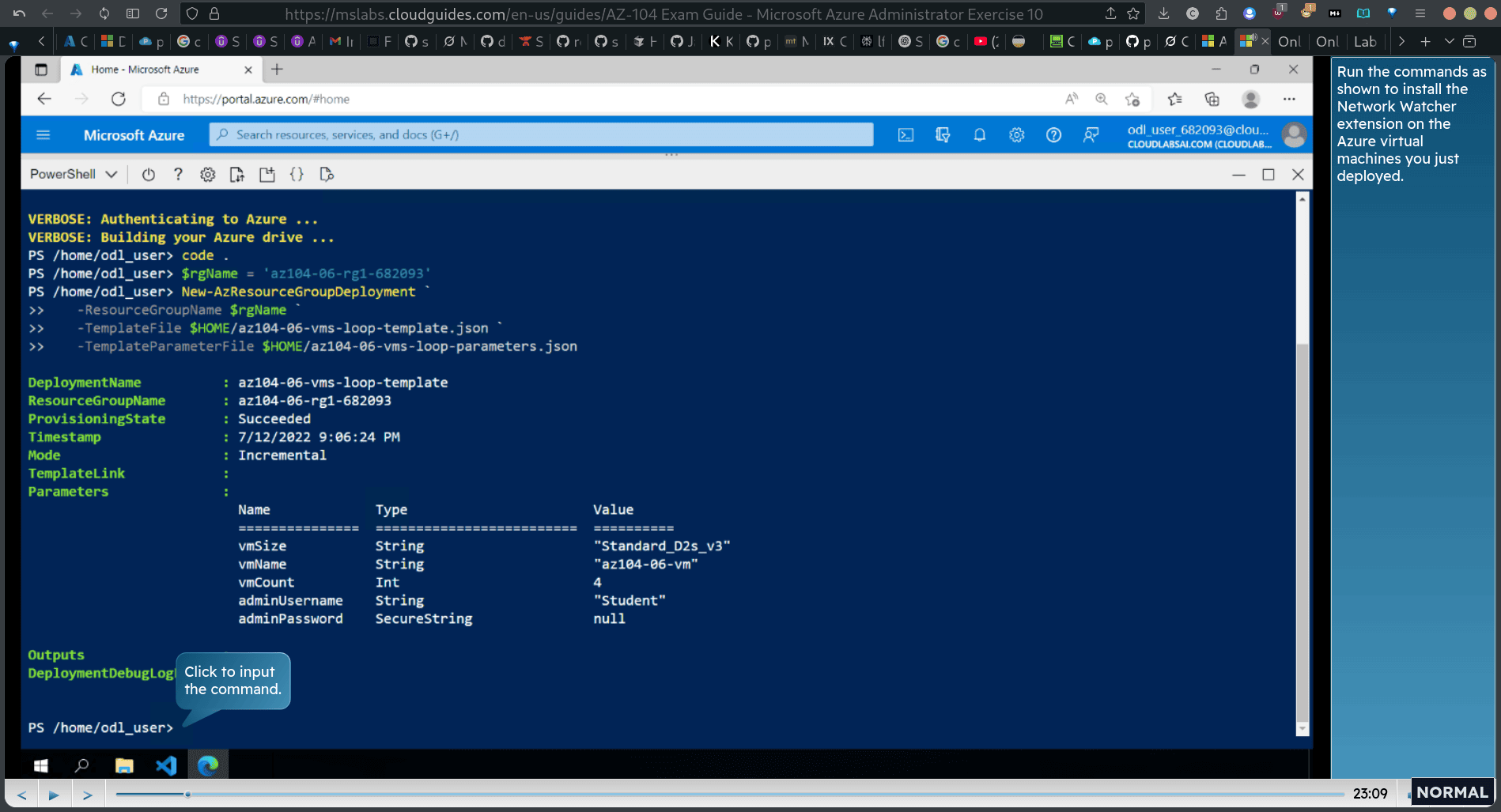
upload loop json , change the password , then
New-AzResourceGroupDeployment
 rgName).location
rgName).Name
rgName).location
rgName).Name
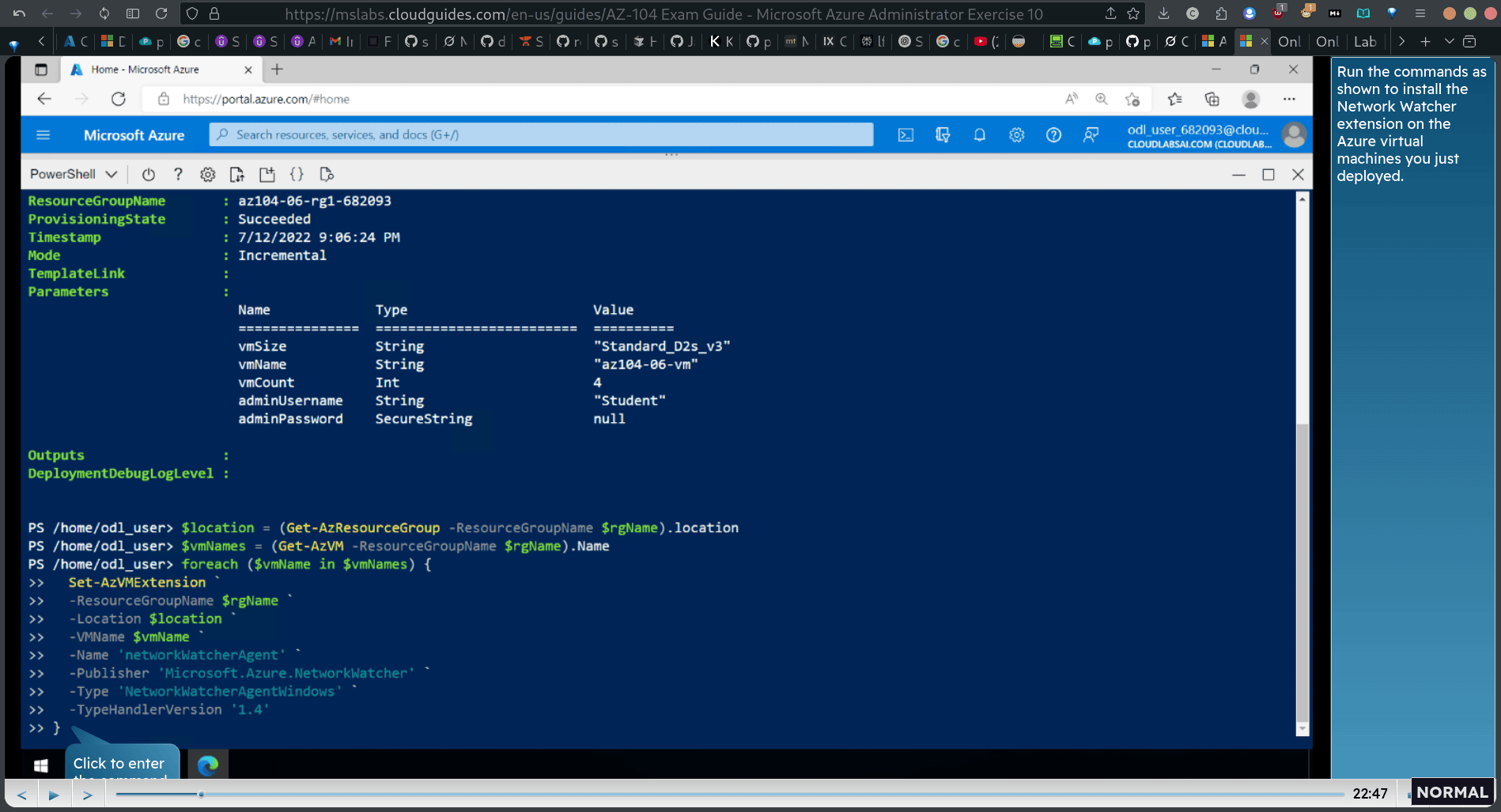
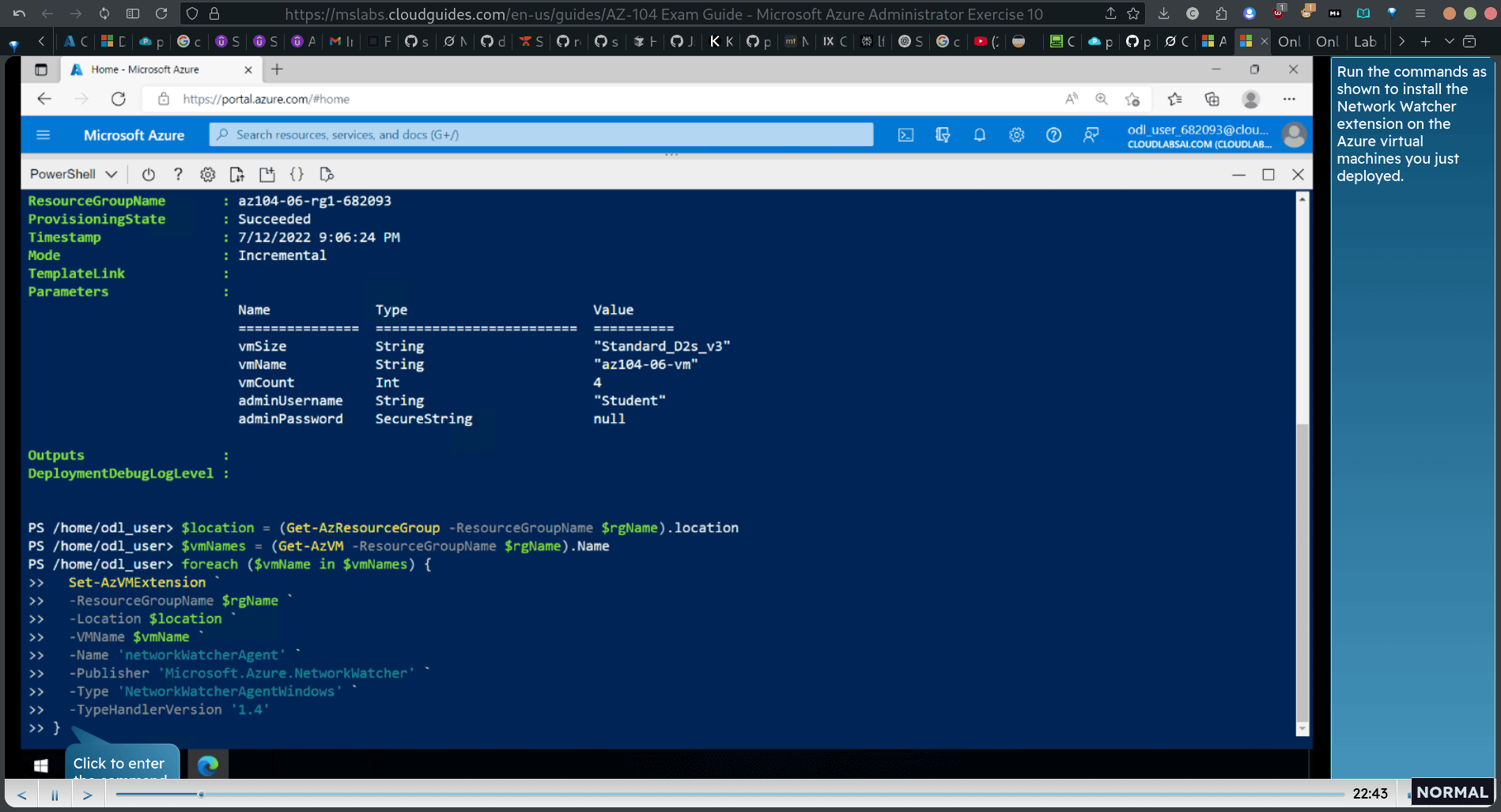
foreach (vmNames) {
Set-AzVMeExtension ° -ResourceGroupName location _ -VMName $vmName _ -Name ‘networkWatcherAgent’ ° -Publisher ‘Microsoft.Azure.NetworkWatcher -Type ‘NetworkWatcherAgentilindows’ * -TypeHandlerVersion ‘1.4’
Task 2: Configure the hub and spoke network topology
virtual netowrk → first → scroll peering
- between the hub virtual network and the first spoke virtual nefwork.
- Note: This step establishes two local peerings: one from az104-06-vnet01 to az104-06-vnet2 and the other from az104-06-vnet2 fo az104-06-vnet0l1.
Note: This step establishes two local peerings: one from az104-06-vnet01 to az104-06-vnet3 and the other from az104-06-vnet3 to az104-06-vnet01, which will complete the hub and spoke topology.
- above operation block traffic as well
Task 3: Test transitivity of virtual network peering
using network watcher
 → connection troubleshot
→ connection troubleshot
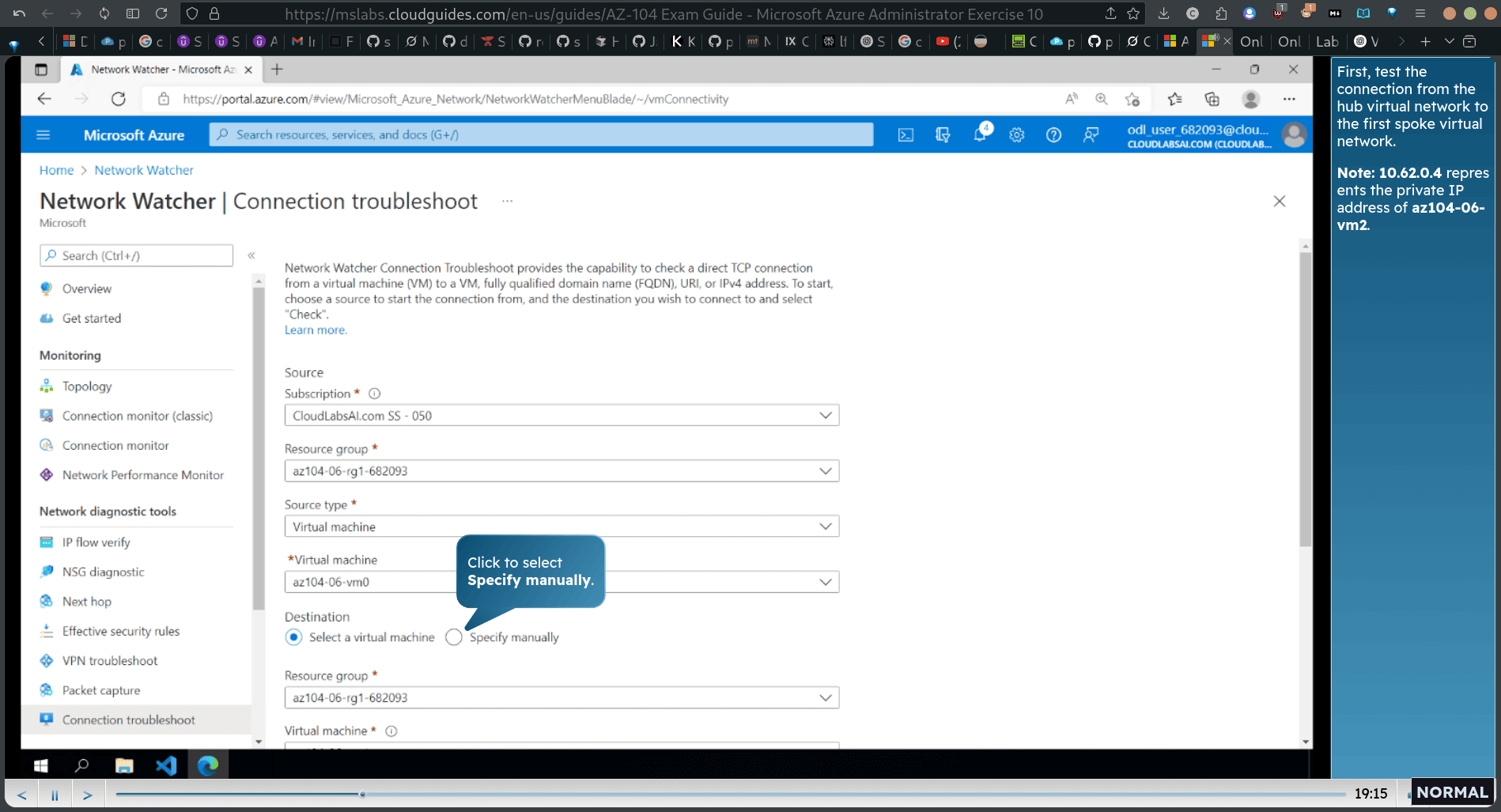
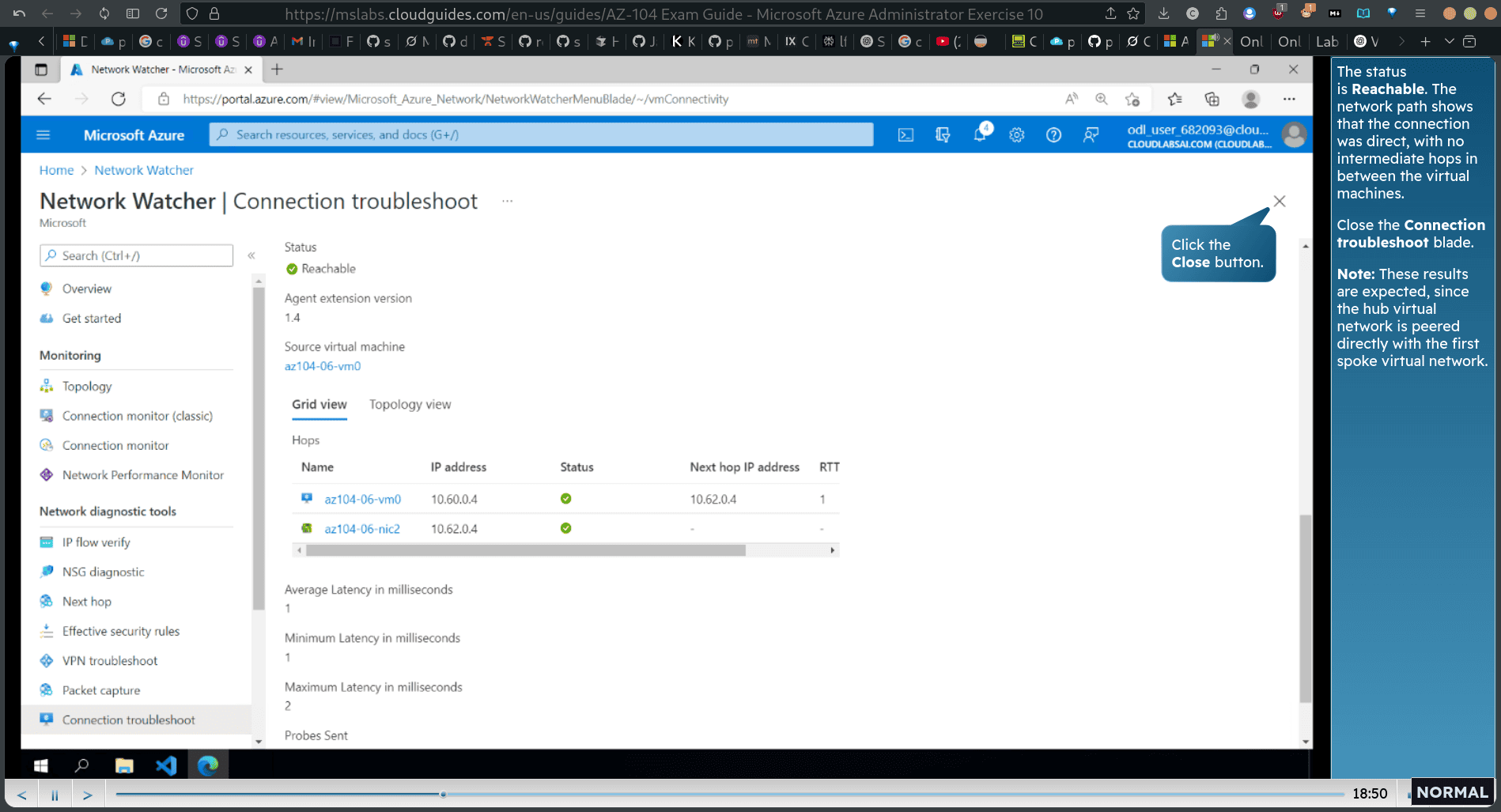
- First, test the connection from the hub virtual network to the first spoke virtual network.
- Note: 10.62.0.4 repres ents the private IP address of az104-06- vm2.
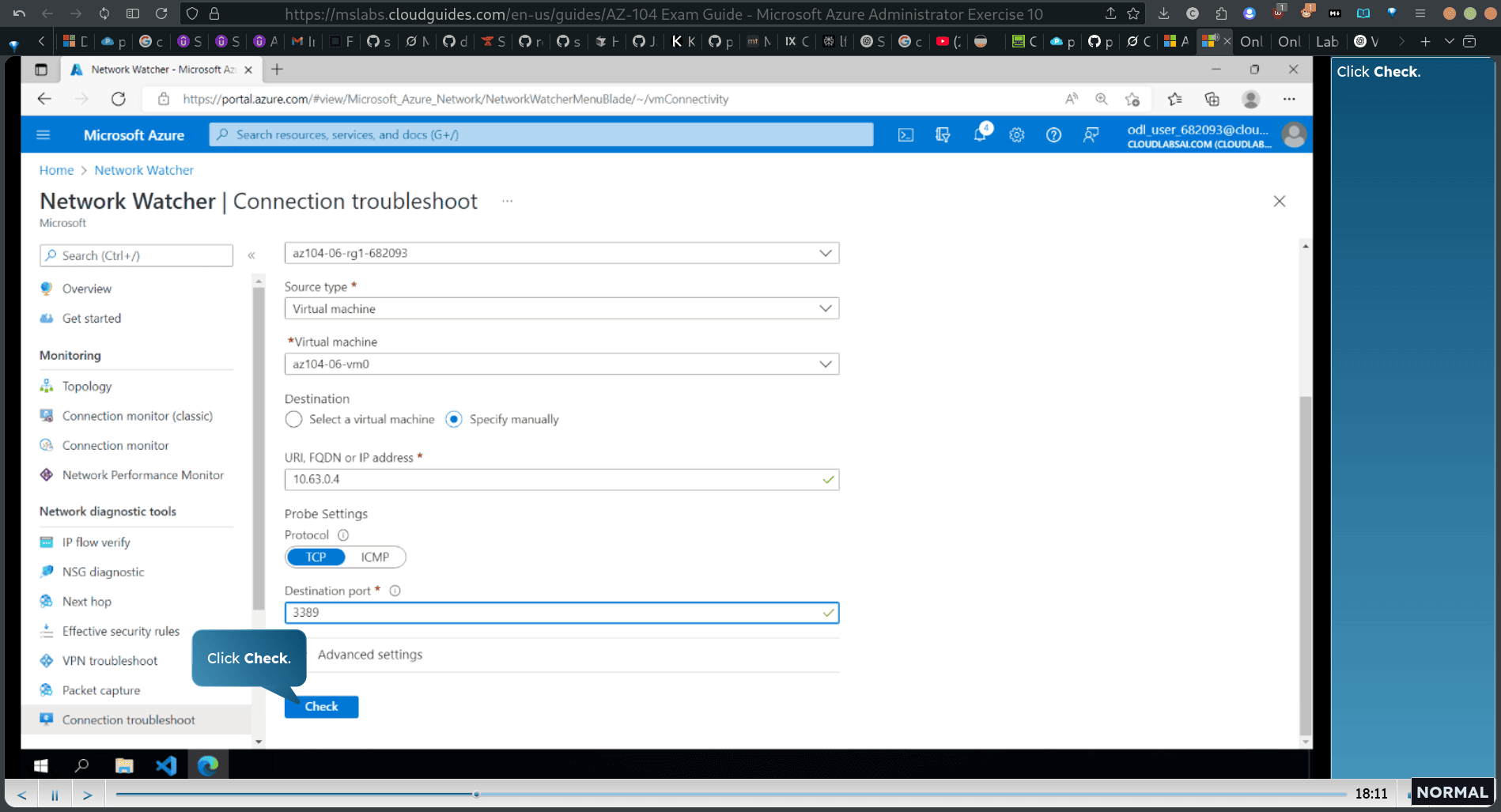
destination → manually → private ip of vm2
destination port → 3382 rdp
 grid view
grid view
- The status is Reachable. The network path shows that the connection was direct, with no intermediate hops in between the virtual machines.
network watcher → connection troubleshoot
Next, test the connection from the hub virtual network to the second spoke virtual network. Note: 10.63.0.4 repre sents the private IP address of az104-06- vm3.
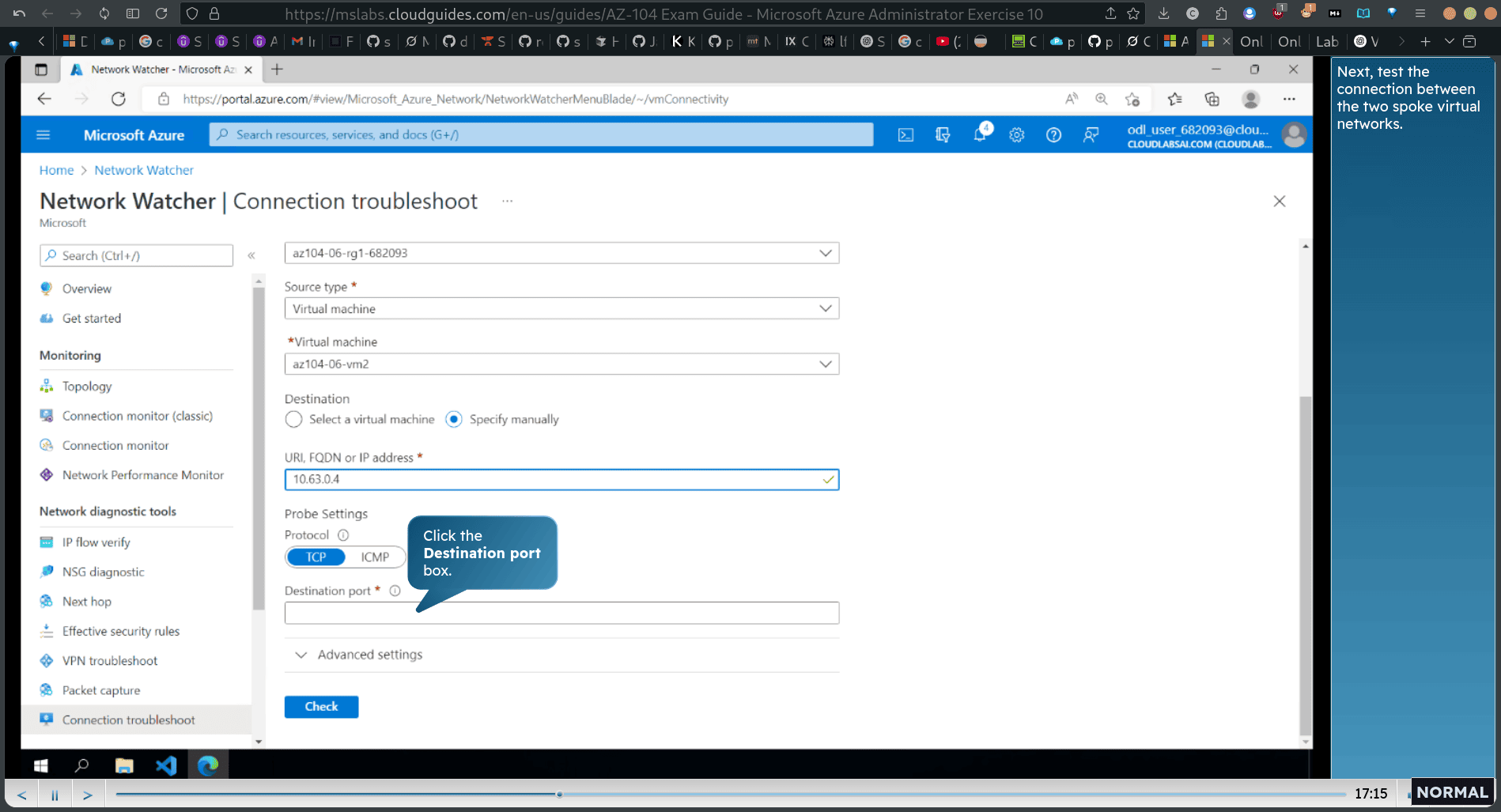 vm2 → private ip of vm3
vm2 → private ip of vm3
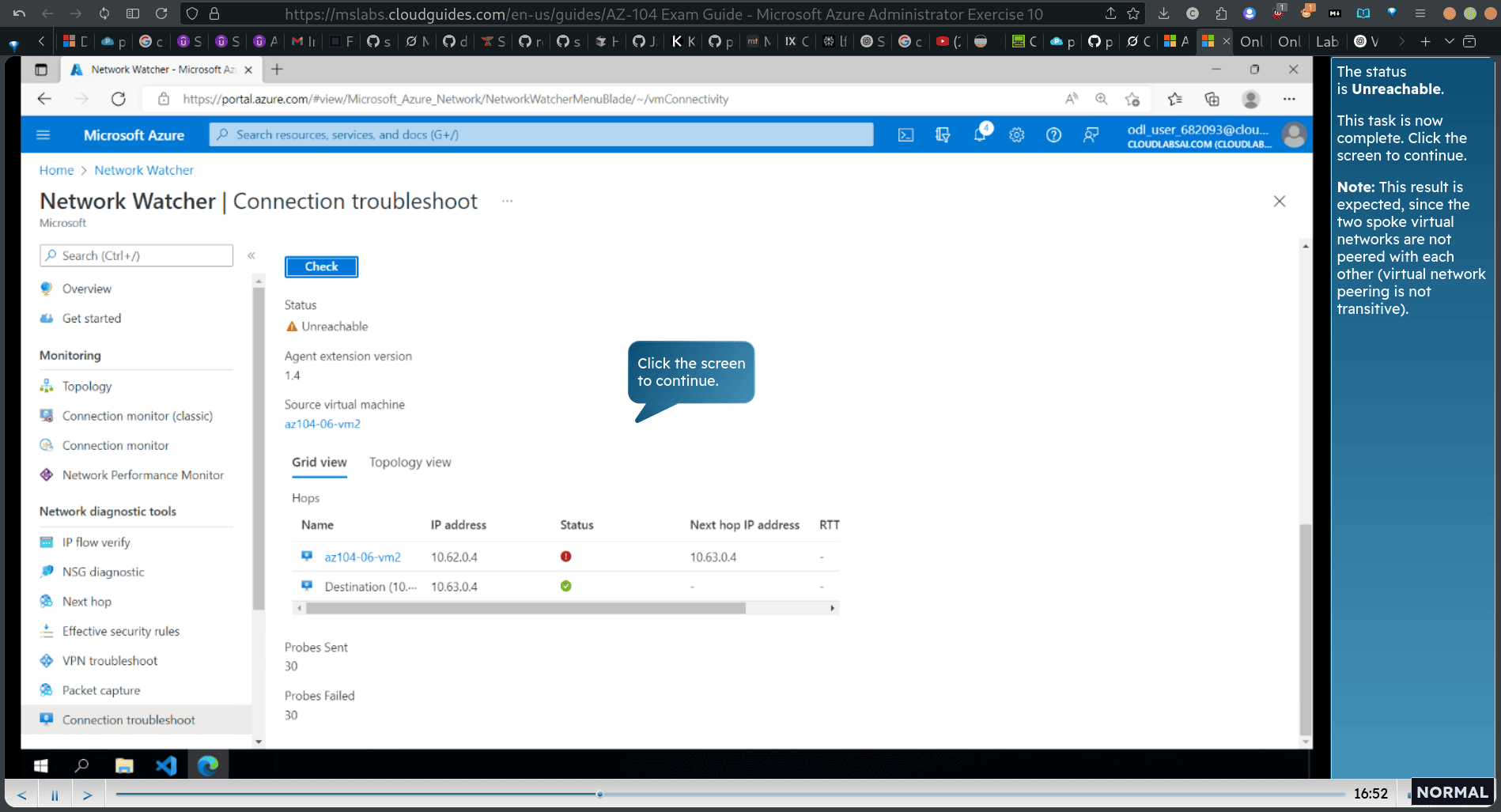
- The status is Unreachable. This task is now complete. Click the screen to continue.
alarm result :
Task 4: Configure routing in the hub and spoke topology
search vm → frist vm0→ networking → network interface link
ip config → ip forwarding → enable
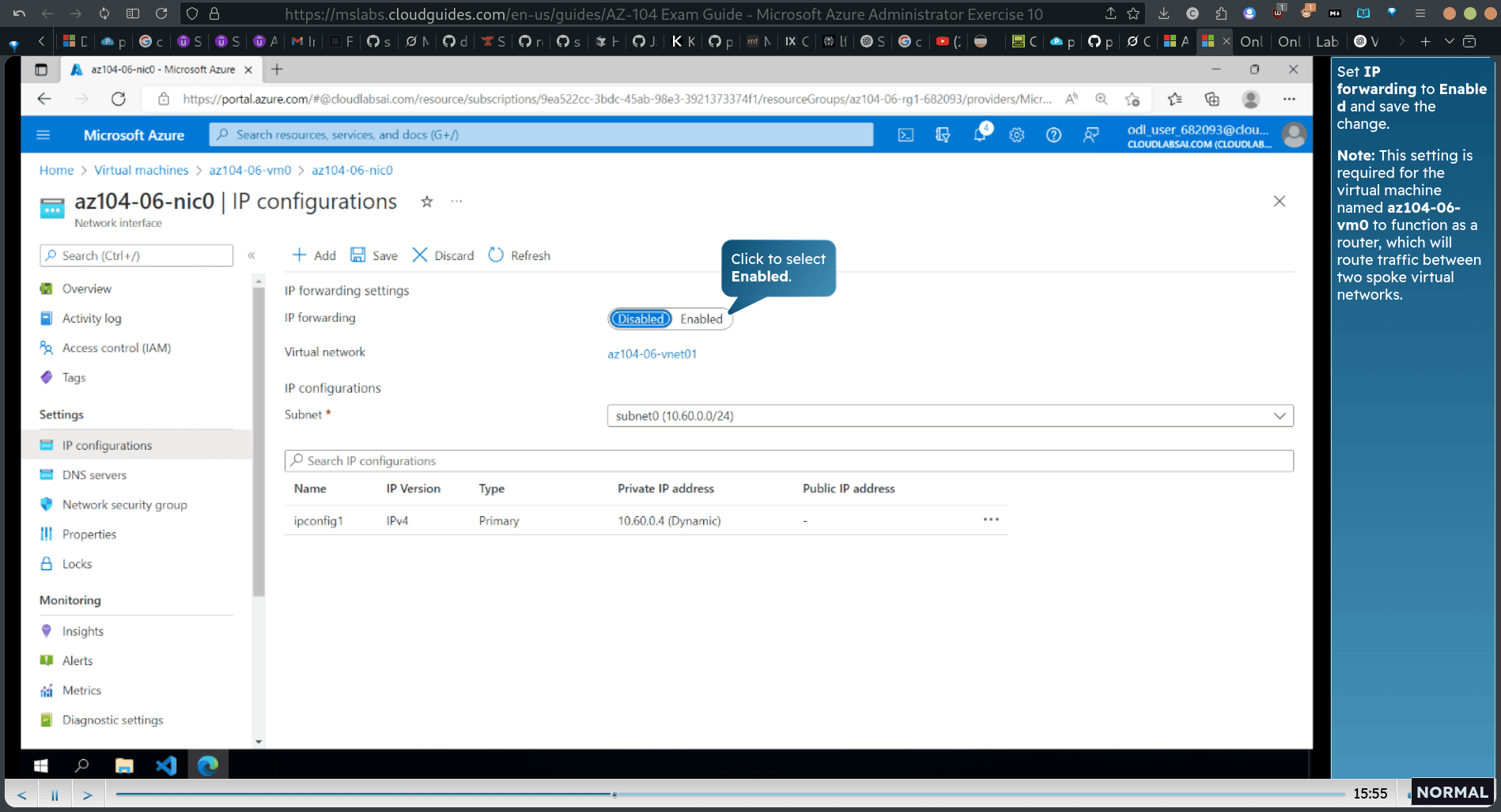
-
Set IP forwarding to Enable d and save the change.
-
Note: This setting is required for the virtual machine named az104-06- vm0 to function as a router, which will route traffic between two spoke virtual networks.
→ click save
→ click vm0 overview → run command (under operation )
 run commad → powershell (turn it into router lol)
run commad → powershell (turn it into router lol)
Install-WindowsFeature RemoteAccess -IncludeManagementTools
Run the script as shown fo install the Remote Access Windows Server role.
back , and click run powershell script
Install-WindowsFeature -Name Routing -IncludeManagementTools -IncludeAllSubFeature Install-WindowsFeature -Name “RSAT-RemoteAccess-Powershell” TInstall-RemoteAccess -VpnType RoutingOnly Get-NetAdapter | Set-NetIPInterface -Forwarding Enabled
Run the script as shown fo install the Routing role service.
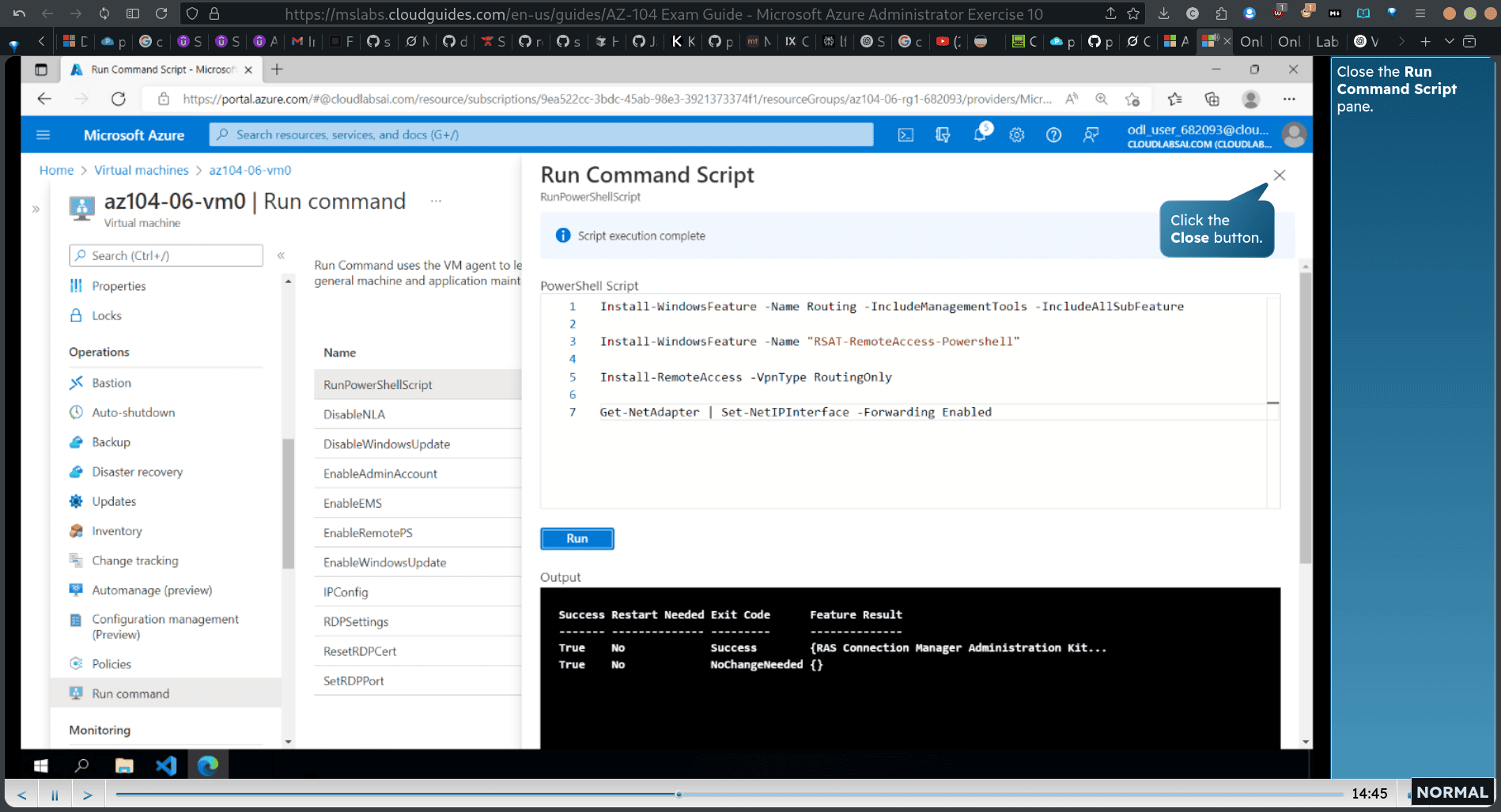
- Next, you’ll create and configure user- defined routes on the spoke virtual networks.
Search for and select Route tables.
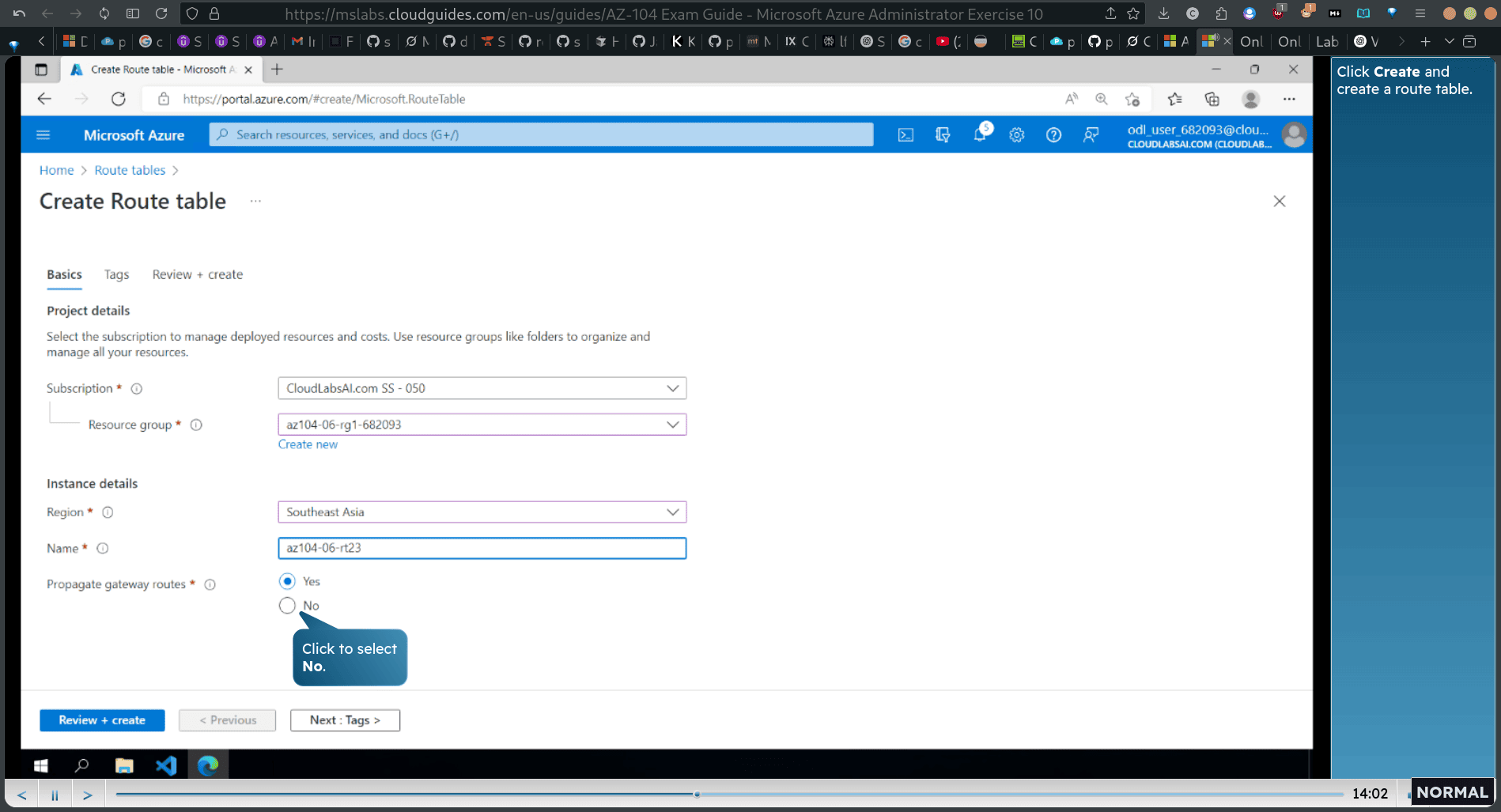
- In Azure Route Tables, the setting “Propagate gateway routes” controls whether routes from a Virtual Network Gateway (VPN or ExpressRoute) are automatically added to your custom route table.
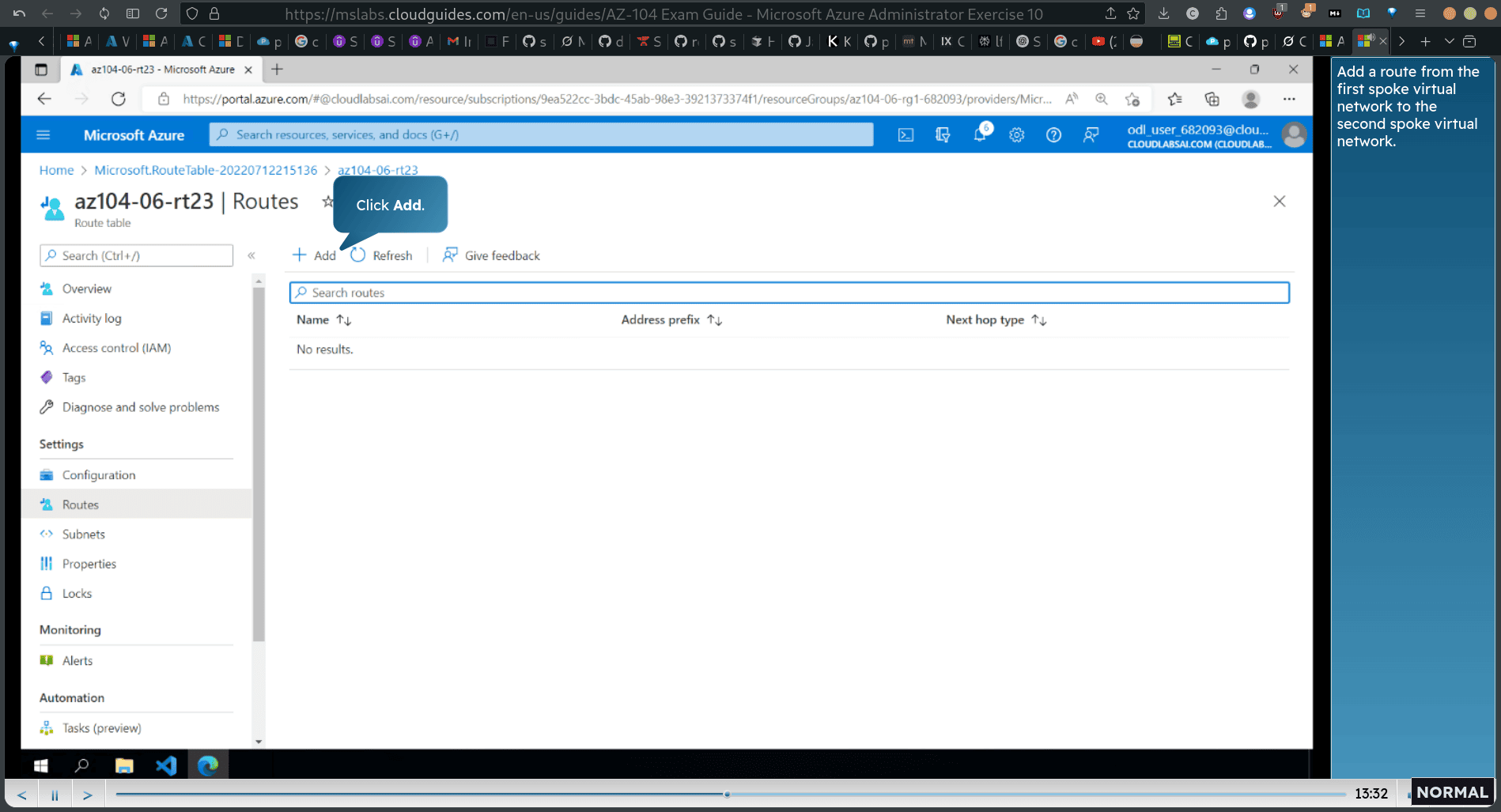
- Add a route from the first spoke virtual nefwork to the second spoke virtual network.
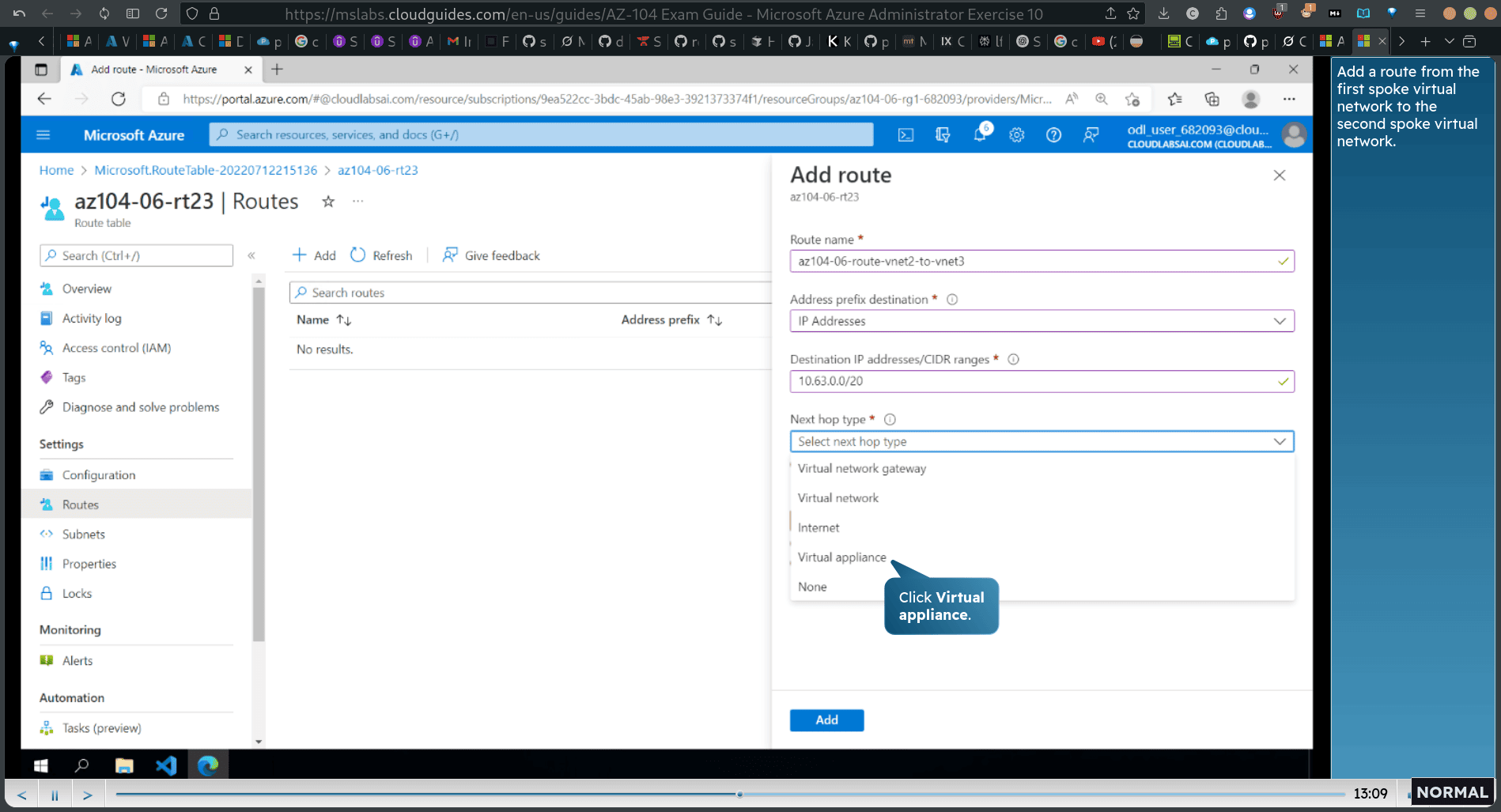 Next hop type
Select next hop type
Virtual network gateway
Virtual network
Internet
Virtual appliance
None
Next hop type
Select next hop type
Virtual network gateway
Virtual network
Internet
Virtual appliance
None
🔹 1. Virtual Network Gateway
-
Used when: You want traffic to go through a VPN gateway or ExpressRoute gateway.
-
Example: Sending traffic to an on-premises network via VPN.
-
Use case:
- Destination:
192.168.0.0/16 - Next hop: Virtual Network Gateway → Tells Azure: “Send this traffic to my on-premises network through the gateway.”
- Destination:
🔹 2. Virtual Network
- Used when: Traffic should stay within the Azure virtual network.
- Effect: Tells Azure: “This traffic is local. Keep it inside the VNet.”
- Use case: You don’t usually set this manually because VNet-to-VNet traffic is routed automatically by Azure. But in complex setups, you might override a more specific route.
🔹 3. Internet
-
Used when: You want traffic to go directly to the internet.
-
Effect: Sends packets out through the Azure default internet gateway.
-
Use case:
- Destination:
0.0.0.0/0 - Next hop: Internet → All outbound traffic not matching any other route goes to the internet.
- Destination:
🔹 4. Virtual Appliance
-
Used when: You have a Network Virtual Appliance (NVA), such as:
- A firewall
- A router (e.g., a Fortinet, Palo Alto, or pfSense VM)
-
You need to specify the IP address of that NVA.
-
Use case:
- Destination:
0.0.0.0/0 - Next hop: Virtual Appliance
- IP address:
10.40.0.4→ Routes all internet-bound traffic through your firewall first.
- Destination:
✅ This is what your tutorial likely uses — to inspect/filter traffic through a custom appliance (for learning or security).
🔹 5. None
-
Used when: You want to block traffic to a specific range.
-
Effect: Azure drops the traffic (no next hop).
-
Use case:
- Destination:
10.0.0.0/8 - Next hop: None → Blocks traffic to that network. Used in network segmentation or security policies.
- Destination:
🧠 Summary Table
| Next Hop Type | Sends Traffic To… | Typical Use |
|---|---|---|
| Virtual Network Gateway | VPN/ExpressRoute gateway to on-premises | Hybrid networking |
| Virtual Network | Inside same Azure VNet | Local routing override |
| Internet | Azure internet gateway | Public outbound |
| Virtual Appliance | Your own firewall/router VM | Custom inspection or control |
| None | Nowhere (drop traffic) | Blocking or isolating |
Great! Let’s break down this route:
🧭 Route Details
- Destination IP/CIDR:
10.63.0.0/20 - Next hop type: Virtual appliance
- Next hop address:
10.60.0.4
🧠 What This Route Means
“Any traffic going to the IP range
10.63.0.0 – 10.63.15.255should be sent to the virtual appliance at IP10.60.0.4.”
✅ Why it’s configured this way
This is a custom route in Azure, probably set up for traffic inspection or control.
The reasons behind it likely include:
🔸 1. Security filtering
10.60.0.4is likely a Network Virtual Appliance (NVA) (e.g., a firewall).- Traffic destined for
10.63.0.0/20(another subnet or VNet) is forced to pass through the firewall for inspection, logging, or policy enforcement.
🔸 2. Centralized routing
-
All routes to certain networks (like
10.63.0.0/20) are sent to a central appliance. -
This allows for:
- Traffic monitoring
- Access control
- Packet filtering
- NAT or proxy services
🔸 3. Hub-and-spoke network design
10.60.0.4is likely in the hub VNet.10.63.0.0/20may be in a spoke VNet.- This route forces spoke-to-spoke or spoke-to-on-prem traffic to go via the hub, using
10.60.0.4as a gateway.
🔐 Why not route directly?
Azure by default allows traffic between subnets in the same VNet, or between peered VNets if allowed. However, this route overrides that to:
- Enforce security policies
- Apply custom logic via the appliance
- Enable logging, IDS/IPS, or DLP controls
📘 Visual Representation
[ VM in Subnet A ]
|
|--(Route to 10.63.0.0/20)-->
| via Virtual Appliance (10.60.0.4)
|
[ Firewall or Router VM (NVA) ]
|
|--> Forwards traffic to 10.63.0.0/20
🚦 Final Note
- This type of setup is common in production-grade Azure environments where segmentation and security are critical.
- Without this route, traffic might bypass security controls and go directly to
10.63.0.0/20.
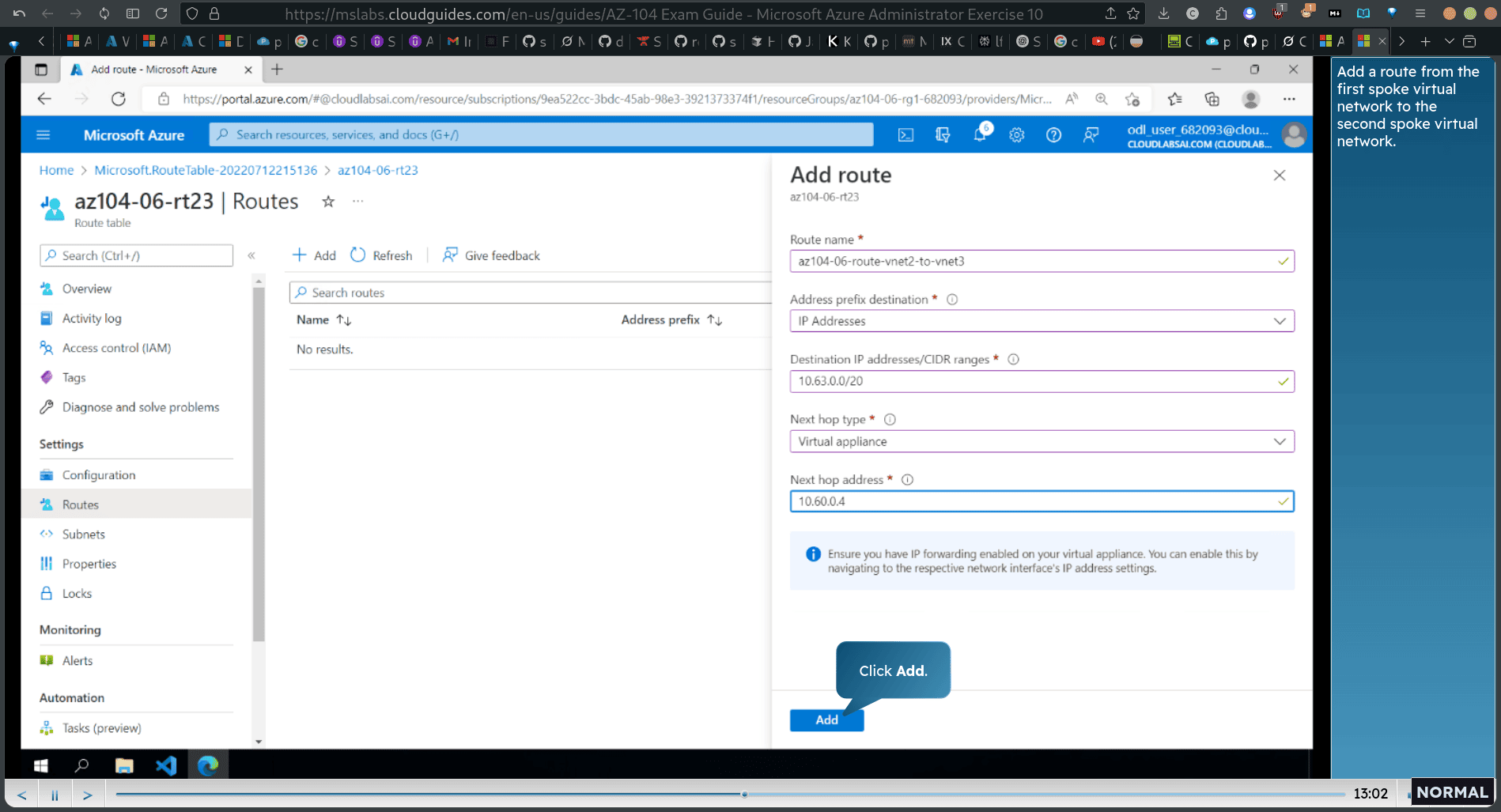
22104-06-route-vnet2-to-vnet3
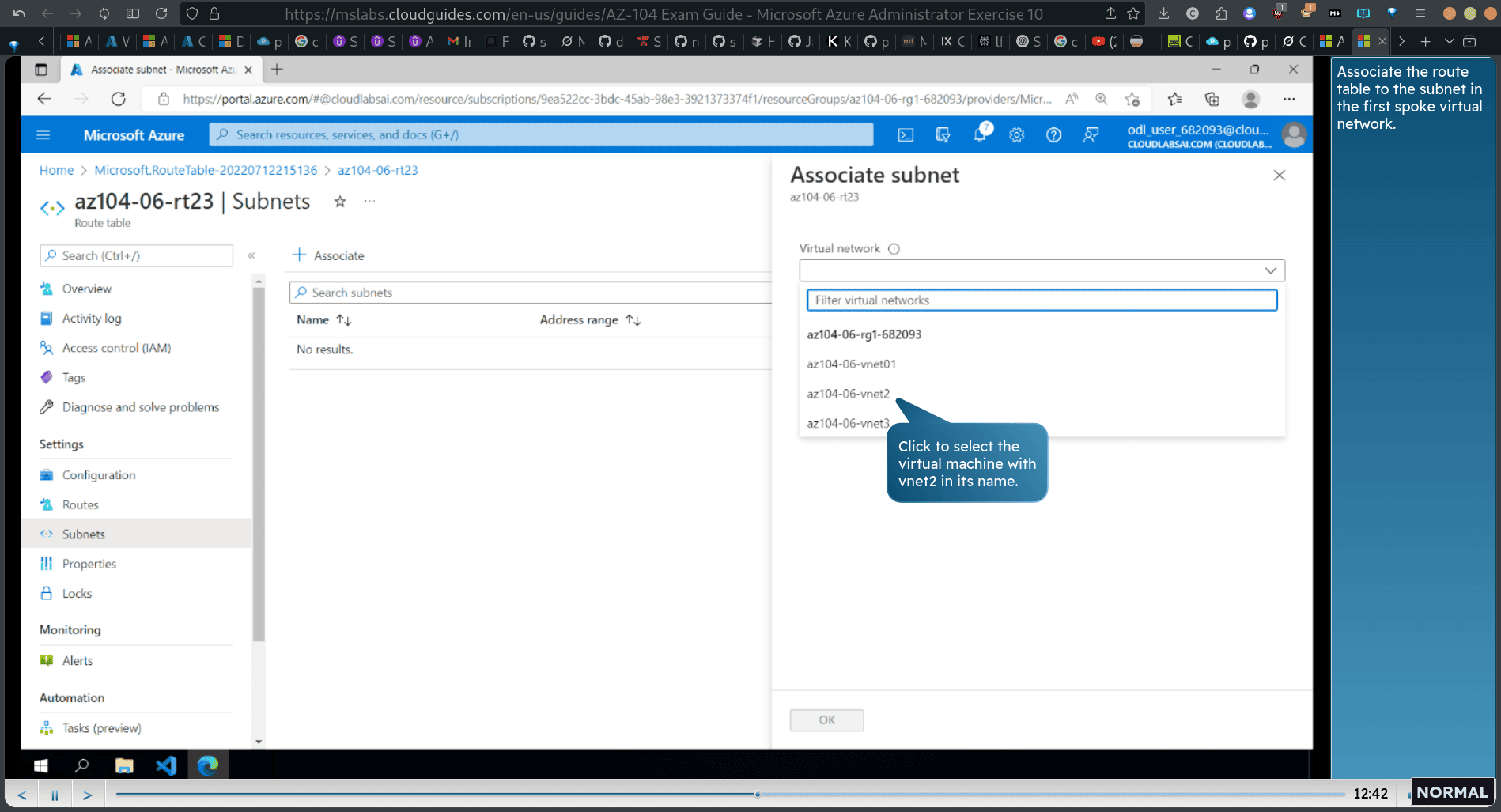
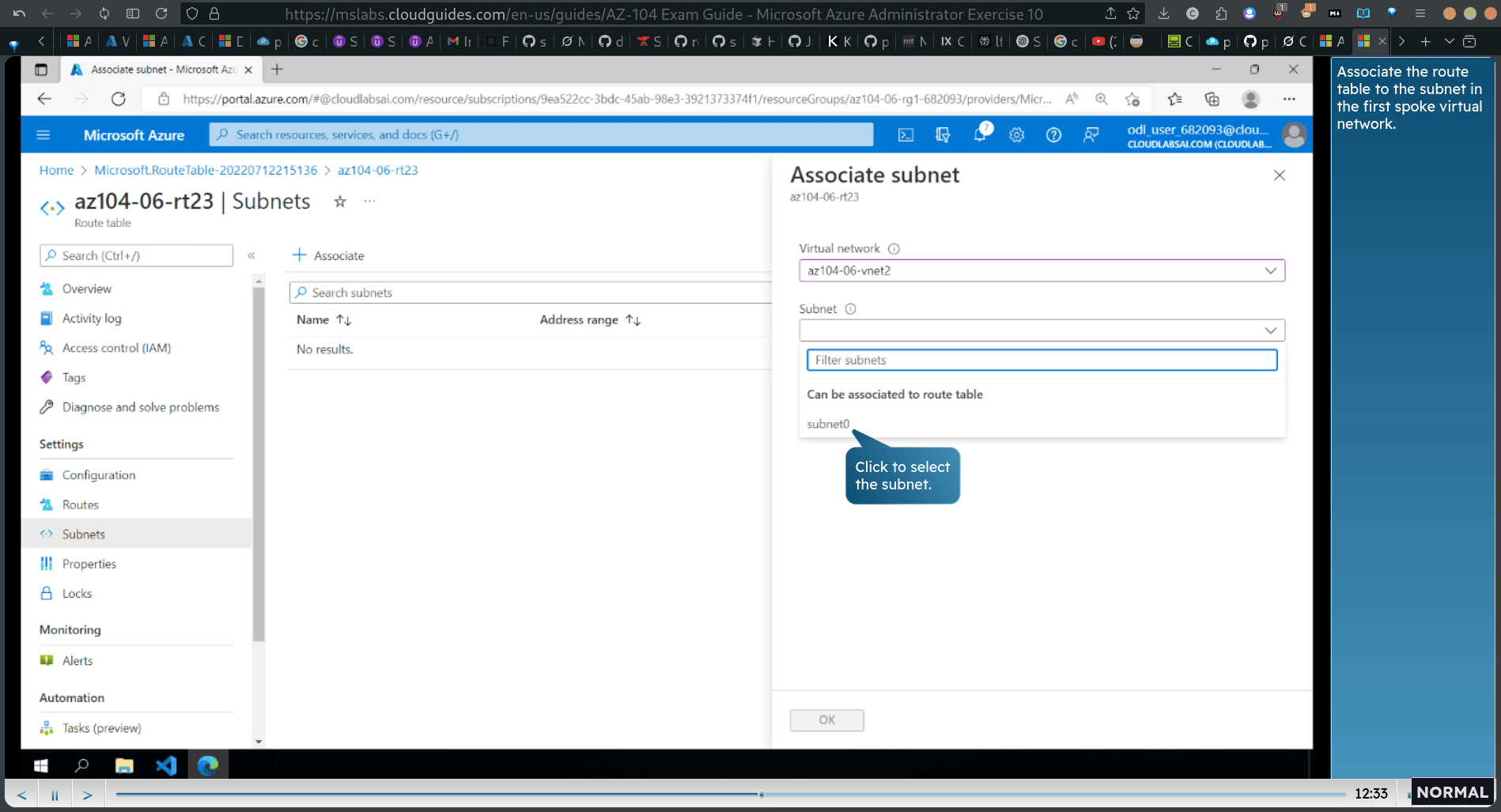
back to routes → setting → subnets → add subnets
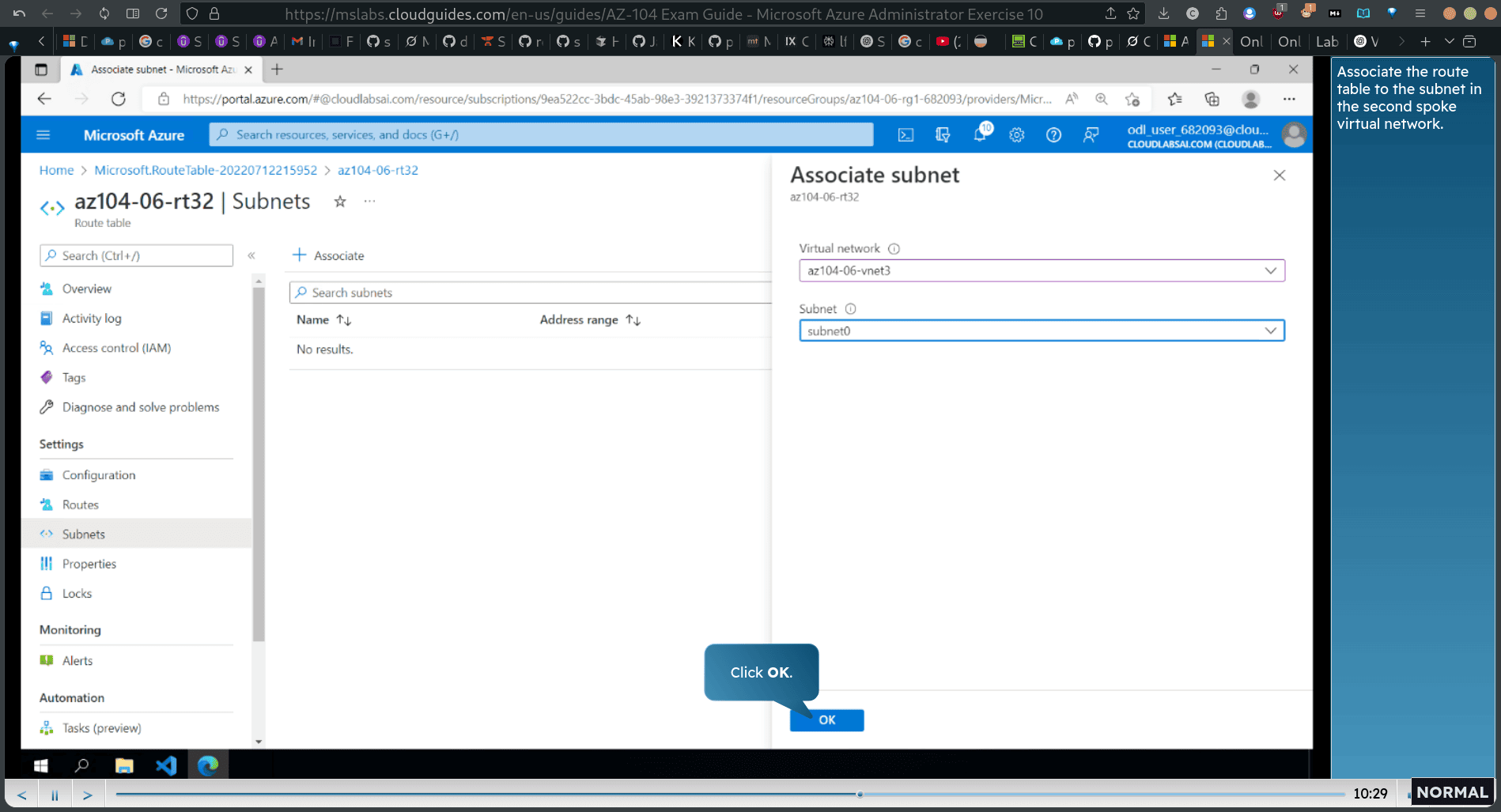
Associate the route table to the subnet in the first spoke virtual nefwork.
search route table and add another
-
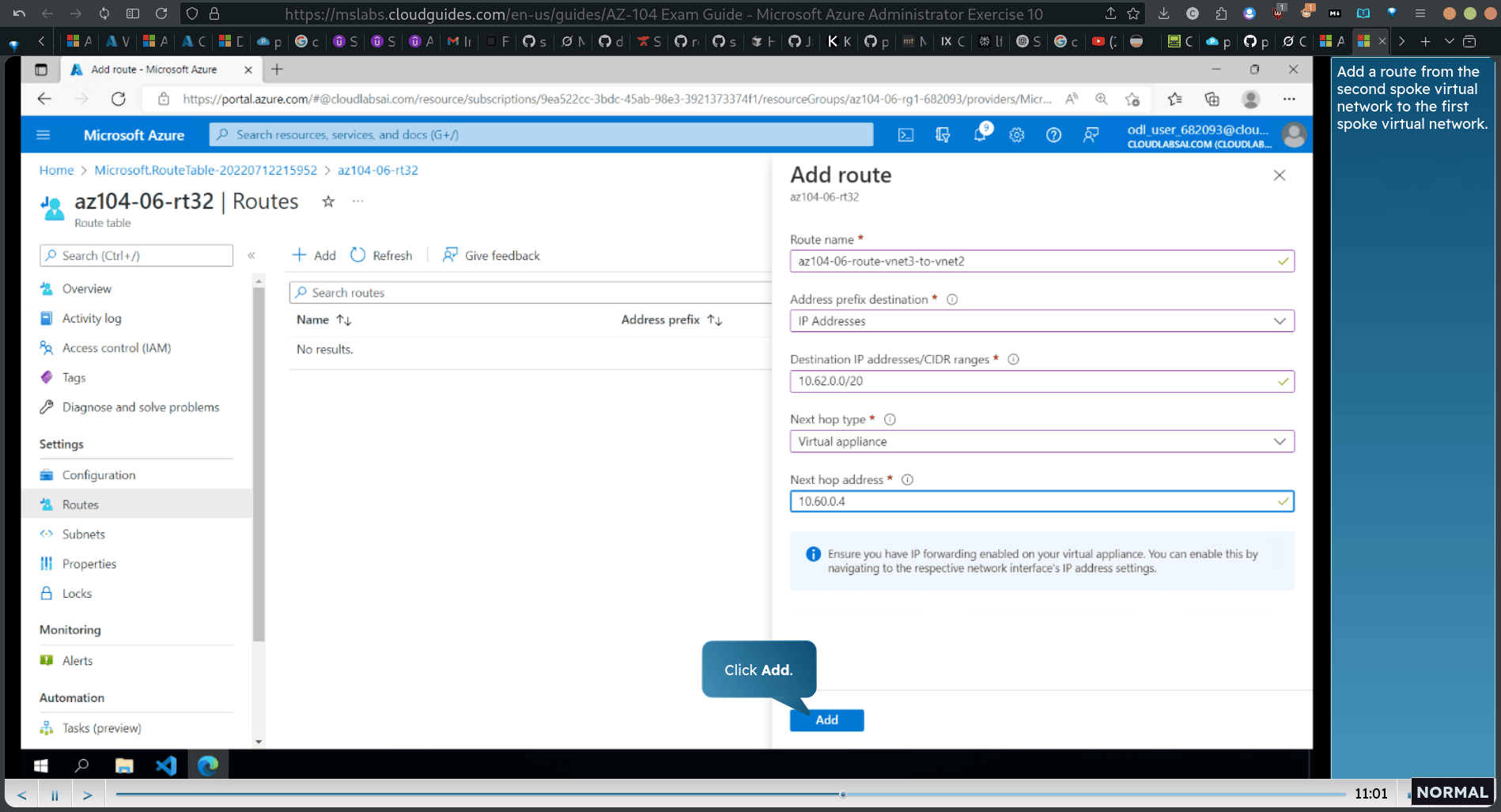
Add a route from the second spoke virtual network to the first spoke virtual network.
-
10.62.0.0/20 (destination ip) → 10.60.0.4 (next hub address)
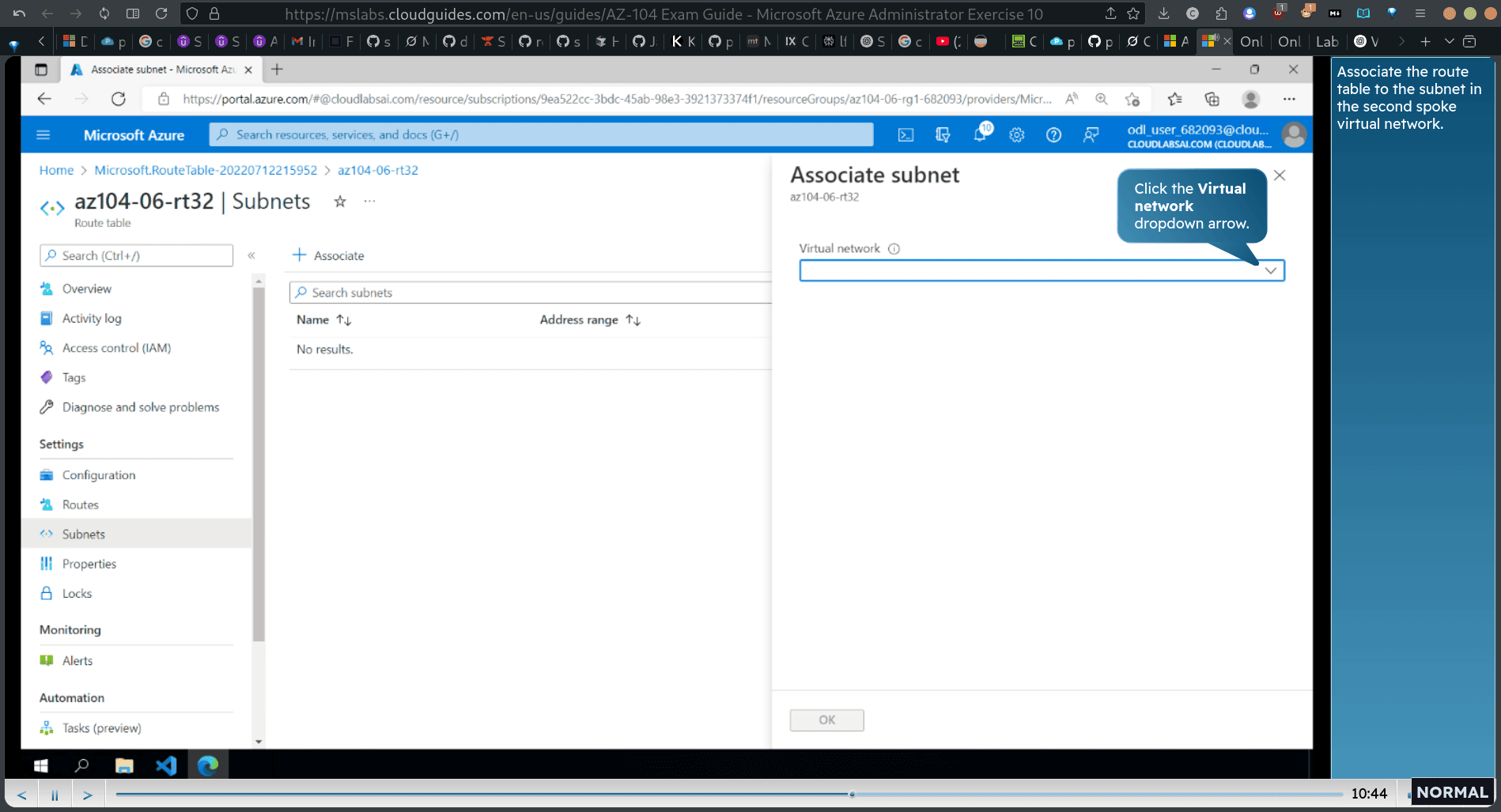
- Associate the route table to the subnet in the second spoke virtual network.
return network watcher → troubleshoot
- Test the connection from the second spoke virtual network to the first spoke virtual network.
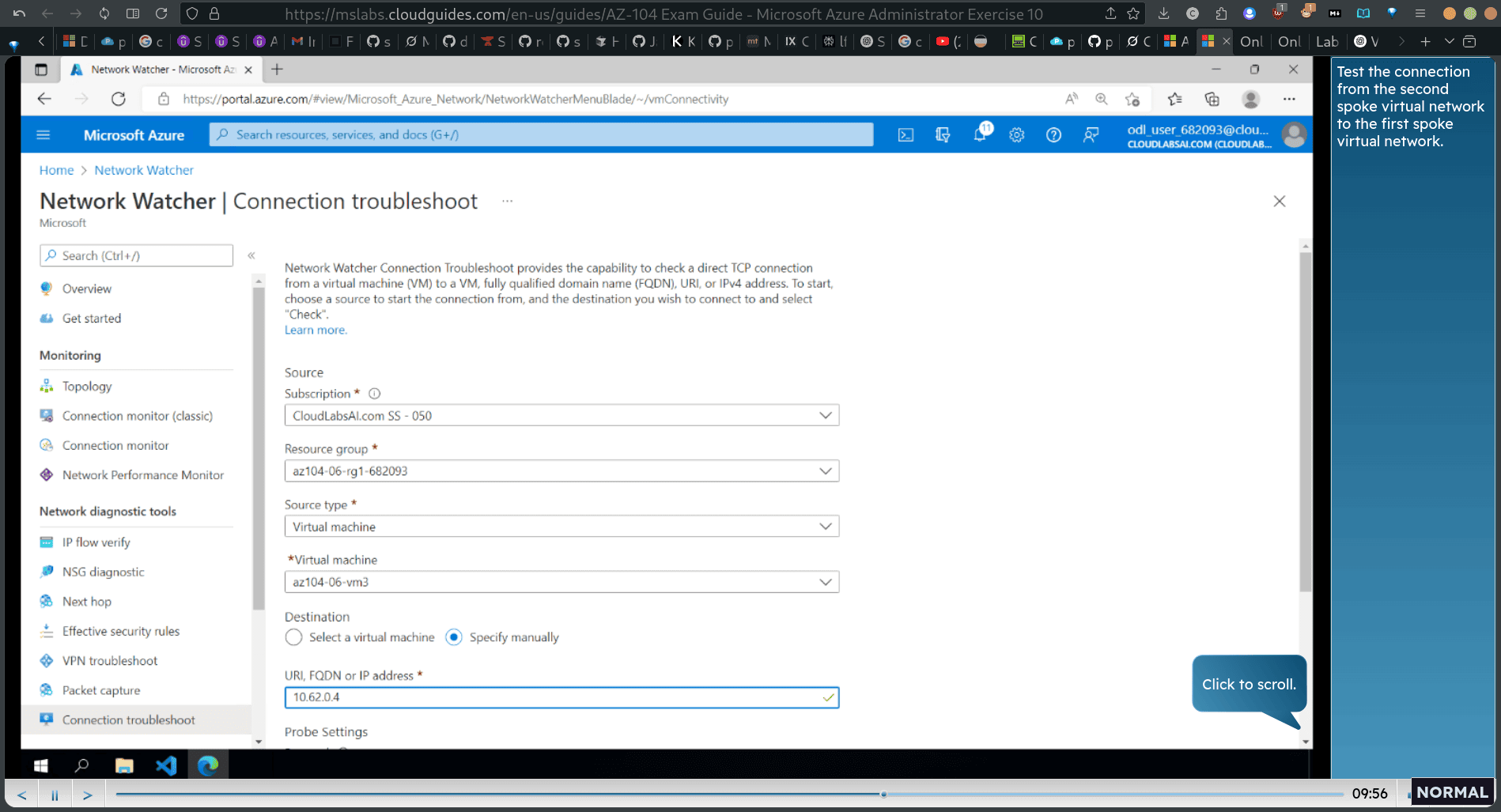
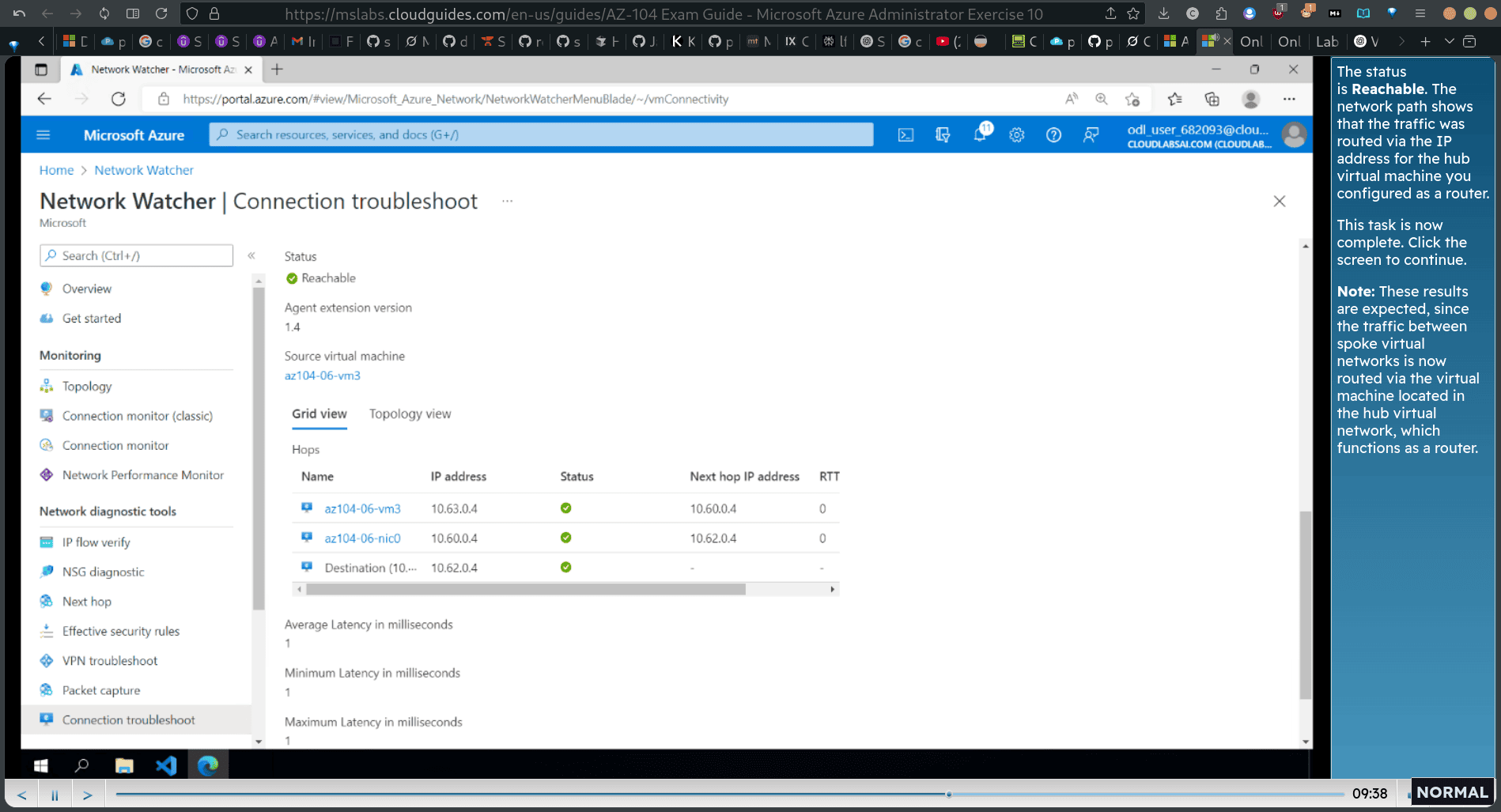
- The status is Reachable. The network path shows that the traffic was routed via the IP address for the hub virtual machine you configured as a router.
Note: These results are expected, since the traffic between spoke virtual networks is now routed via the virtual machine located in the hub virtual network, which functions as a router.
Task 5: Implement Azure Load Balancer
search load balancer
create
 add a frontend ip confirm
add a frontend ip confirm
 no zone (testing)
no zone (testing)
adding backend pool
 vnet01
vnet01
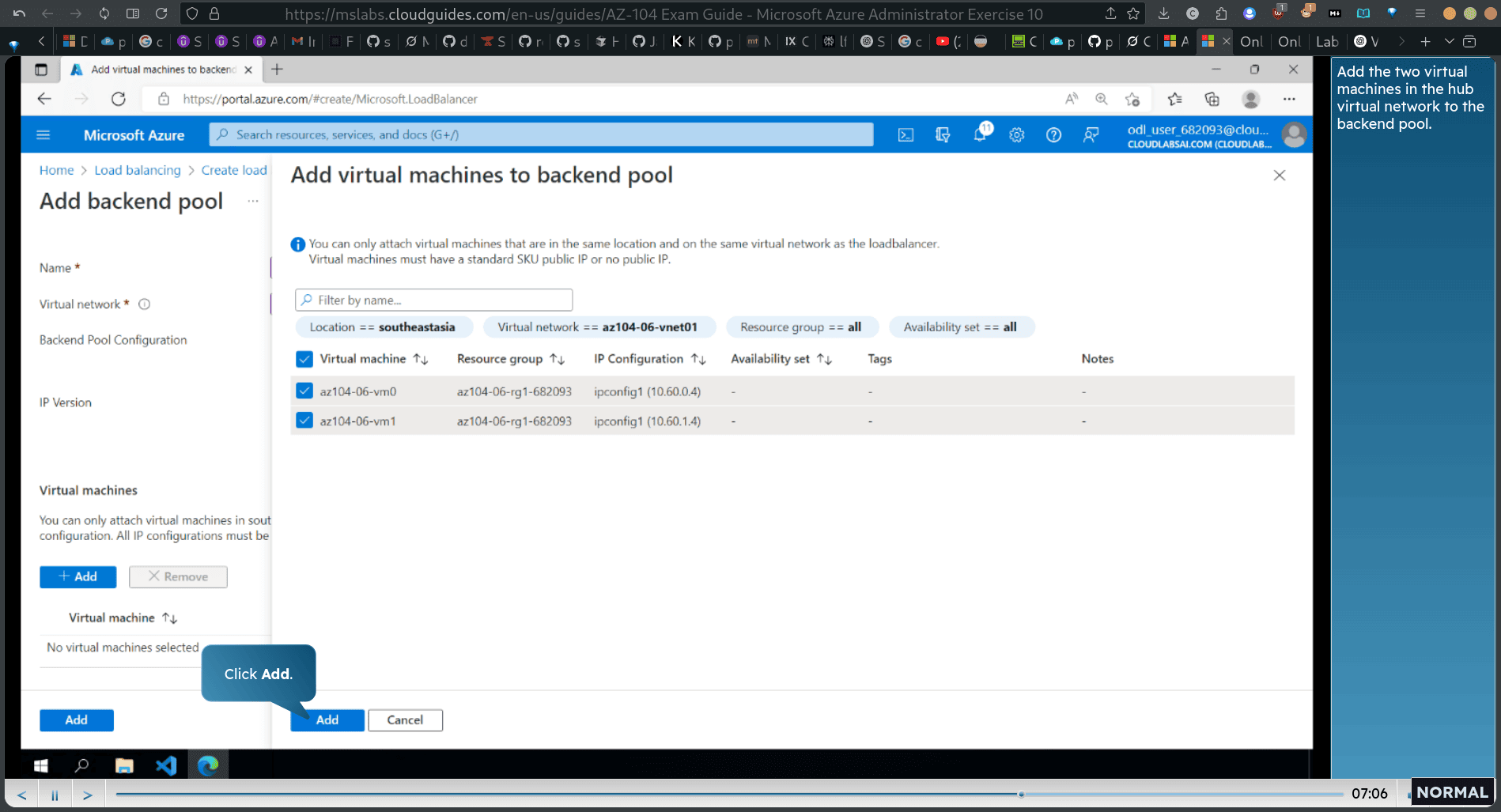
- Add the two virtual machines in the hub virtual network to the backend pool.
add load balancing rule
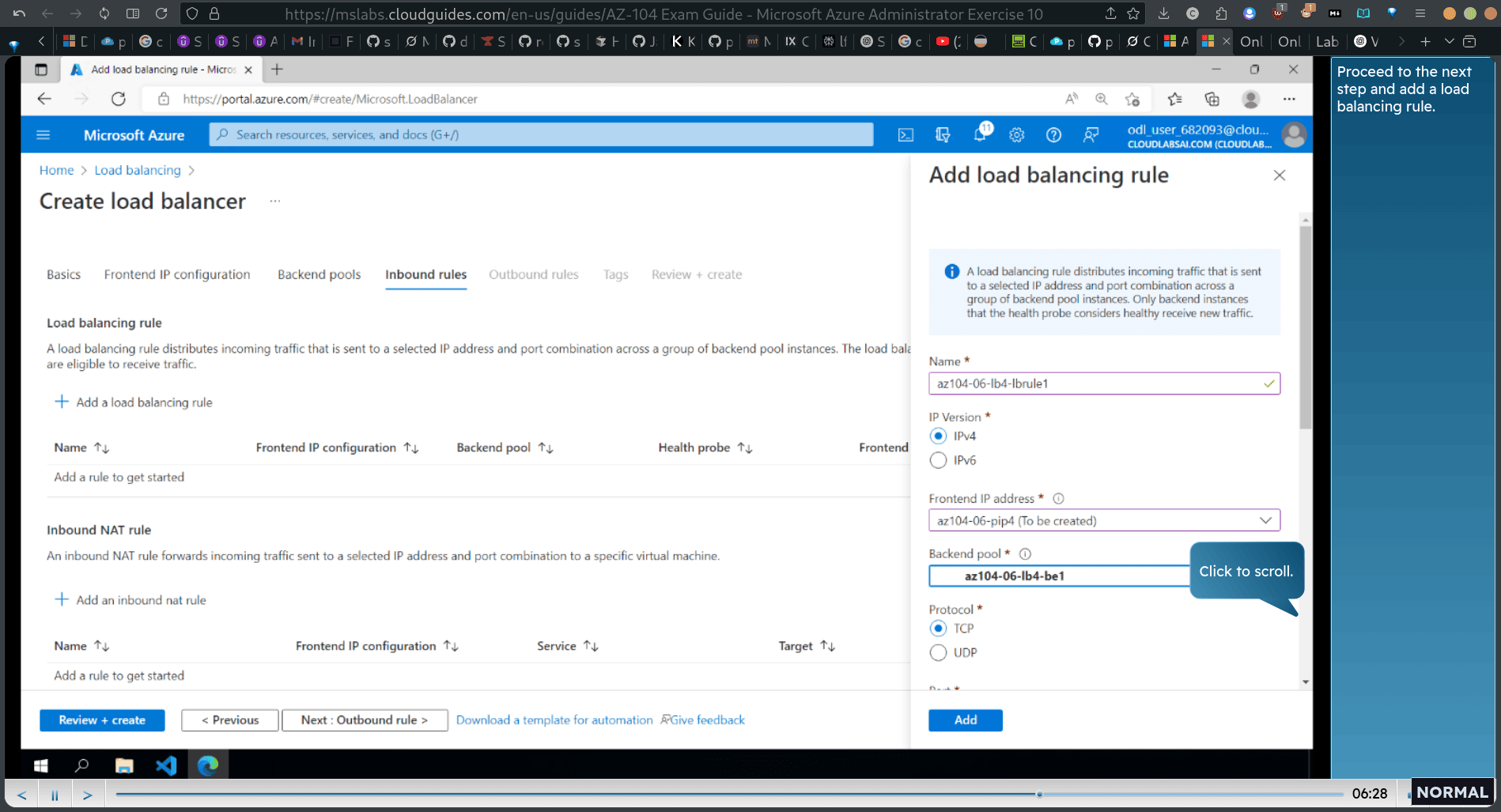
port , backend port 80
new health probe
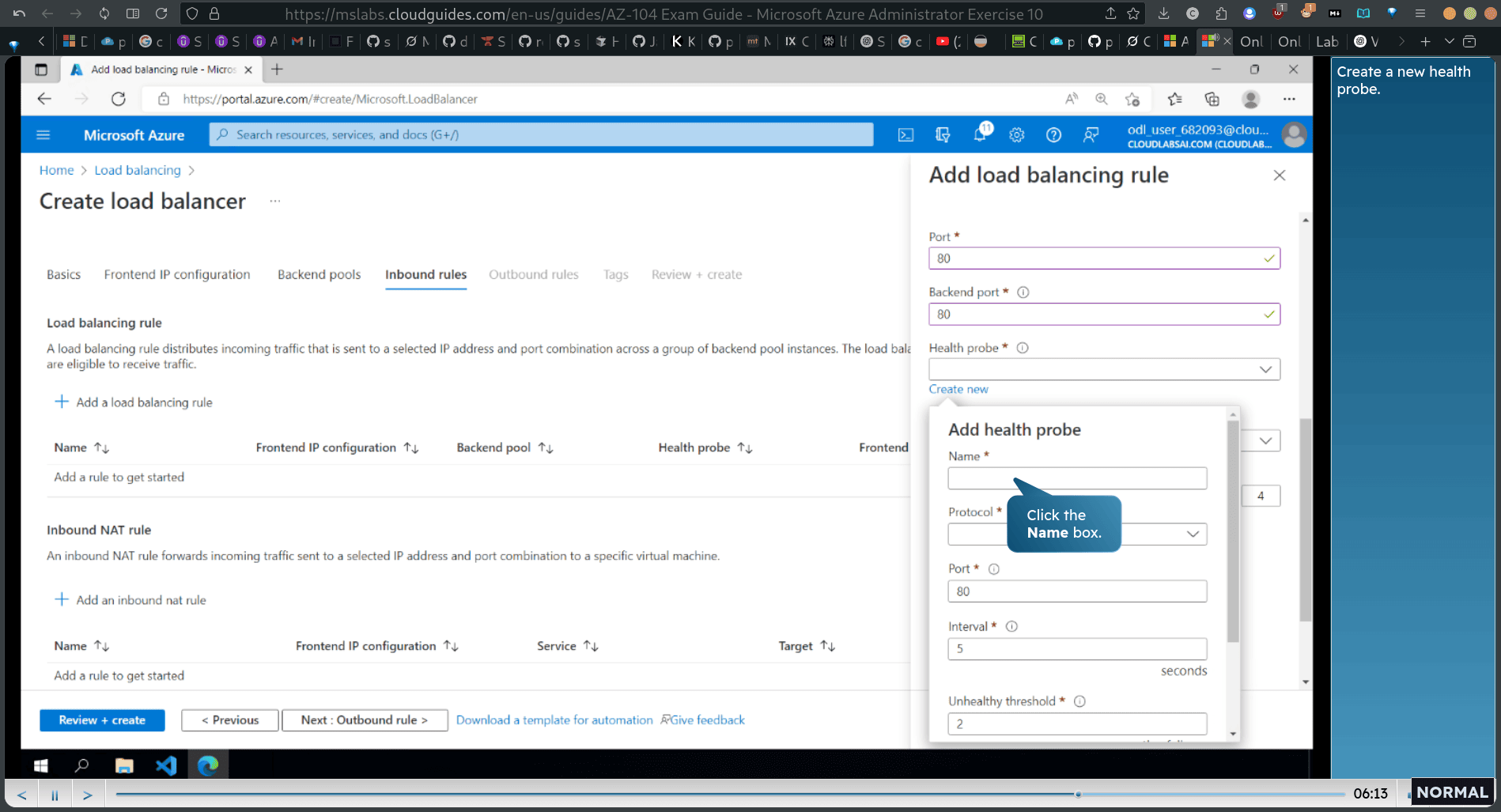
Great question! Here’s why port 80 is often used for both the frontend port (on the Azure Load Balancer) and the backend port (on your VM or service):
🔹 What is Port 80?
- Port 80 is the default port for HTTP (unencrypted web traffic).
- It’s what browsers use when you type a URL without “https://” — e.g.,
http://example.com.
🔄 Frontend Port vs. Backend Port in Azure Load Balancer
| Term | Meaning |
|---|---|
| Frontend port | The port that users connect to on the load balancer’s public IP |
| Backend port | The port on the virtual machine (backend) where the request is forwarded |
✅ Why both are set to 80 in most tutorials:
🔸 1. Simple Web Server Demo
- Most basic web apps or test VMs run HTTP servers like Nginx, Apache, or IIS on port 80.
- Matching frontend and backend ports = straightforward setup.
🔸 2. No Port Translation Needed
-
Setting both ports to 80 means:
- The user accesses:
http://<load-balancer-ip>:80 - Azure forwards it directly to
http://<backend-vm-ip>:80
- The user accesses:
-
This avoids confusion and makes debugging easier.
🔸 3. Browser Compatibility
- Browsers automatically assume port 80 for HTTP.
- Users don’t need to specify a port in the URL.
🧪 Example
-
You deploy a load balancer in front of 3 VMs.
-
Each VM runs a web server on port 80.
-
You configure:
- Frontend port: 80
- Backend port: 80
-
A user hits
http://<LB-IP>, and Azure routes the request to a healthy backend VM on port 80.
🔐 What if you want to use HTTPS (secure)?
-
Then you’d use port 443 instead:
- Frontend port: 443
- Backend port: 443
-
You’d also need an SSL certificate installed.
🔁 What if frontend ≠ backend ports?
You can set:
- Frontend: 8080
- Backend: 80
Then users would need to access:
http://<LB-IP>:8080
Azure would forward it to port 80 on the backend.
This is useful in special cases, like:
- Port conflict on frontend IP
- Hosting multiple services with different public ports
✅ Summary
| Setting | Reason |
|---|---|
| Port 80 | Default for HTTP traffic |
| Same frontend & backend ports | Simplifies setup and avoids translation |
| Tutorials use it | Because it’s the most common web app scenario |
 outbond rules→ none here
outbond rules→ none here
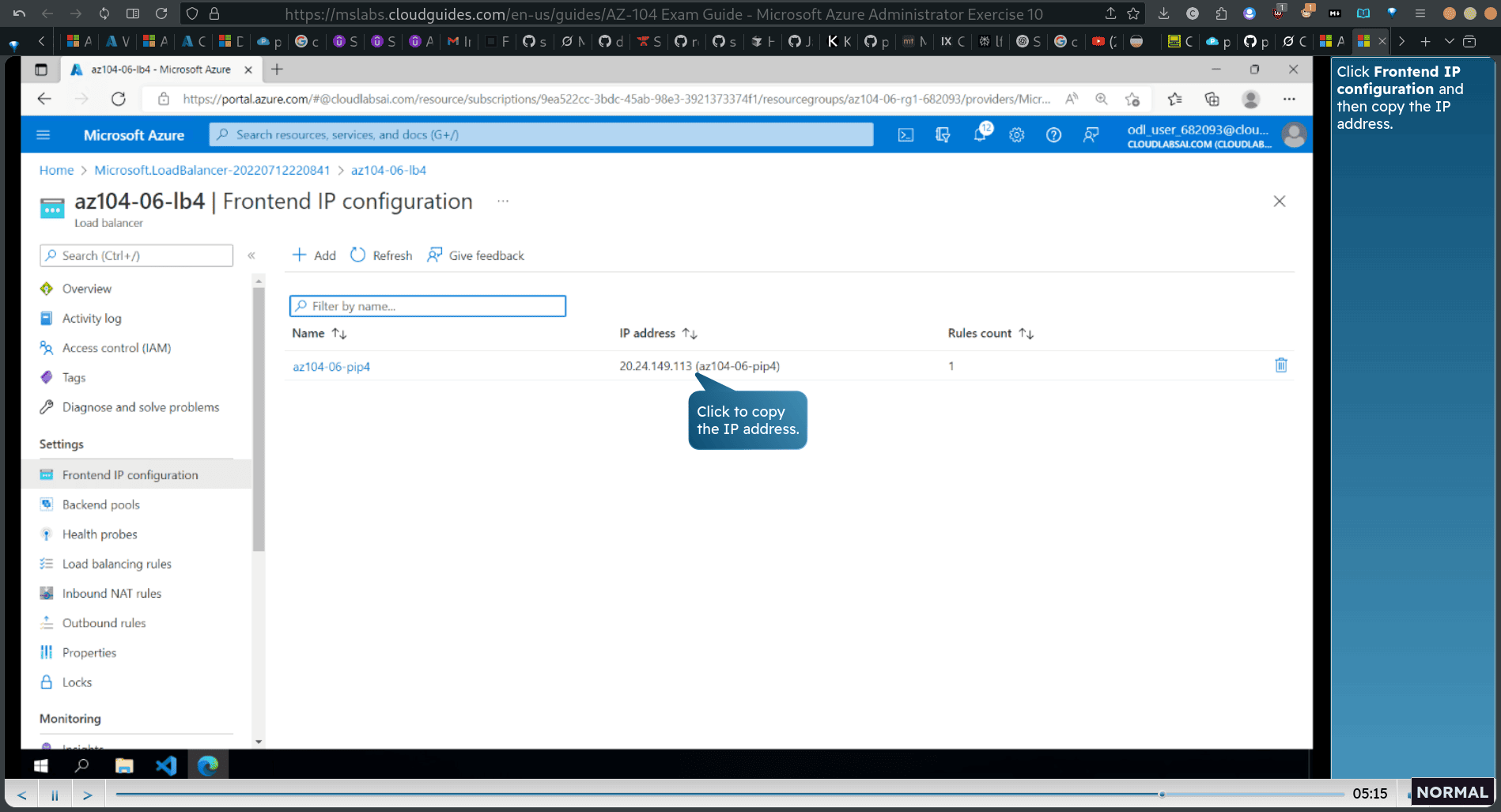
go to resource → frontend ip config → copy the ip address
test it in local browser
The target virtual machine changed to the second VM in the hub virtual network, as indicated by the message. This task is now complete. Close the browser tab.
refresh the ip → from vm0 to vm1 (load balanced)
Task 6: Implement Azure Application Gateway
- In this next task, you will implement an Azure Application Gateway in front of the two Azure virtual machines in the spoke virtual networks.
 vnet01 → subnet → add subnet
vnet01 → subnet → add subnet
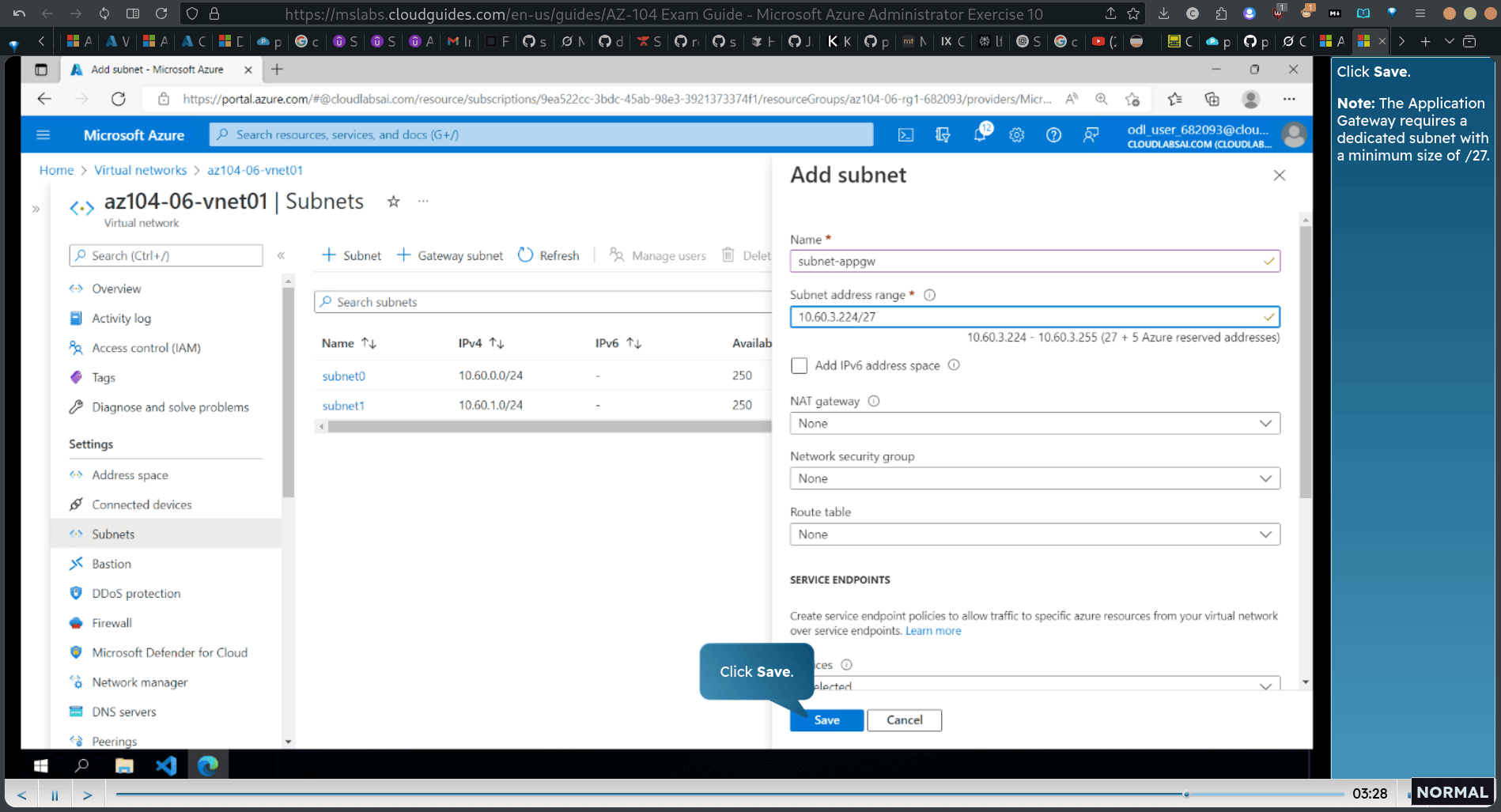 Click save.
Click save.
- Note: The Application Gateway requires a dedicated subnet with a minimum size of /27.
search application gateway → creat
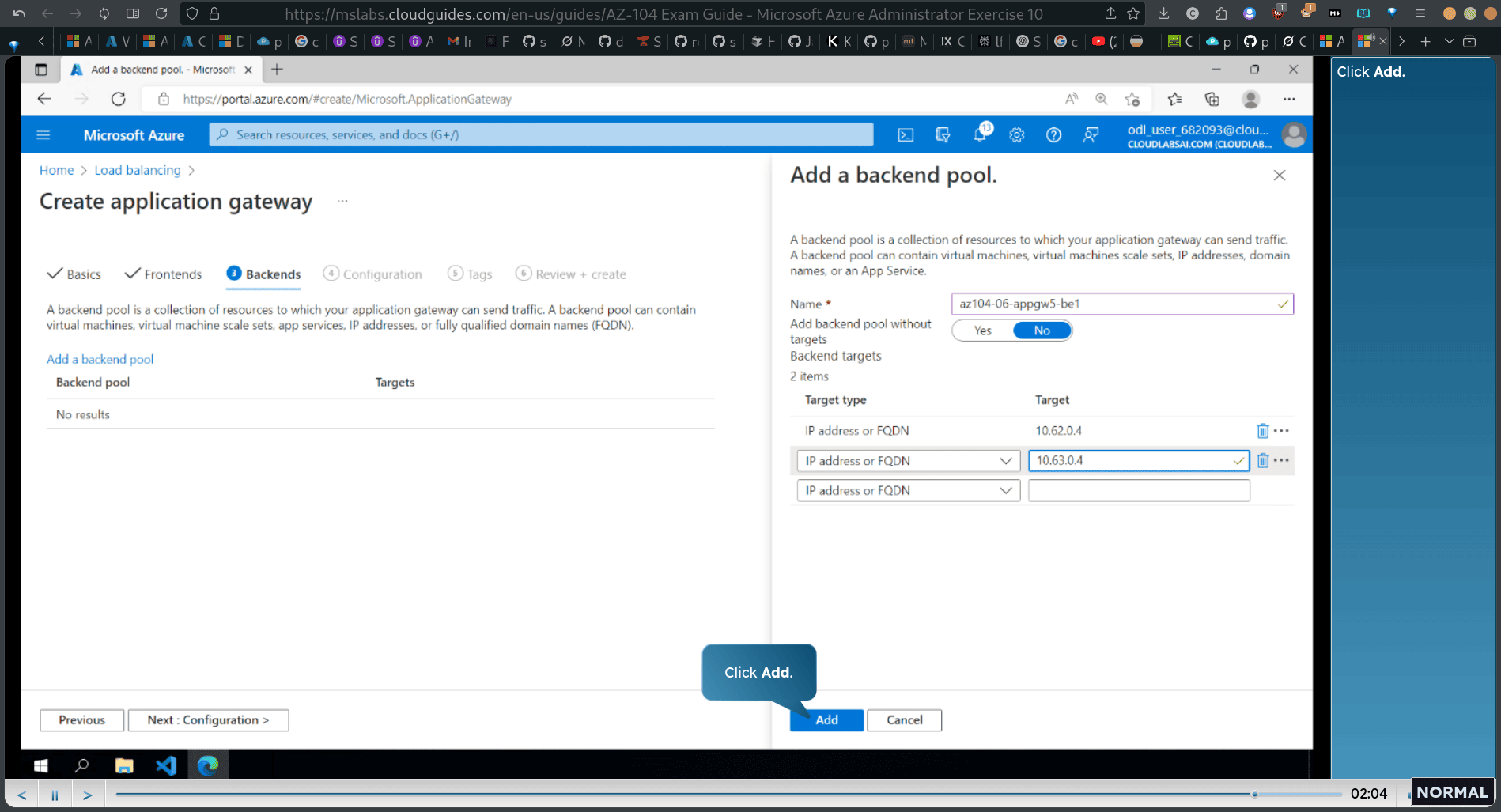
- In the Target column, enter the private IP addresses of virtual machines in the spoke virtual networks.
adding routing rule
listener
backend setting:
 add new backend setting
add new backend setting
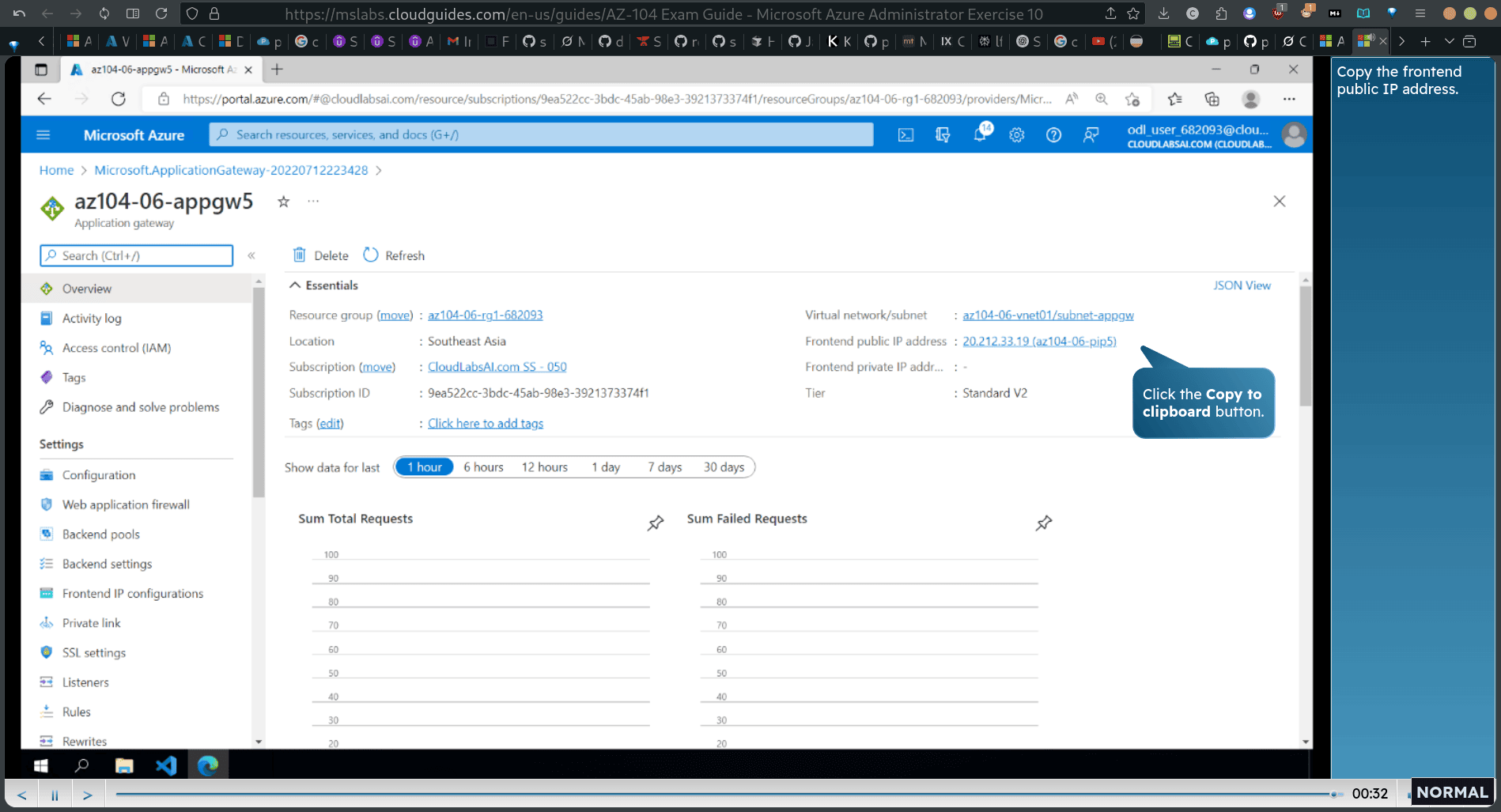 copy the frontend ip address
The target virtual machine changed to the VM in the second spoke virtual network, as indicated by the message.
copy the frontend ip address
The target virtual machine changed to the VM in the second spoke virtual network, as indicated by the message.
- Note: This result illustrates that Application Gateway can target virtual machines on multiple virtual networks. Additionally, Application Gateway can target endpoints in other Azure regions or even outside of Azure, - unlike Azure Load Balancer, which load balances across virtual machines in the same virtual network.
11. Manage Azure Storage
Lab scenario: In this lab, you’ll evaluate the use of Azure Storage for storing files currently residing in on-premises data stores. To minimize the cost of storage, you’ll place less frequently accessed files in lower-priced storage ftiers. You’ll also explore different protection mechanisms that Azure Storage offers, including network access, authentication, authorization, and replication. Finally, you’ll determine to what extent the Azure Files service might be suitable for hosting your on-premises file shares.
Task 1: Deploy an Azure virtual machine
Task 2: Create and configure an Azure Storage account
 storage ac → rg1
storage ac → rg1
hot type
enable soft delete
 click the new ac → geo replication→ setting → config
click the new ac → geo replication→ setting → config
Set Replication to Locally-redundant storage (LRS) and save the change.
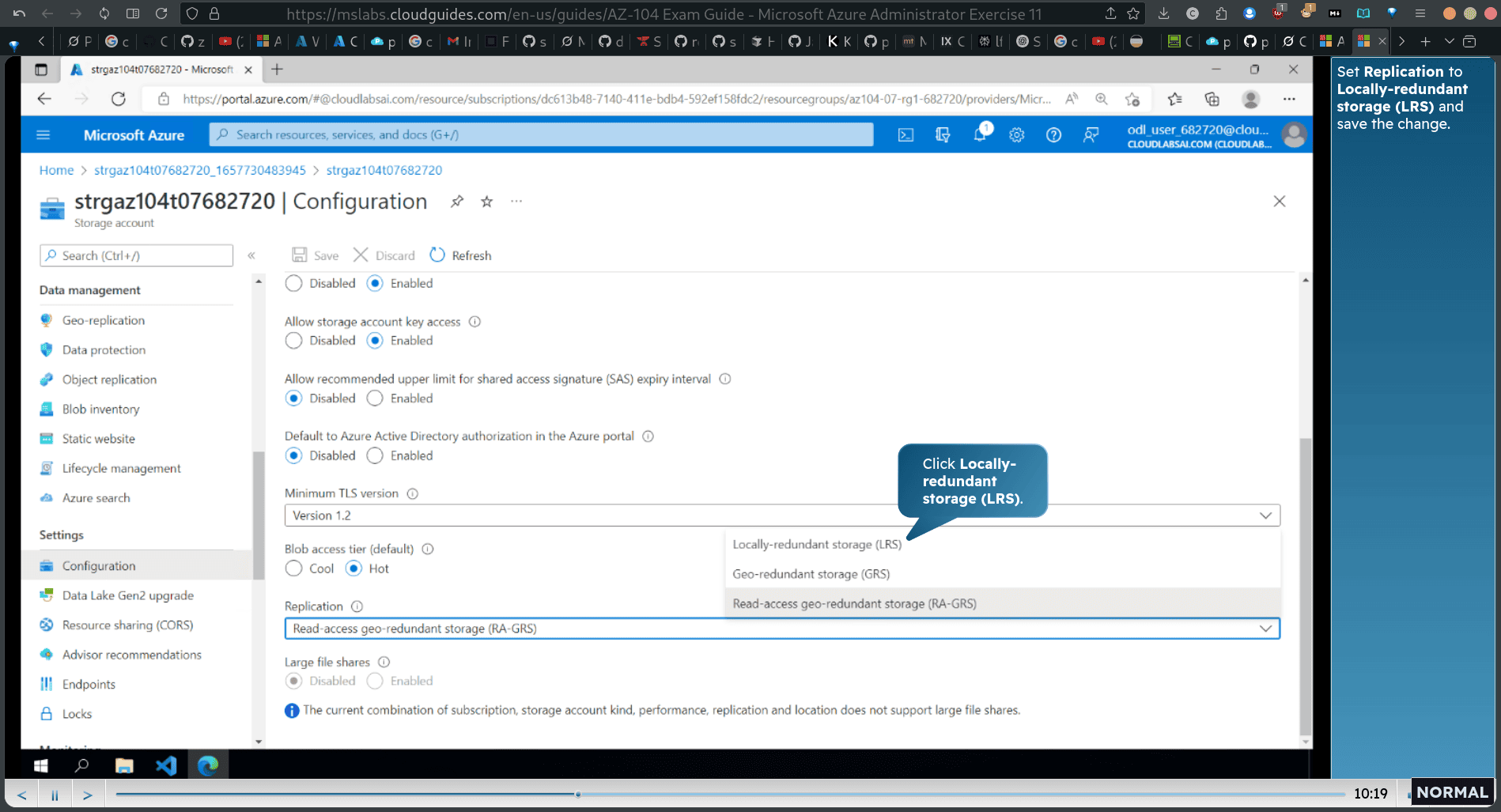
Note that the storage account only has the primary location. Return to the Configuration blade.
- Set Blob access tier (default) to Cool and save the change. Note: The cool access tier is optimal for data that is not accessed frequently.
save
Task 3: Manage blob storage
ac → container → new → upload a blob
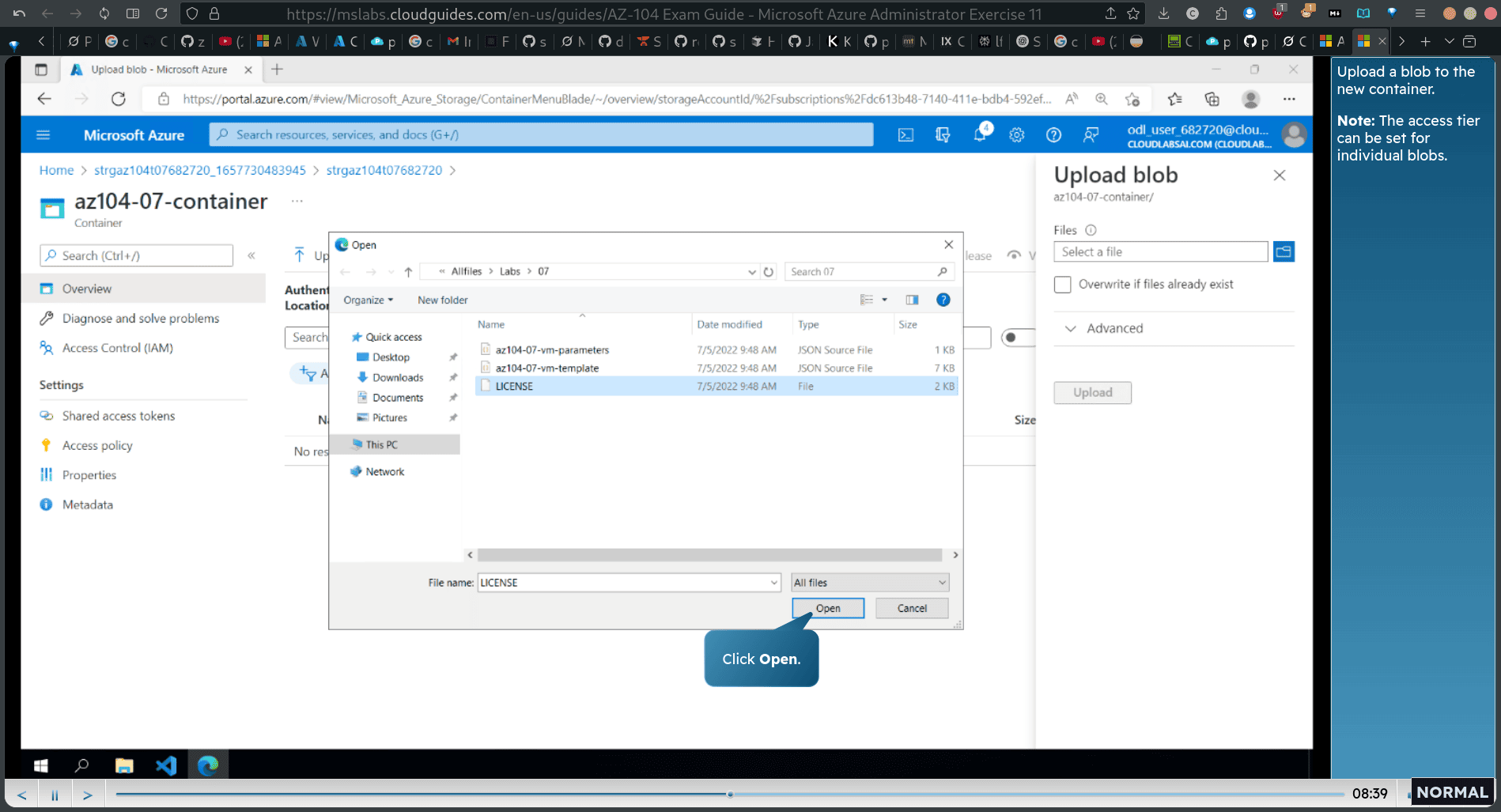 upload license
upload license
hot type
Note: You can download the blob, change its access tier, acquire a lease, and assign custom metadata. You can also edit the file directly within the Azure portal, create snapshots, and generate an SAS token.
Task 4: Manage authentication and authorization for Azure Storage
copy the blob url → firefox → url
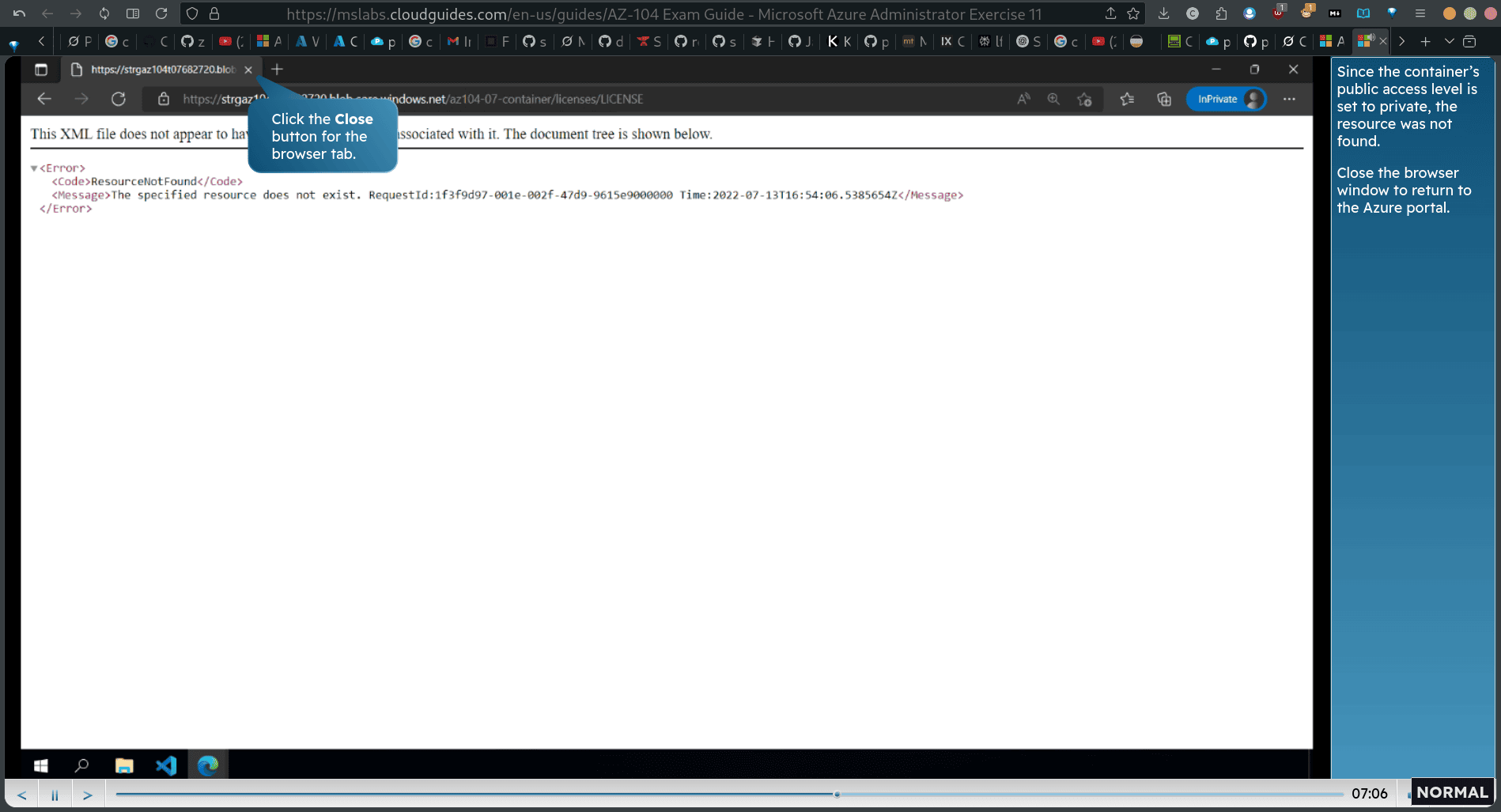
Since the container’s public access level is set to private, the resource was not found. Close the browser window to return to the Azure portal.
-
Open the Generate SAS tab.
-
Update the start date and then click Generate SAS token and URL.
generate the real url
now the browser can view it
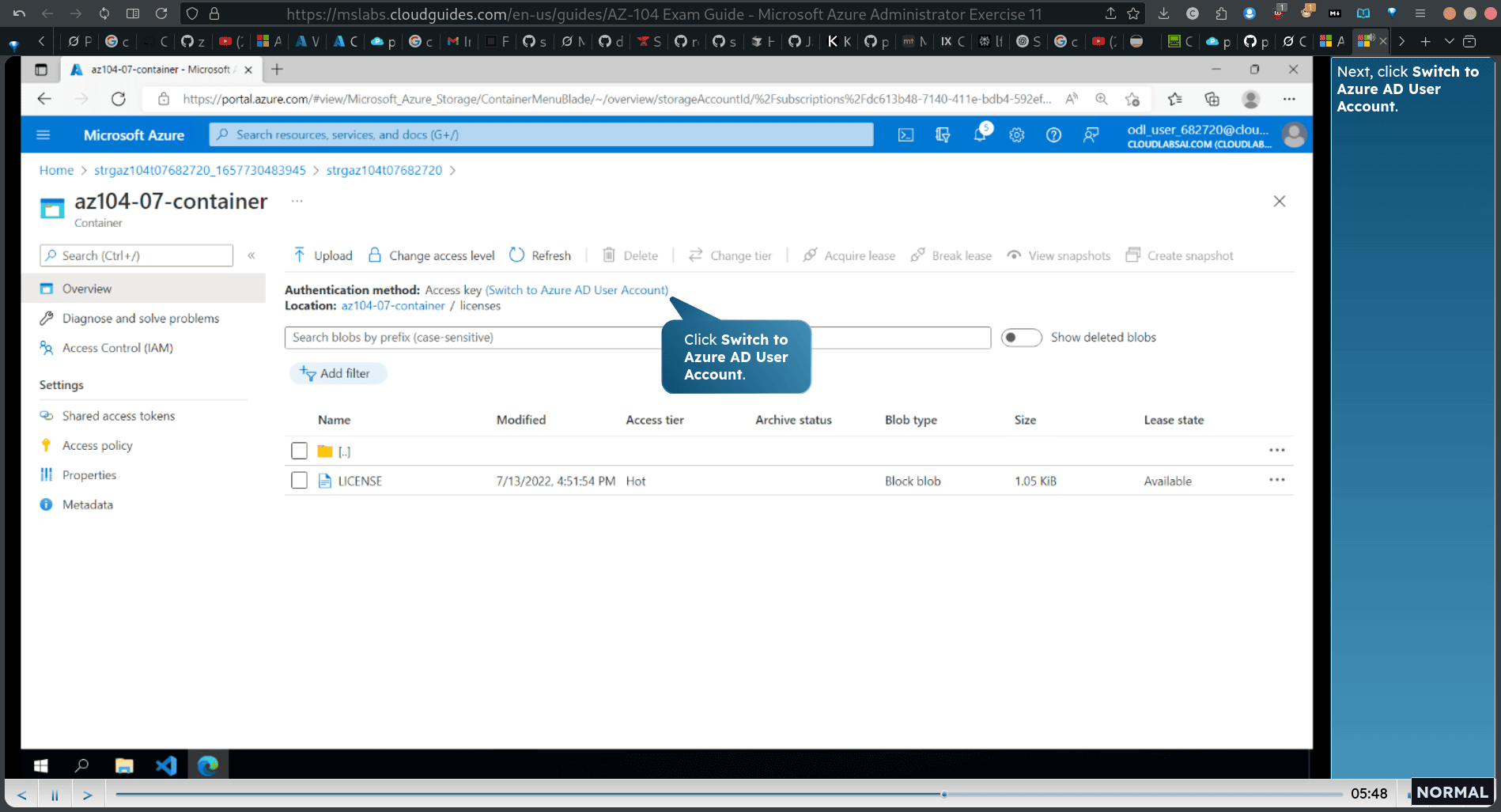
- Next, click Switch to Azure AD User Account.
An error appears because you do not have permission to change the authentication method. In the left pane, click Access Control (IAM).
add role assignment
- Search for and then select the Storage Blob Data Owner role.
select member , search for username → review and assign
back to
- Click Switch to Azure AD User Account fo verify that you can change the authentication method.
Task 5: Create and configure an Azure Files share
container → file share
 new share Scroll down the Windows tab and copy the script.
new share Scroll down the Windows tab and copy the script.
you can select different os here
search VM
- paste the scrpit you copy early
$connectTestResult = if (SconnectTestResult.TcpTestSucceeded) {
Save the password so the drive will persist on reboot
cmd.exe /C “cmdkey /add:® “strgaz104t07682720.file.core.windows.net™ ” /user:” “localhost\strg:
Test-NetConnection -ComputerName strgaz104t07682720.file.core.windows.net
Mount the drive
New-PSDrive -Name Z -PSProvider FileSystem -Root “\strgaz104t07682720.file.core.windows.ne’
} else [ Write-Error -Message “Unable to reach the Azure storage account via port 445. Check to make
another script:
New-Item -Type Directory -Path ‘Z:\az104-07-folder’
New-Item -Type File -Path ‘Z:\az104-07-folder\az-104-07-file.txt”
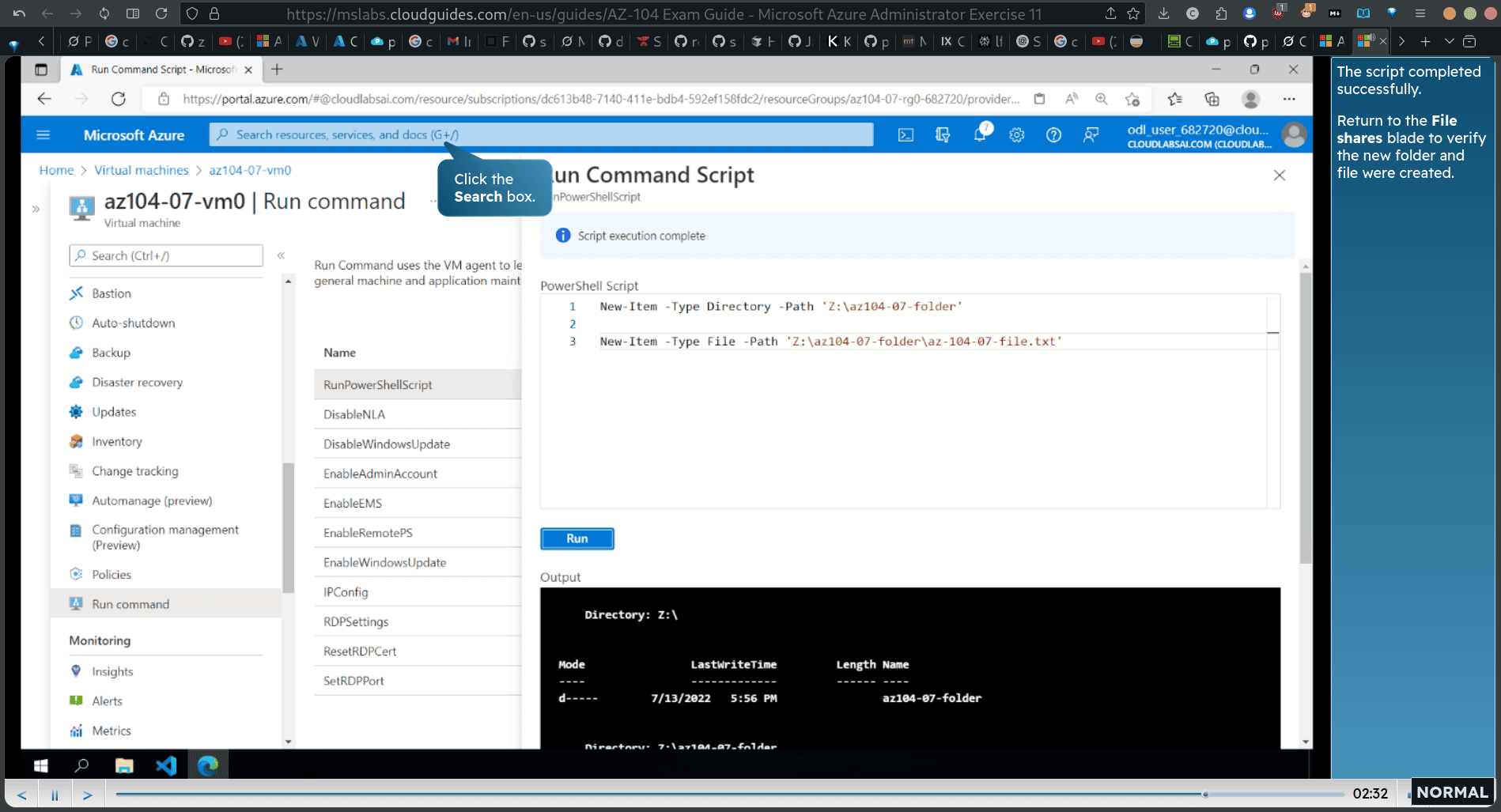 Return fo the File shares blade to verify the new folder and file were created.
Return fo the File shares blade to verify the new folder and file were created.
the folder and the file is created (lol why need this part)
Task 6: Manage network access for Azure Storage
back to file share blades (storage ac)
- Under Security + networking in the left pane, click Networking.
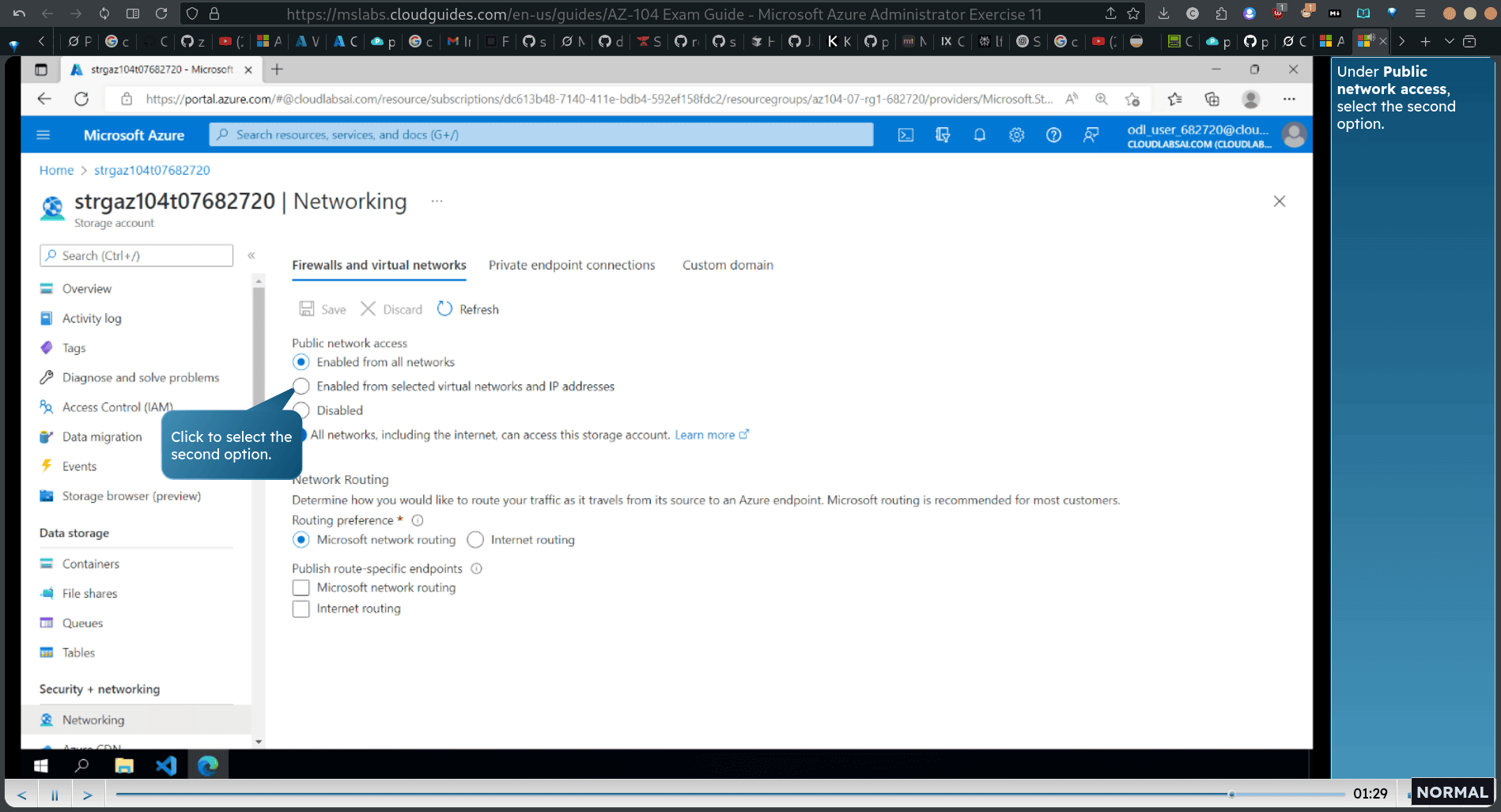
- Enabled from selected virtual networks and IP addresses rather than all networks
Note: You can use these settings to configure direct connectivity between Azure virtual machines on designated subnets of virtual networks and the storage account by using service endpoints.
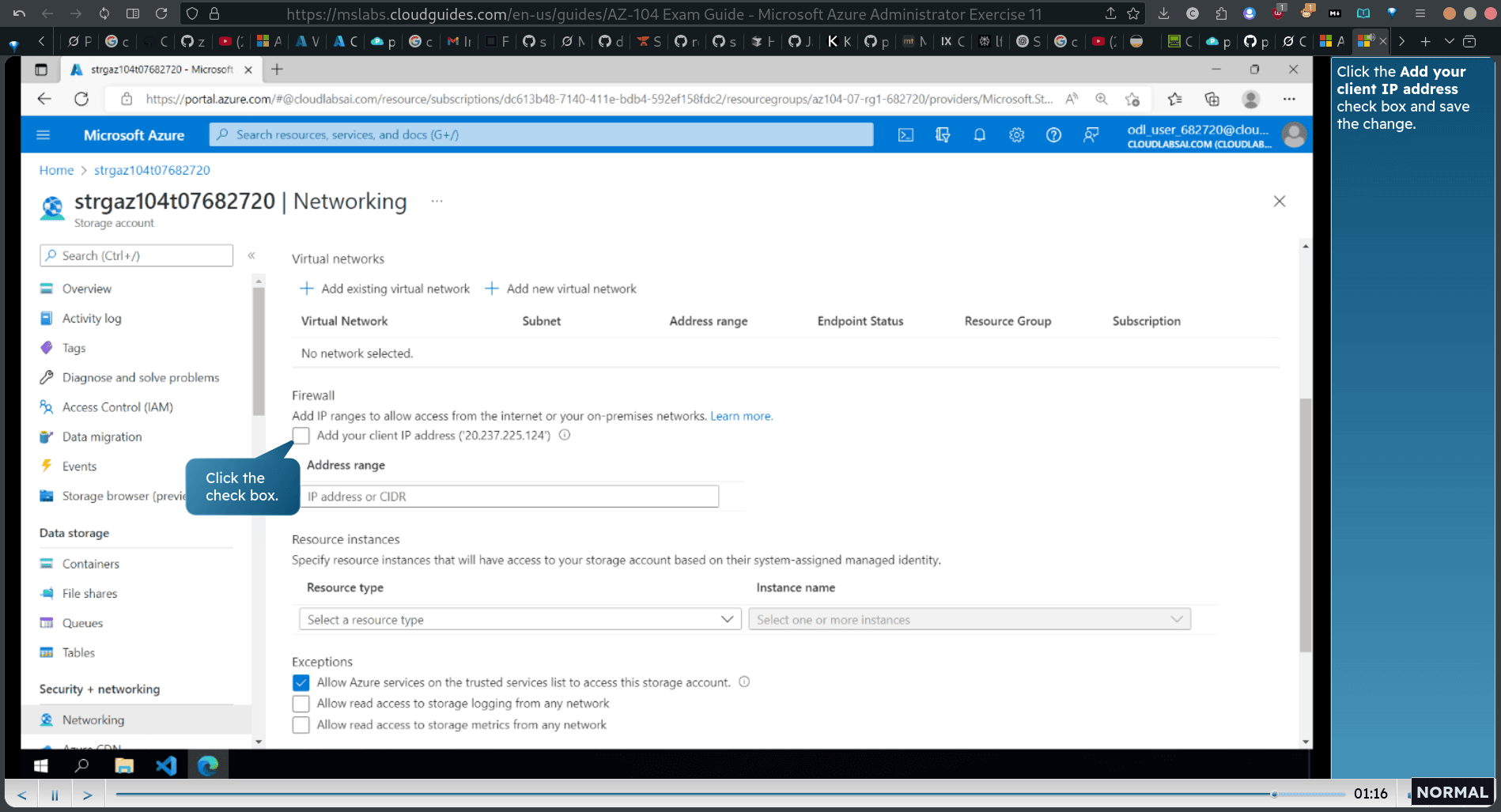
Click the Add your client IP address check box and save the change.
Next, open a new InPrivate window and navigate to the blob SAS URL you generated previously. Since you are connecting from your client IP address, the license file downloaded successfully.
Invoke-WebRequest -URI ‘your sas url’
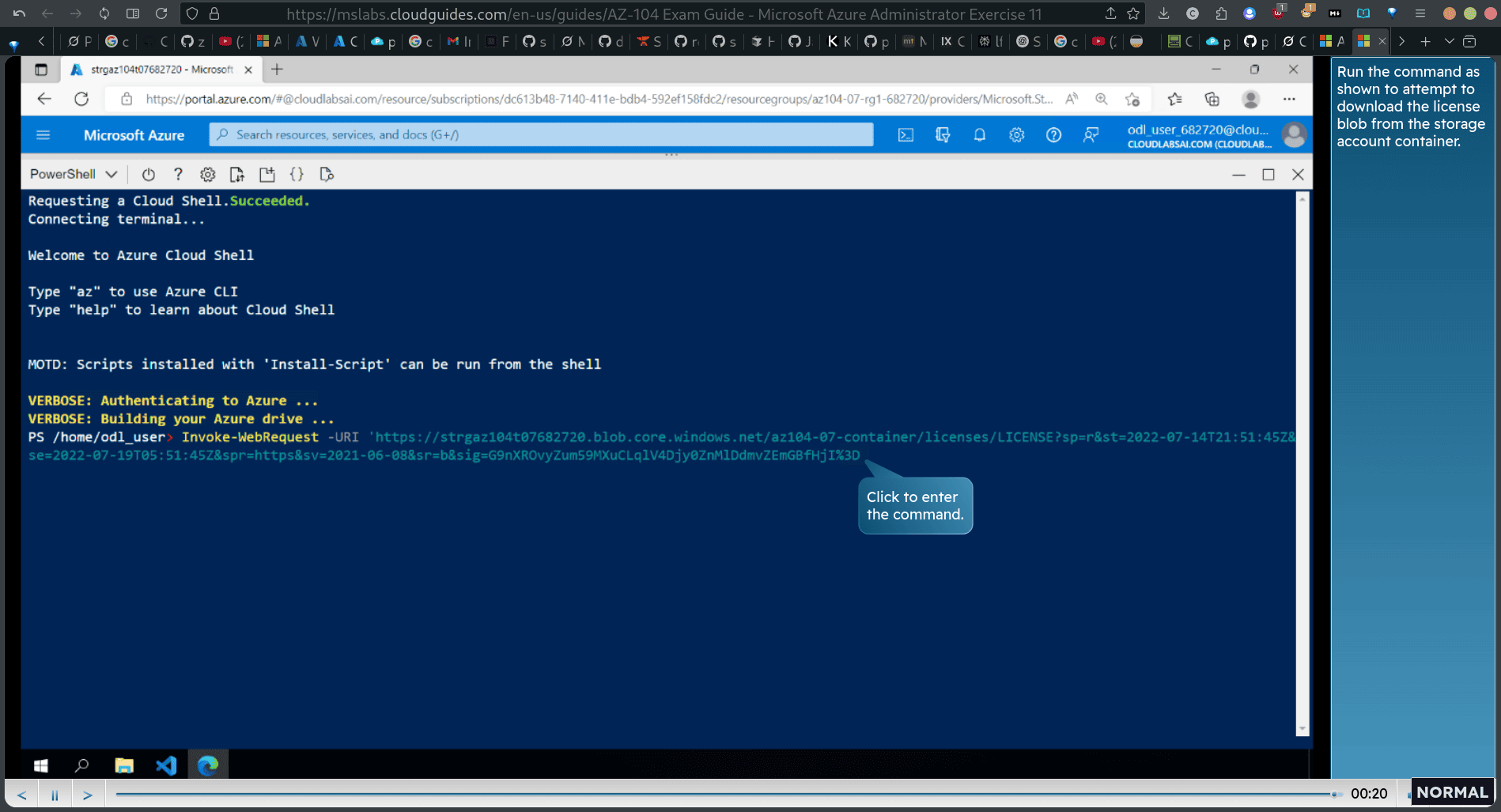
- Since you are connecting from the IP address assigned to an Azure virtual machine hosting the Cloud Shell instance, the download attempt failed. red word
12. Manage virtual machines >
Lab scenario: In this lab, you’ll identify different options for deploying and configuring Azure virtual machines. First, you’ll determine different compute and storage resiliency and scalability options you can implement when using Azure virtual machines. Next, you’ll investigate compute and storage resiliency and scalability options that are available when using Azure virtual machine scale sets. You’ll also explore the ability to automatically configure virtual machines and virtual machine scale sets by using the Azure virtual machine Custom Script Extension.
Task 1: Deploy zone-resilient Azure virtual machines using the Azure portal and an Azure Resource Manager template
new vm , window server , zone 1
 none public inbond ports
none public inbond ports
 craet new vnet
craet new vnet
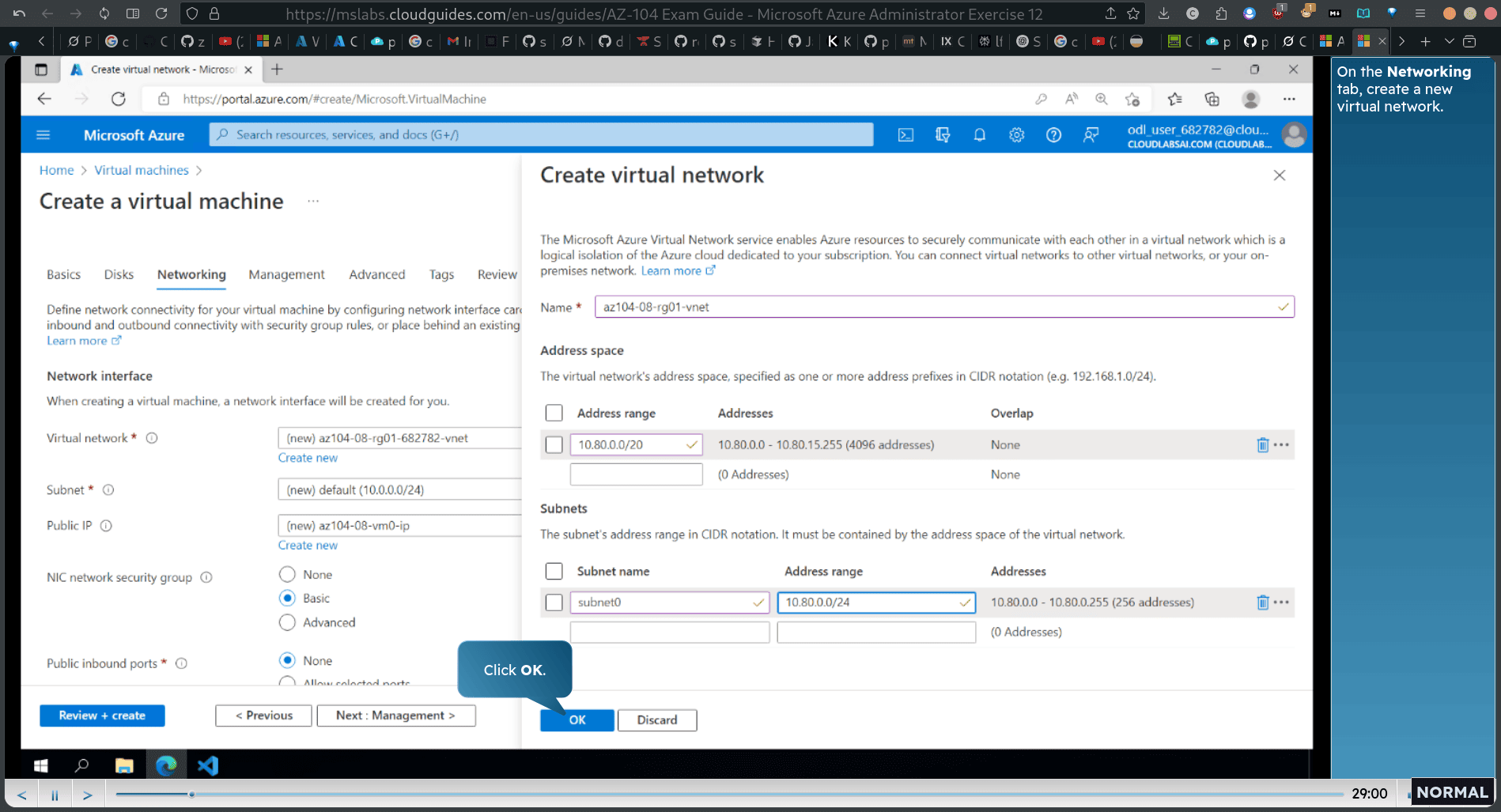 new subnet
address range: 10.80.0.0/20 (10.80.0.0 - 10.80.15.255 (4096 addresses))
Address: 10.80.0.0 00001010.01010000.0000 0000.00000000
Netmask: 255.255.240.0 = 20 11111111.11111111.1111 0000.00000000
Wildcard: 0.0.15.255 00000000.00000000.0000 1111.11111111
⇒
Network: 10.80.0.0/20 00001010.01010000.0000 0000.00000000 (Class A)
Broadcast: 10.80.15.255 00001010.01010000.0000 1111.11111111
HostMin: 10.80.0.1 00001010.01010000.0000 0000.00000001
HostMax: 10.80.15.254 00001010.01010000.0000 1111.11111110
Hosts/Net: 4094 (Private Internet)
new subnet
address range: 10.80.0.0/20 (10.80.0.0 - 10.80.15.255 (4096 addresses))
Address: 10.80.0.0 00001010.01010000.0000 0000.00000000
Netmask: 255.255.240.0 = 20 11111111.11111111.1111 0000.00000000
Wildcard: 0.0.15.255 00000000.00000000.0000 1111.11111111
⇒
Network: 10.80.0.0/20 00001010.01010000.0000 0000.00000000 (Class A)
Broadcast: 10.80.15.255 00001010.01010000.0000 1111.11111111
HostMin: 10.80.0.1 00001010.01010000.0000 0000.00000001
HostMax: 10.80.15.254 00001010.01010000.0000 1111.11111110
Hosts/Net: 4094 (Private Internet)
subnet address range 10.80.0.0/24 , 10.80.00 - 10.80.0.255 (256 addresses)
- unselect accelerated networking
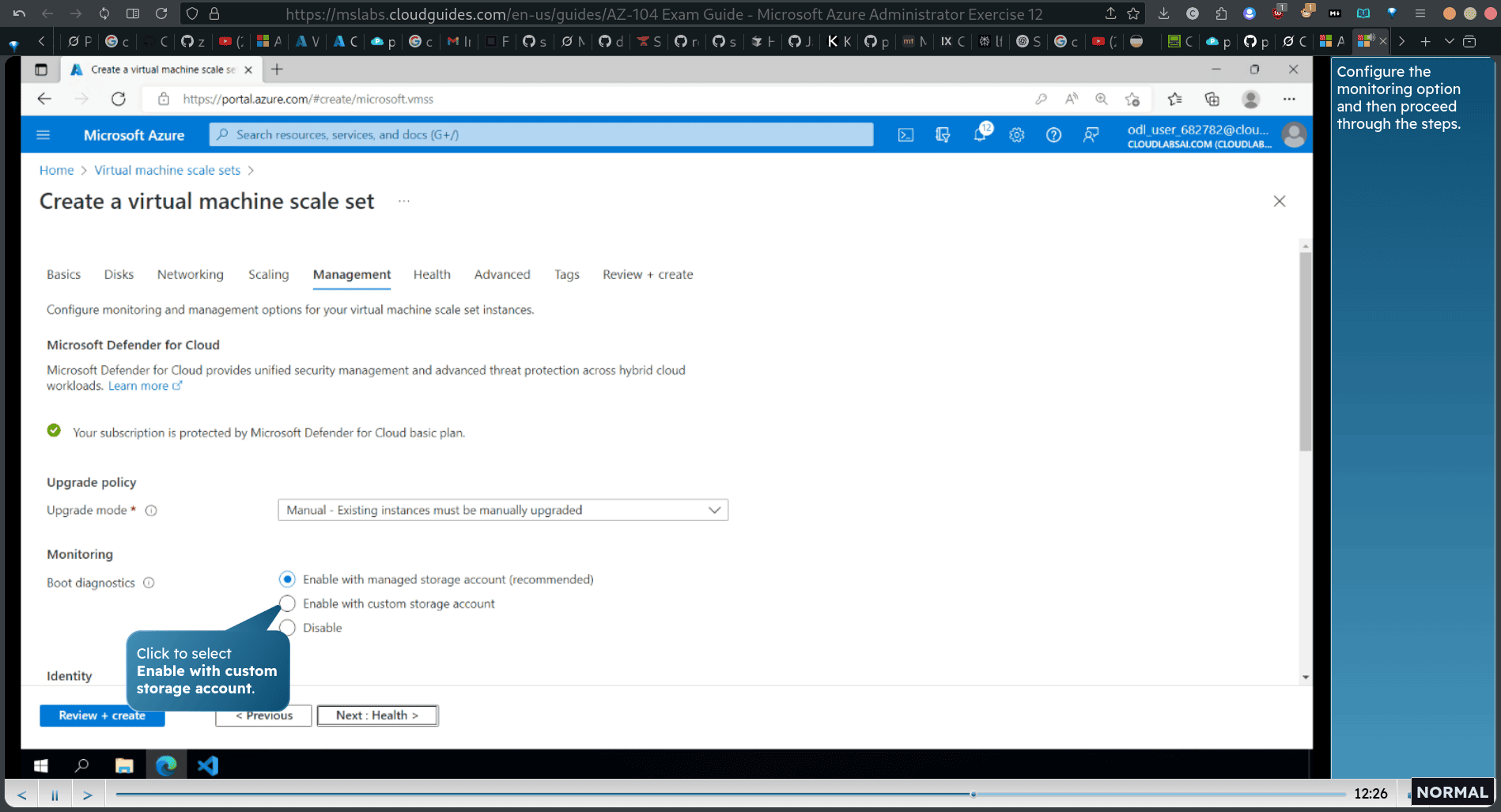
- Enable with custom storage account
Os manual update
creat
 deploment → template
deploment → template
 review
review
-
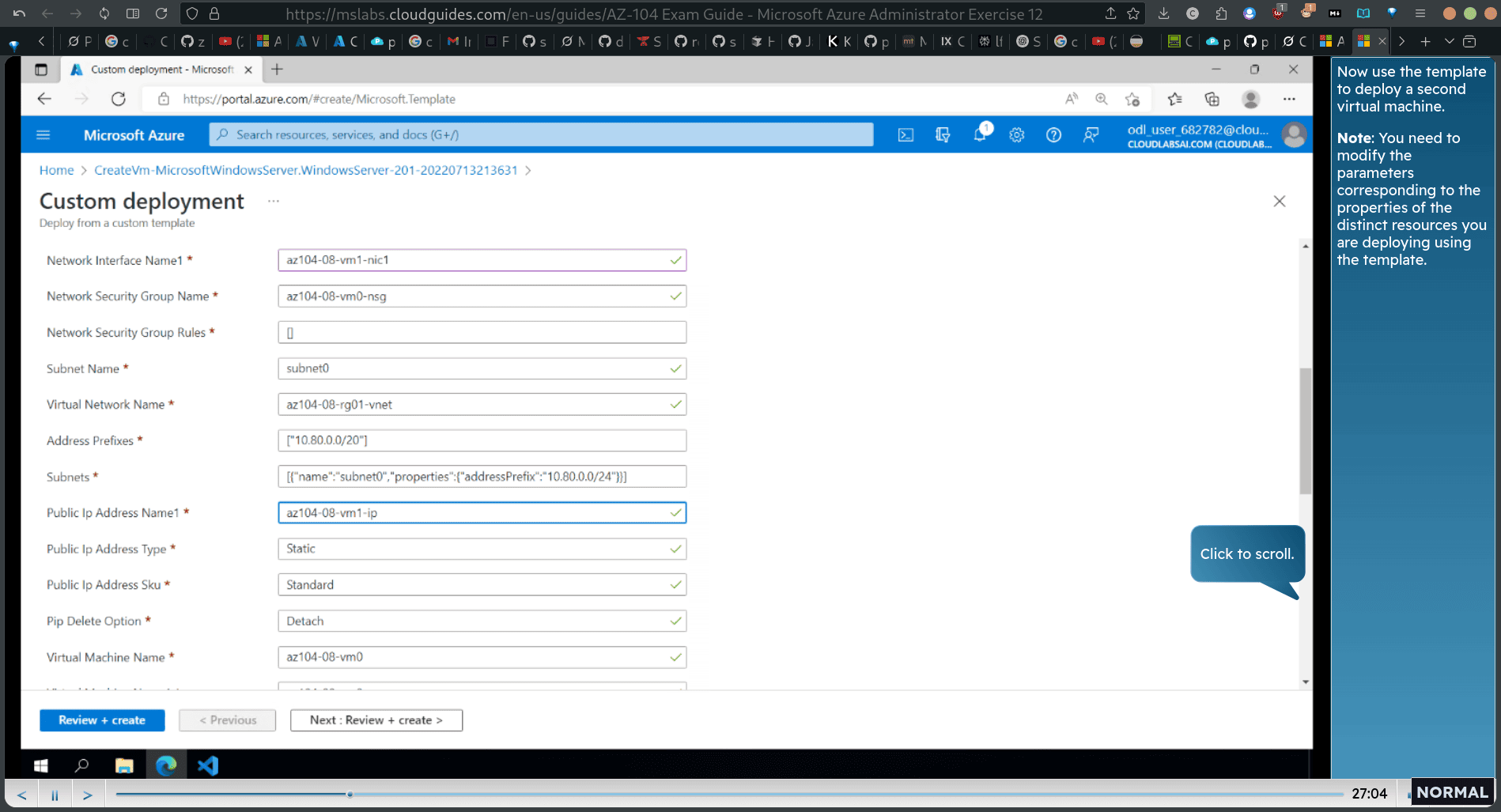
Now use the template to deploy a second virtual machine.
-
Note: You need to modify the parameters corresponding to the properties of the distinct resources you are deploying using the template.
click deploy
 changed it
changed it
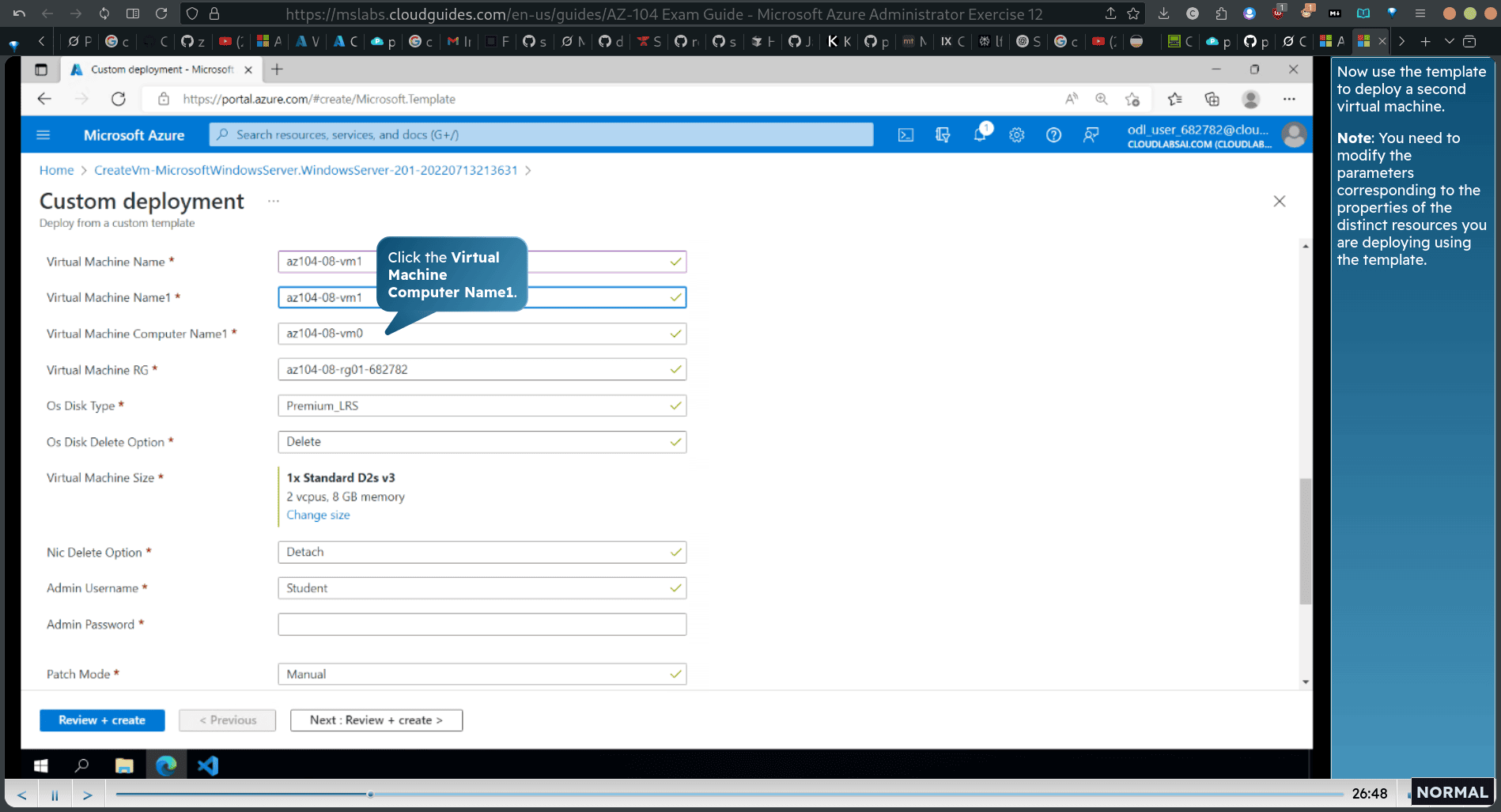 from vm0 to vm1
from vm0 to vm1
zone → 2
Task 2: Configure Azure virtual machines using a virtual machine extension
storage → container → new container
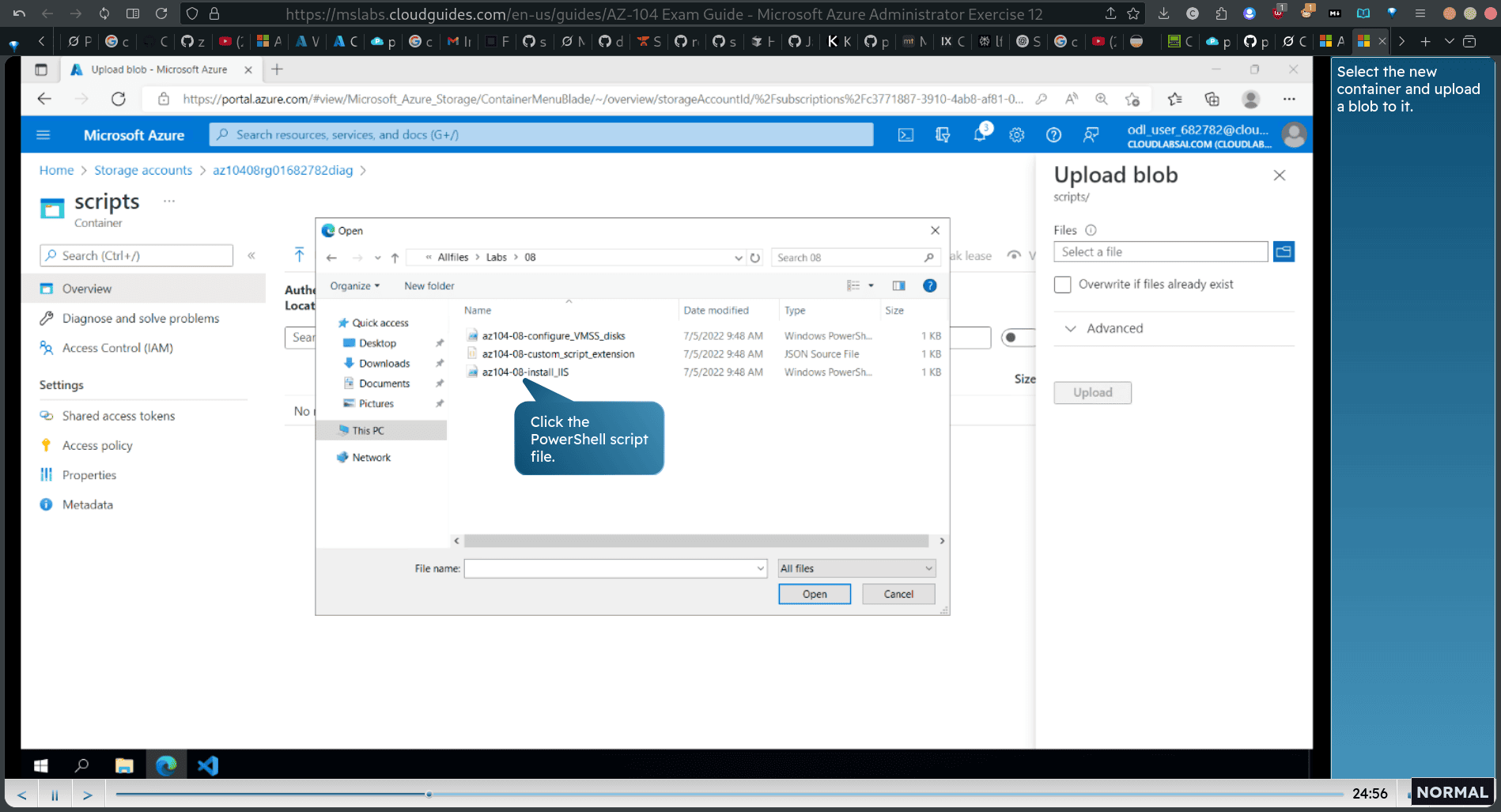
search → vm → first vm0
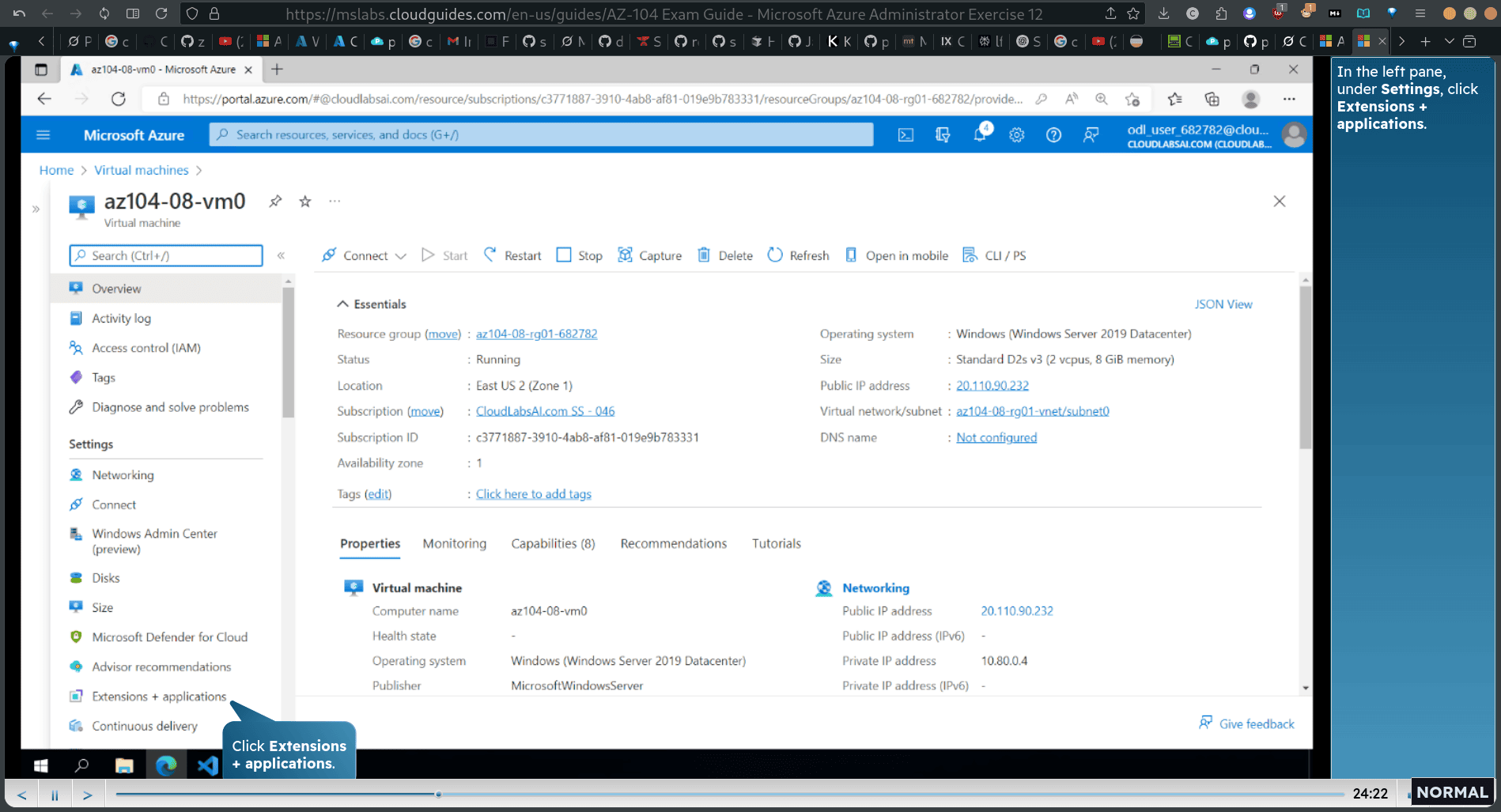
- Extensions + applications
add ing Search for Custom Script Extension and select it.
browser → click the scrip that upload early
review and create
select the second vm(vm1)
→ automation → export template → deploy (wtf)
On the Custom deployment blade, click Edit template.
edit Note: This section of the template defines the same Azure virtual machine Custom Script Extension that you deployed earlier to the first virtual machine via Azure PowerShell.
insert in 20 line that extension :
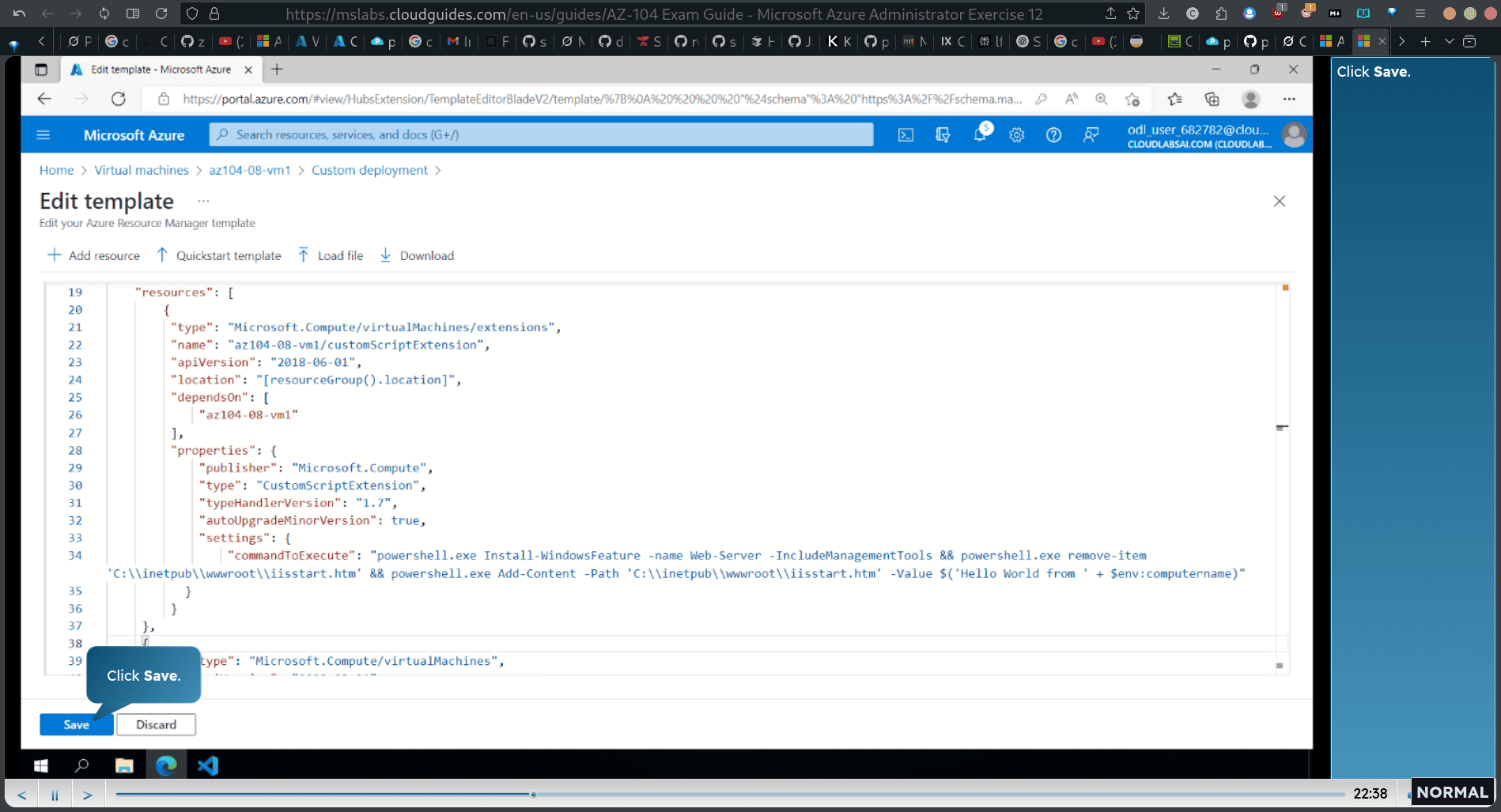 below resource
below resource
“"Microsoft.Compute/virtualMachines/extensions™,
“az104-08-vml/customScriptExtension®,
“apiVersion”: "2018-06-01",
“location": "[resource6roup().location]",
“dependsOn”: [
"az104-08-vm1"
1
“properties”: {
“publisher”: "Microsoft.Compute”,
“type": “"CustomScriptExtension”,
"typeHandlerVersion”: "1.7",
“autoUpgradeMinorVersion”: true,
"settings": {
“commandToExecute”: “"powershell.exe Install-WindowsFeature -name Web-Server -IncludeManagementTools & powershell.exe remove-item
'C:\\inetpub\\wwwroot\\iisstart.htm' && powershell.exe Add-Content -Path 'C:\\inetpub\\wwwroot\\iisstart.htm' -Value $('Hello World from ' + $env:computername)"
powershell.exe Install-WindowsFeature -Name Web-Server -IncludeManagementTools; `powershell.exe Remove-Item 'C:\inetpub\wwwroot\iisstart.htm' -Force;`
powershell.exe Add-Content -Path 'C:\inetpub\wwwroot\iisstart.htm' -Value ("Hello World from " + $env:COMPUTERNAME)create
verify the vm1 that just craetd
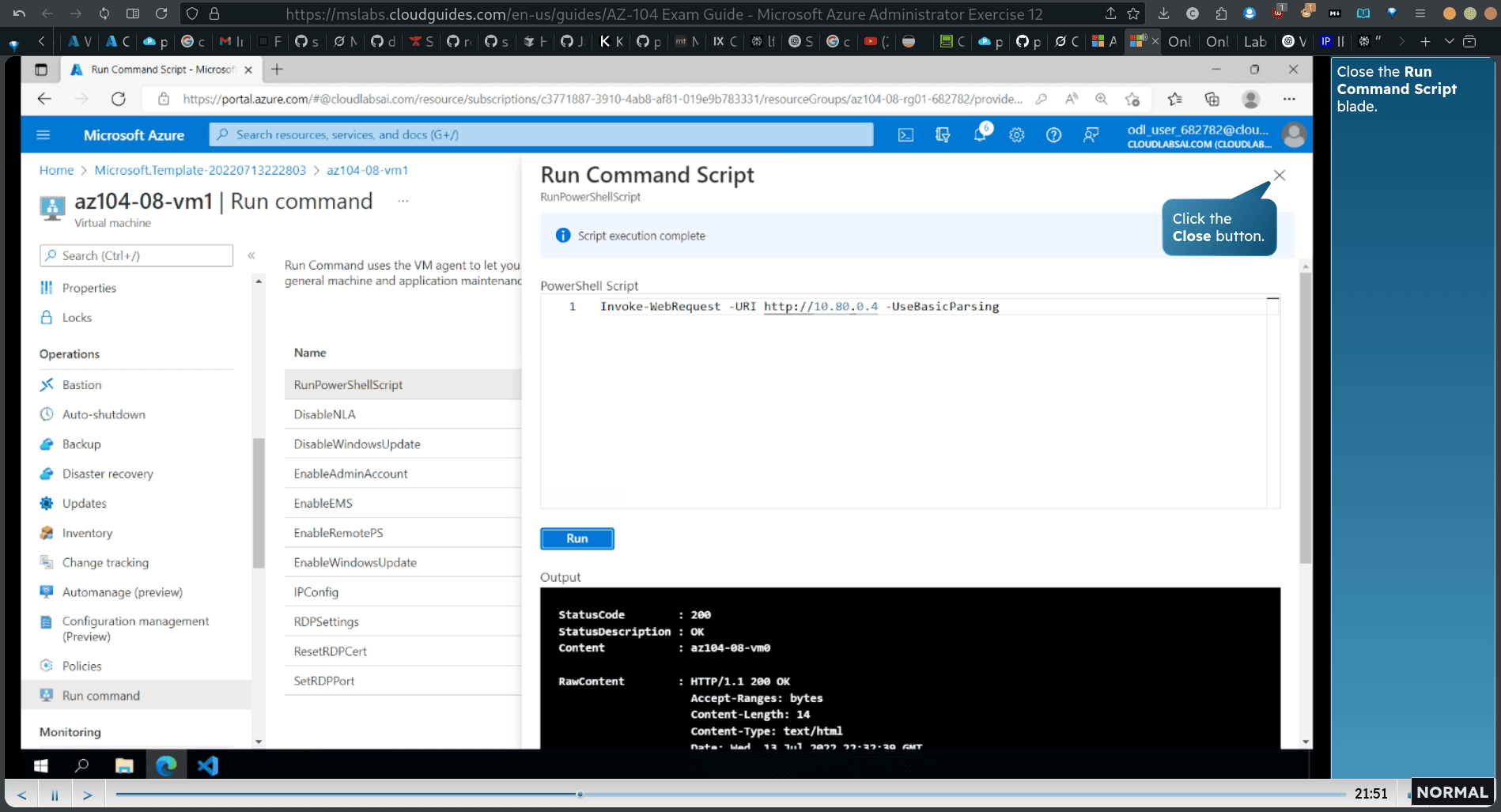
run powershellscrpit in that
- Note: The - UseBasi Parslng parameter is necessary to eliminate dependency on Microsoft Edge to complete the execution of the cmdlet.
Invoke-WebRequest -URI http://10.80.0.4 -UseBasicParsing
Task 3: Scale compute capacity and storage for Azure virtual machines
vm0 → size → ds1_v2 disk → creat and attach a new disk
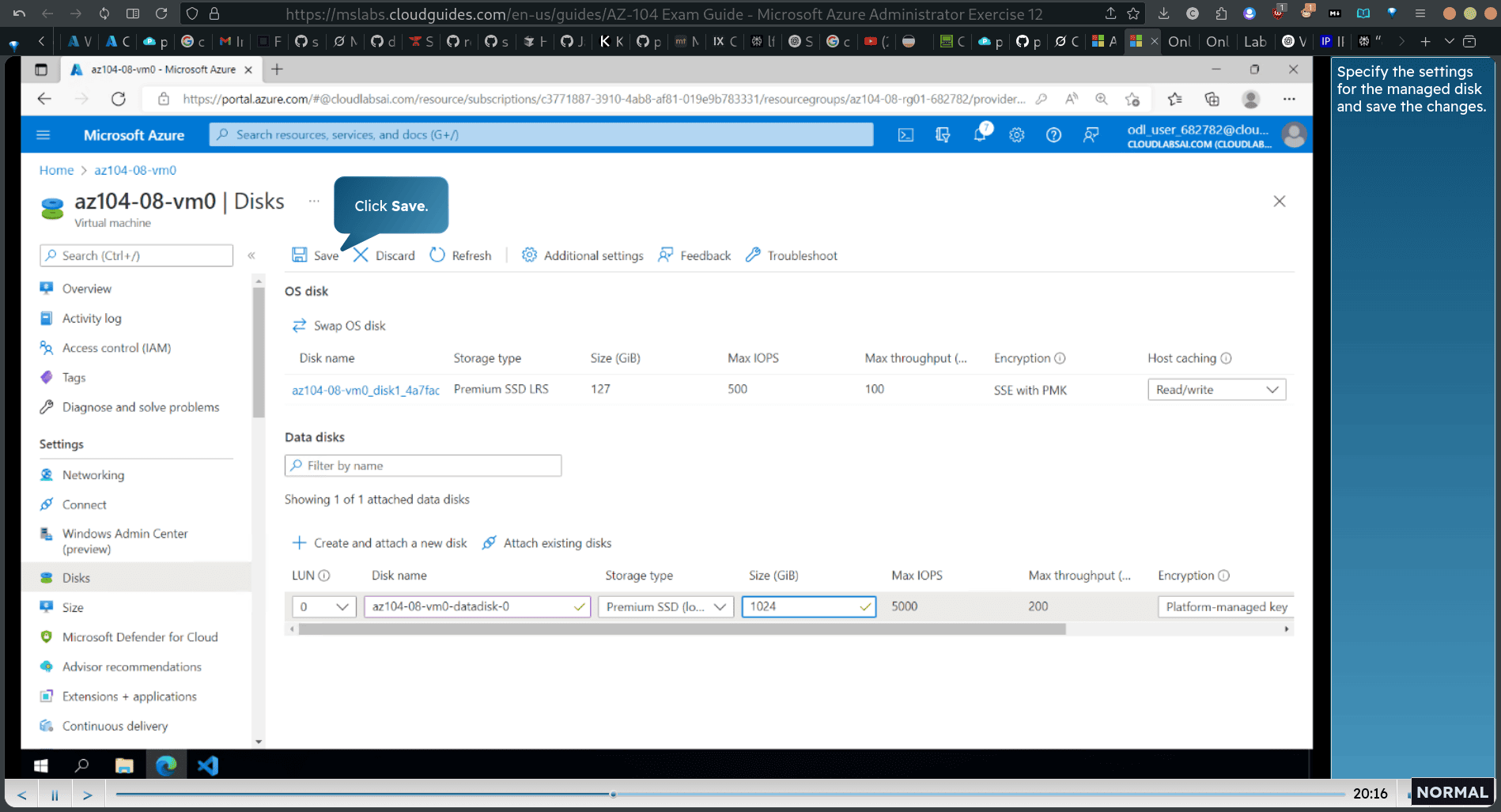
powershellscrpit
- Run the command script as shown to create a Z: drive consisting of the two newly attached disks with the simple layout and fixed provisioning.
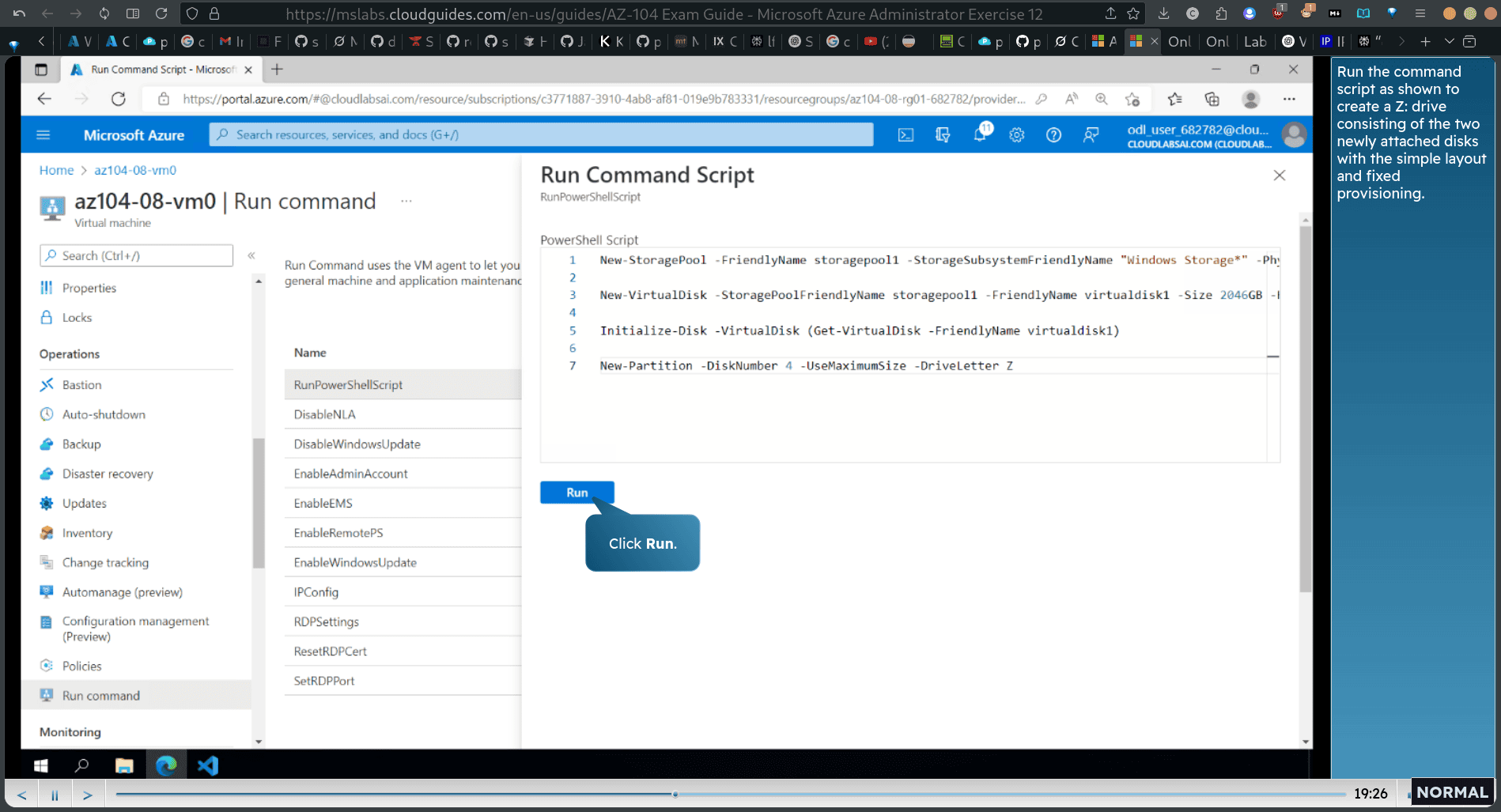
Sure! Let’s reconstruct the correct full PowerShell script based on the OCR output and your goal:
🎯 Goal:
-
Create a Z: drive
-
Combine 2 newly attached disks
-
Use:
- Simple layout (striped, no resiliency)
- Fixed provisioning
-
Likely in Windows (e.g., Azure VM with Windows Server)
✅ Corrected & Completed PowerShell Script:
# Step 1: Create a storage pool from available physical disks
New-StoragePool -FriendlyName "storagepool1" `
-StorageSubsystemFriendlyName "Windows Storage*" `
-PhysicalDisks (Get-PhysicalDisk -CanPool $True)
# Step 2: Create a virtual disk using the storage pool
New-VirtualDisk -StoragePoolFriendlyName "storagepool1" `
-FriendlyName "virtualdisk1" `
-Size 2046GB `
-ResiliencySettingName "Simple" `
-ProvisioningType "Fixed"
# Step 3: Initialize the new virtual disk
Initialize-Disk -VirtualDisk (Get-VirtualDisk -FriendlyName "virtualdisk1")
# Step 4: Create a new partition and assign drive letter Z
New-Partition -DiskNumber (Get-Disk | Where-Object PartitionStyle -Eq "RAW").Number `
-UseMaximumSize `
-DriveLetter Z | Format-Volume -FileSystem NTFS -Confirm:$false🧠 Explanation:
| Command | Purpose |
|---|---|
New-StoragePool | Creates a storage pool from all available unpooled disks |
New-VirtualDisk | Creates a simple (striped) virtual disk with fixed provisioning |
Initialize-Disk | Prepares the virtual disk for use |
New-Partition | Creates a full-size partition and assigns drive letter Z |
Format-Volume | Formats the partition as NTFS without confirmation |
⚠️ Important Notes:
-ResiliencySettingName "Simple"= No redundancy (good for performance but no fault tolerance).-ProvisioningType "Fixed"= Pre-allocates the full 2046GB (not thin).-StorageSubsystemFriendlyName "Windows Storage*"matches the Windows Storage Spaces subsystem.
another vm → vm1 → export tempalet → deploy edit template → scroll down and replace the vm size
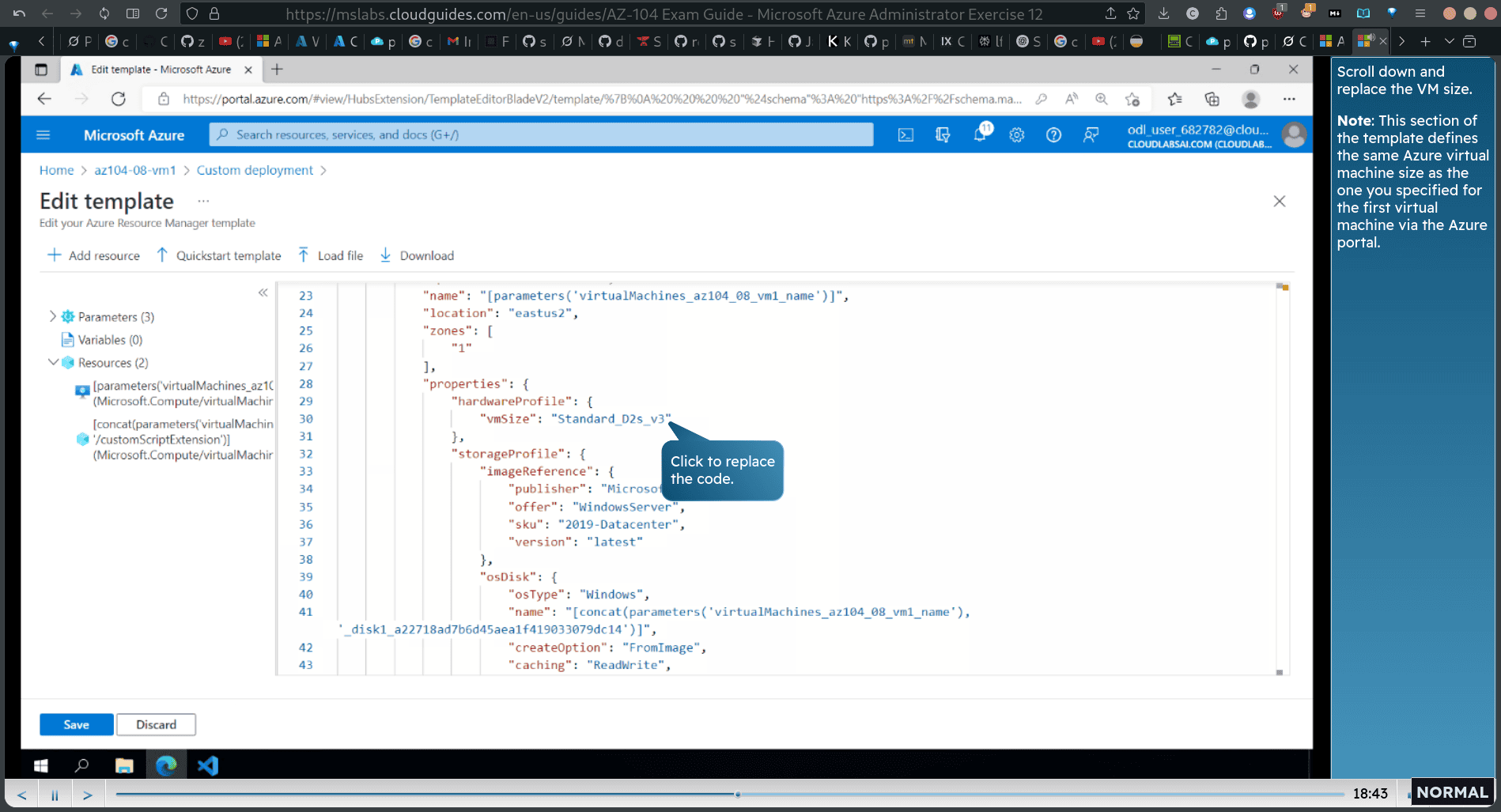 to ds1_v2
to ds1_v2
Replace line 51 with the code as shown to create two managed disks and attach them to the virtual machine.
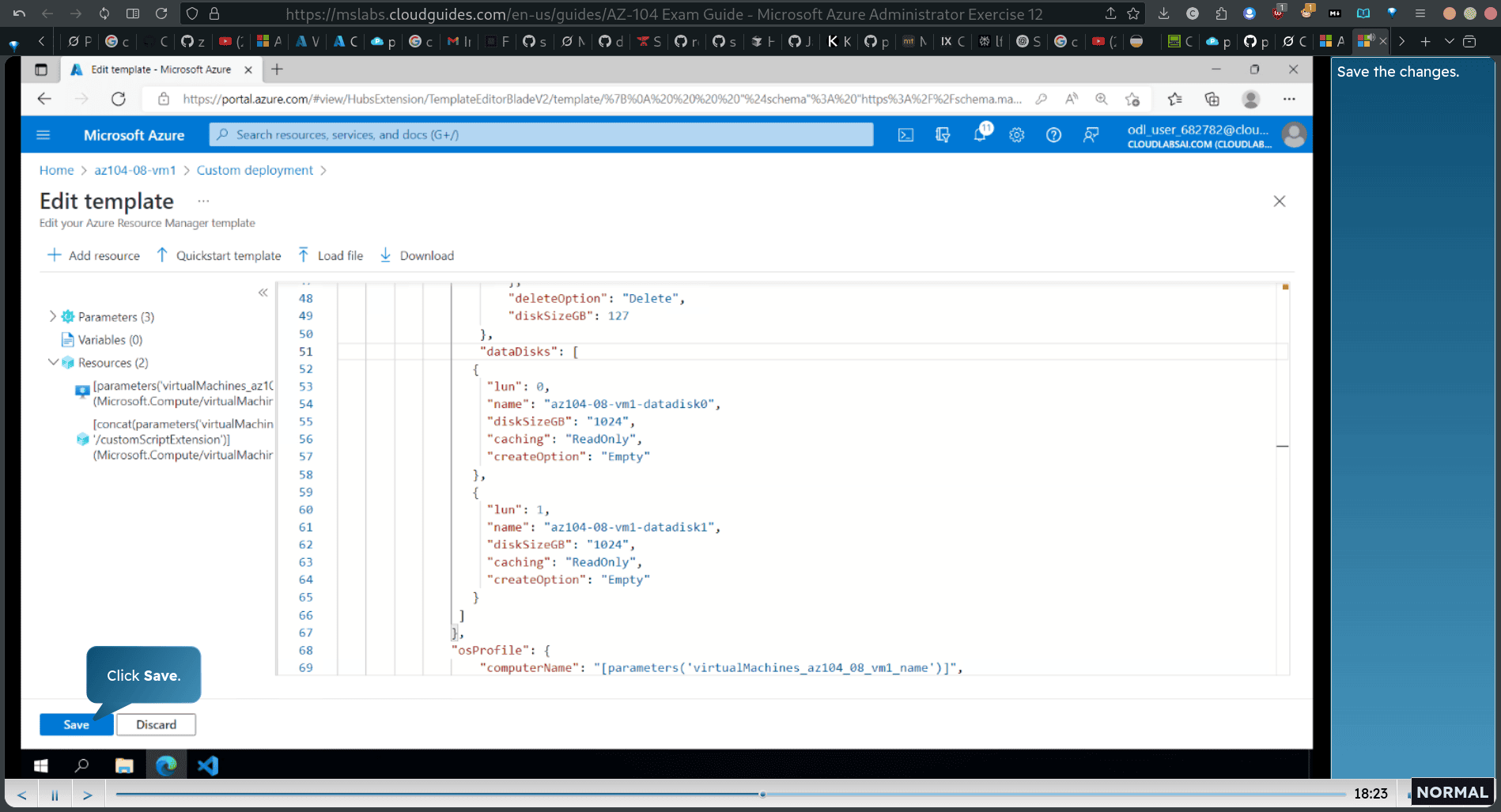 adding two data disks
adding two data disks
craete
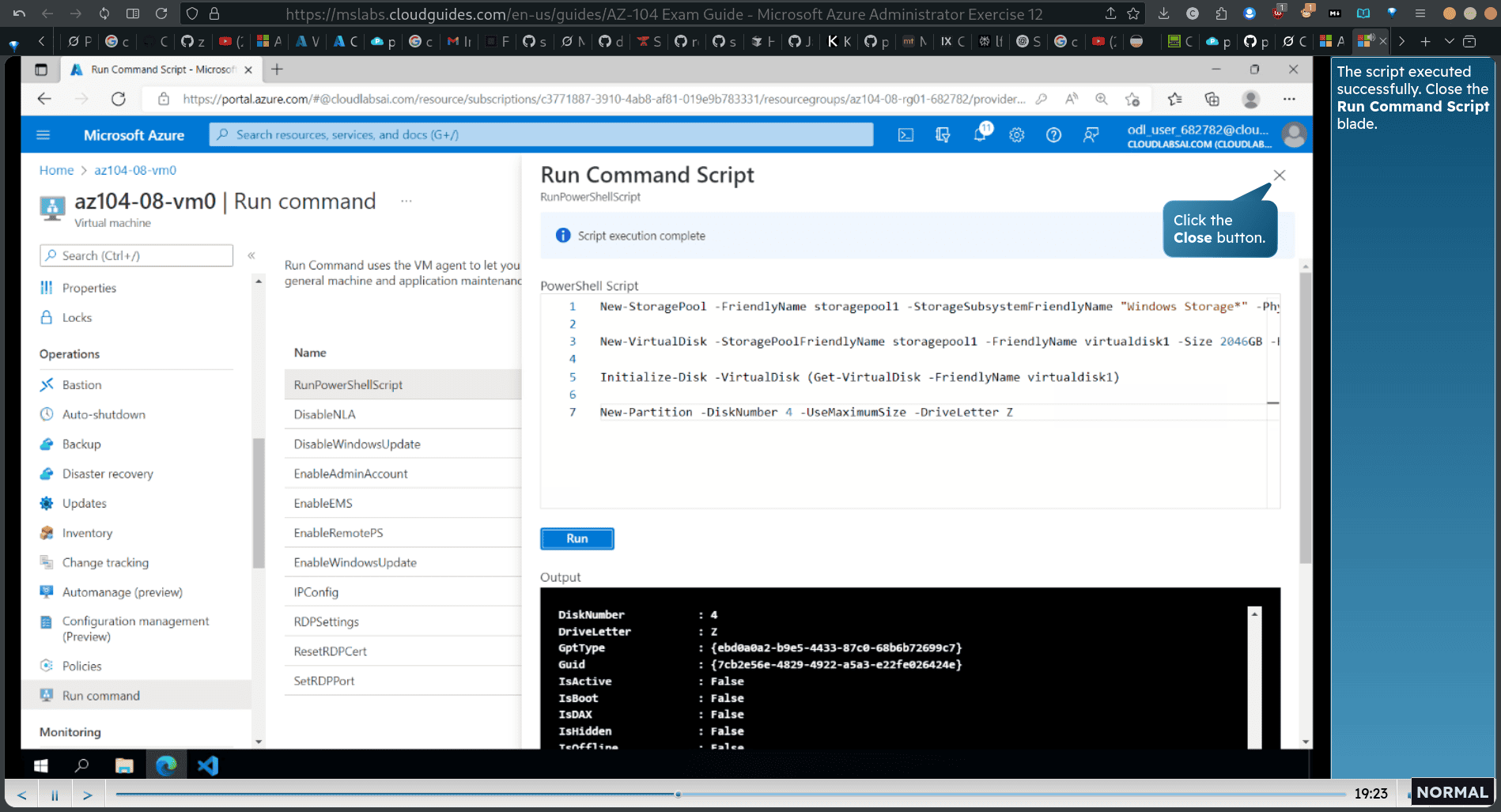
click vm1 → run command
Run the command script as shown to create a Z: drive consisting of the two newly attached disks with the simple layout and fixed provisioning.
same as previous
Task 4: Register resource providers
Run the commands as shown tfo register the Microsoft.Insights and Microsoft.AlertsMana gement resource providers.
Register-AzResourceProvider -ProviderNamespace Microsoft.Insights
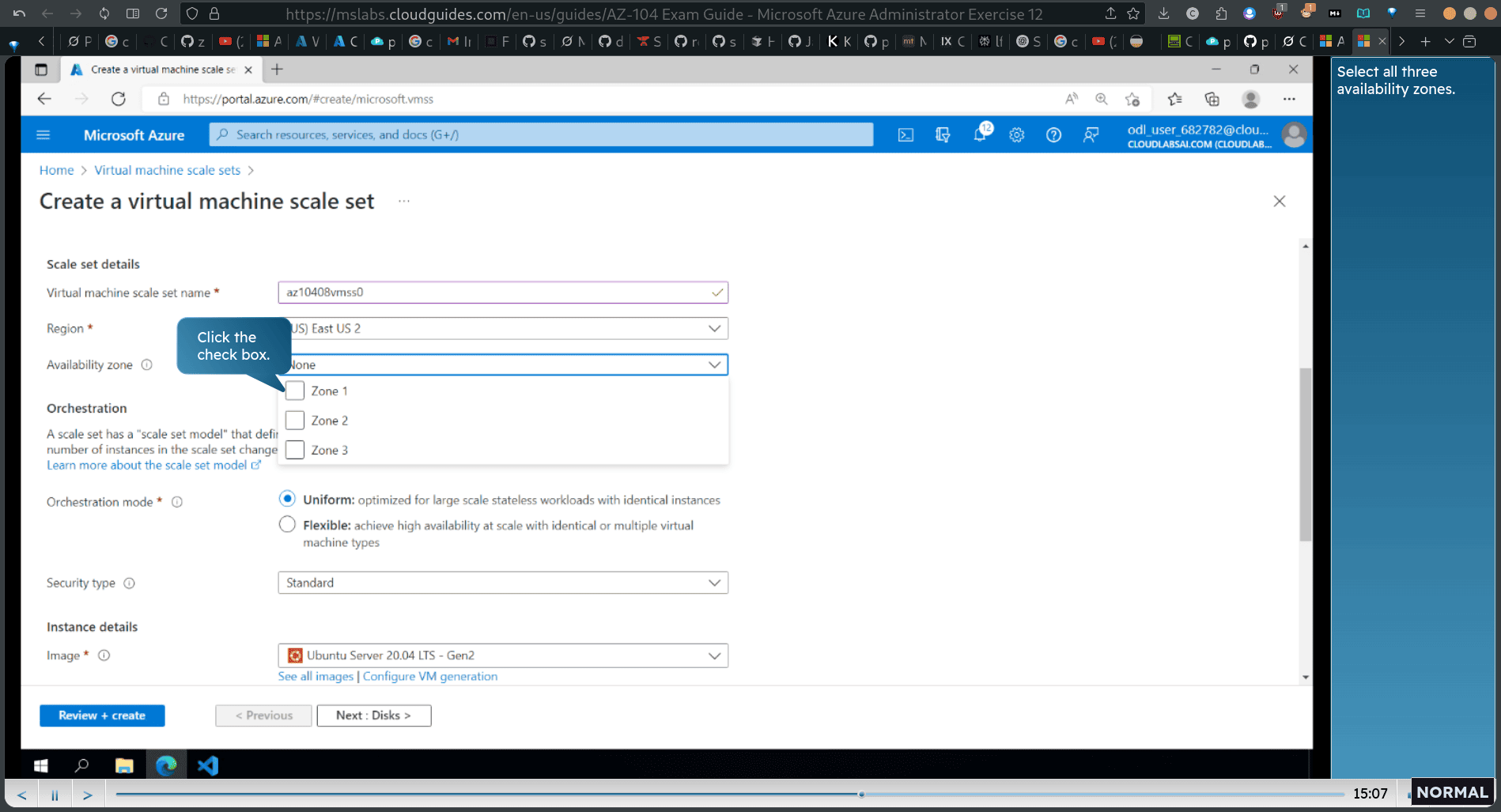
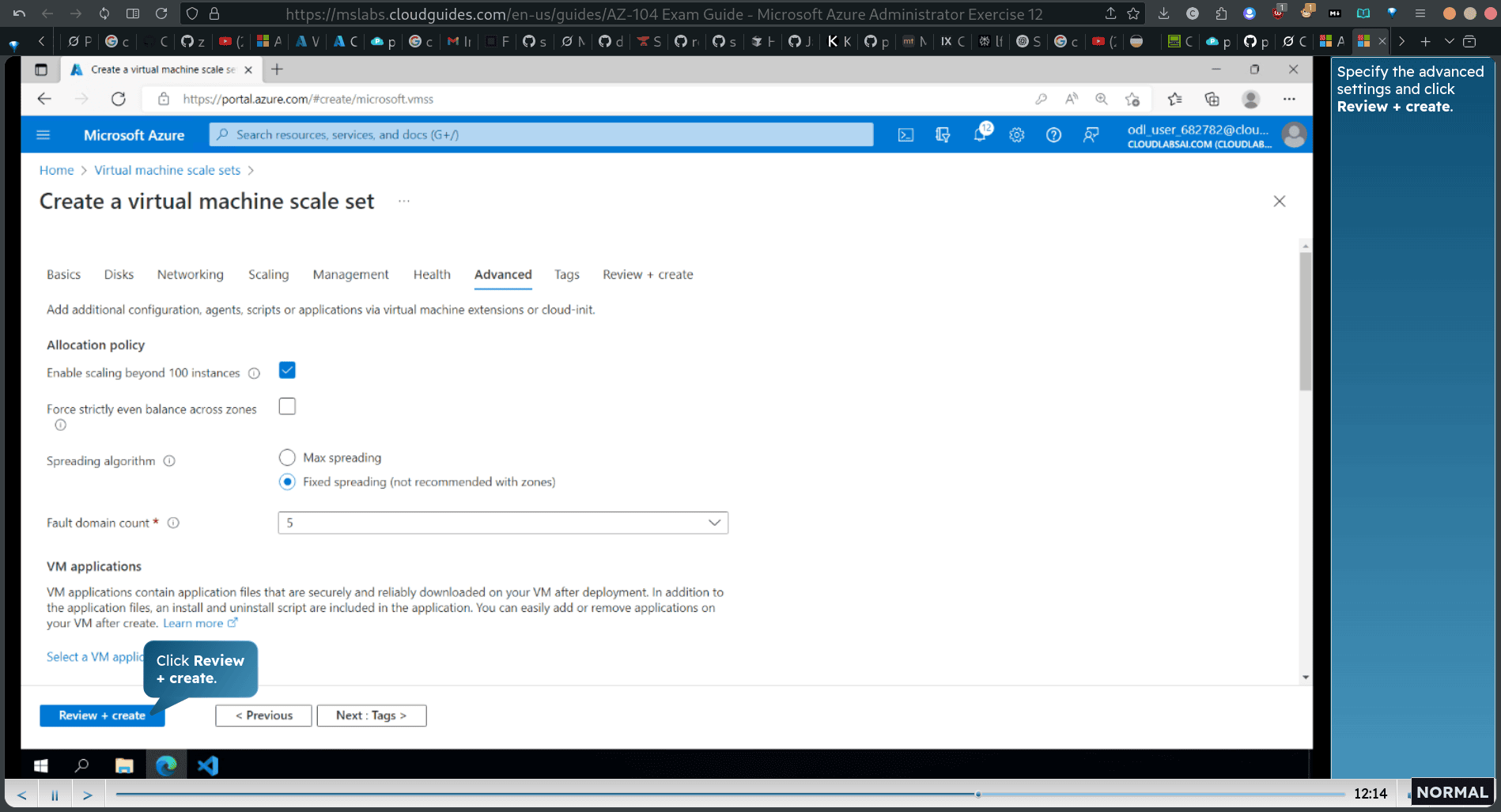
Task 5: Deploy a zone-resilient Azure virtual machine scale set using the Azure portal
search vm scale set
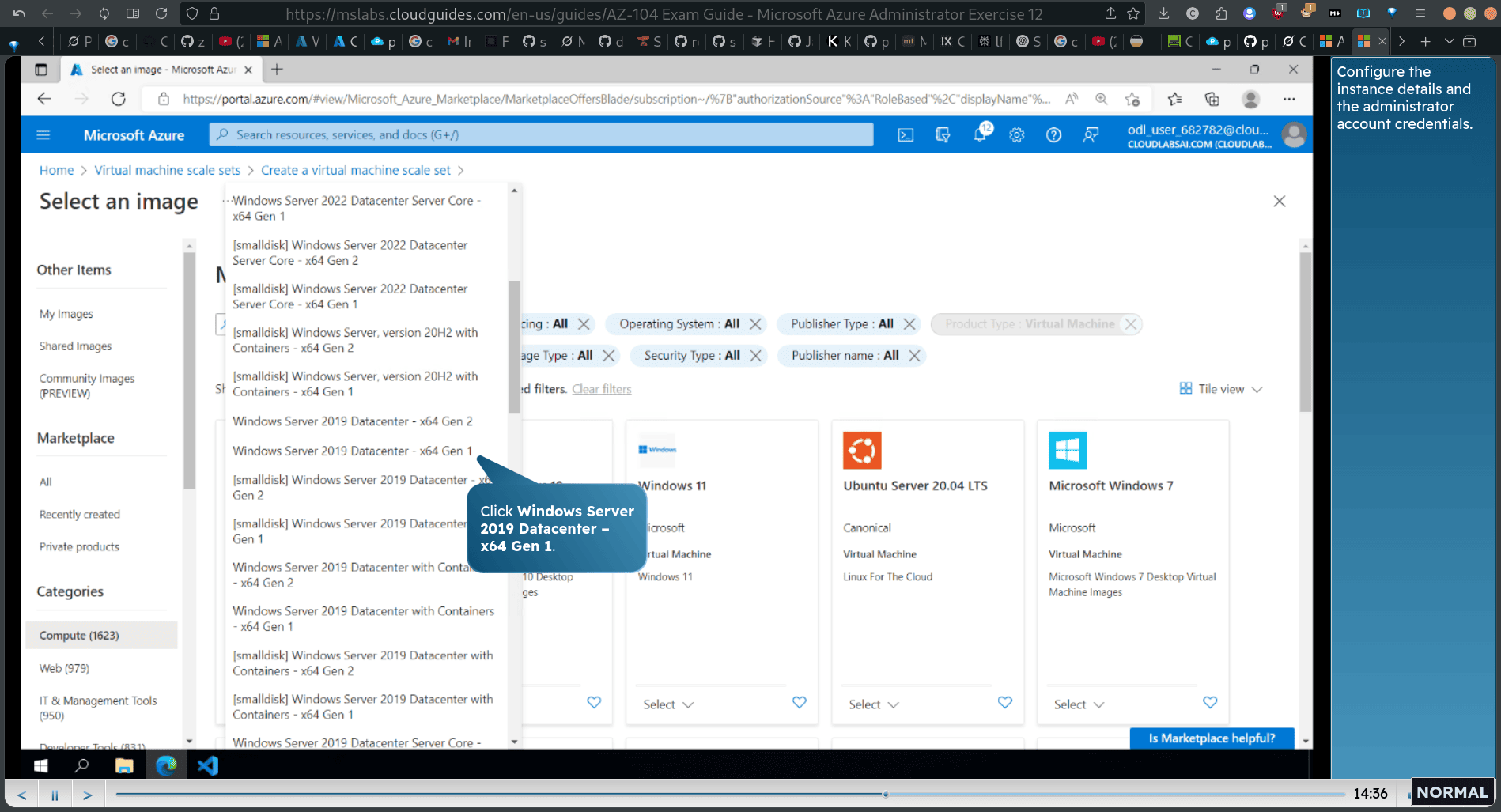 window datacenter 2019 x64 gen1
window datacenter 2019 x64 gen1
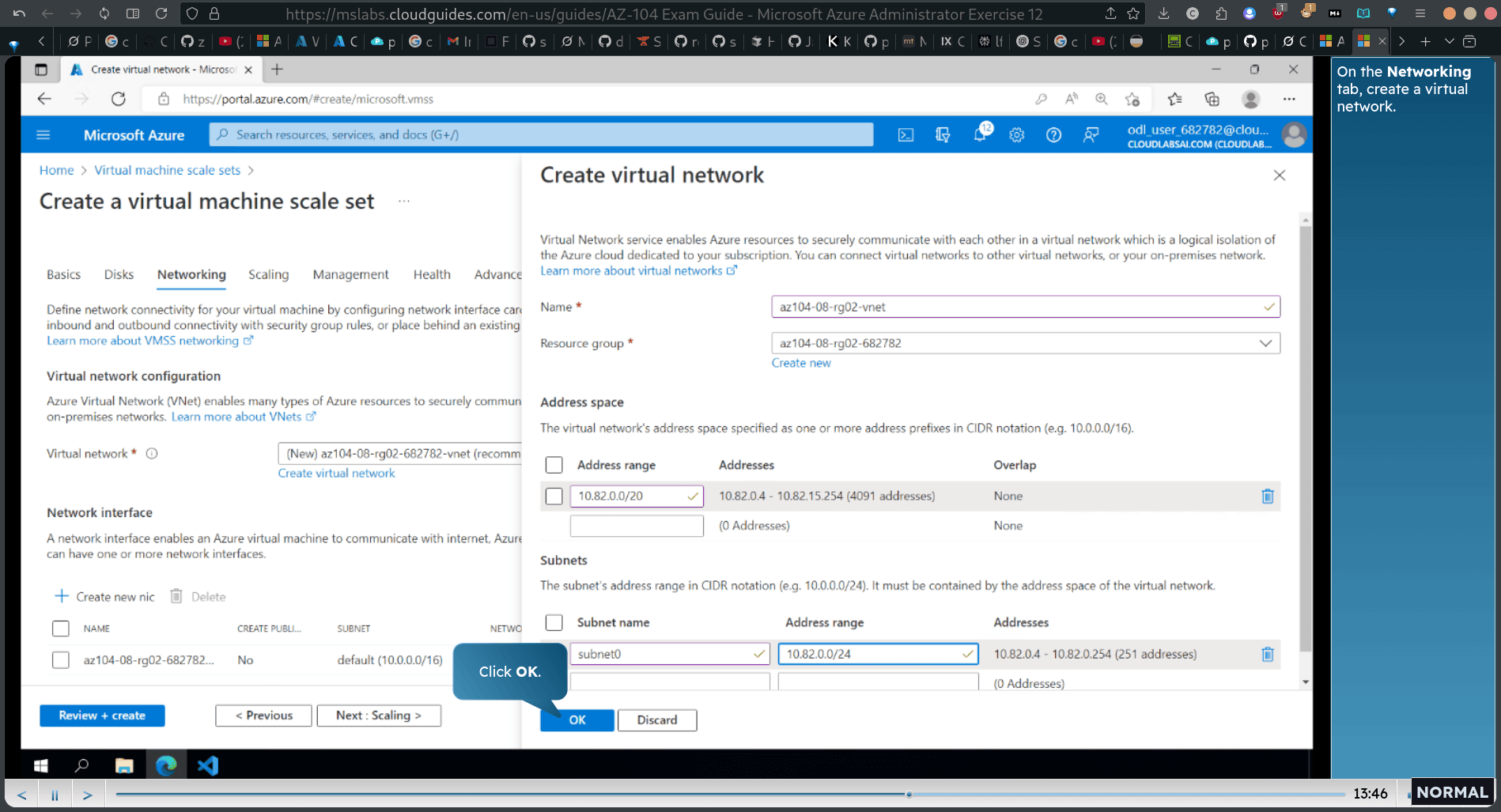 new vnet
new vnet
-
Set NIC network security group fo Advanced and then create a new network security group.
-
create new network security group
adding inbond rule
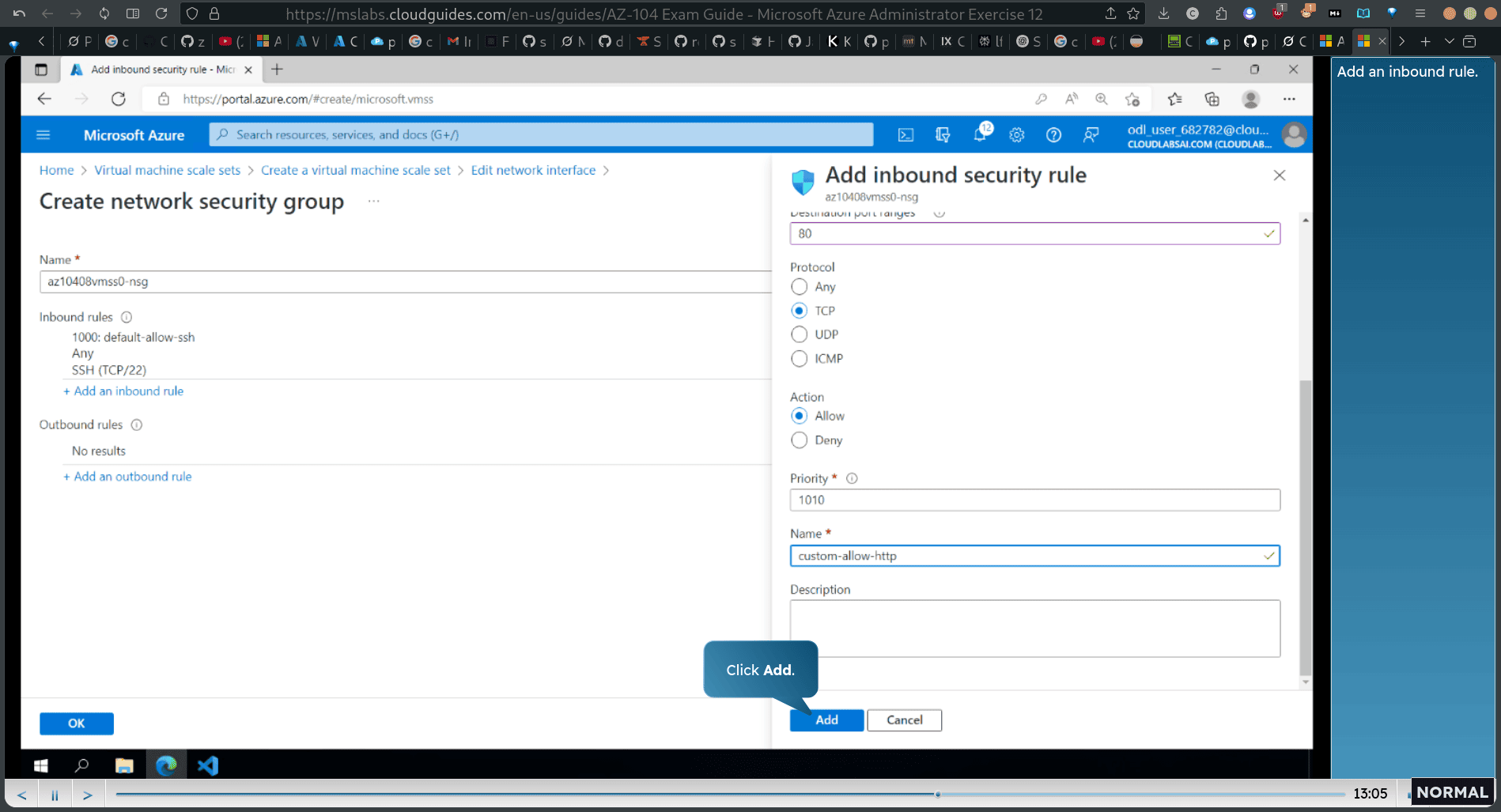 set enable public ip address
set enable public ip address
 enable Fixed spreading (not recommended with zones)
enable Fixed spreading (not recommended with zones)
click the vm scale set newly
Task 6: Configure an Azure virtual machine scale set using a virtual machine extension
storage ac(second one ) → container → new container (scrpt) → upload a blog → script
return to previous vm scale set item → extention & applicaton→ search customer scrip ext → select prvieous uploaded blog script
return to previous vm scale set item → instances Select the check boxes next to the virtual machine scale set instances and then click Upgrade.
search load balancer → select → frontend ip → copy public ip →test the ip
Task 7: Scale compute and storage for the Azure virtual machine scale set
return to previous vm scale set item → size → ds1_v2 → resize → insance → upgrade → select the first instance
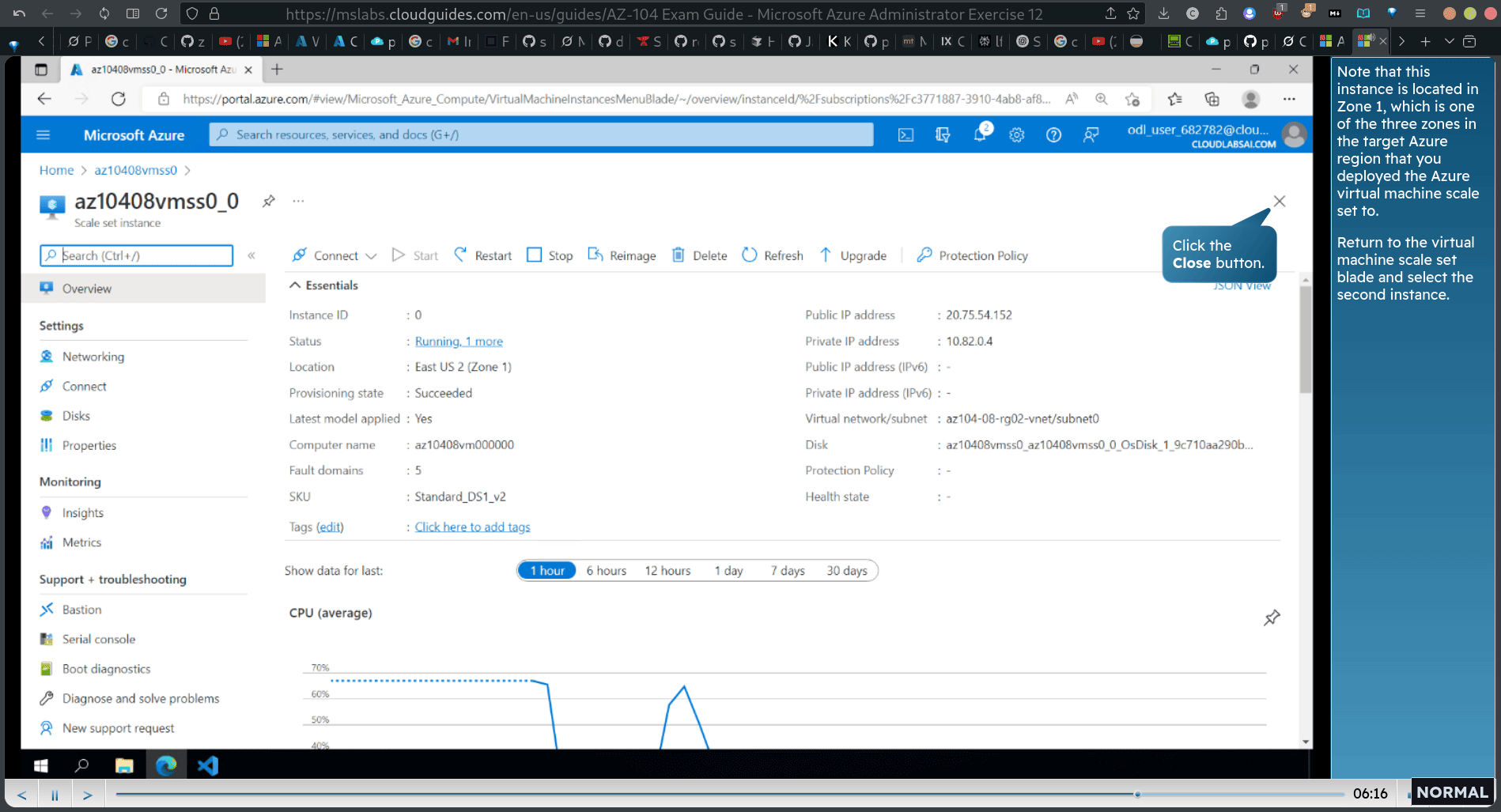
- Note that this instance is located in Zone 1, which is one of the three zones in the target Azure region that you deployed the Azure virtual machine scale set to. Return to the virtual machine scale set blade and select the second instance.
2nd instance Note that this instance is located in Zone 2, which is another one of the three zones that you deployed the Azure virtual machine scale set fo. Refurn to the Instances blade.
→ scaling → custom autoscale
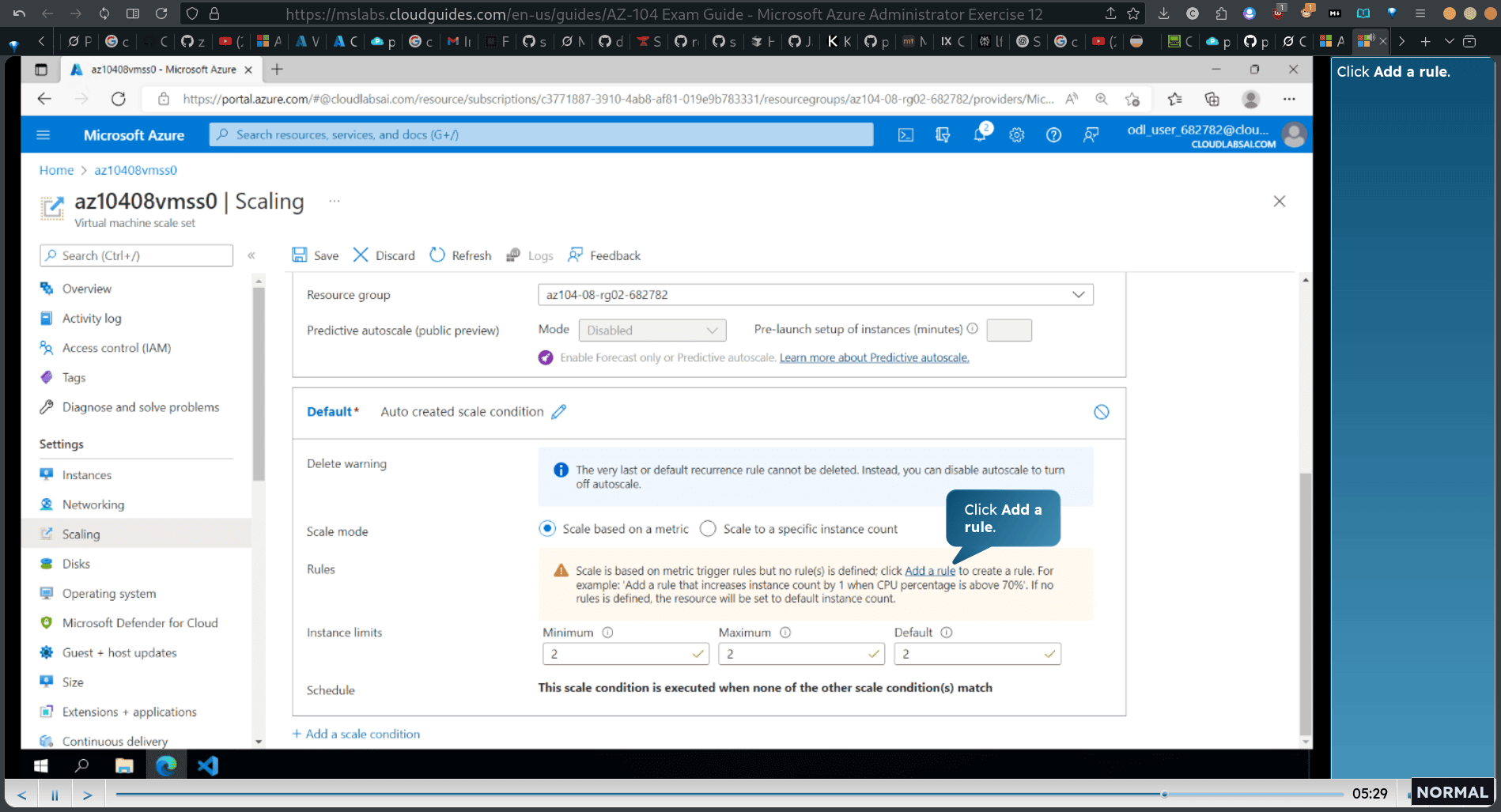 add rule
add rule
select ‘network in total’
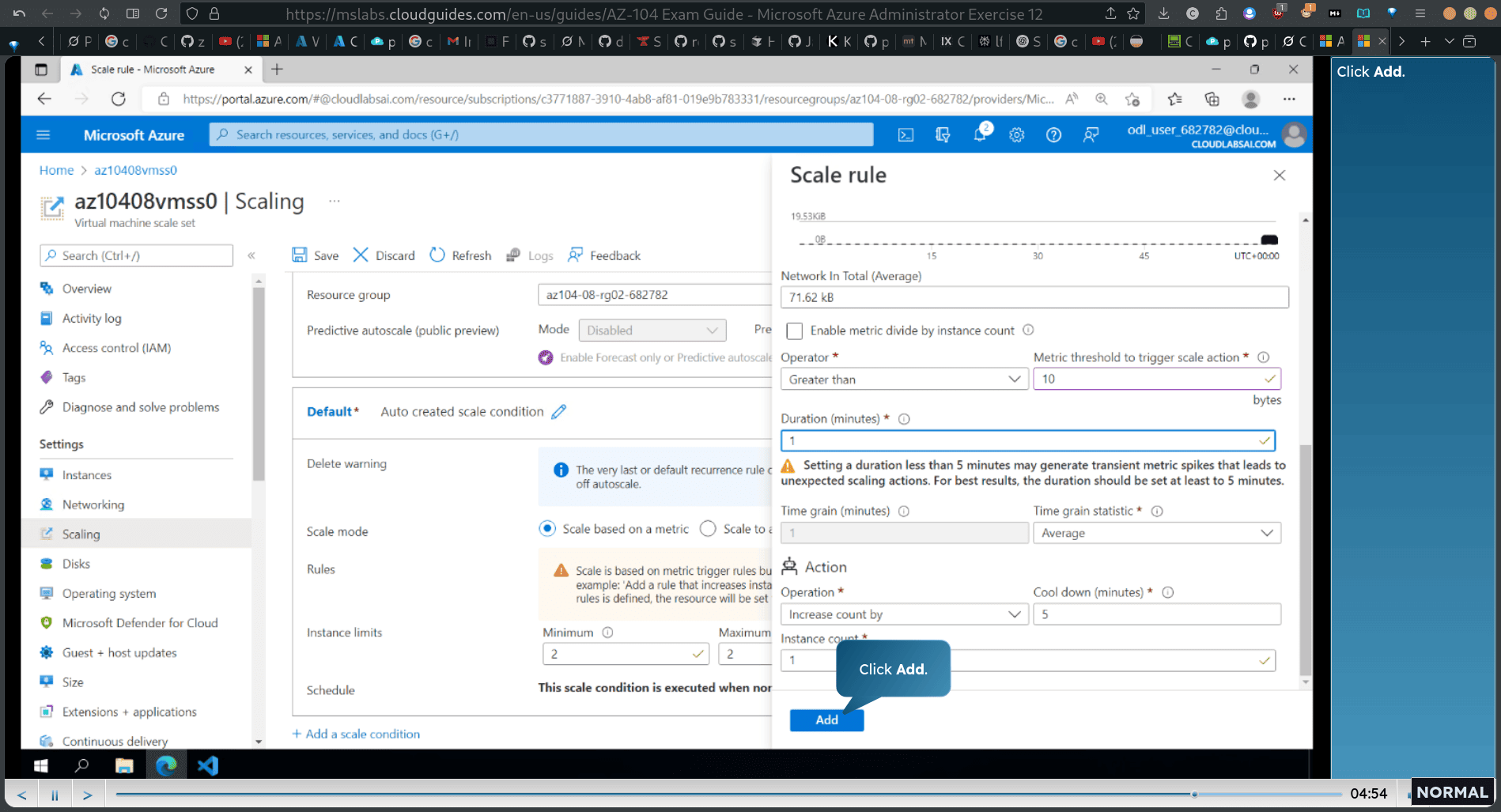
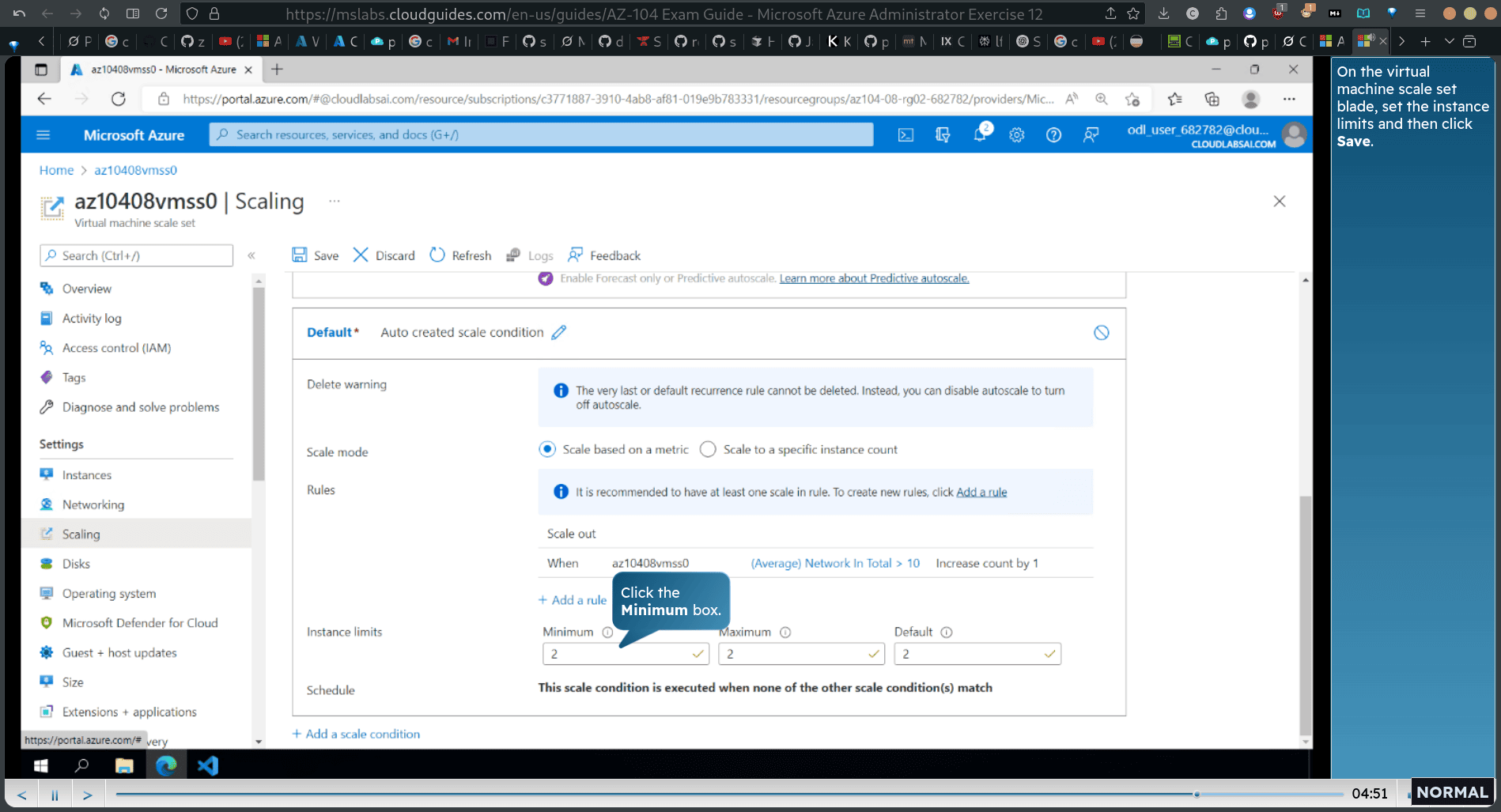
- set the instance limit
SrgName = ‘az104-08-rgh2-682782”
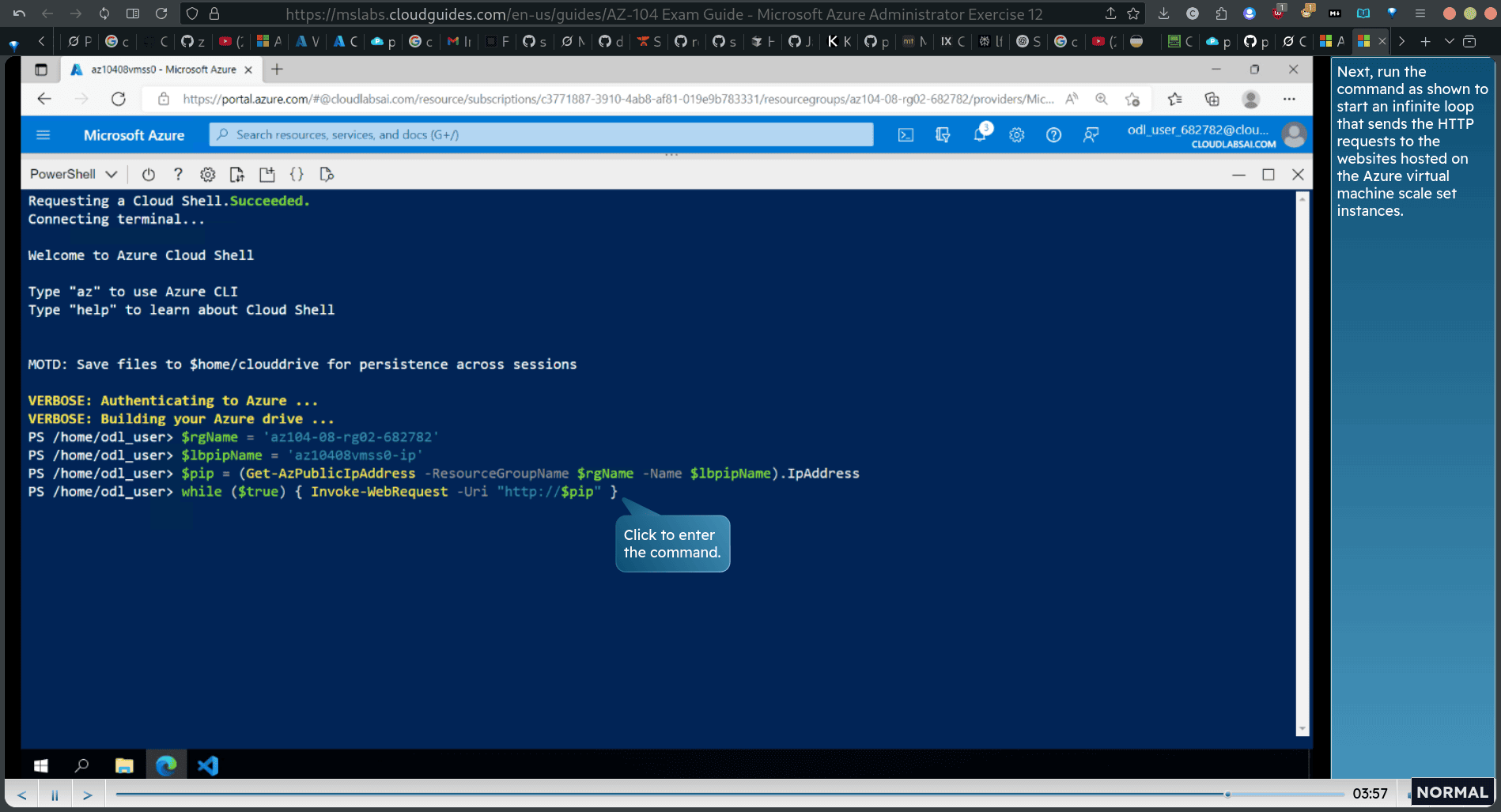
Run the commands as shown to identify the public IP address of the load balancer in front of the Azure virtual machine scale set.
pip = (Get-AzPublicIpAddress -ResourceGroupName lbpipName).IpAddress
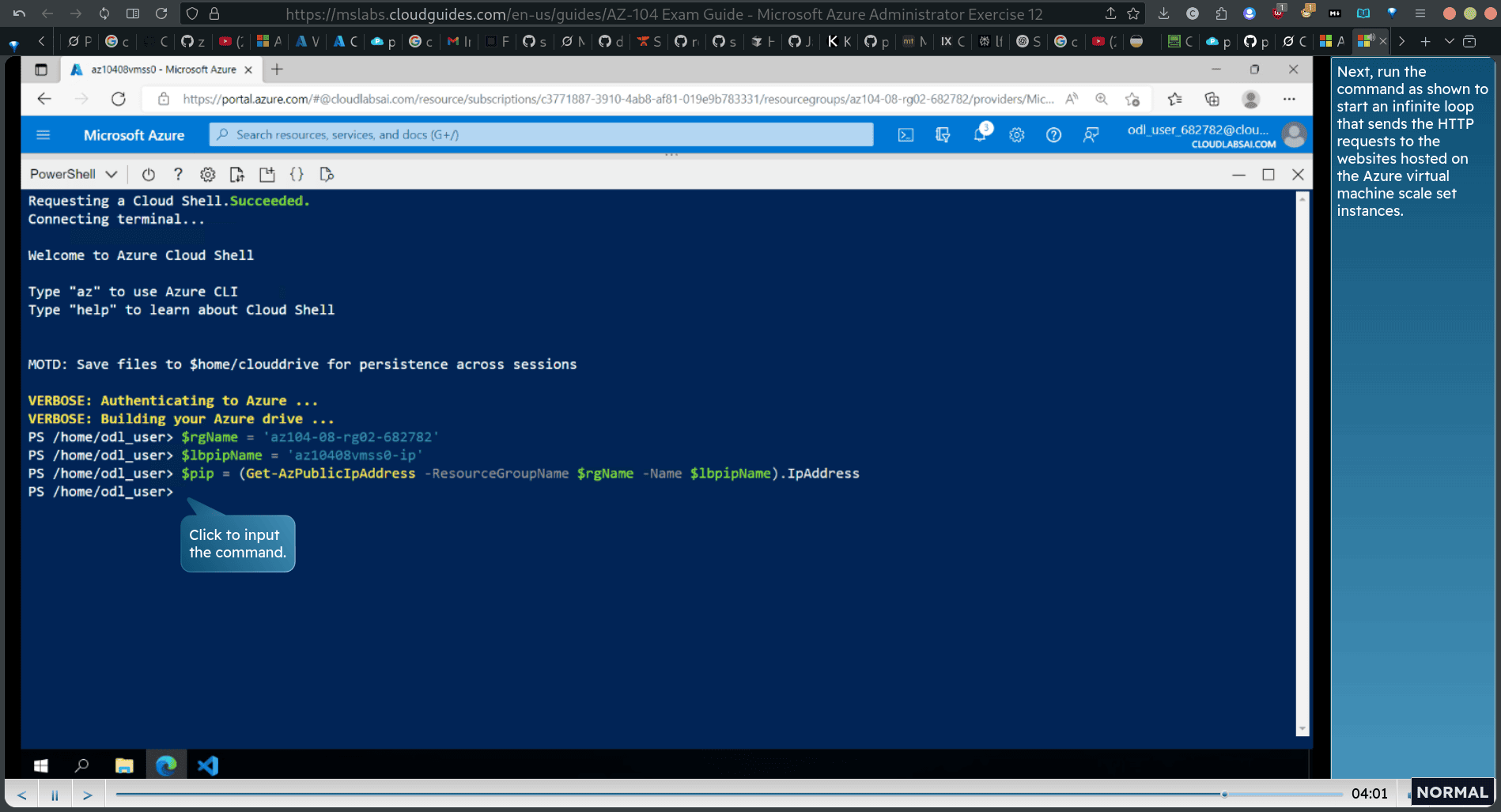
- Next, run the command as shown fo start an infinite loop that sends the HTTP requests to the websites hosted on the Azure virtual machine scale set instances. while (true) { Invoke-WebRequest -Uri “http://pip”” }
return the instance
The third instance has been provisioned. Select it fo view its location.
The location is Zone 3, which is different than the two zones you identified earlier in this task.
back to vm scale set → disk → craeate and attach disk HDD 32 gb
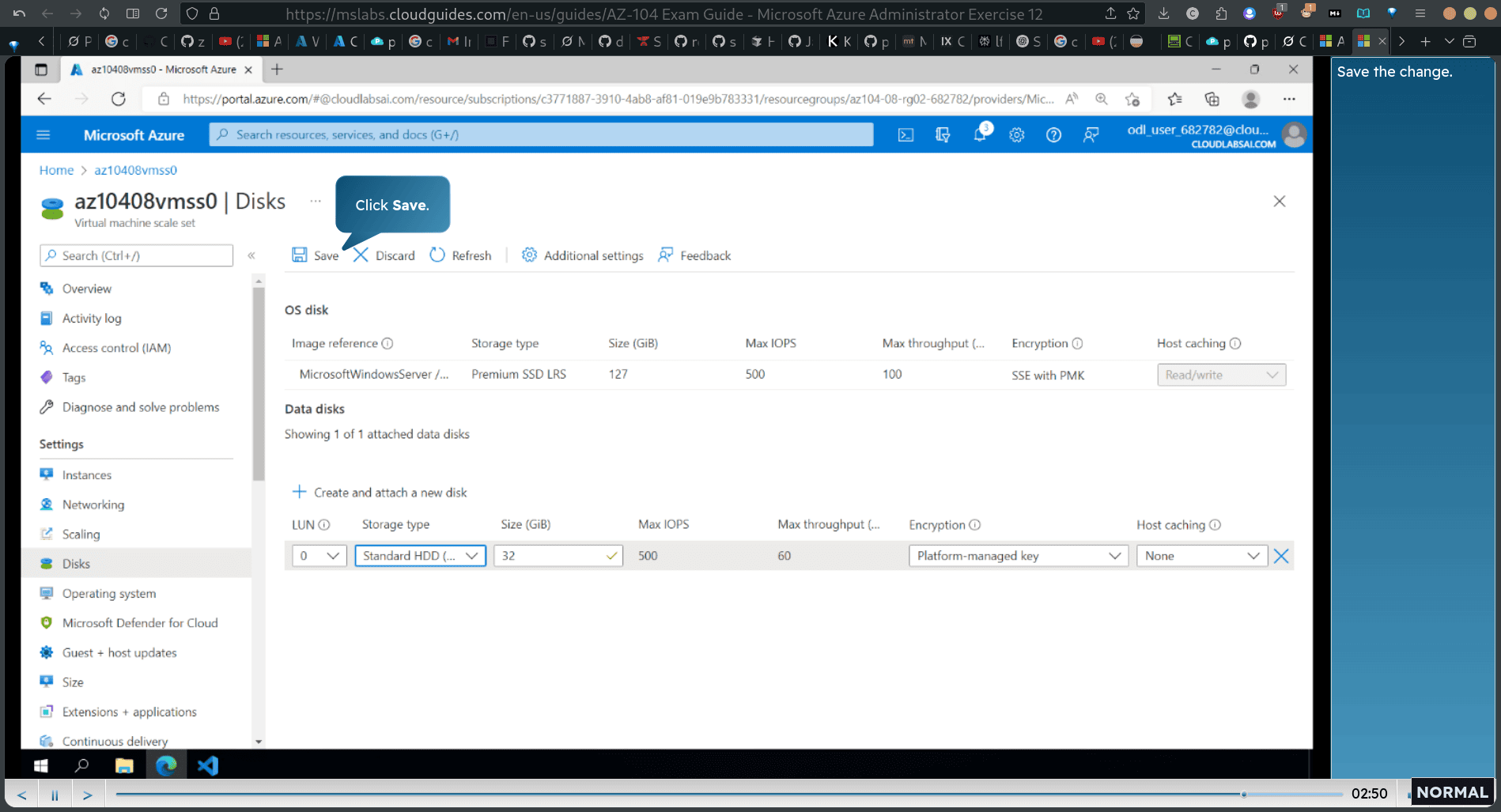
back → instance → select all → upgrade → extenstion → click customscrip extension → click unintsall
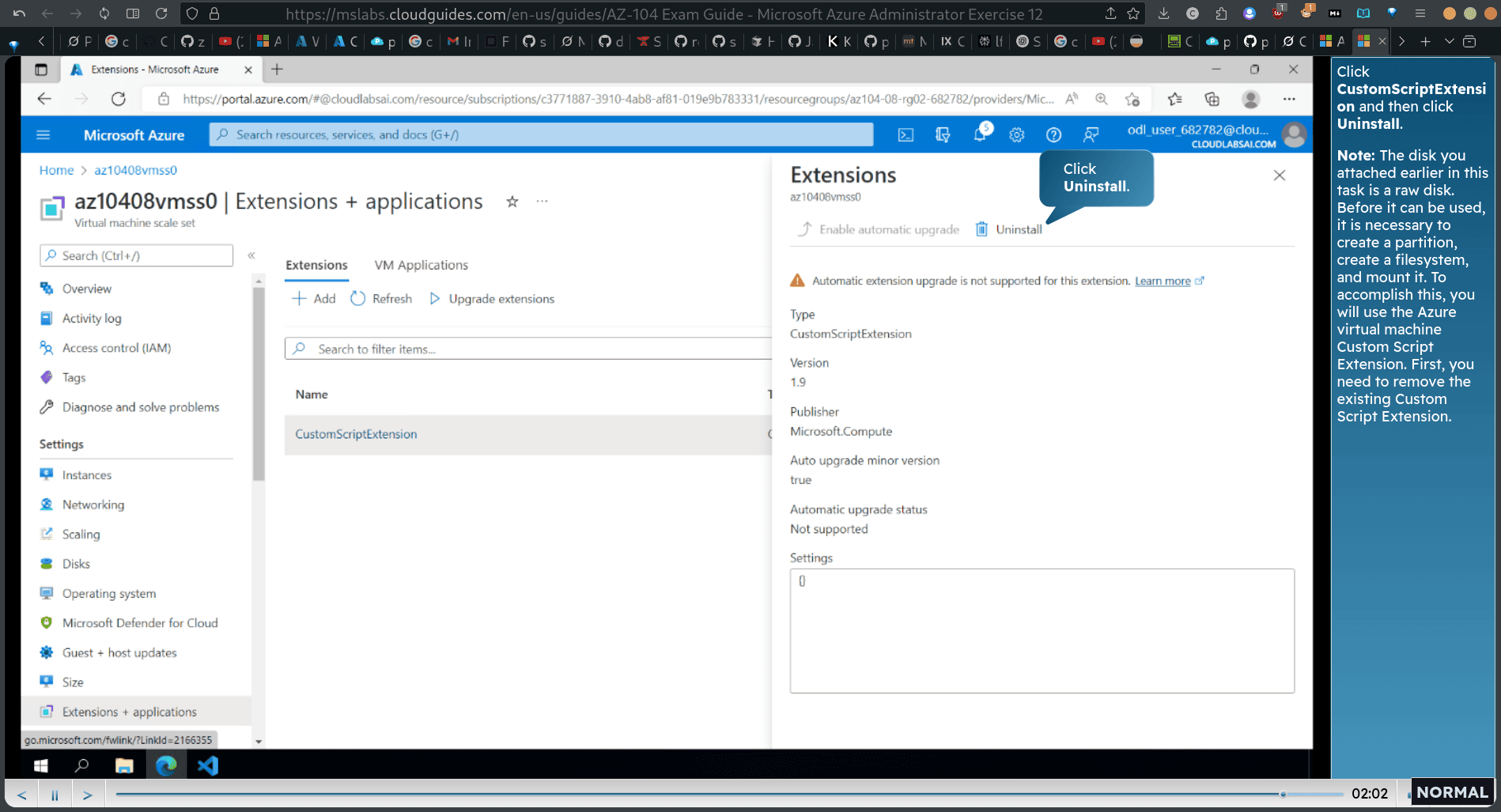 edit the config for vm scale set script (firs file)
edit the config for vm scale set script (firs file)
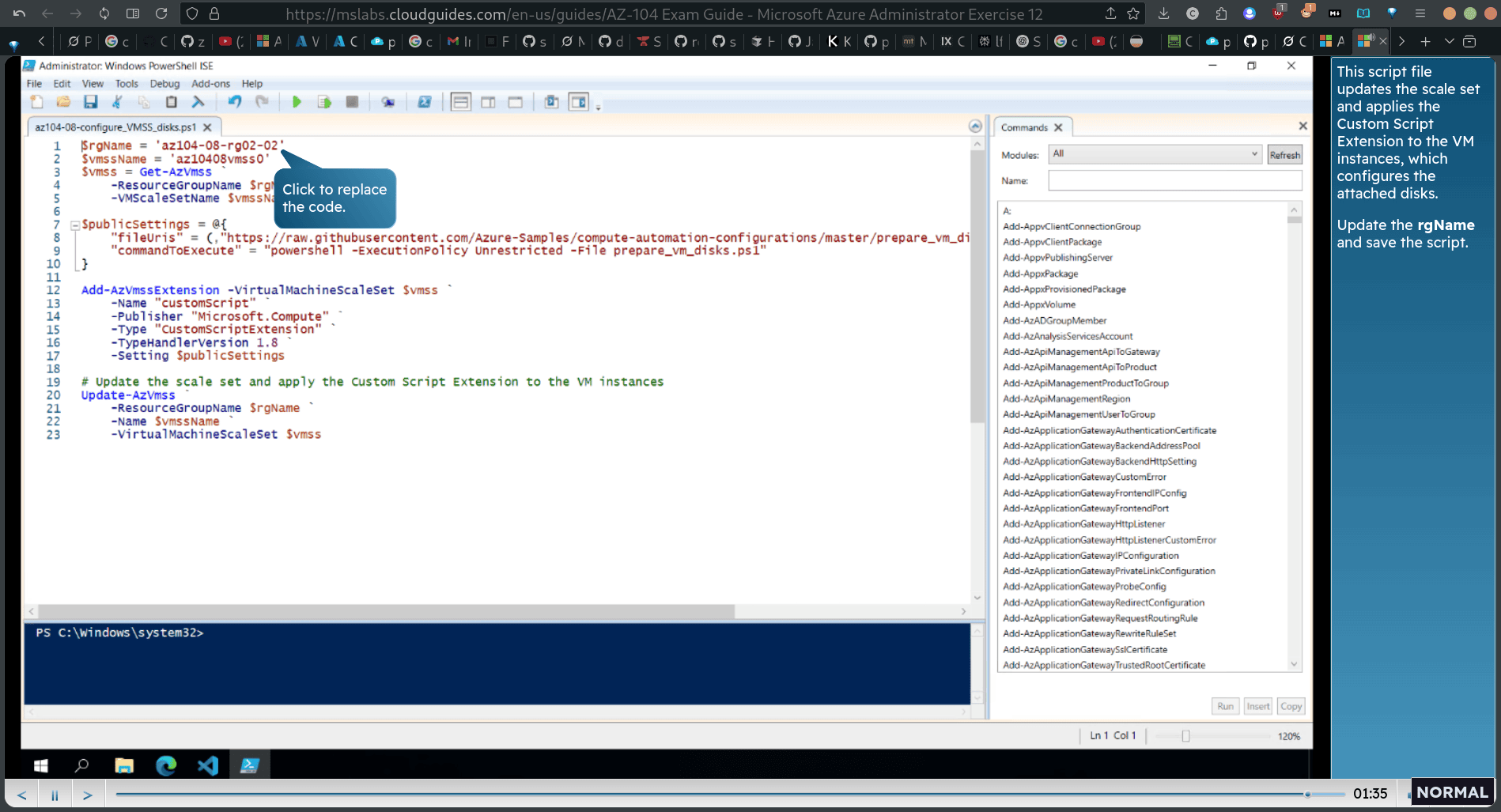 This script file updates the scale set and applies the Custom Script Extension to the VM instances, which configures the attached disks. Update the rgName and save the script.
This script file updates the scale set and applies the Custom Script Extension to the VM instances, which configures the attached disks. Update the rgName and save the script.
upload the edited script
./az104-08-configure_VMSS_disks.psl
back → instance → upgrade
13. Implement Azure Web Apps >
Lab scenario: In this lab, you’ll evaluate the use of Azure Web Apps for hosting websites that are currently hosted in on-premises data centers. The websites are running on Windows servers using the PHP runtime stack. You’ll also determine how you can implement DevOps practices by leveraging Azure Web Apps deployment slots.
Task 1: Create an Azure web app
Task 2: Create a staging deployment slot
click overview url in browser
deploymen slot → add slot → stag(name)
click the new stage slot
Task 3: Configure web app deployment settings
deployment center
→ local git
save Git Clone Uri
→ Local GIt/FTPS credentials
set user scope
save
Task 4: Deploy code to the staging deployment slot
- git clone https://github.com/Azure-Samples/php-docs-hello-world in the cloud powershell
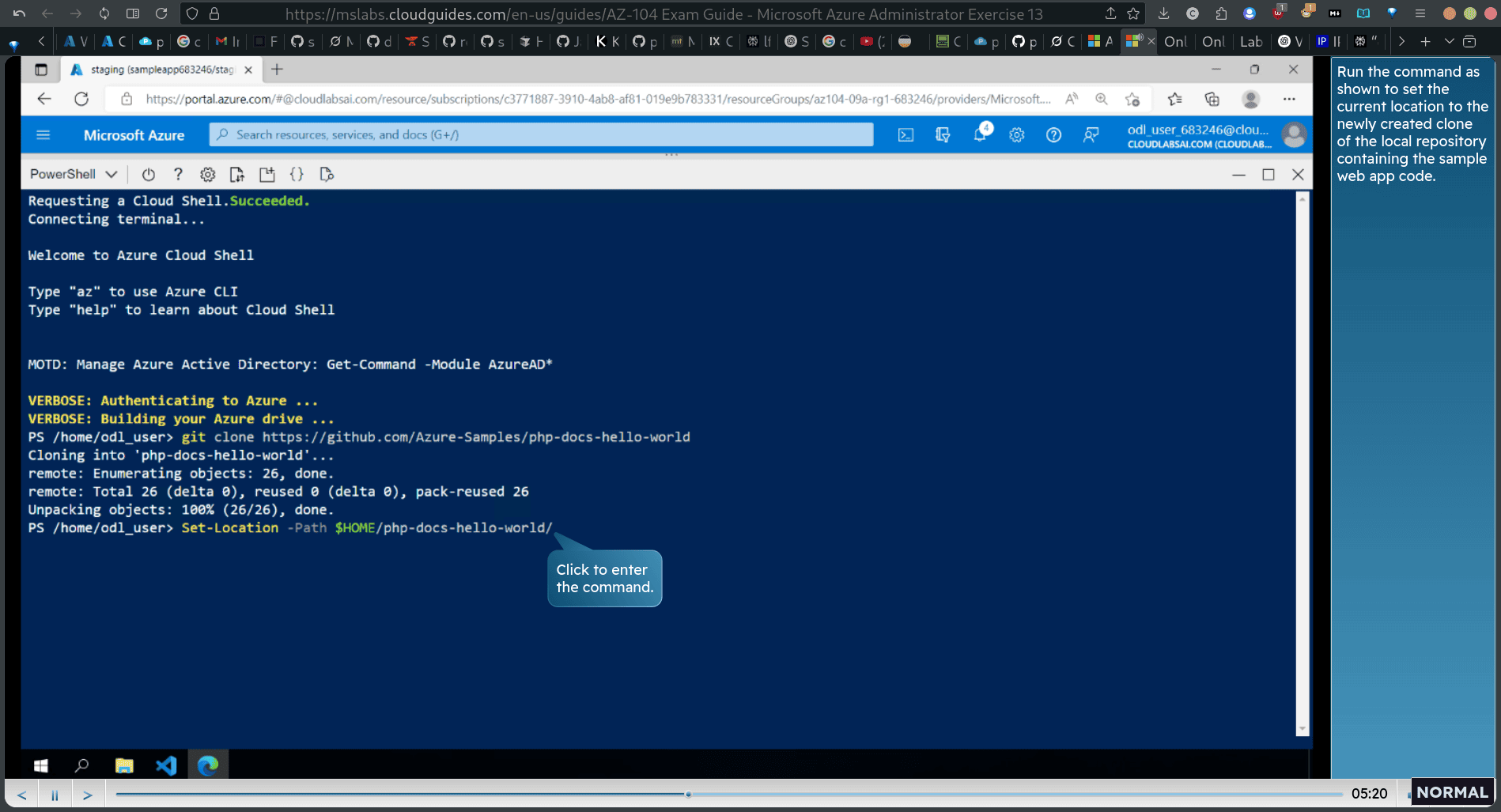 Set-Location -Path $HOME/php-docs-hello-world/
Set-Location -Path $HOME/php-docs-hello-world/
git remote add ContosoDev683246 https://sampleapp683246-staging.scm.azurewebsites.net:443/sampleapp683246.git
git push ContosoDev683246 master
- Run the command as shown to push the sample web app code from the local repository to the Azure web app staging deployment slot.
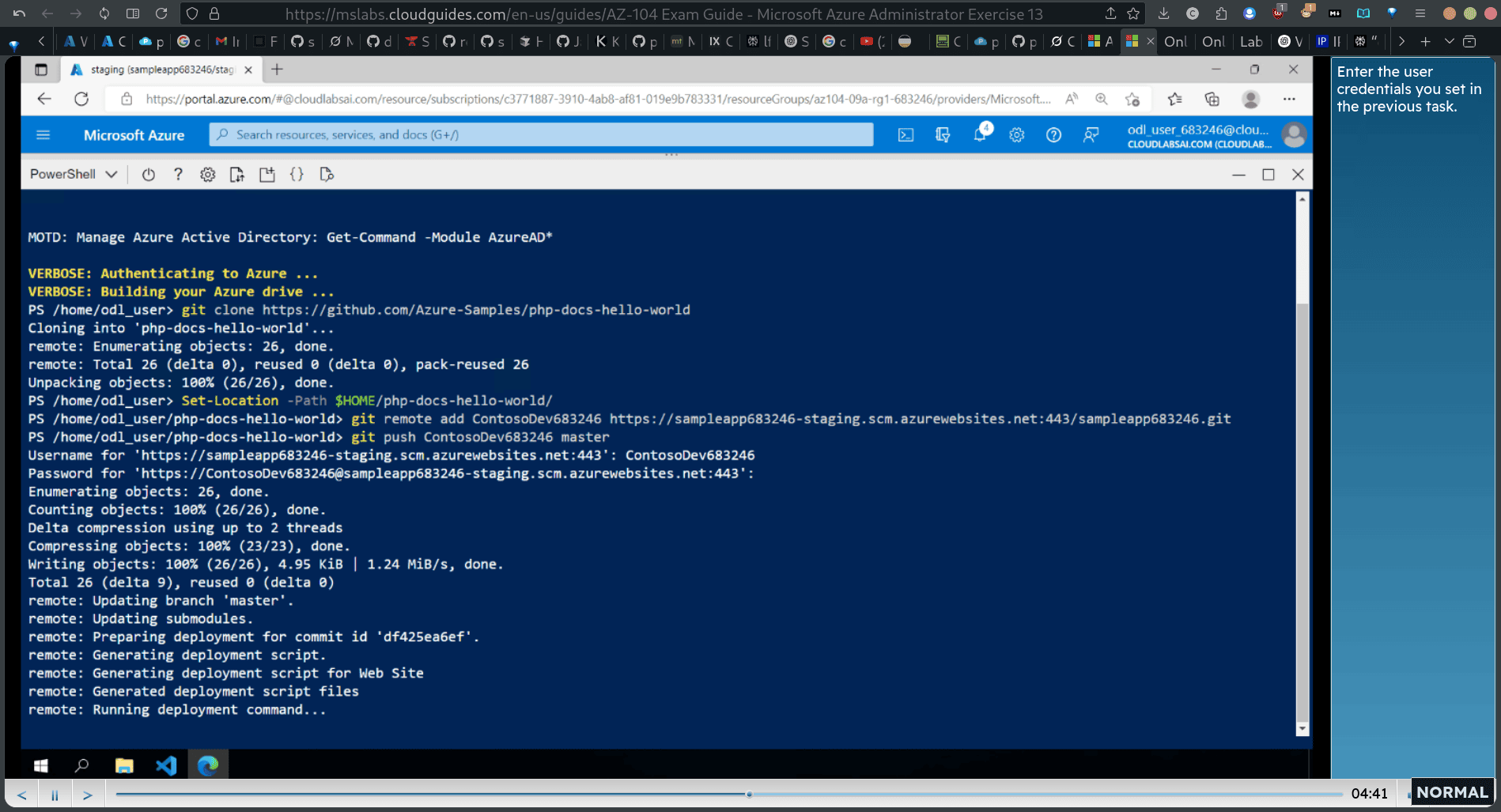
enter previous set user ac
Next, click the URL link to open the web page in a new browser tab. from stage item
→ url work in php now → hello world
Task 5: Swap the staging slots
return to the app service blade → deployment slot
click swap
app service → url
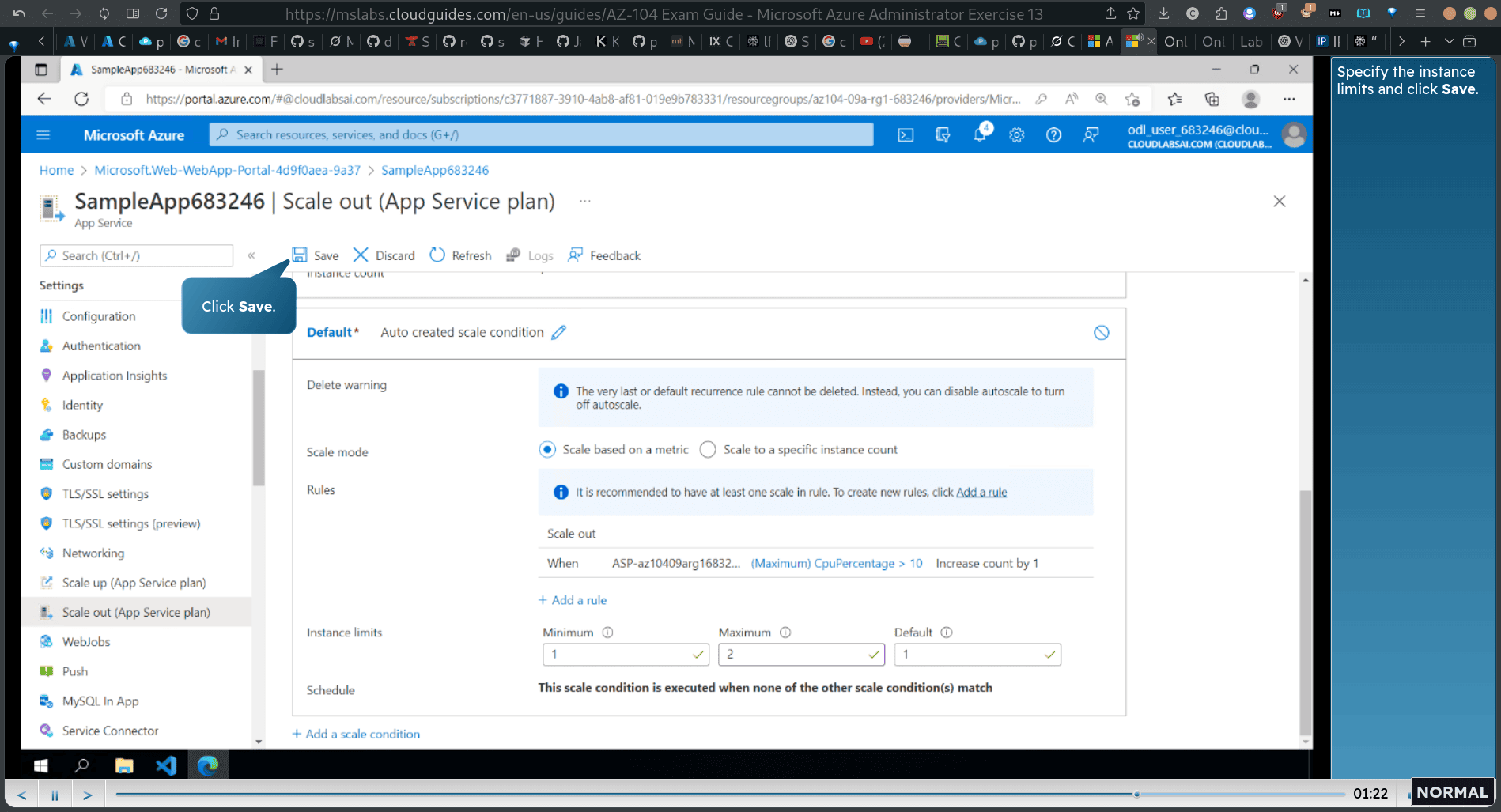
Task 6: Configure and test autoscaling of the Azure web app
 scale out (app service plan)
scale out (app service plan)
custom auto scale
- time aggregation + cpu percentage
 webapp Get-AzWebApp -ResourceGroupName $rgNam=‘
webapp Get-AzWebApp -ResourceGroupName $rgNam=‘
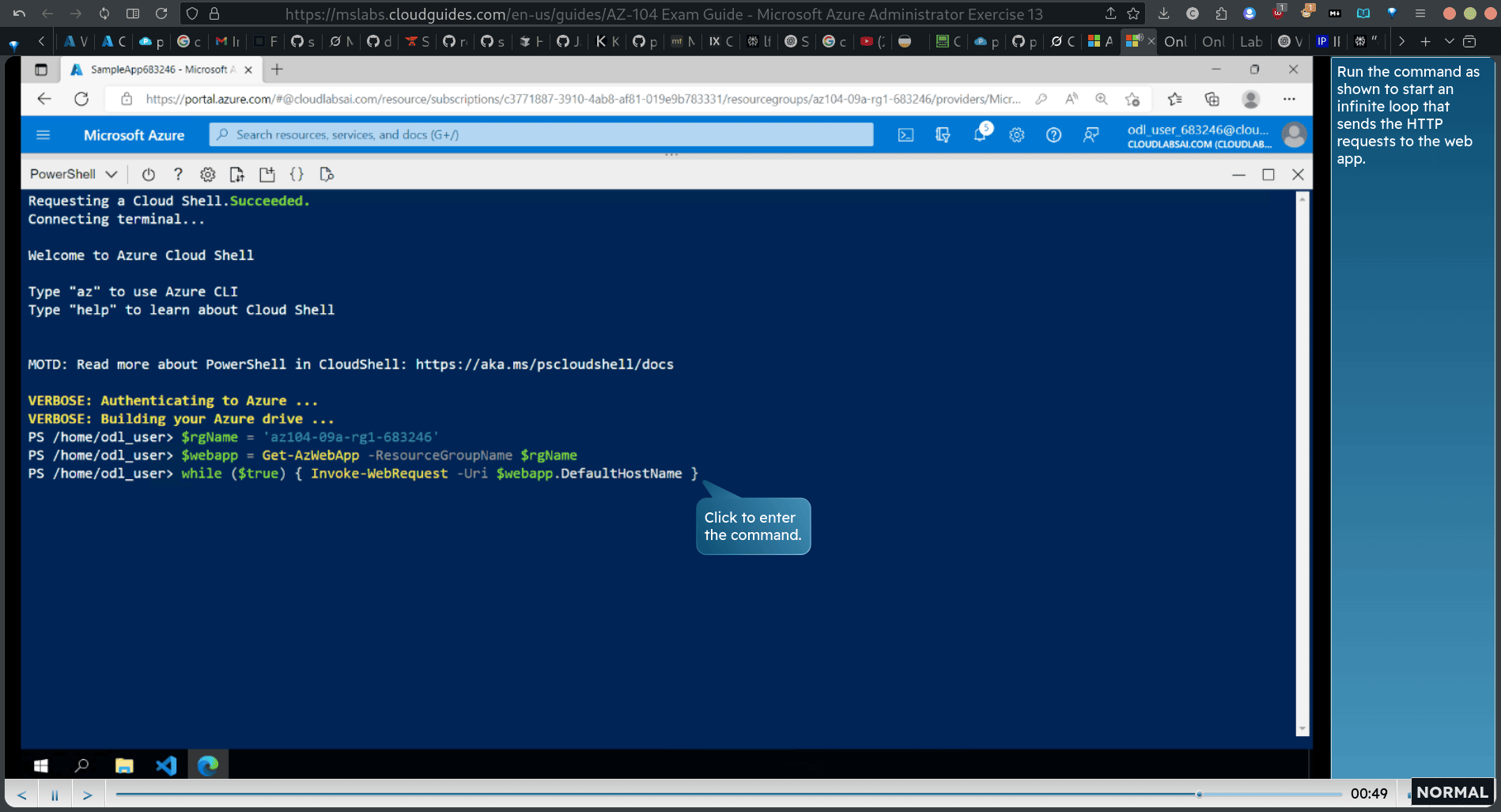 Run the command as shown fo start an infinite loop that sends the HTTP requests to the web app.
Run the command as shown fo start an infinite loop that sends the HTTP requests to the web app.
while (true) { Invoke-WebRequest -Uri webapp.DefaultHostName }
 → process explorer
→ process explorer
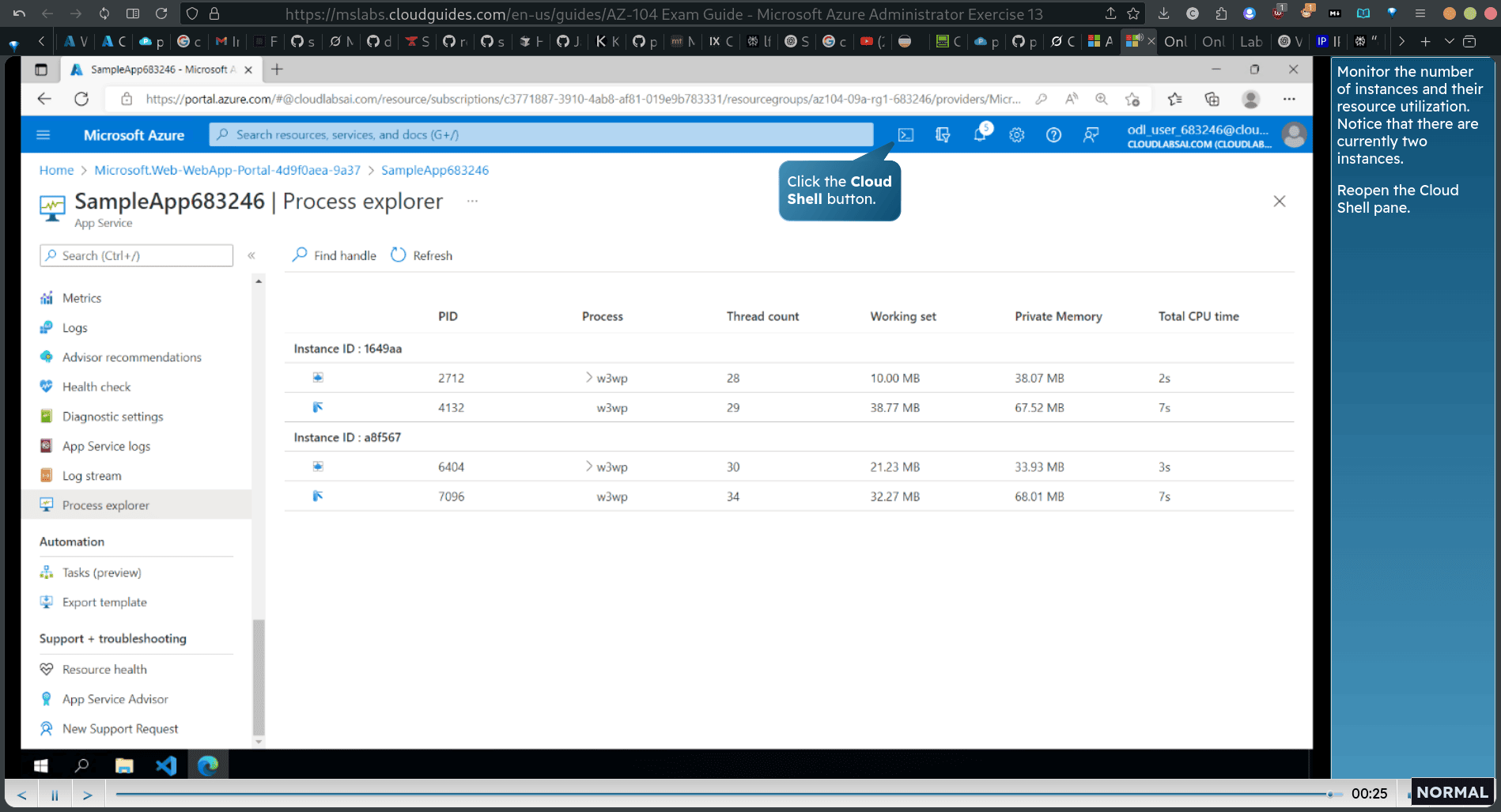
- Monitor the number of instances and their resource utilization. Notice that there are currently two instances. Reopen the Cloud Shell pane.
14. Implement Azure Container Instances >
In this lab, you will complete the tasks listed on your screen. Lab scenario: In this lab, you’ll evaluate the use of Azure Container Instances for the deployment of Docker images to minimize container management.
Task 1: Deploy a Docker image using the Azure Container Instance
→ Container instance → dns name label
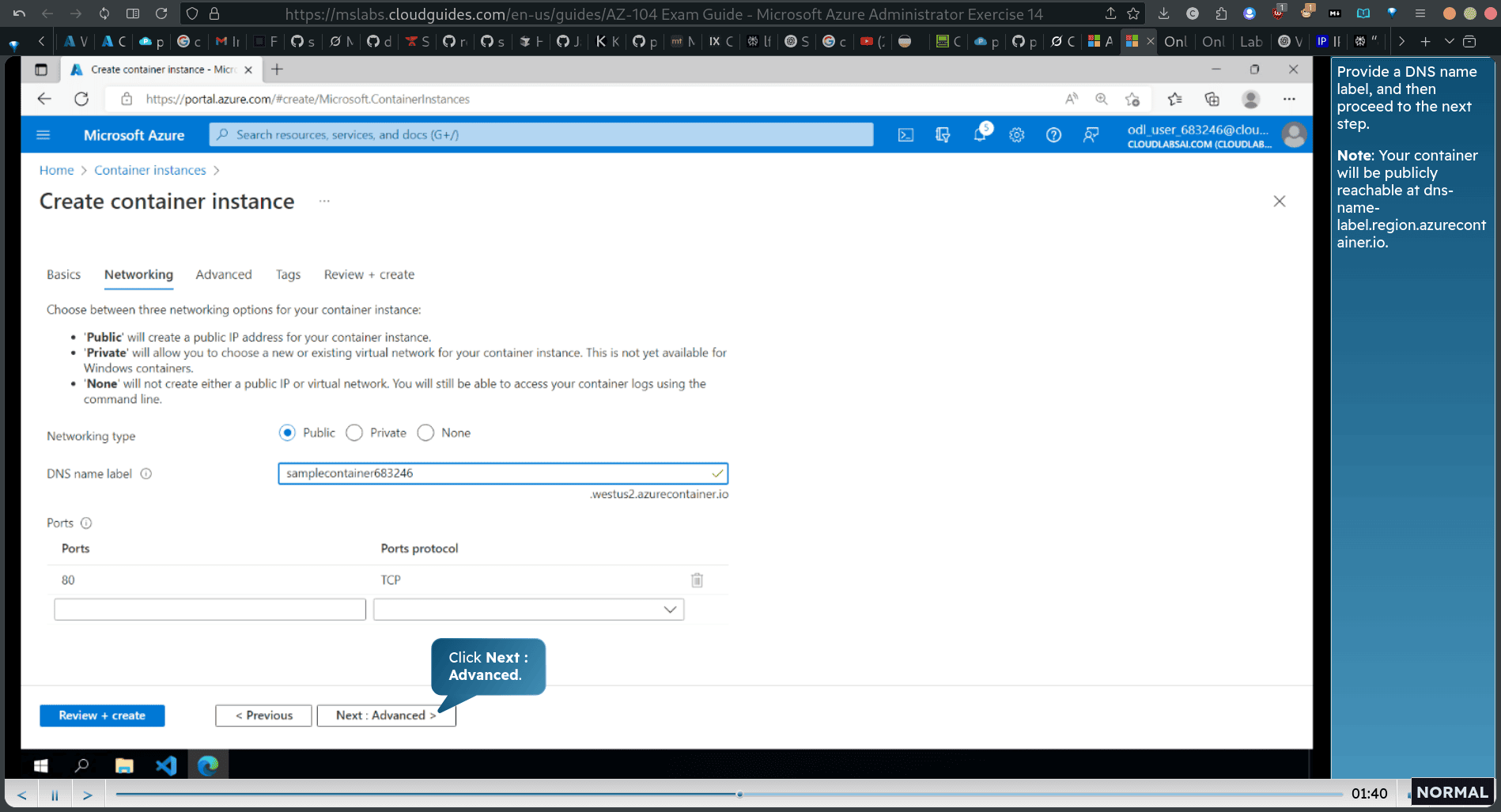
Task 2: Review the functionality of the Azure Container Instance
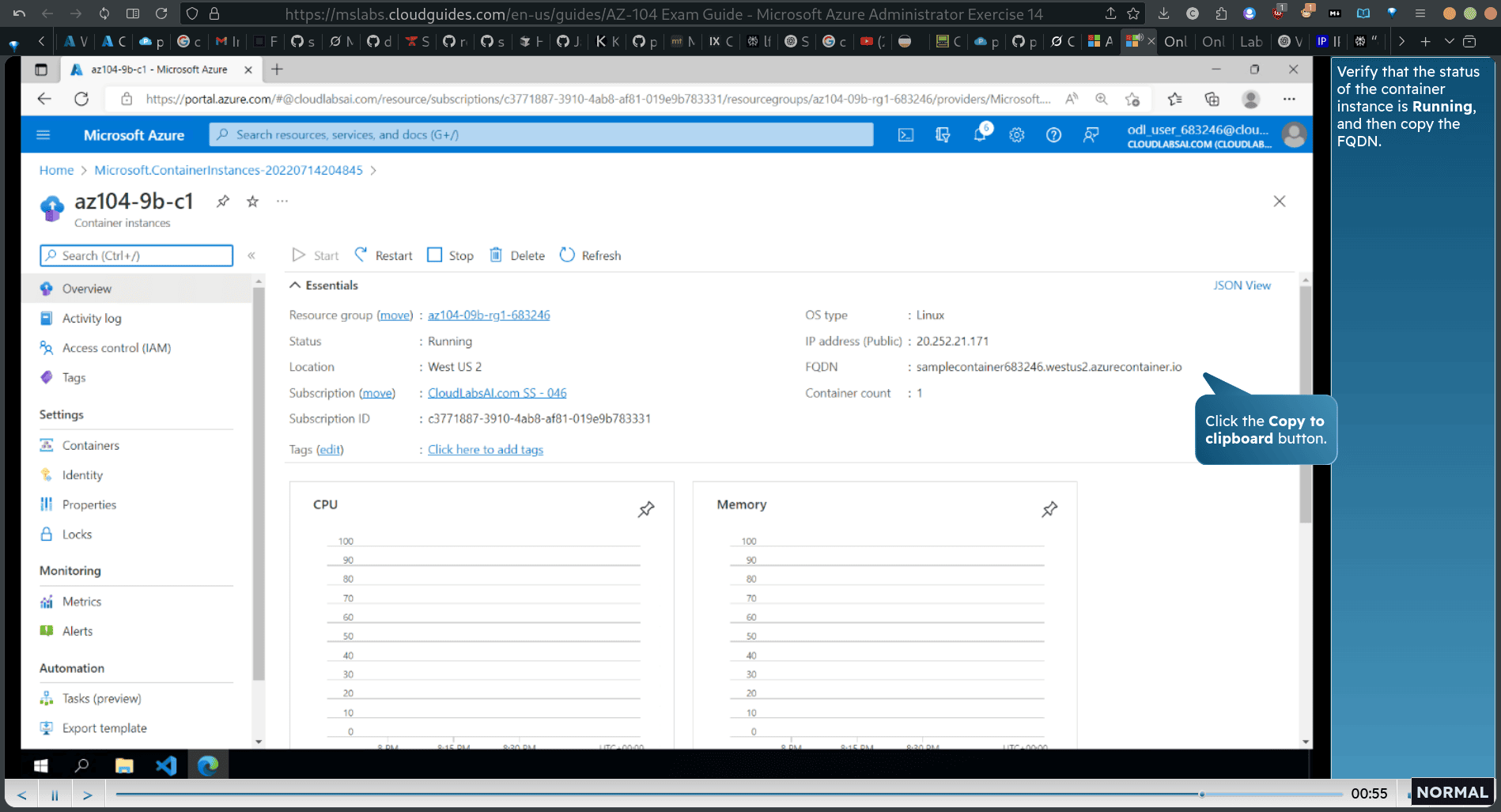 Verify that the status of the container instance is Running, and then copy the FQDN.
Verify that the status of the container instance is Running, and then copy the FQDN.
url → io in browser
→ container → logs You can see the log entries representing the HTTP GET request generated by displaying the application in the browser.
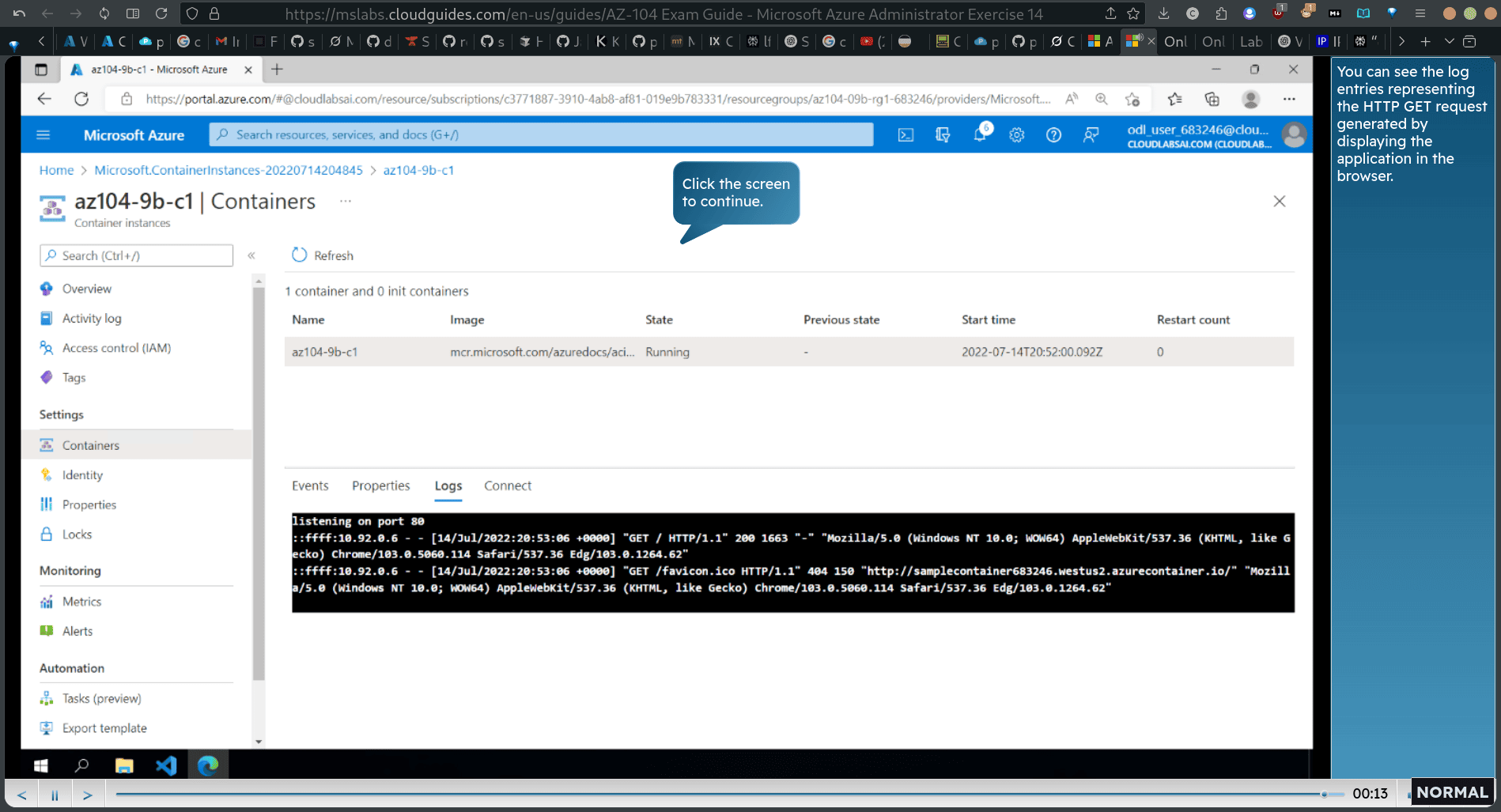
15. Implement Azure Kubernetes Service >
Task 1: Register resource providers
→ subscription → resource provider → search k8s
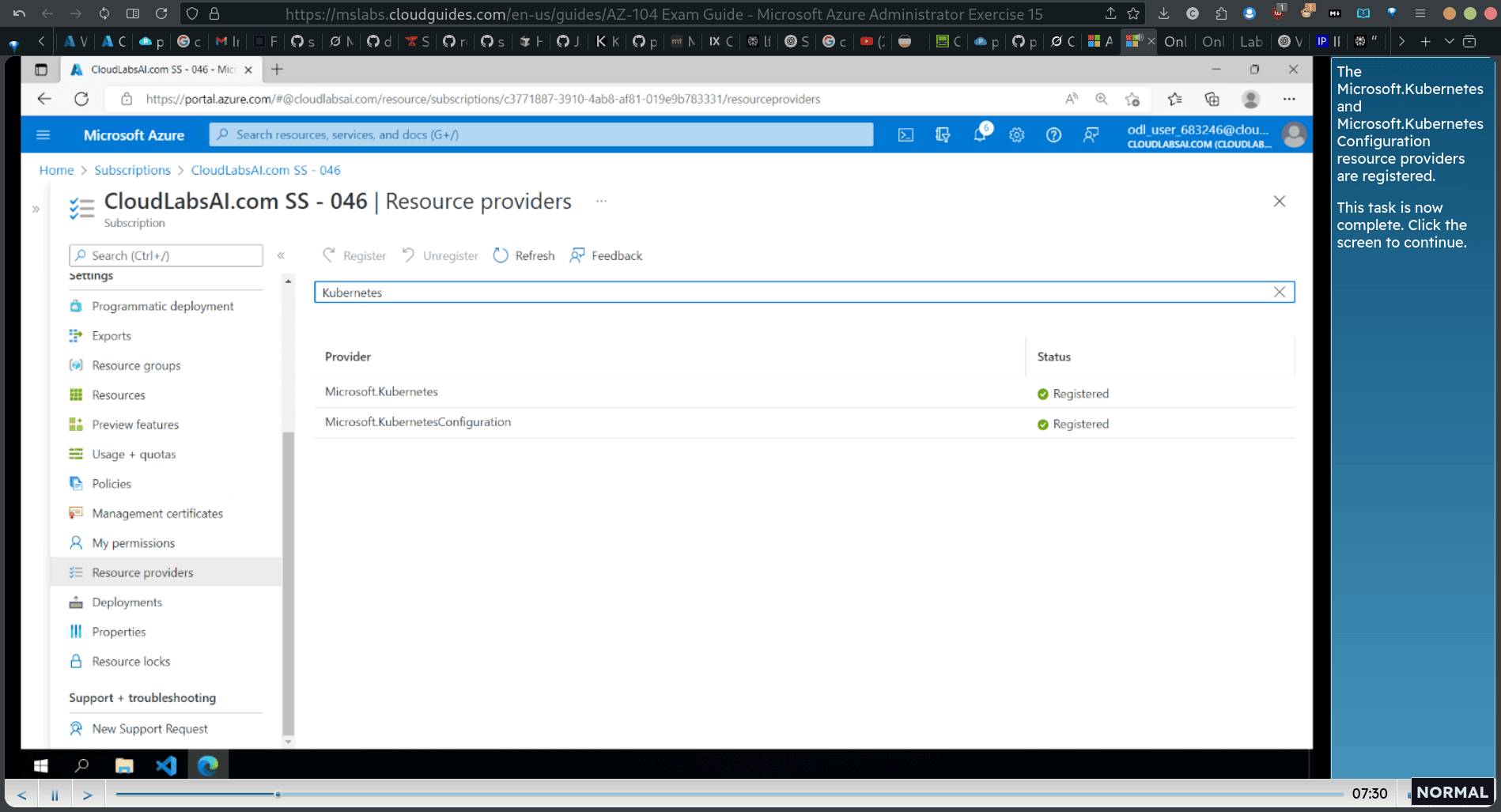 The Microsoft.Kubernetes and Microsoft.Kubernetes Configuration resource providers are registered. This task is now complete. Click the screen to continue.
The Microsoft.Kubernetes and Microsoft.Kubernetes Configuration resource providers are registered. This task is now complete. Click the screen to continue.
Task 2: Deploy an Azure Kubernetes Service cluster
→ search k8s service → craeter k8s cluster
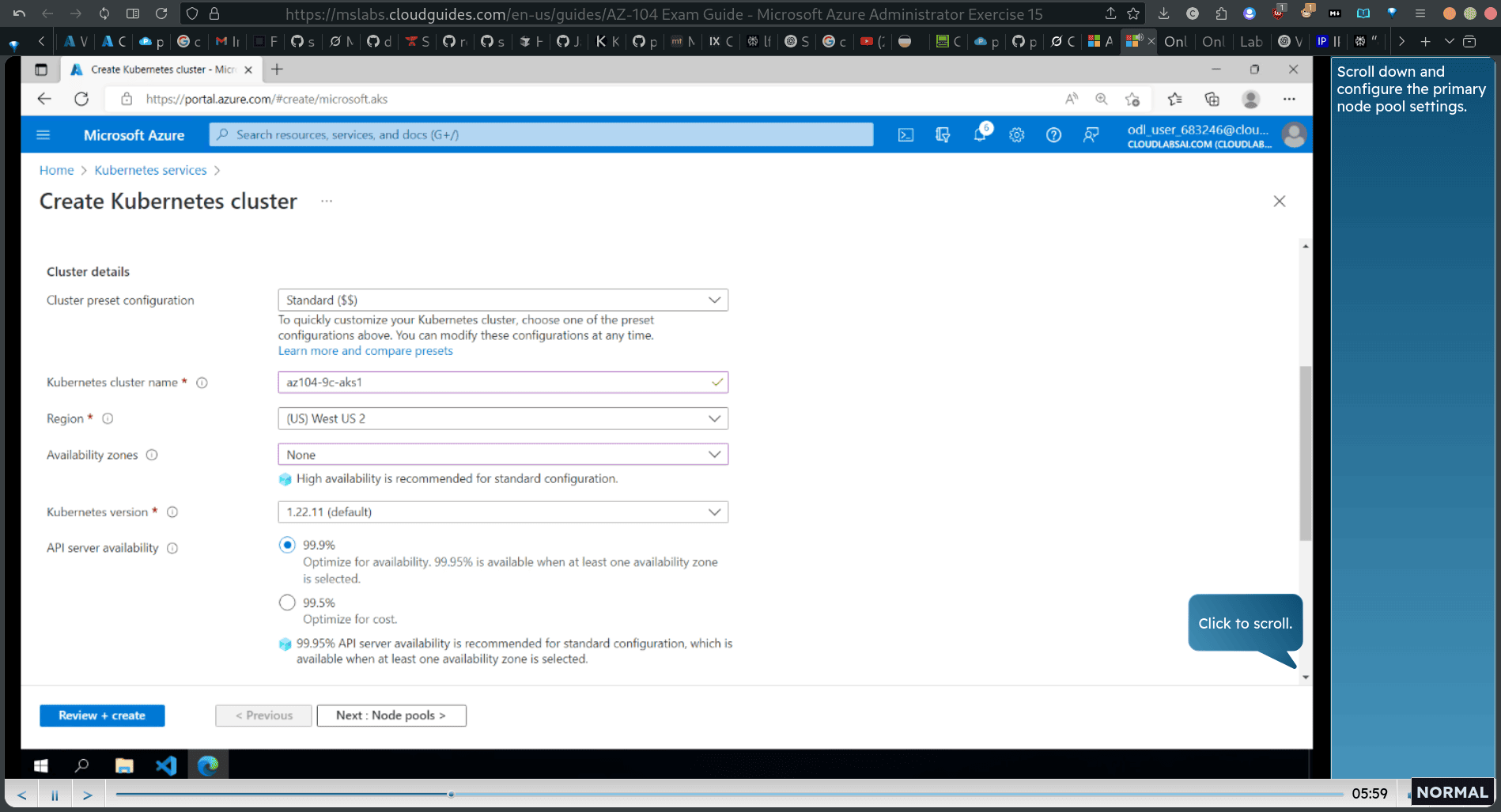 Scroll down and configure the primary node pool settings.
Scroll down and configure the primary node pool settings.
manual → 1 here
Provide a DNS name prefix and continue to the next step.
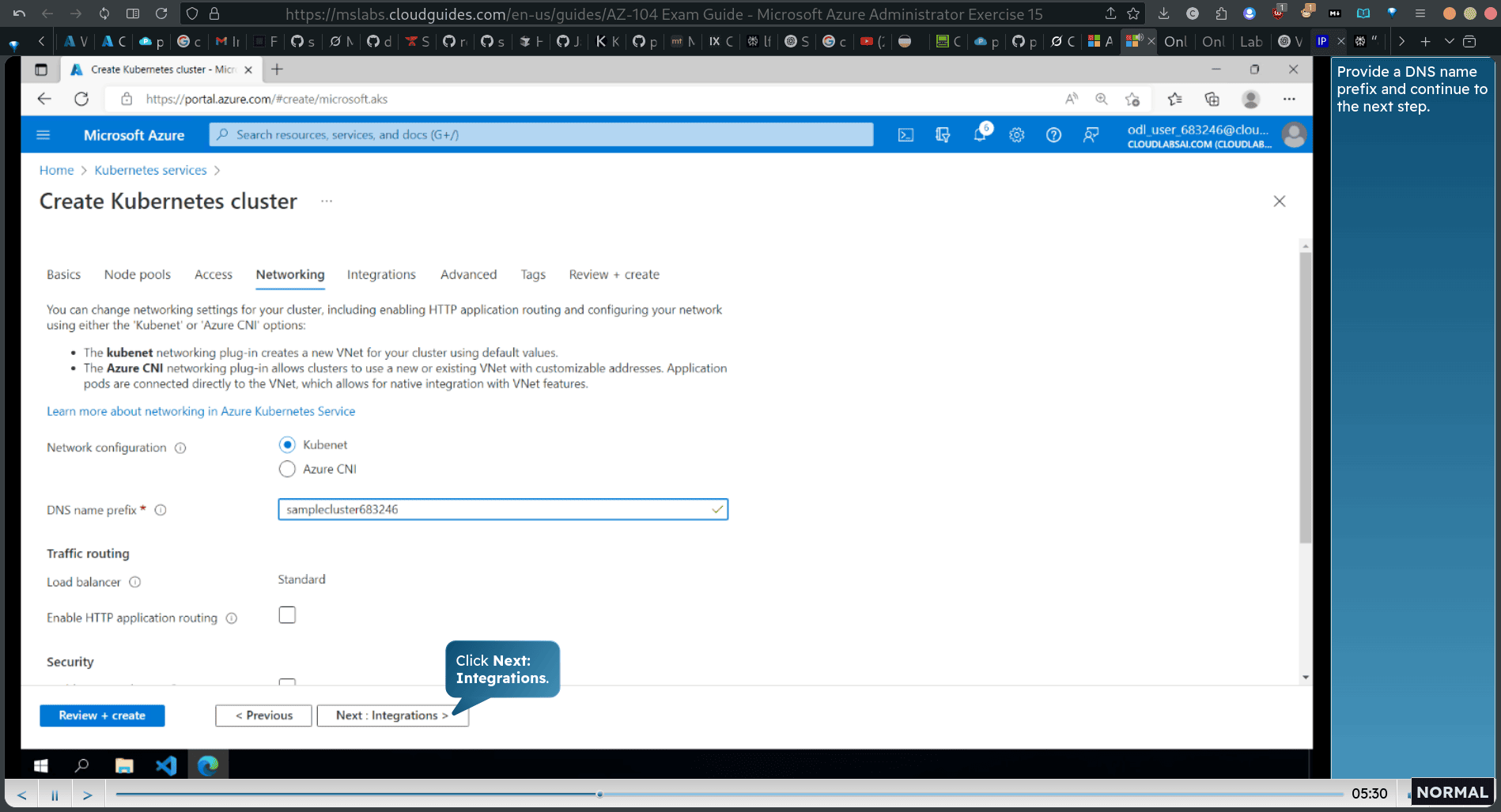 disable container monitoring
disable container monitoring
Task 3: Deploy a pod into the Azure Kubernetes Service cluster
→ k8s service → node pools
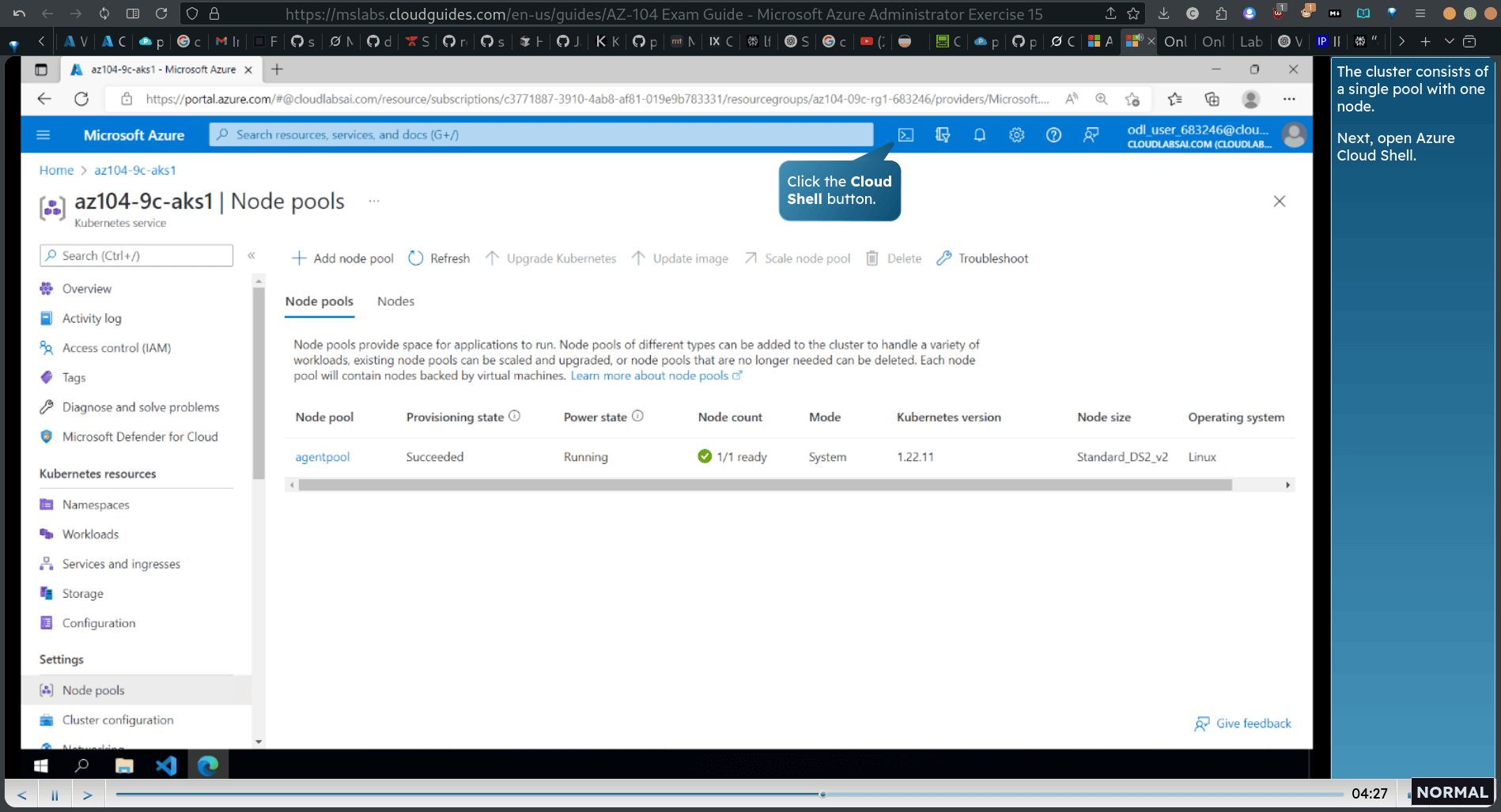
cloud → bash
RESOURCE_GROUP=“‘az104-09c-rgl-683246
AKS_CLUSTER=“az104-9c-aks1’
az aks get-credentials —resource-group AKS_CLUSTER
kubectl get nodes
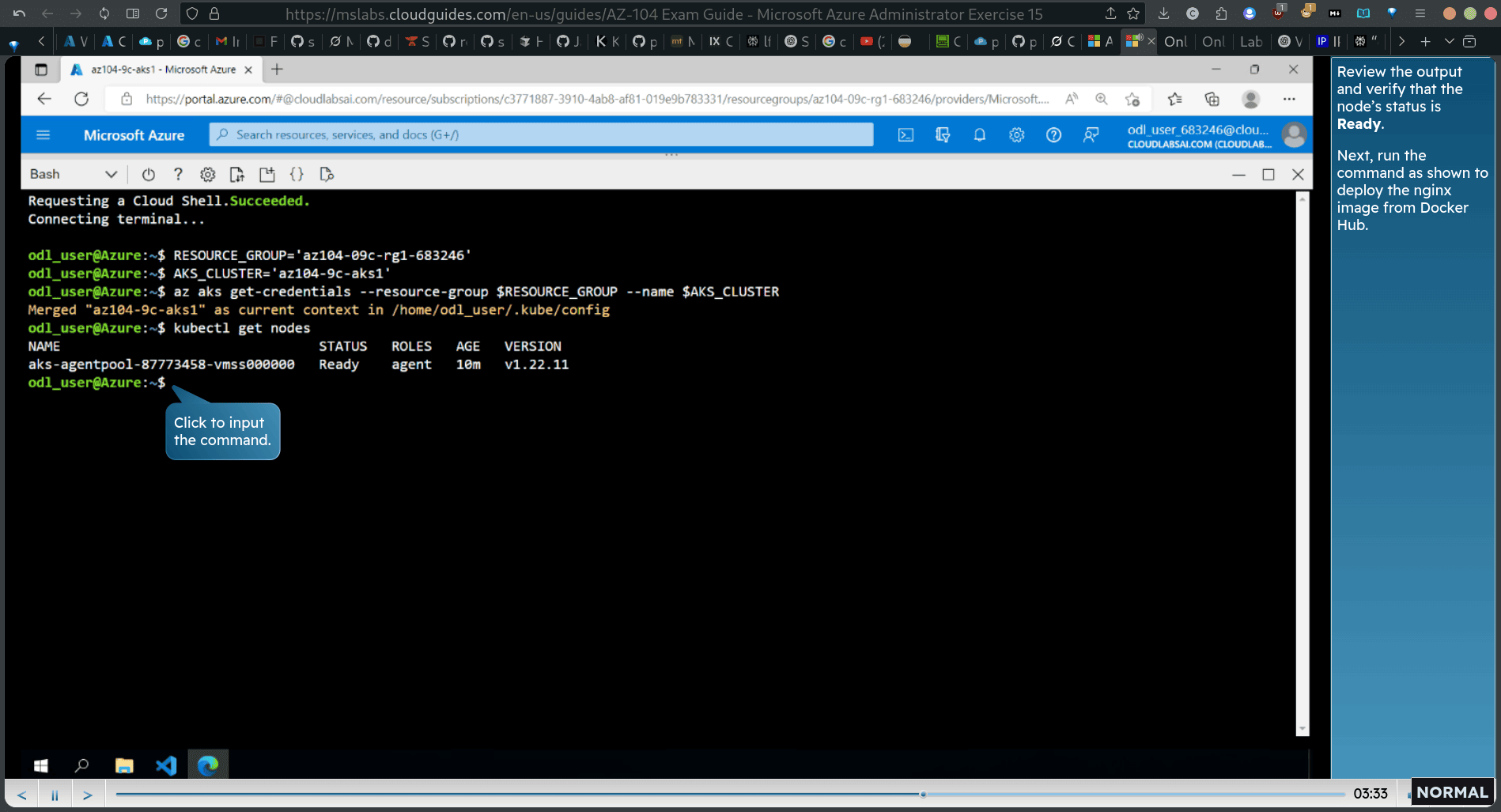 kubectl create deployment nginx-deployment —image=nginx
kubectl create deployment nginx-deployment —image=nginx
kubectl get pods
kubectl get deployment
kubectl expose deployment nginx-deployment —port=80 —type=LoadBalancer
kubectl get service
- (public ip address provisioned)
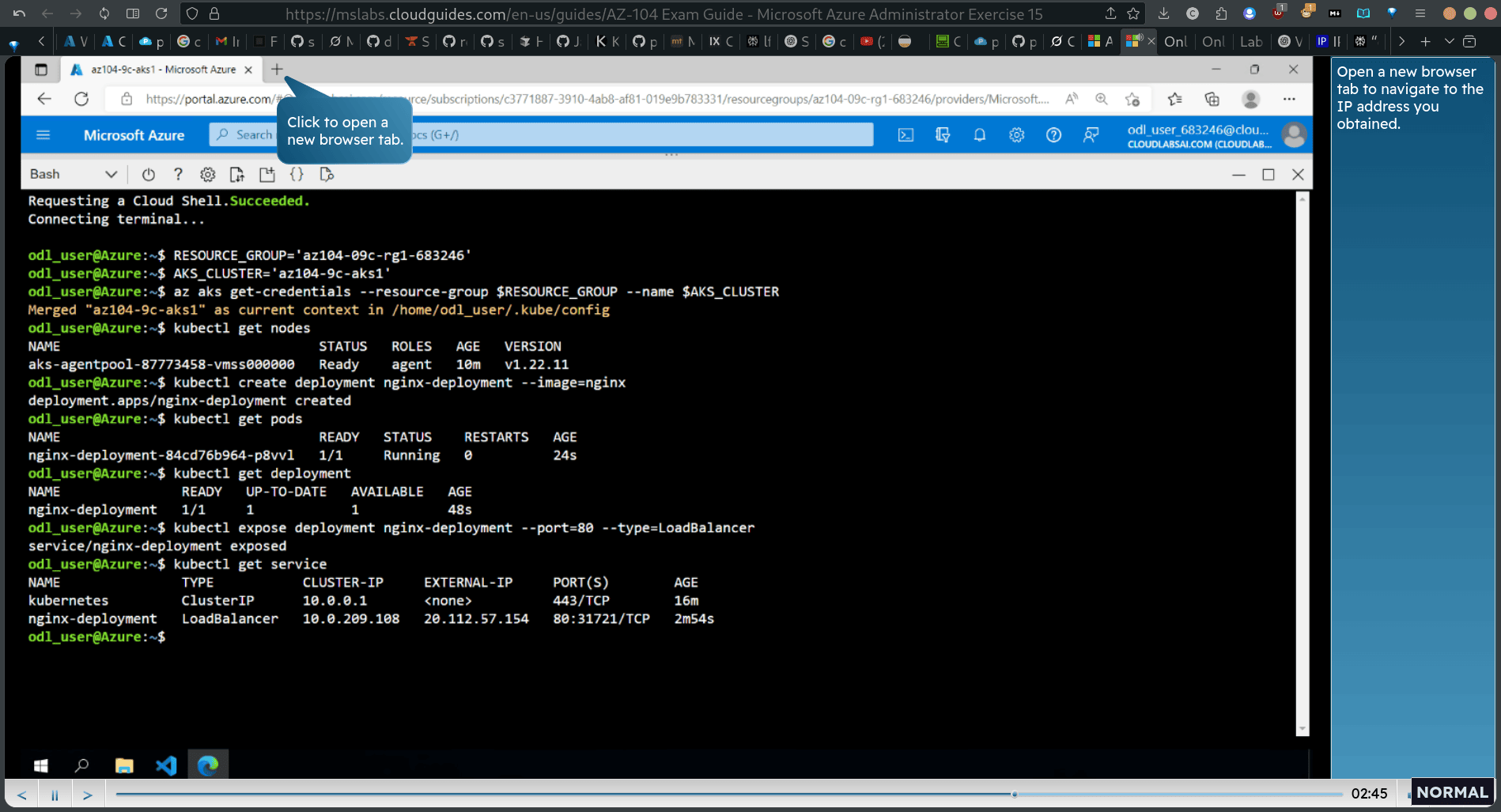
browser get the ip address from kubectl get service
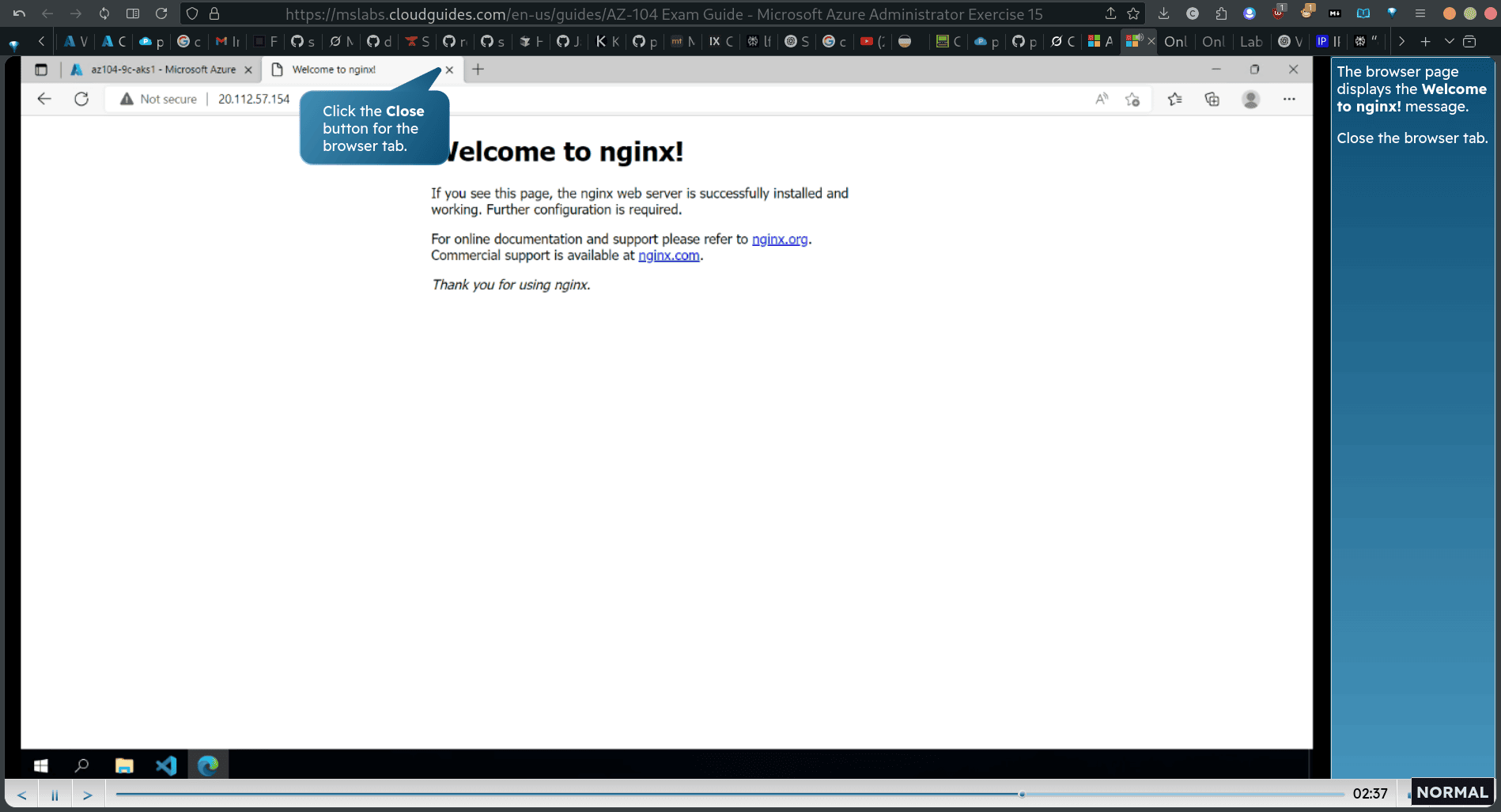
Task 4: Scale containerized workloads in the Azure Kubernetes Service cluster
kubectl scale —replicas=2 deployment/nginx-deployment
- increase pod
→ scaled
kubectl get pods
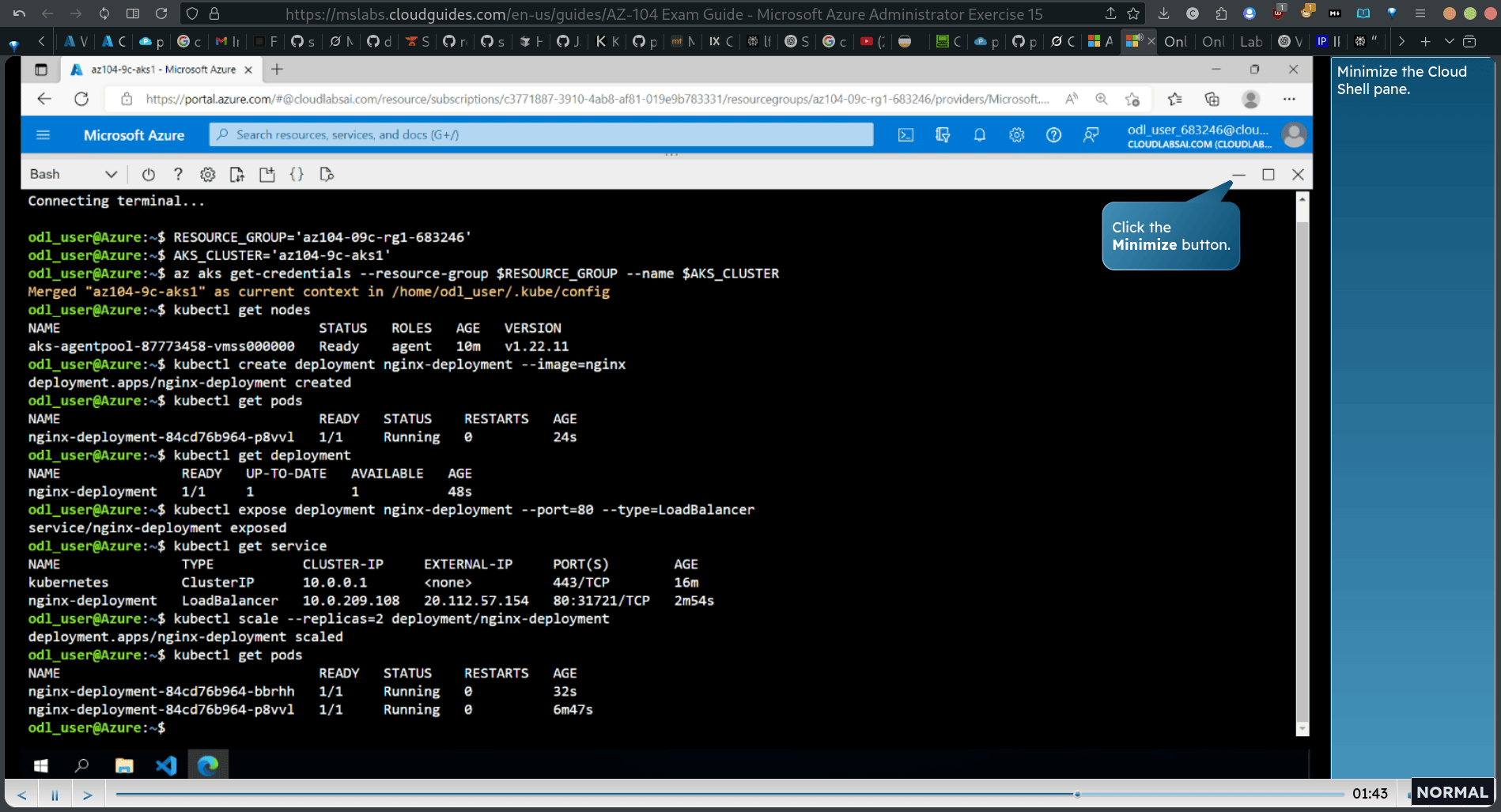
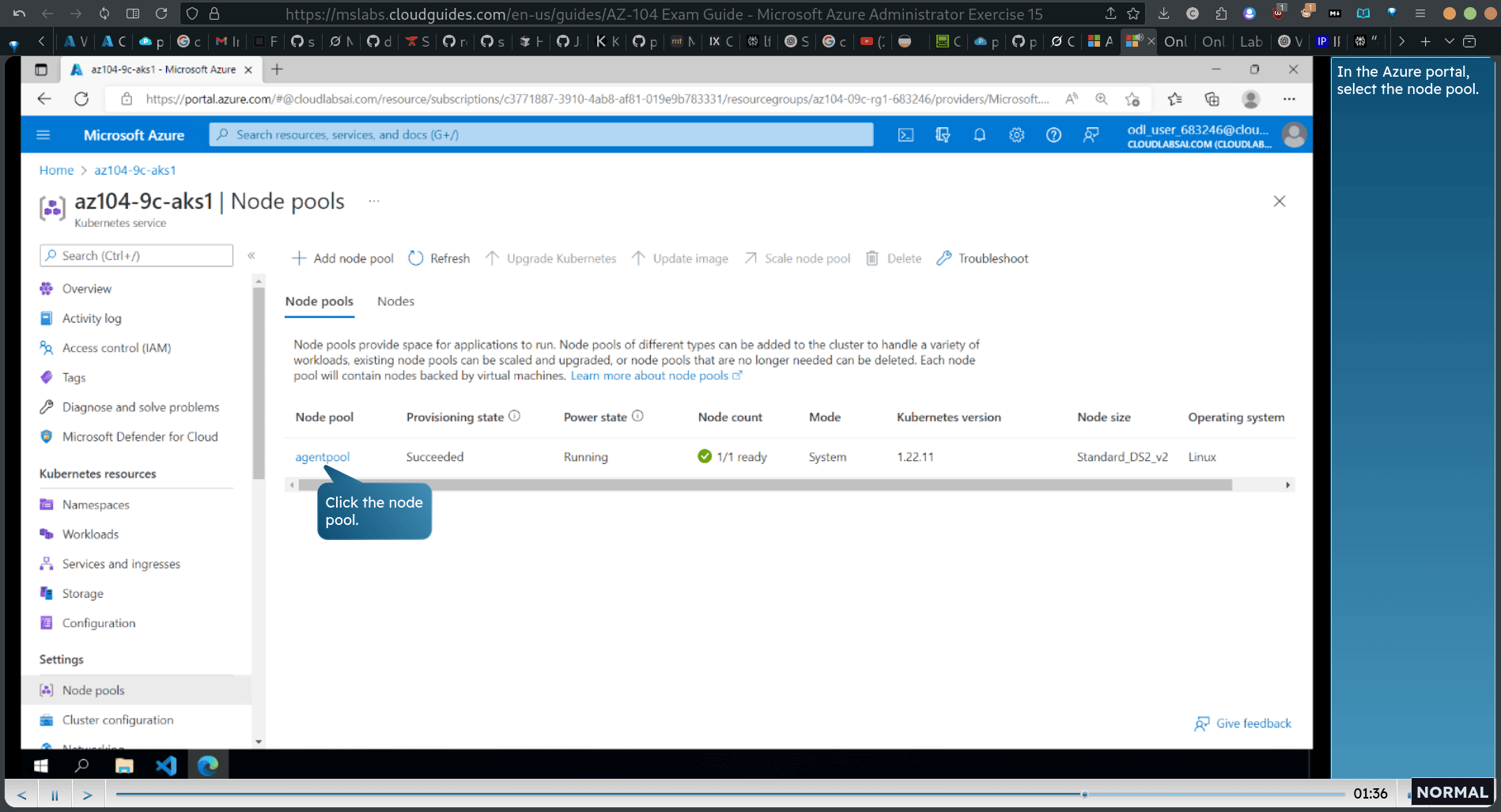 back → node pools → scale node pools
back → node pools → scale node pools
 az aks scale —resource-group AKS_CLUSTER —node-count 2
az aks scale —resource-group AKS_CLUSTER —node-count 2
 kubectl get nodes
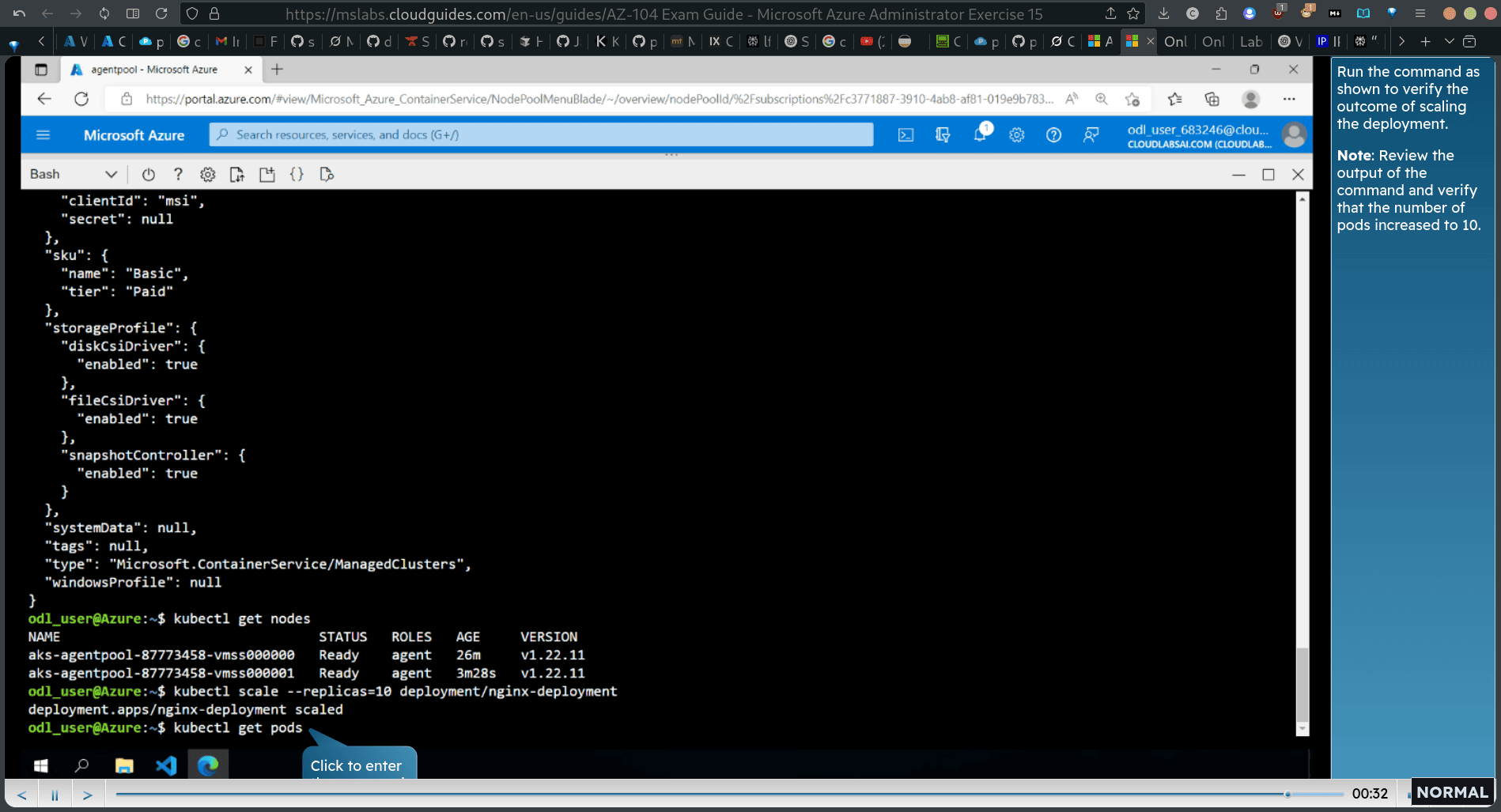
kubectl scale —replicas=1@ deployment/nginx-deployment
kubectl get nodes
kubectl scale —replicas=1@ deployment/nginx-deployment
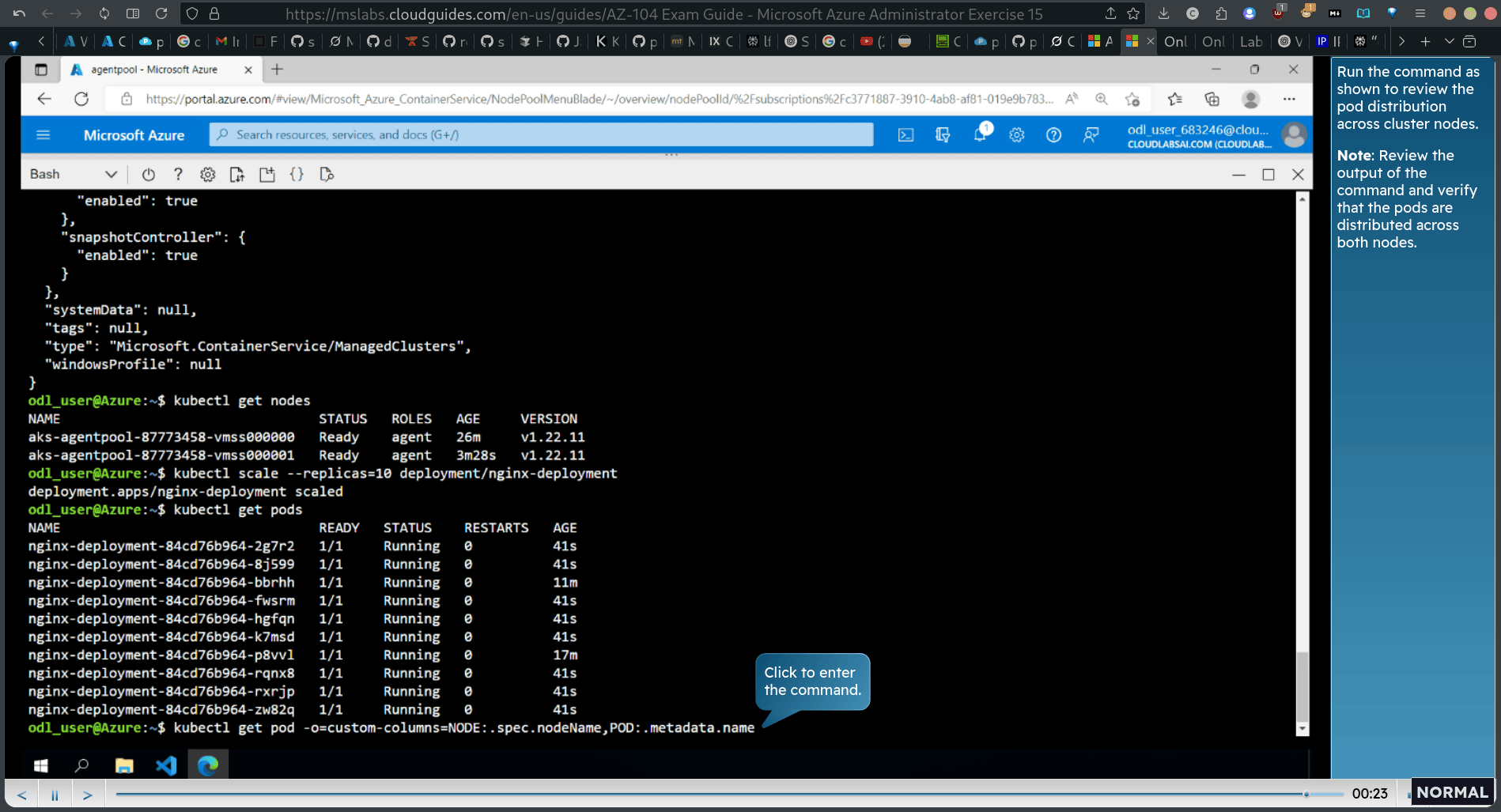
kubectl get pods kubectl get pod -o=custom-columns=NODE:.spec.nodeName,POD: .metadata.name
Run the command as shown fo review the pod distribution across cluster nodes. Note: Review the output of the command and verify that the pods are distributed across both nodes.
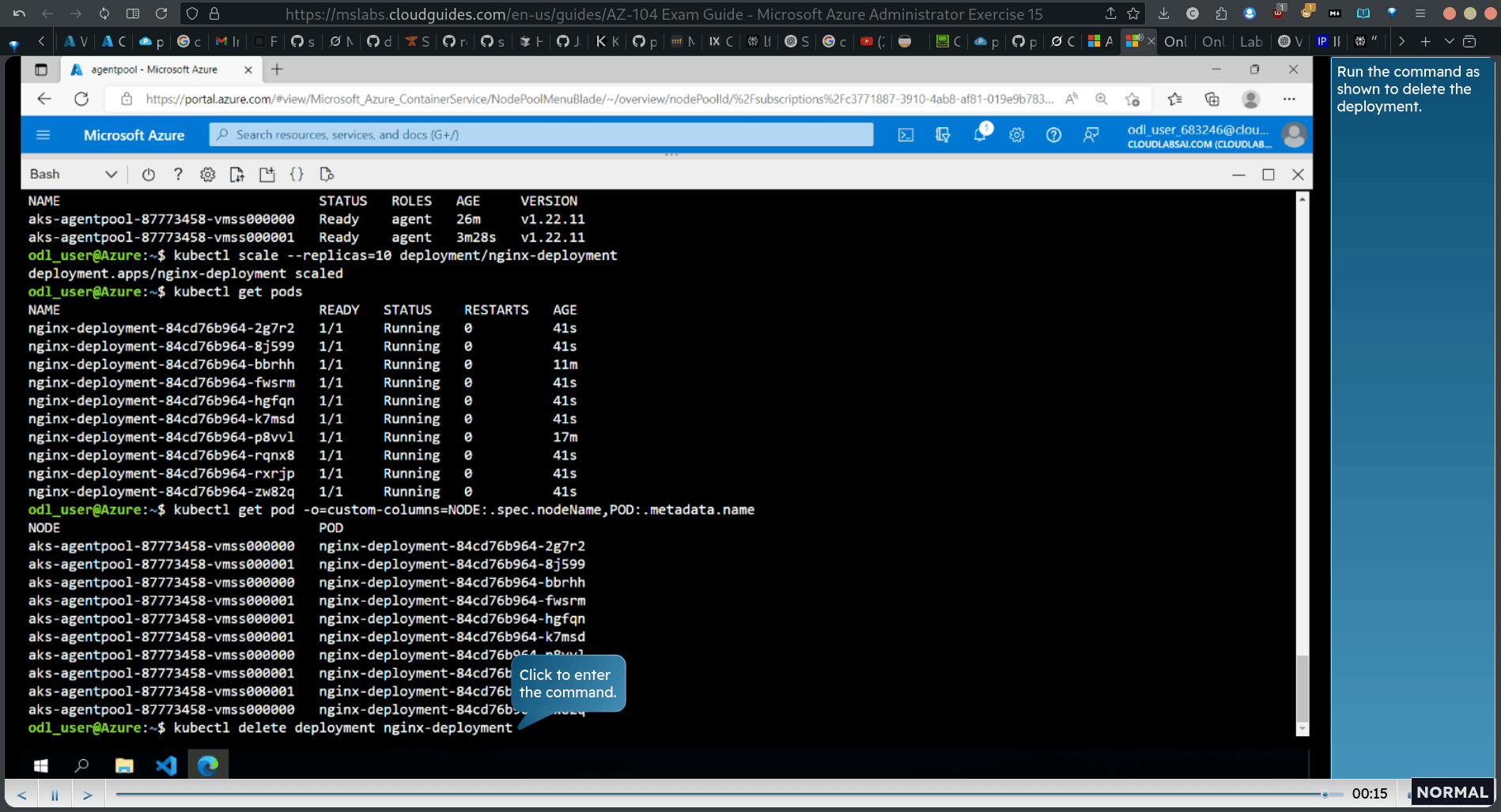 kubectl delete deployment nginx-deployment
kubectl delete deployment nginx-deployment